سنسور های خودرو
2 ماه پیش
2.63 مگابایت
نوع : pdf
بازدید : 550
منتشرکننده : فردین گردی
|
جانمایی فیوزها و رله های خودرو ری را
6 ماه پیش
0.53 مگابایت
نوع : pdf
بازدید : 1477
منتشرکننده : رستگاری
|
نقشه ایسیو سقا (SAGHA) دنا EF7
6 ماه پیش
1.6 مگابایت
نوع : pdf
بازدید : 1693
منتشرکننده : رستگاری
|
راهنمای باز و بست و جانمایی دسته سیمهای خودرو تارا
7 ماه پیش
1.8 مگابایت
نوع : pdf
بازدید : 1097
منتشرکننده : رضا
|
نکات کلیدی گیربکس اتوماتیک تارا
7 ماه پیش
2.82 مگابایت
نوع : pdf
بازدید : 1064
منتشرکننده : رضا
|
راهنمای باز و بست گیربکس اتوماتیک تارا
7 ماه پیش
3.35 مگابایت
نوع : pdf
بازدید : 1207
منتشرکننده : رضا
|
جزوه روشن نشدن خودرو از سایت دکتر مکانیک
10 ماه پیش
11.79 مگابایت
نوع : pdf
بازدید : 1856
منتشرکننده : yhxyhxc
|
دوره دزگیر فن اموزان
10 ماه پیش
1.19 مگابایت
نوع : pdf
بازدید : 1640
منتشرکننده : yhxyhxc
|
دوره سیستم صوتی فن اموزان
10 ماه پیش
2.62 مگابایت
نوع : pdf
بازدید : 1539
منتشرکننده : yhxyhxc
|
جزوه دوره سیم کشی دکتر مکانیک
|
دستورالعمل عیب یابی دریچه گاز و پدال گاز الکترونیکی
10 ماه پیش
0.53 مگابایت
نوع : pdf
بازدید : 2393
منتشرکننده : رستگاری
|
دستورالعمل عیب یابی خطای multiplicative mixture دنا و سورن
10 ماه پیش
0.49 مگابایت
نوع : pdf
بازدید : 1214
منتشرکننده : رستگاری
|
جزوه ایمنی تعمیرات در خودروهای برقی مدیران خودرو
10 ماه پیش
2.81 مگابایت
نوع : pdf
بازدید : 1108
منتشرکننده : رستگاری
|
استفاده از کامپوزیت در خودرو ها
10 ماه پیش
0.47 مگابایت
نوع : pdf
بازدید : 1075
منتشرکننده : حارث
|
تعویض ledهای ۲۰۶
|
جزوه کاراموزی موتور سایپا
|
جعبه فیوز های ایرانخودرو و سایپا
|
مالتی پلکس سمند و سورن
|
دور موتور در دور آرام بالاست
|
معرفی موتور پراید b3
|
دلایل داغ شدن موتور
|
اصلاحات فنی موتور
|
عیب یابی با دود اگزوز
|
دیکشنری اصلاحات خودرو
|
سیستم ترمز ESP 2
|
معرفی ترمز های هوشمندesp
|
کتاب راهنمای تعمیرات و سرویس ترمز absایرانخودرو
|
جدول روغن گیربکس های هیوندایی
|
انواع سیستم ترمز پیشرفته الکترونیکی امداد خودرو
|
تفاوت سوپر شارژ و توربوشارژر
|
جدول عیب یابی ترمز abs
|
سرویس عیب یابی ترمز پراید
|
جزوه آشنایی با توری فرمانهای پرقدرت هیدرولیکی و برقی
|
جزوه دوره تعمیرات ایسیو فرشاد حسین پور
|
دانستنی های تعویض روغن موتور خودرو
|
کنترل الکترونیکی سوپاپها
|
پین اوت ایسیو چادگان ایدو
|
تعریف کلید تمامی خودرو های هیوندا کیا
|
اصلاح کیلومتر از طریق پروتوکل mbus
|
پین اوت bsiدر خودروc5
|
نقشه فارسی سیستم کنترل پایداری esp
|
جزوه دوره تخصصی برق و انژکتور مگان
|
پین اوت ایسیو دلفی
|
نقشه کیلس تارا
|
ریست کردن دستی چراغ چک انواع خودرو۲
|
کتاب سنسور ها در خودرو های سواری
|
تست سلامت قطعات الکترونیکی
|
بررسی و آنالیز پارامترهاي ارائه شده توسط دستگاه پنج گاز و معاینه فنی
|
راهنمای کار با وینولز
|
ریست کردن دستی چراغ چک انواع خودرو
|
پین اوت ایسیو بوش ۷.۹.۷
|
راهنمای تعمیرات و عیب یابی بدنه پژو 405 ، پارس پژو RD و روآ
11 ماه پیش
27.21 مگابایت
نوع : pdf
بازدید : 1330
منتشرکننده : امیررضا فرجی
|
ریمپ ایسیو با دیاگ
|
اتصالات مختلف در ایسیو های ساژم و زیمنس
|
جدول دانلود ایسیوها
|
راهنمای دانلود ایسیوها
|
کتاب سنسور های حرارتی
|
اموزش تنطیم چراغ های جلو
|
عیب یابی تخصصی خودروی دوگانه سوز فابریک با ایسیو ساکس ۵۰۰
|
برق انژکتور مالتی پلکس هیوندا کیا
|
تعمیر موتور هیوندا کیا
|
گیربکس اتوماتیک ۴ و۵ سرعته hiviceهیوندا کیا
|
گیربکس ۶ سرعته هیوندا کیا
|
بالا آمدن ایسیو و عیب یابی ان
|
سیستم های تنظیم ارتفاع هیوندا کیا
|
سیستم اسمارت کی هیوندا کیا
|
ایسیو هایی که باید دامپ مشابه بزنیم
|
چک لیست عیب یابی سیستم انژکتور fai
|
نوسان دور موتور آرام پراید
|
بی کد کردن انواع ایسیو
|
جزوه شناخت سیستم سوخت رسانی سی ان جی cng
|
اموزش کار با ایسیو کیت
|
جزوه ریمپ کارپلاس
|
کتاب تعمیر ایسیو جدید
|
جزوه ریمپ j35
|
جزوه تعمیر ایسیوj34
|
جزوه تعمیر ایسیو والئوvaleo
|
جزوه تعمیر ایسیو دیجی خودرو
|
جداول ایسیو ها
|
کتاب جامع تعمیر ایسیو
|
کتاب طراحی اسانسور
11 ماه پیش
10.2 مگابایت
نوع : pdf
بازدید : 891
منتشرکننده : Najvavgg
|
محل ذخیره کیلومتر در انواع خودرو
|
کلیات شبکه مالتی پلکس
|
تعمیرات جامع پکیج شوفاژگازی علی اکبر نوروزی
|
اموزش جامع سیستم مالتی پلکس
11 ماه پیش
9.11 مگابایت
نوع : pdf
بازدید : 1538
منتشرکننده : Davr
|
ایکس۲۲
11 ماه پیش
5.46 مگابایت
نوع : pdf
بازدید : 898
منتشرکننده : اشکان
|
کارگاه ماشین ابزار
11 ماه پیش
13.84 مگابایت
نوع : pdf
بازدید : 813
منتشرکننده : فنی حرفه ای
|
جزوه ابزار شناسی
11 ماه پیش
26.38 مگابایت
نوع : pdf
بازدید : 1575
منتشرکننده : فنی حرفه ای
|
کتاب اموزش کاربردی میکرو کنترلر های avrخلج منفرد
11 ماه پیش
37.83 مگابایت
نوع : pdf
بازدید : 1068
منتشرکننده : فنی حرفه ای
|
تبرید و اصول و روش ها
11 ماه پیش
18.31 مگابایت
نوع : pdf
بازدید : 830
منتشرکننده : فنی حرفه ای
|
راهنمای جامع نقشه برق خودرو نگار خودرو
11 ماه پیش
36.05 مگابایت
نوع : pdf
بازدید : 1639
منتشرکننده : فنی حرفه ای
|
اموزش تخصص گیربکس al4صمد فلاح گنجه
11 ماه پیش
66.68 مگابایت
نوع : pdf
بازدید : 948
منتشرکننده : فنی حرفه ای
|
جزوه یادگیری سریع سیستم سوخت رسانی cng
11 ماه پیش
15.21 مگابایت
نوع : pdf
بازدید : 1228
منتشرکننده : فنی حرفه ای
|
جزوه تنظیم موتور تکمیل
11 ماه پیش
1.07 مگابایت
نوع : pdf
بازدید : 2214
منتشرکننده : فنی حرفه ای
|
جزوه تنظیم موتور موتور ازما
11 ماه پیش
81.56 مگابایت
نوع : pdf
بازدید : 1259
منتشرکننده : فنی حرفه ای
|
جزوه اتومکانیک خودروهای بنزینی درجه ۲ مومنی
11 ماه پیش
2.06 مگابایت
نوع : pdf
بازدید : 990
منتشرکننده : فنی حرفه ای
|
کتاب قدم صفر هیدرولیک
11 ماه پیش
32.94 مگابایت
نوع : pdf
بازدید : 948
منتشرکننده : فنی حرفه ای
|
جزوه دوره مربی گری بین المللی جوش
11 ماه پیش
12.27 مگابایت
نوع : pdf
بازدید : 714
منتشرکننده : فنی حرفه ای
|
جوشکاری قوس الکتریکی فنی حرفه ای
11 ماه پیش
9.23 مگابایت
نوع : pdf
بازدید : 850
منتشرکننده : فنی حرفه ای
|
جزوه کارگاه جوشکاری فنی حرفه ای
11 ماه پیش
2.41 مگابایت
نوع : pdf
بازدید : 1572
منتشرکننده : فنی حرفه ای
|
کتاب کارگاه جوشکاری کاری و ورق کاری مسعود فکوری
11 ماه پیش
3.51 مگابایت
نوع : pdf
بازدید : 881
منتشرکننده : فنی حرفه ای
|
نقشه پایه های رله دوبل سمندef7 موتور ملی دوگانه بدون مالتی بلکس بوش معمولی
11 ماه پیش
11.7 مگابایت
نوع : pdf
بازدید : 3188
منتشرکننده : امیر حقگو
|
جزوه کلاسی برق خودرو درجه ۲
11 ماه پیش
7.13 مگابایت
نوع : pdf
بازدید : 1403
منتشرکننده : فنی حرفه ای
|
سوالات تعمیر خودرو های بنزینی درجه ۲ فنی حرفه ای
11 ماه پیش
0.77 مگابایت
نوع : pdf
بازدید : 885
منتشرکننده : فنی حرفه ای
|
نمونه سوالات آزمون آنلاین تعمیر خودرو بنزینی درجه ۲ فنی حرفه ای
11 ماه پیش
1.83 مگابایت
نوع : pdf
بازدید : 866
منتشرکننده : فنی حرفه ای
|
جزوه اموزشی ایساکو سیستم تهویه مطبوع
11 ماه پیش
11.31 مگابایت
نوع : pdf
بازدید : 1317
منتشرکننده : محمد امین عرب
|
راهنمای سوخت رسانی و جرقه آریسان 1
11 ماه پیش
1.58 مگابایت
نوع : pdf
بازدید : 1409
منتشرکننده : محمد امین عرب
|
آشنایی با موتور چهار زمانه و سیستم های خودرو
11 ماه پیش
10.21 مگابایت
نوع : pdf
بازدید : 972
منتشرکننده : فنی حرفه ای
|
منبع اموزش دوره تعمیرکار برق خودرو درجه ۲
11 ماه پیش
31.9 مگابایت
نوع : pdf
بازدید : 1307
منتشرکننده : فنی حرفه ای
|
ایرادات شایع خودرو جک
11 ماه پیش
2.78 مگابایت
نوع : pdf
بازدید : 1042
منتشرکننده : اشکان
|
جزوه سیمولینک سامانی
11 ماه پیش
1.76 مگابایت
نوع : pdf
بازدید : 921
منتشرکننده : فنی حرفه ای
|
سوالات برق خودرو درجه ۲ با جواب(قبولی تضمینی )
11 ماه پیش
0.5 مگابایت
نوع : pdf
بازدید : 1214
منتشرکننده : فنی حرفه ای
|
سوالات آزمون مکانیک خودرو بنزینی فنی حرفه ای با جواب(قبولی تضمینی )
11 ماه پیش
3.75 مگابایت
نوع : pdf
بازدید : 1536
منتشرکننده : فنی حرفه ای
|
جزوه سوخت رسانی گازی بهزاد سامانی
11 ماه پیش
4.39 مگابایت
نوع : pdf
بازدید : 885
منتشرکننده : فنی حرفه ای
|
جزوه سیستم های هواپیما
11 ماه پیش
3.4 مگابایت
نوع : pdf
بازدید : 1350
منتشرکننده : فنی حرفه ای
|
جزوه مکانیک خودرو درجه 2 تعمیر کار خودرو های بنزینی
11 ماه پیش
25.45 مگابایت
نوع : pdf
بازدید : 1287
منتشرکننده : فنی حرفه ای
|
جزوه کاربرد تکنلوژی پیشرفته در خودرو بهزاد سامانی
1 سال پیش
3.16 مگابایت
نوع : pdf
بازدید : 984
منتشرکننده : فنی حرفه ای
|
جزوه راهنمای فنی موتور و گیربکس خودرو تارا دستی (TU5پلاس و BE4-تارا)
1 سال پیش
6.51 مگابایت
نوع : pdf
بازدید : 2654
منتشرکننده : رستگاری
|
ریمپ ایسیو والئو با tnmوwinols
1 سال پیش
3.17 مگابایت
نوع : pdf
بازدید : 1823
منتشرکننده : اشکان
|
جزوه عیب یابی نگارخودرو
1 سال پیش
0.24 مگابایت
نوع : pdf
بازدید : 2064
منتشرکننده : رستگاری
|
پایداری خودرو
1 سال پیش
3.77 مگابایت
نوع : pdf
بازدید : 1373
منتشرکننده : حارث
|
سنسور مپ
1 سال پیش
1.64 مگابایت
نوع : pdf
بازدید : 2060
منتشرکننده : حارث
|
پین اوت سوکت ایسیو ساژم و والیو s2000
1 سال پیش
0.07 مگابایت
نوع : pdf
بازدید : 21042
منتشرکننده : یحیی منصورزاده
|
راهنمای تعمیرات موتور جدید xu7p پارس و سورن
1 سال پیش
7.66 مگابایت
نوع : pdf
بازدید : 12410
منتشرکننده : وحید
|
پین اوت سوکت ایسیو و سنسورهای وانت پیکاپ ژاپنی
1 سال پیش
0.4 مگابایت
نوع : pdf
بازدید : 3141
منتشرکننده : یحیی منصورزاده
|
پین اوت BM34 پژو 206 فرانسوی
1 سال پیش
0.12 مگابایت
نوع : pdf
بازدید : 8976
منتشرکننده : یحیی منصورزاده
|
Spark plug repair information
1 سال پیش
3.35 مگابایت
نوع : pdf
بازدید : 1494
منتشرکننده : SImon
|
پین اوت CEC پژو پارس
1 سال پیش
0.31 مگابایت
نوع : pdf
بازدید : 6444
منتشرکننده : یحیی منصورزاده
|
نقشه سیم کشی هوندا 125
1 سال پیش
6.76 مگابایت
نوع : pdf
بازدید : 33857
منتشرکننده : ناصر خاک زاد
|
پین اوت کیلومتر پراید بدون شبکه
1 سال پیش
0.12 مگابایت
نوع : pdf
بازدید : 18132
منتشرکننده : یحیی منصورزاده
|
آموزش تعویض فلت دسته چراغ 206 فرانسوی
1 سال پیش
0.69 مگابایت
نوع : pdf
بازدید : 6310
منتشرکننده : یحیی منصورزاده
|
آشنایی با قطعات و سیستم مدیریت موتور BOSCH ME17.9.71_TU5
2 سال پیش
2.72 مگابایت
نوع : pdf
بازدید : 3013
منتشرکننده : صابر قپانوری
|
پین اوت سوکتهای bcm برند کروز نصب شده روی خودردهای ایرانخودرو
2 سال پیش
0.29 مگابایت
نوع : pdf
بازدید : 14282
منتشرکننده : یحیی منصورزاده
|
پین اوت فارسی ایسیو و سنسورهای دوو ریسر ،اسپیرو وسیلو
2 سال پیش
0.36 مگابایت
نوع : pdf
بازدید : 3472
منتشرکننده : یحیی منصورزاده
|
پین اوت صفحه کیلومتر L90
2 سال پیش
0.31 مگابایت
نوع : pdf
بازدید : 5875
منتشرکننده : یحیی منصورزاده
|
ترجمه لیست پیوست قطعات،تجهیزات و دسته سیم های 206 مالتی پلکس فول ماکس فرانسه
2 سال پیش
2.12 مگابایت
نوع : pdf
بازدید : 2917
منتشرکننده : یاسین داداش پور
|
ترجمه لیست پیوست قطعات،تجهیزات و کانکتور های رنو ال نود(L90)
2 سال پیش
0.35 مگابایت
نوع : pdf
بازدید : 2458
منتشرکننده : یاسین داداش پور
|
ترجمه لیست پیوست قطعات،تجهیزات و کانکتور های رنو ال نود(L90)
2 سال پیش
0.24 مگابایت
نوع : pdf
بازدید : 3064
منتشرکننده : یاسین داداش پور
|
جزوه آموزشي سيستم تعليقات خودروي كپچر
2 سال پیش
2.88 مگابایت
نوع : pdf
بازدید : 2099
منتشرکننده : صابر قپانوری
|
راهنماي آموزش كپچر سطح B
2 سال پیش
1.71 مگابایت
نوع : pdf
بازدید : 2177
منتشرکننده : صابر قپانوری
|
راهنمای توربو شارژ خودرو کپچر
2 سال پیش
0.64 مگابایت
نوع : pdf
بازدید : 2126
منتشرکننده : صابر قپانوری
|
آماده سازی و محدوده رنگ سنسور پارک عقب
2 سال پیش
0.24 مگابایت
نوع : pdf
بازدید : 1948
منتشرکننده : صابر قپانوری
|
مشخصات روغن گیربکس اتوماتیک رنو کپچر
2 سال پیش
0.19 مگابایت
نوع : pdf
بازدید : 2013
منتشرکننده : صابر قپانوری
|
هواگیری سیستم خنک کننده کپچر
2 سال پیش
0.36 مگابایت
نوع : pdf
بازدید : 3359
منتشرکننده : صابر قپانوری
|
پین اوت صفحه کیلومتر کروز دو فیش نصب شده روی پژو 405و پیکان
2 سال پیش
0.45 مگابایت
نوع : pdf
بازدید : 26784
منتشرکننده : یحیی منصورزاده
|
راهنمای تعویض فلت lcd ساعت 206
2 سال پیش
1.43 مگابایت
نوع : pdf
بازدید : 9081
منتشرکننده : یحیی منصورزاده
|
کیلومترهای مورد استفاده در پراید ازآغاز تا کنون
2 سال پیش
2.26 مگابایت
نوع : pdf
بازدید : 5945
منتشرکننده : یحیی منصورزاده
|
راهنمای فیوزها و رله های تارا اتوماتیک
2 سال پیش
0.54 مگابایت
نوع : pdf
بازدید : 9268
منتشرکننده : ابولفضل رضایی
|
راهنمای مدارهای الکتریکی ساینا S
2 سال پیش
24.84 مگابایت
نوع : pdf
بازدید : 33849
منتشرکننده : ابولفضل رضایی
|
راهنمای تعمیرات و سرویس مدارهای الکتریکی سایپا شاهین
2 سال پیش
20.44 مگابایت
نوع : pdf
بازدید : 15211
منتشرکننده : ابولفضل رضایی
|
نقشه و دیاگرام برق / الکتریکال جیلی امگرند ، دنده / cvt
2 سال پیش
9.71 مگابایت
نوع : pdf
بازدید : 7269
منتشرکننده : سیدحسین سیدی
|
تکنولوژی رانندگی با سیم (x_by_wire)
2 سال پیش
0.78 مگابایت
نوع : pdf
بازدید : 2773
منتشرکننده : احمد تقی بیگی
|
نقشه های الکتریکی خودروی تارا
2 سال پیش
18.19 مگابایت
نوع : pdf
بازدید : 20662
منتشرکننده : نادر رهام
|
مشخصات خودروی لئو امایکس۸ (LEO MX8)
3 سال پیش
0.88 مگابایت
نوع : pdf
بازدید : 2462
منتشرکننده : علی حسینزاده
|
دفترچه راهنمای خودروی لاماری ایما (Lamari Eama Manual Book)
3 سال پیش
37.42 مگابایت
نوع : pdf
بازدید : 43015
منتشرکننده : علی حسینزاده
|
کاتالوگ خودروی دایون وای ۵ (Dayun Y5)
3 سال پیش
45.84 مگابایت
نوع : pdf
بازدید : 3554
منتشرکننده : علی حسینزاده
|
دفترچه راهنمای خودروی دایون وای ۵ (Dayun Y5)
3 سال پیش
30.32 مگابایت
نوع : pdf
بازدید : 8470
منتشرکننده : علی حسینزاده
|
کاتالوگ خودروی لاماری ایما (LAMARI EAMA)
3 سال پیش
5.84 مگابایت
نوع : pdf
بازدید : 10766
منتشرکننده : علی حسینزاده
|
پین اوت ایسیو و سنسورهای وانت مزدا ژاپنی
3 سال پیش
0.13 مگابایت
نوع : pdf
بازدید : 19138
منتشرکننده : یحیی منصورزاده
|
جزوه تیگو8پرو
|
کاتالوگ smd
3 سال پیش
1.93 مگابایت
نوع : pdf
بازدید : 3393
منتشرکننده : عنایت قرایی
|
بوق ۲۰۶
3 سال پیش
0.47 مگابایت
نوع : pdf
بازدید : 3665
منتشرکننده : عنایت قرایی
|
عیوب شایع x33
3 سال پیش
0.28 مگابایت
نوع : pdf
بازدید : 3899
منتشرکننده : عنایت قرایی
|
بازکردن موتور ۲۰۶ تیپ ۳
3 سال پیش
36.85 مگابایت
نوع : pdf
بازدید : 3465
منتشرکننده : 09352145514
|
موتور + hp پراید
3 سال پیش
0.31 مگابایت
نوع : pdf
بازدید : 9603
منتشرکننده : Ali m
|
مولتی پلکس
3 سال پیش
8.89 مگابایت
نوع : pdf
بازدید : 6337
منتشرکننده : عنایت قرایی
|
کاتالوگ رسمی جک S5 جدید (نیوفیس)
3 سال پیش
0.54 مگابایت
نوع : pdf
بازدید : 20259
منتشرکننده : علی حسینزاده
|
سنسور دمای آب موتور در اچ سی کراس
3 سال پیش
0.3 مگابایت
نوع : pdf
بازدید : 4081
منتشرکننده : چراغ چک
|
دفترچه راهنمای رنو فلوئنس
3 سال پیش
7.23 مگابایت
نوع : pdf
بازدید : 11192
منتشرکننده : علی حسینزاده
|
دفترچه راهنمای رنو داستر
3 سال پیش
21.83 مگابایت
نوع : pdf
بازدید : 13969
منتشرکننده : علی حسینزاده
|
کاتالوگ رنو داستر
3 سال پیش
0.33 مگابایت
نوع : pdf
بازدید : 4193
منتشرکننده : علی حسینزاده
|
دفترچه راهنما و گارانتی خودروی KMC K7 کرمان موتور
3 سال پیش
10.78 مگابایت
نوع : pdf
بازدید : 17797
منتشرکننده : علی حسینزاده
|
کاتالوگ خودروی KMC K7 کرمان موتور
3 سال پیش
3.47 مگابایت
نوع : pdf
بازدید : 7971
منتشرکننده : علی حسینزاده
|
دفترچه راهنمای تعمیرگاهی رنو داستر
3 سال پیش
26.17 مگابایت
نوع : pdf
بازدید : 4854
منتشرکننده : علی حسینزاده
|
کتاب جامع تعمیر موتور هیوندا و کیا
3 سال پیش
5.4 مگابایت
نوع : pdf
بازدید : 20042
منتشرکننده : بهنام یلمه
|
یکسره کردن رله دوبل
4 سال پیش
0.05 مگابایت
نوع : pdf
بازدید : 25137
منتشرکننده : نرم افزار iMAP
|
معرفی ترانسپوندر محصولات پارس خودرو
4 سال پیش
0.06 مگابایت
نوع : pdf
بازدید : 4474
منتشرکننده : نرم افزار iMAP
|
آموزش تبدیل پمپ بنزین بیرون باکی به پمپ بنزین داخل باکی
4 سال پیش
0.78 مگابایت
نوع : pdf
بازدید : 26905
منتشرکننده : کارگیک
|
راهنمای برق و الکترونیک آریزو۵
4 سال پیش
7.39 مگابایت
نوع : pdf
بازدید : 12526
منتشرکننده : کارگیک
|
راهنمای برق و الکترونیک MVM 550
4 سال پیش
6.47 مگابایت
نوع : pdf
بازدید : 24267
منتشرکننده : کارگیک
|
راهنمای برق و الکترونیک MVM 530
4 سال پیش
6.61 مگابایت
نوع : pdf
بازدید : 6181
منتشرکننده : کارگیک
|
راهنمای تعمیرات سیستم فرمان خودرو دنا
4 سال پیش
5.11 مگابایت
نوع : pdf
بازدید : 5580
منتشرکننده : کارگیک
|
راهنمای تعمیرات موتور سوزوکی کیزاشی
4 سال پیش
12.53 مگابایت
نوع : pdf
بازدید : 3947
منتشرکننده : کارگیک
|
Delivering Advanced Unmanned Autonomous Systems and Artificial Intelligence for Naval Superiority
4 سال پیش
4.66 مگابایت
نوع : pdf
بازدید : 3271
منتشرکننده : کارگیک
|
A Security Analysis of Garage Door Remotes and the Danger of DOR Attacks
4 سال پیش
3.24 مگابایت
نوع : pdf
بازدید : 2973
منتشرکننده : کارگیک
|
طراحی سامانه های پیرانش موشکی سوخت جامد
4 سال پیش
6.46 مگابایت
نوع : pdf
بازدید : 3630
منتشرکننده : کارگیک
|
آشنایی با موتورهای هواپیما (پیستونی، جت و ملخ)
4 سال پیش
53.17 مگابایت
نوع : pdf
بازدید : 5416
منتشرکننده : کارگیک
|
جزوه آموزشی موتور دیزل
4 سال پیش
11.42 مگابایت
نوع : pdf
بازدید : 20592
منتشرکننده : کارگیک
|
آشنایی با هواپیماهای مدل
4 سال پیش
5.84 مگابایت
نوع : pdf
بازدید : 3536
منتشرکننده : کارگیک
|
ISO/SAE 21434 : Setting the Standard for Connected Cars’ Cybersecurity
4 سال پیش
4.33 مگابایت
نوع : pdf
بازدید : 3000
منتشرکننده : کارگیک
|
Driving Security Into Connected Cars: Threat Model and Recommendations
4 سال پیش
2.01 مگابایت
نوع : pdf
بازدید : 3078
منتشرکننده : کارگیک
|
راهنمای تعمیرات و عیب یابی بدنه و تزیینات هایما
4 سال پیش
9.85 مگابایت
نوع : pdf
بازدید : 3725
منتشرکننده : کارگیک
|
راهنمای پارامترهای فنی خودرو هایما S7 توربوشارژ
4 سال پیش
1.64 مگابایت
نوع : pdf
بازدید : 4509
منتشرکننده : کارگیک
|
جزوه آموزشی و نقشه های برق MVM110s
4 سال پیش
6.95 مگابایت
نوع : pdf
بازدید : 12633
منتشرکننده : کارگیک
|
اصول و مفاهیم و رویکردهای یادگیری عمیق
4 سال پیش
9.3 مگابایت
نوع : pdf
بازدید : 3883
منتشرکننده : کارگیک
|
Industrial Cybersecurity
4 سال پیش
45.83 مگابایت
نوع : pdf
بازدید : 3019
منتشرکننده : کارگیک
|
آشنایی با کاربرد و مشخصات روانکارها (هپکو)
4 سال پیش
3.72 مگابایت
نوع : pdf
بازدید : 3594
منتشرکننده : کارگیک
|
راهنمای انتخاب و مصرف سیالات خنک کننده (ضدیخ ، ضدجوش و ضدزنگ) خودرو
4 سال پیش
1.13 مگابایت
نوع : pdf
بازدید : 3808
منتشرکننده : کارگیک
|
تشریح مدارها و راهنمای کاربردی غلتک HC100C هپکو
4 سال پیش
2.4 مگابایت
نوع : pdf
بازدید : 7453
منتشرکننده : کارگیک
|
نقشه مدار ACU سمند
4 سال پیش
1.51 مگابایت
نوع : pdf
بازدید : 9281
منتشرکننده : کارگیک
|
کتاب 1800 Mechanical Movements: Devices and Appliances
4 سال پیش
92.22 مگابایت
نوع : pdf
بازدید : 3911
منتشرکننده : کارگیک
|
دفترچه راهنمای تویوتا CH-R هیبرید
4 سال پیش
17.91 مگابایت
نوع : pdf
بازدید : 5489
منتشرکننده : کارگیک
|
جزوه آموزشی سیستم برق چری تیگو۷
4 سال پیش
7.37 مگابایت
نوع : pdf
بازدید : 7121
منتشرکننده : کارگیک
|
راهنمای عیب یابی و تنظیم سیستم هیدرولیک لودر کاترپیلار CAT988b
4 سال پیش
7.6 مگابایت
نوع : pdf
بازدید : 6274
منتشرکننده : کارگیک
|
راهنمای دانلود ایسیو
4 سال پیش
1.4 مگابایت
نوع : pdf
بازدید : 6013
منتشرکننده : کارگیک
|
کتاب تکنولوژی پهپادها (unmanned aircraft system (UAS))
4 سال پیش
7.19 مگابایت
نوع : pdf
بازدید : 3984
منتشرکننده : کارگیک
|
راهنمای آموزشی سیستم سوخت رسانی جیلی GC6
4 سال پیش
5.09 مگابایت
نوع : pdf
بازدید : 4737
منتشرکننده : کارگیک
|
جزوه آموزشی سیستم مدیریت موتور هاوال
4 سال پیش
4.81 مگابایت
نوع : pdf
بازدید : 3196
منتشرکننده : کارگیک
|
راهنمای سیستم های الکتریکی MVM X33
4 سال پیش
9.61 مگابایت
نوع : pdf
بازدید : 24538
منتشرکننده : کارگیک
|
جزوه آموزشی سیستم های MVM X22
4 سال پیش
8.27 مگابایت
نوع : pdf
بازدید : 49973
منتشرکننده : کارگیک
|
راهنمای تعمیرات بدنه خودرو دنا
4 سال پیش
30.51 مگابایت
نوع : pdf
بازدید : 4328
منتشرکننده : کارگیک
|
راهنمای پوشش داخلی و تودوزی تندر۹۰
4 سال پیش
5.15 مگابایت
نوع : pdf
بازدید : 4031
منتشرکننده : کارگیک
|
نکات آزمون شهری و آیین نامه رانندگی (۲از۲)
4 سال پیش
0.53 مگابایت
نوع : pdf
بازدید : 4155
منتشرکننده : کارگیک
|
نکات آزمون شهری و آیین نامه رانندگی (۱از۲)
4 سال پیش
0.4 مگابایت
نوع : pdf
بازدید : 4134
منتشرکننده : کارگیک
|
نمونه سئوالات تشریحی آزمون آیین نامه رانندگی
4 سال پیش
0.57 مگابایت
نوع : pdf
بازدید : 3500
منتشرکننده : کارگیک
|
نمونه سئوالات جامع آزمون آیین نامه رانندگی (۶۶۳سئوال)
4 سال پیش
5.31 مگابایت
نوع : pdf
بازدید : 4161
منتشرکننده : کارگیک
|
نمونه سئوالات آزمون آیین نامه رانندگی (240سئوال)
4 سال پیش
2.25 مگابایت
نوع : pdf
بازدید : 3914
منتشرکننده : کارگیک
|
نمونه سئوالات آزمون آیین نامه رانندگی (۲۹از29)
4 سال پیش
0.82 مگابایت
نوع : pdf
بازدید : 3714
منتشرکننده : کارگیک
|
نمونه سئوالات آزمون آیین نامه رانندگی (۲۸از29)
4 سال پیش
0.8 مگابایت
نوع : pdf
بازدید : 3068
منتشرکننده : کارگیک
|
نمونه سئوالات آزمون آیین نامه رانندگی (۲۷از29)
4 سال پیش
1.04 مگابایت
نوع : pdf
بازدید : 3248
منتشرکننده : کارگیک
|
نمونه سئوالات آزمون آیین نامه رانندگی (۲۶از29)
4 سال پیش
0.86 مگابایت
نوع : pdf
بازدید : 3176
منتشرکننده : کارگیک
|
نمونه سئوالات آزمون آیین نامه رانندگی (۲۵از29)
4 سال پیش
0.54 مگابایت
نوع : pdf
بازدید : 3009
منتشرکننده : کارگیک
|
نمونه سئوالات آزمون آیین نامه رانندگی (۲۴از29)
4 سال پیش
0.75 مگابایت
نوع : pdf
بازدید : 3465
منتشرکننده : کارگیک
|
نمونه سئوالات آزمون آیین نامه رانندگی (۲۳از29)
4 سال پیش
0.96 مگابایت
نوع : pdf
بازدید : 3091
منتشرکننده : کارگیک
|
نمونه سئوالات آزمون آیین نامه رانندگی (22از29)
4 سال پیش
0.85 مگابایت
نوع : pdf
بازدید : 3000
منتشرکننده : کارگیک
|
نمونه سئوالات آزمون آیین نامه رانندگی (۲۱از29)
4 سال پیش
0.76 مگابایت
نوع : pdf
بازدید : 3222
منتشرکننده : کارگیک
|
نمونه سئوالات آزمون آیین نامه رانندگی (۲۰از29)
4 سال پیش
1.1 مگابایت
نوع : pdf
بازدید : 3366
منتشرکننده : کارگیک
|
نمونه سئوالات آزمون آیین نامه رانندگی (۱۹از29)
4 سال پیش
1.11 مگابایت
نوع : pdf
بازدید : 2823
منتشرکننده : کارگیک
|
نمونه سئوالات آزمون آیین نامه رانندگی (۱۸از29)
4 سال پیش
1.17 مگابایت
نوع : pdf
بازدید : 3227
منتشرکننده : کارگیک
|
نمونه سئوالات آزمون آیین نامه رانندگی (۱۷از29)
4 سال پیش
0.96 مگابایت
نوع : pdf
بازدید : 3216
منتشرکننده : کارگیک
|
نمونه سئوالات آزمون آیین نامه رانندگی (۱۶از29)
4 سال پیش
0.92 مگابایت
نوع : pdf
بازدید : 3227
منتشرکننده : کارگیک
|
نمونه سئوالات آزمون آیین نامه رانندگی (۱۵از29)
4 سال پیش
1.08 مگابایت
نوع : pdf
بازدید : 3287
منتشرکننده : کارگیک
|
نمونه سئوالات آزمون آیین نامه رانندگی (۱۴از29)
4 سال پیش
1.2 مگابایت
نوع : pdf
بازدید : 3387
منتشرکننده : کارگیک
|
نمونه سئوالات آزمون آیین نامه رانندگی (۱۳از29)
4 سال پیش
1.14 مگابایت
نوع : pdf
بازدید : 3160
منتشرکننده : کارگیک
|
نمونه سئوالات آزمون آیین نامه رانندگی (12از29)
4 سال پیش
1.06 مگابایت
نوع : pdf
بازدید : 3087
منتشرکننده : کارگیک
|
نمونه سئوالات آزمون آیین نامه رانندگی (۱۱از29)
4 سال پیش
0.94 مگابایت
نوع : pdf
بازدید : 3702
منتشرکننده : کارگیک
|
نمونه سئوالات آزمون آیین نامه رانندگی (۱۰از29)
4 سال پیش
0.3 مگابایت
نوع : pdf
بازدید : 3191
منتشرکننده : کارگیک
|
نمونه سئوالات آزمون آیین نامه رانندگی (۹از29)
4 سال پیش
0.49 مگابایت
نوع : pdf
بازدید : 3435
منتشرکننده : کارگیک
|
نمونه سئوالات آزمون آیین نامه رانندگی (۸از29)
4 سال پیش
0.43 مگابایت
نوع : pdf
بازدید : 3293
منتشرکننده : کارگیک
|
نمونه سئوالات آزمون آیین نامه رانندگی (۷از29)
4 سال پیش
0.35 مگابایت
نوع : pdf
بازدید : 3335
منتشرکننده : کارگیک
|
نمونه سئوالات آزمون آیین نامه رانندگی (۶از29)
4 سال پیش
0.35 مگابایت
نوع : pdf
بازدید : 3134
منتشرکننده : کارگیک
|
نمونه سئوالات آزمون آیین نامه رانندگی (5از29)
4 سال پیش
0.36 مگابایت
نوع : pdf
بازدید : 3201
منتشرکننده : کارگیک
|
نمونه سئوالات آزمون آیین نامه رانندگی (۴از29)
4 سال پیش
0.35 مگابایت
نوع : pdf
بازدید : 3155
منتشرکننده : کارگیک
|
نمونه سئوالات آزمون آیین نامه رانندگی (۳از29)
4 سال پیش
0.44 مگابایت
نوع : pdf
بازدید : 3214
منتشرکننده : کارگیک
|
نمونه سئوالات آزمون آیین نامه رانندگی (۲از29)
4 سال پیش
0.47 مگابایت
نوع : pdf
بازدید : 3415
منتشرکننده : کارگیک
|
نمونه سئوالات آزمون آیین نامه رانندگی (1از29)
4 سال پیش
0.41 مگابایت
نوع : pdf
بازدید : 3374
منتشرکننده : کارگیک
|
نقشه ایسیو بوش ۷.۴.۹ موتور EF7
4 سال پیش
1.19 مگابایت
نوع : pdf
بازدید : 14005
منتشرکننده : amir-gorji
|
دفترچه راهنمای سیستم صوتی رنو کپچر
4 سال پیش
4.02 مگابایت
نوع : pdf
بازدید : 3621
منتشرکننده : کارگیک
|
نقشه ها و راهنمای برقی کیا پراید کاربراتور کره ای قدیم
4 سال پیش
10 مگابایت
نوع : pdf
بازدید : 20839
منتشرکننده : کارگیک
|
L90ایسیو
4 سال پیش
0.17 مگابایت
نوع : pdf
بازدید : 3265
منتشرکننده : حسین حیدری
|
کروز کنترل
4 سال پیش
0.37 مگابایت
نوع : pdf
بازدید : 3537
منتشرکننده : حسین حیدری
|
مشخصات فنی گیربکس اتوماتیک DP2 رنو
4 سال پیش
0.71 مگابایت
نوع : pdf
بازدید : 4396
منتشرکننده : علی حسینزاده
|
مشخصات فنی گیربکس دستی JHQ رنو
4 سال پیش
0.65 مگابایت
نوع : pdf
بازدید : 8385
منتشرکننده : علی حسینزاده
|
راهنمای بروزرسانی نرمافزار پخشهای کنوود
4 سال پیش
0.03 مگابایت
نوع : pdf
بازدید : 5174
منتشرکننده : علی حسینزاده
|
دفترچه راهنمای فارسی رنو ساندرو و استپوی
4 سال پیش
1.67 مگابایت
نوع : pdf
بازدید : 38400
منتشرکننده : علی حسینزاده
|
کتاب مجموعه نقشه های خودروهای انژکتوری موتورآزماثمین
4 سال پیش
65.3 مگابایت
نوع : pdf
بازدید : 51506
منتشرکننده : کارگیک
|
نمونه سئوالات آزمون کارشناس فنی ایساکو سال 97 + پاسخنامه
4 سال پیش
1.84 مگابایت
نوع : pdf
بازدید : 4162
منتشرکننده : کارگیک
|
نمونه سئوالات آزمون کارشناس فنی ایساکو سال 96 + پاسخنامه
4 سال پیش
2.87 مگابایت
نوع : pdf
بازدید : 3156
منتشرکننده : کارگیک
|
نمونه سئوالات آزمون کارشناس فنی ایساکو سال 95 + پاسخنامه (دفترچه 2)
4 سال پیش
1.17 مگابایت
نوع : pdf
بازدید : 2910
منتشرکننده : کارگیک
|
نمونه سئوالات آزمون کارشناس فنی ایساکو سال 95 + پاسخنامه (دفترچه 1)
4 سال پیش
1.4 مگابایت
نوع : pdf
بازدید : 3423
منتشرکننده : کارگیک
|
نمونه سئوالات آزمون کارشناس فنی ایساکو سال 94 + پاسخنامه
4 سال پیش
5.36 مگابایت
نوع : pdf
بازدید : 3033
منتشرکننده : کارگیک
|
نمونه سئوالات آزمون کارشناس فنی ایساکو سال 93 + پاسخنامه
4 سال پیش
4.79 مگابایت
نوع : pdf
بازدید : 3167
منتشرکننده : کارگیک
|
نمونه سئوالات آزمون کارشناس فنی (برق و مکانیک) ایساکو + پاسخ صحیح
4 سال پیش
0.47 مگابایت
نوع : pdf
بازدید : 3400
منتشرکننده : کارگیک
|
نمونه سئوالات آزمون کارشناس فنی ایساکو
4 سال پیش
0.42 مگابایت
نوع : pdf
بازدید : 4038
منتشرکننده : کارگیک
|
نمونه سئوالات آزمون کارشناس فنی ایساکو سال 89 + پاسخنامه
4 سال پیش
2.46 مگابایت
نوع : pdf
بازدید : 4424
منتشرکننده : کارگیک
|
نمونه سئوالات آزمون مهارتی شغل مکانیک ایساکو سال 97 + پاسخنامه
4 سال پیش
1.6 مگابایت
نوع : pdf
بازدید : 3423
منتشرکننده : کارگیک
|
نمونه سئوالات آزمون مهارتی شغل مکانیک ایساکو سال 96 + پاسخنامه
4 سال پیش
2.34 مگابایت
نوع : pdf
بازدید : 3051
منتشرکننده : کارگیک
|
نمونه سئوالات آزمون مهارتی شغل مکانیک ایساکو سال 95 + پاسخنامه
4 سال پیش
1.07 مگابایت
نوع : pdf
بازدید : 2897
منتشرکننده : کارگیک
|
نمونه سئوالات آزمون مهارتی شغل مکانیک ایساکو سال 94 + پاسخنامه
4 سال پیش
4.87 مگابایت
نوع : pdf
بازدید : 2957
منتشرکننده : کارگیک
|
نمونه سئوالات آزمون مهارتی شغل مکانیک ایساکو سال 93 + پاسخنامه
4 سال پیش
1 مگابایت
نوع : pdf
بازدید : 2942
منتشرکننده : کارگیک
|
نمونه سئوالات آزمون سرپرست مکانیک ایساکو سال 92 + پاسخنامه
4 سال پیش
0.2 مگابایت
نوع : pdf
بازدید : 2656
منتشرکننده : کارگیک
|
نمونه سئوالات آزمون سرپرست مکانیک ایساکو
4 سال پیش
0.34 مگابایت
نوع : pdf
بازدید : 2887
منتشرکننده : کارگیک
|
نمونه سئوالات آزمون سرپرست مکانیک ایساکو سال 89 + پاسخنامه
4 سال پیش
2.35 مگابایت
نوع : pdf
بازدید : 2801
منتشرکننده : کارگیک
|
نمونه سئوالات آزمون مهارتی گازسوز کار ایساکو سال 97 + پاسخنامه
4 سال پیش
1.34 مگابایت
نوع : pdf
بازدید : 2963
منتشرکننده : کارگیک
|
نمونه سئوالات آزمون مهارتی گازسوز کار ایساکو سال 96 + پاسخنامه
4 سال پیش
2.33 مگابایت
نوع : pdf
بازدید : 3045
منتشرکننده : کارگیک
|
نمونه سئوالات آزمون مهارتی گازسوز کار ایساکو سال 95 + پاسخنامه
4 سال پیش
0.85 مگابایت
نوع : pdf
بازدید : 2937
منتشرکننده : کارگیک
|
نمونه سئوالات آزمون مهارتی گازسوز کار ایساکو سال 94 + پاسخنامه
4 سال پیش
4.93 مگابایت
نوع : pdf
بازدید : 2706
منتشرکننده : کارگیک
|
نمونه سئوالات آزمون مهارتی گازسوز کار ایساکو سال 93 + پاسخنامه
4 سال پیش
0.88 مگابایت
نوع : pdf
بازدید : 2879
منتشرکننده : کارگیک
|
نمونه سئوالات آزمون مهارت سیستم CNG ایساکو + پاسخ صحیح
4 سال پیش
0.12 مگابایت
نوع : pdf
بازدید : 3047
منتشرکننده : کارگیک
|
نمونه سئوالات آزمون مهارت سیستم تعلیقات ایساکو + پاسخ صحیح
4 سال پیش
0.22 مگابایت
نوع : pdf
بازدید : 2890
منتشرکننده : کارگیک
|
نمونه سئوالات آزمون مهارتی جلوبندی کار ایساکو سال 97 + پاسخنامه
4 سال پیش
2.24 مگابایت
نوع : pdf
بازدید : 2742
منتشرکننده : کارگیک
|
نمونه سئوالات آزمون مهارتی سرپرست جلوبندی ایساکو سال 96 + پاسخنامه
4 سال پیش
2.24 مگابایت
نوع : pdf
بازدید : 2803
منتشرکننده : کارگیک
|
نمونه سئوالات آزمون مهارتی جلوبندی کار ایساکو سال 95 + پاسخنامه
4 سال پیش
0.94 مگابایت
نوع : pdf
بازدید : 3266
منتشرکننده : کارگیک
|
نمونه سئوالات آزمون مهارتی شغل تعلیق کار ایساکو سال 94 + پاسخنامه
4 سال پیش
4.9 مگابایت
نوع : pdf
بازدید : 2649
منتشرکننده : کارگیک
|
نمونه سئوالات آزمون مهارتی شغل تعلیق کار ایساکو سال 93
4 سال پیش
0.98 مگابایت
نوع : pdf
بازدید : 2916
منتشرکننده : کارگیک
|
نمونه سئوالات آزمون سراسری تعلیق ، ترمز و فرمان ایساکو
4 سال پیش
0.42 مگابایت
نوع : pdf
بازدید : 3107
منتشرکننده : کارگیک
|
نمونه سئوالات آزمون مهارتی شغل سرپرست جلوبندی کار ایساکو سال 89
4 سال پیش
1.1 مگابایت
نوع : pdf
بازدید : 2718
منتشرکننده : کارگیک
|
نمونه سئوالات آزمون مهارتی شغل تعلیق کار ایساکو
4 سال پیش
0.6 مگابایت
نوع : pdf
بازدید : 2852
منتشرکننده : کارگیک
|
نمونه سئوالات آزمون مهارتی شغل تعلیق کار ایساکو سال 96
4 سال پیش
0.16 مگابایت
نوع : pdf
بازدید : 3237
منتشرکننده : کارگیک
|
نمونه سئوالات آزمون شغل مکانیک ایساکو سال 96
4 سال پیش
0.19 مگابایت
نوع : pdf
بازدید : 3230
منتشرکننده : کارگیک
|
نمونه سئوالات آزمون برقکار ایساکو سال 97
4 سال پیش
1.35 مگابایت
نوع : pdf
بازدید : 3480
منتشرکننده : کارگیک
|
نمونه سئوالات آزمون برقکار ایساکو سال 96
4 سال پیش
2.33 مگابایت
نوع : pdf
بازدید : 3059
منتشرکننده : کارگیک
|
نمونه سئوالات آزمون برقکار ایساکو سال 95
4 سال پیش
0.92 مگابایت
نوع : pdf
بازدید : 2824
منتشرکننده : کارگیک
|
نمونه سئوالات آزمون برقکار ایساکو سال 94
4 سال پیش
5.09 مگابایت
نوع : pdf
بازدید : 3006
منتشرکننده : کارگیک
|
نمونه سئوالات آزمون مهارتی شغل برقکار ایساکو سال 93
4 سال پیش
1.06 مگابایت
نوع : pdf
بازدید : 3047
منتشرکننده : کارگیک
|
نمونه سئوالات آزمون سراسری سرپرست برق نمایندگی های ایران خودرو (ایساکو) سال 92
4 سال پیش
0.23 مگابایت
نوع : pdf
بازدید : 3440
منتشرکننده : کارگیک
|
نمونه سئوالات آزمون برقکار ایساکو سال 90
4 سال پیش
0.19 مگابایت
نوع : pdf
بازدید : 3008
منتشرکننده : کارگیک
|
نمونه سئوالات آزمون سرپرست برق ایساکو سال 89
4 سال پیش
1.1 مگابایت
نوع : pdf
بازدید : 2953
منتشرکننده : کارگیک
|
نمونه سئوالات آزمون برق ایساکو
4 سال پیش
0.6 مگابایت
نوع : pdf
بازدید : 3144
منتشرکننده : کارگیک
|
نمونه سئوالات آزمون مهارتی شغل برقکار ایساکو سال 96
4 سال پیش
0.2 مگابایت
نوع : pdf
بازدید : 3320
منتشرکننده : کارگیک
|
10 دوره آزمون های پایانی اتومکانیک درجه دو سازمان فنی و حرفه ای
4 سال پیش
0.81 مگابایت
نوع : pdf
بازدید : 3387
منتشرکننده : کارگیک
|
نمونه سئوالات آزمون عملی تعمیرکار درجه دو اتومبیل های سواری بنزینی
4 سال پیش
0.14 مگابایت
نوع : pdf
بازدید : 10504
منتشرکننده : کارگیک
|
نمونه سئوالات آزمون اتومکانیک درجه 2 سازمان فنی و حرفه ای (سری 17 از 17)
4 سال پیش
0.32 مگابایت
نوع : pdf
بازدید : 3446
منتشرکننده : کارگیک
|
نمونه سئوالات آزمون اتومکانیک درجه 2 سازمان فنی و حرفه ای (سری 16 از 17)
4 سال پیش
0.34 مگابایت
نوع : pdf
بازدید : 3009
منتشرکننده : کارگیک
|
نمونه سئوالات آزمون اتومکانیک درجه 2 سازمان فنی و حرفه ای (سری 15 از 17)
4 سال پیش
0.36 مگابایت
نوع : pdf
بازدید : 2811
منتشرکننده : کارگیک
|
نمونه سئوالات آزمون اتومکانیک درجه 2 سازمان فنی و حرفه ای (سری 14 از 17)
4 سال پیش
0.13 مگابایت
نوع : pdf
بازدید : 2832
منتشرکننده : کارگیک
|
نمونه سئوالات آزمون اتومکانیک درجه 2 سازمان فنی و حرفه ای (سری 13 از 17)
4 سال پیش
0.4 مگابایت
نوع : pdf
بازدید : 2591
منتشرکننده : کارگیک
|
نمونه سئوالات آزمون اتومکانیک درجه 2 سازمان فنی و حرفه ای (سری 12 از 17)
4 سال پیش
0.35 مگابایت
نوع : pdf
بازدید : 2616
منتشرکننده : کارگیک
|
نمونه سئوالات آزمون اتومکانیک درجه 2 سازمان فنی و حرفه ای (سری 11 از 17)
4 سال پیش
0.19 مگابایت
نوع : pdf
بازدید : 2710
منتشرکننده : کارگیک
|
نمونه سئوالات آزمون اتومکانیک درجه 2 سازمان فنی و حرفه ای (سری 10 از 17)
4 سال پیش
0.19 مگابایت
نوع : pdf
بازدید : 3005
منتشرکننده : کارگیک
|
نمونه سئوالات آزمون اتومکانیک درجه 2 سازمان فنی و حرفه ای (سری 9 از 17)
4 سال پیش
0.18 مگابایت
نوع : pdf
بازدید : 3299
منتشرکننده : کارگیک
|
نمونه سئوالات آزمون اتومکانیک درجه 2 سازمان فنی و حرفه ای (سری 8 از 17)
4 سال پیش
0.14 مگابایت
نوع : pdf
بازدید : 2969
منتشرکننده : کارگیک
|
نمونه سئوالات آزمون اتومکانیک درجه 2 سازمان فنی و حرفه ای (سری 7 از 17)
4 سال پیش
0.15 مگابایت
نوع : pdf
بازدید : 2854
منتشرکننده : کارگیک
|
نمونه سئوالات آزمون اتومکانیک درجه 2 سازمان فنی و حرفه ای (سری 6 از 17)
4 سال پیش
0.15 مگابایت
نوع : pdf
بازدید : 3008
منتشرکننده : کارگیک
|
نمونه سئوالات آزمون اتومکانیک درجه 2 سازمان فنی و حرفه ای (سری 5 از 17)
4 سال پیش
0.26 مگابایت
نوع : pdf
بازدید : 3086
منتشرکننده : کارگیک
|
نمونه سئوالات آزمون اتومکانیک درجه 2 سازمان فنی و حرفه ای (سری 4 از 17)
4 سال پیش
0.15 مگابایت
نوع : pdf
بازدید : 2912
منتشرکننده : کارگیک
|
نمونه سئوالات آزمون اتومکانیک درجه 2 سازمان فنی و حرفه ای (سری 3 از 17)
4 سال پیش
0.17 مگابایت
نوع : pdf
بازدید : 2912
منتشرکننده : کارگیک
|
نمونه سئوالات آزمون اتومکانیک درجه 2 سازمان فنی و حرفه ای (سری 2 از 17)
4 سال پیش
0.18 مگابایت
نوع : pdf
بازدید : 2908
منتشرکننده : کارگیک
|
نمونه سئوالات آزمون اتومکانیک درجه 2 سازمان فنی و حرفه ای (سری 1 از 17)
4 سال پیش
0.15 مگابایت
نوع : pdf
بازدید : 2911
منتشرکننده : کارگیک
|
نمونه سئوالات آزمون تعمیر موتورسیکلت (سری 9 از 9)
4 سال پیش
0.2 مگابایت
نوع : pdf
بازدید : 3103
منتشرکننده : کارگیک
|
نمونه سئوالات آزمون تعمیر موتورسیکلت (سری 8 از 9)
4 سال پیش
0.19 مگابایت
نوع : pdf
بازدید : 3068
منتشرکننده : کارگیک
|
نمونه سئوالات آزمون تعمیر موتورسیکلت (سری 7 از 9)
4 سال پیش
0.68 مگابایت
نوع : pdf
بازدید : 2714
منتشرکننده : کارگیک
|
نمونه سئوالات آزمون تعمیر موتورسیکلت (سری 6 از 9)
4 سال پیش
0.26 مگابایت
نوع : pdf
بازدید : 3368
منتشرکننده : کارگیک
|
نمونه سئوالات آزمون تعمیر موتورسیکلت (سری 5 از 9)
4 سال پیش
0.25 مگابایت
نوع : pdf
بازدید : 2805
منتشرکننده : کارگیک
|
نمونه سئوالات آزمون تعمیر موتورسیکلت (سری 4 از 9)
4 سال پیش
0.25 مگابایت
نوع : pdf
بازدید : 2817
منتشرکننده : کارگیک
|
نمونه سئوالات آزمون تعمیر موتورسیکلت (سری 3 از 9)
4 سال پیش
0.25 مگابایت
نوع : pdf
بازدید : 3258
منتشرکننده : کارگیک
|
نمونه سئوالات آزمون تعمیر موتورسیکلت (سری 2 از 9)
4 سال پیش
0.25 مگابایت
نوع : pdf
بازدید : 2990
منتشرکننده : کارگیک
|
نمونه سئوالات آزمون تعمیر موتورسیکلت (سری 1 از 9)
4 سال پیش
0.14 مگابایت
نوع : pdf
بازدید : 3109
منتشرکننده : کارگیک
|
نمونه سئوالات آزمون سیستم تعلیق خودرو (سری3از3)
4 سال پیش
0.41 مگابایت
نوع : pdf
بازدید : 3228
منتشرکننده : کارگیک
|
نمونه سئوالات آزمون سیستم تعلیق خودرو (سری2از3)
4 سال پیش
0.4 مگابایت
نوع : pdf
بازدید : 2727
منتشرکننده : کارگیک
|
نمونه سئوالات آزمون سیستم تعلیق خودرو (سری1از3)
4 سال پیش
0.4 مگابایت
نوع : pdf
بازدید : 3289
منتشرکننده : کارگیک
|
نمونه سئوالات آزمون سیستم انژکتور خودرو (سری6از6)
4 سال پیش
0.32 مگابایت
نوع : pdf
بازدید : 3626
منتشرکننده : کارگیک
|
نمونه سئوالات آزمون سیستم انژکتور خودرو (سری5از6)
4 سال پیش
0.33 مگابایت
نوع : pdf
بازدید : 3387
منتشرکننده : کارگیک
|
نمونه سئوالات آزمون سیستم انژکتور خودرو (سری4از6)
4 سال پیش
0.33 مگابایت
نوع : pdf
بازدید : 3426
منتشرکننده : کارگیک
|
نمونه سئوالات آزمون سیستم انژکتور خودرو (سری3از6)
4 سال پیش
0.32 مگابایت
نوع : pdf
بازدید : 3381
منتشرکننده : کارگیک
|
نمونه سئوالات آزمون سیستم انژکتور خودرو (سری2از6)
4 سال پیش
0.1 مگابایت
نوع : pdf
بازدید : 3325
منتشرکننده : کارگیک
|
نمونه سئوالات آزمون سیستم انژکتور خودرو (سری1از6)
4 سال پیش
0.13 مگابایت
نوع : pdf
بازدید : 3717
منتشرکننده : کارگیک
|
نمونه سئوالات آزمون سرویس و نگه داری خودرو (سری8از8)
4 سال پیش
0.27 مگابایت
نوع : pdf
بازدید : 2732
منتشرکننده : کارگیک
|
نمونه سئوالات آزمون سرویس و نگه داری خودرو (سری7از8)
4 سال پیش
0.28 مگابایت
نوع : pdf
بازدید : 2734
منتشرکننده : کارگیک
|
نمونه سئوالات آزمون سرویس و نگه داری خودرو (سری6از8)
4 سال پیش
0.3 مگابایت
نوع : pdf
بازدید : 2702
منتشرکننده : کارگیک
|
نمونه سئوالات آزمون سرویس و نگه داری خودرو (سری5از8)
4 سال پیش
0.24 مگابایت
نوع : pdf
بازدید : 3079
منتشرکننده : کارگیک
|
نمونه سئوالات آزمون سرویس و نگه داری خودرو (سری4از8)
4 سال پیش
0.77 مگابایت
نوع : pdf
بازدید : 2742
منتشرکننده : کارگیک
|
نمونه سئوالات آزمون سرویس و نگه داری خودرو (سری3از8)
4 سال پیش
0.24 مگابایت
نوع : pdf
بازدید : 2706
منتشرکننده : کارگیک
|
نمونه سئوالات آزمون سرویس و نگه داری خودرو (سری2از8)
4 سال پیش
0.24 مگابایت
نوع : pdf
بازدید : 2854
منتشرکننده : کارگیک
|
نمونه سئوالات آزمون سرویس و نگه داری خودرو (سری1از8)
4 سال پیش
0.24 مگابایت
نوع : pdf
بازدید : 2734
منتشرکننده : کارگیک
|
نمونه سئوالات آزمون تون آپ خودرو (سری5از5)
4 سال پیش
0.23 مگابایت
نوع : pdf
بازدید : 5785
منتشرکننده : کارگیک
|
نمونه سئوالات آزمون تون آپ خودرو (سری4از5)
4 سال پیش
0.19 مگابایت
نوع : pdf
بازدید : 3084
منتشرکننده : کارگیک
|
نمونه سئوالات آزمون تون آپ خودرو (سری3از5)
4 سال پیش
0.25 مگابایت
نوع : pdf
بازدید : 3915
منتشرکننده : کارگیک
|
نمونه سئوالات آزمون تون آپ خودرو (سری2از5)
4 سال پیش
0.73 مگابایت
نوع : pdf
بازدید : 2886
منتشرکننده : کارگیک
|
نمونه سئوالات آزمون تون آپ خودرو (سری1از5)
4 سال پیش
0.26 مگابایت
نوع : pdf
بازدید : 3470
منتشرکننده : کارگیک
|
نمونه سئوالات سیستم ترمز هیدروپنوماتیک
4 سال پیش
0.56 مگابایت
نوع : pdf
بازدید : 2809
منتشرکننده : کارگیک
|
نمونه سئوالات قطعه شناسی اتومکانیک خودرو
4 سال پیش
0.22 مگابایت
نوع : pdf
بازدید : 3409
منتشرکننده : کارگیک
|
نمونه سئوالات سیستم سوخت رسانی دیزل (سری5از5)
4 سال پیش
0.39 مگابایت
نوع : pdf
بازدید : 2812
منتشرکننده : کارگیک
|
نمونه سئوالات سیستم سوخت رسانی دیزل (سری4از5)
4 سال پیش
0.3 مگابایت
نوع : pdf
بازدید : 3132
منتشرکننده : کارگیک
|
نمونه سئوالات سیستم سوخت رسانی دیزل (سری3از5)
4 سال پیش
0.29 مگابایت
نوع : pdf
بازدید : 2977
منتشرکننده : کارگیک
|
نمونه سئوالات سیستم سوخت رسانی دیزل (سری2از5)
4 سال پیش
0.29 مگابایت
نوع : pdf
بازدید : 3263
منتشرکننده : کارگیک
|
نمونه سئوالات سیستم سوخت رسانی دیزل (سری1از5)
4 سال پیش
0.31 مگابایت
نوع : pdf
بازدید : 3214
منتشرکننده : کارگیک
|
نمونه سئوالات دیاگ مکانیک خودرو
4 سال پیش
0.16 مگابایت
نوع : pdf
بازدید : 3849
منتشرکننده : کارگیک
|
نمونه سئوالات CNG و اتومبیل های گازسوز مکانیک خودرو
4 سال پیش
0.75 مگابایت
نوع : pdf
بازدید : 3002
منتشرکننده : کارگیک
|
نمونه سئوالات کاربراتور مکانیک خودرو
4 سال پیش
0.44 مگابایت
نوع : pdf
بازدید : 3211
منتشرکننده : کارگیک
|
نمونه سئوالات شناسایی ایرادات مولد قدرت اتومکانیک خودرو درجه یک
4 سال پیش
0.17 مگابایت
نوع : pdf
بازدید : 2639
منتشرکننده : کارگیک
|
نمونه سئوالات نقشه کشی صنعتی اتوخودرو درجه یک
4 سال پیش
0.58 مگابایت
نوع : pdf
بازدید : 2662
منتشرکننده : کارگیک
|
نمونه سئوالات جلوبندی و جعبه فرمان مکانیک خودرو درجه یک
4 سال پیش
0.32 مگابایت
نوع : pdf
بازدید : 2958
منتشرکننده : کارگیک
|
نمونه سئوالات سیستم ترمز معمولی و ABS مکانیک خودرو درجه یک
4 سال پیش
0.6 مگابایت
نوع : pdf
بازدید : 3015
منتشرکننده : کارگیک
|
نمونه سئوالات انتقال قدرت مکانیک خودرو درجه یک
4 سال پیش
0.92 مگابایت
نوع : pdf
بازدید : 7675
منتشرکننده : کارگیک
|
نمونه سئوالات برق و الکترونیک و سیستم جرقه مکانیک خودرو درجه یک
4 سال پیش
0.76 مگابایت
نوع : pdf
بازدید : 3125
منتشرکننده : کارگیک
|
نمونه سئوالات سوخت رسانی مکانیک خودرو درجه یک
4 سال پیش
1.03 مگابایت
نوع : pdf
بازدید : 2960
منتشرکننده : کارگیک
|
نمونه سئوالات مولد قدرت مکانیک خودرو درجه یک
4 سال پیش
0.88 مگابایت
نوع : pdf
بازدید : 3063
منتشرکننده : کارگیک
|
نمونه سئوالات ابزارشناسی مکانیک خودرو درجه یک
4 سال پیش
0.3 مگابایت
نوع : pdf
بازدید : 2564
منتشرکننده : کارگیک
|
سئوالات تئوری ﺗﻌﻤﻴﺮ ﻣﻮﺗﻮر و ﺑﺮق ﺧﻮدرو ﻫﺸﺘﻤﻴﻦ دوره ﻣﺴﺎﺑﻘﺎت علمی کاربردی ﻣﺮﺣﻠﻪ استانیﻣﻜﺎﻧﻴﻚ ﺧﻮدرو
4 سال پیش
0.12 مگابایت
نوع : pdf
بازدید : 3045
منتشرکننده : کارگیک
|
راهنمای ضدیخ ضدجوش برای خودروهای سواری
4 سال پیش
1.71 مگابایت
نوع : pdf
بازدید : 5075
منتشرکننده : mkrm
|
آموزش تنظیم موتور،بازکردن،تعمیر و تنظیم کاربراتور ودلکو 28:28
4 سال پیش
1.8 مگابایت
نوع : pdf
بازدید : 11287
منتشرکننده : Aminmogadas
|
اموزش برق بیل کوماتسو ۴۰۰ خط ۷
4 سال پیش
0.06 مگابایت
نوع : pdf
بازدید : 6849
منتشرکننده : alireza barani
|
Bosch 7.4.5 برد خام ECU
4 سال پیش
2.73 مگابایت
نوع : pdf
بازدید : 7788
منتشرکننده : afi1001
|
Hacking Connected Cars Tactics, Techniques, and Procedures
4 سال پیش
16.86 مگابایت
نوع : pdf
بازدید : 4113
منتشرکننده : کارگیک
|
The Car Hacker's Handbook
4 سال پیش
24.61 مگابایت
نوع : pdf
بازدید : 4183
منتشرکننده : کارگیک
|
Cybersecurity in Robotics: Challenges, Quantitative Modeling, and Practice
4 سال پیش
5.71 مگابایت
نوع : pdf
بازدید : 4118
منتشرکننده : کارگیک
|
نقشه کولر زانتیا
4 سال پیش
0.15 مگابایت
نوع : pdf
بازدید : 18224
منتشرکننده : hoceinrazavi
|
نقشه سیمکشی یونیت فن سمند
4 سال پیش
0.15 مگابایت
نوع : pdf
بازدید : 24021
منتشرکننده : hoceinrazavi
|
mbus tnm فایل امباس tnm
4 سال پیش
3.21 مگابایت
نوع : pdf
بازدید : 6071
منتشرکننده : سعید
|
نقشه سیمکشی دنا پلاس توربو اکوماکس
5 سال پیش
0.73 مگابایت
نوع : pdf
بازدید : 23715
منتشرکننده : hoceinrazavi
|
کتاب سیستم سوخت رسانی شرکت بوش
5 سال پیش
10.56 مگابایت
نوع : pdf
بازدید : 13647
منتشرکننده : Foad
|
ایسیو مگنتی مارلی
5 سال پیش
0.21 مگابایت
نوع : pdf
بازدید : 9598
منتشرکننده : hoceinrazavi
|
j34 pinout
5 سال پیش
0.11 مگابایت
نوع : pdf
بازدید : 25872
منتشرکننده : hoceinrazavi
|
تکنولوژی های جدید در موتور خودرو
5 سال پیش
1.57 مگابایت
نوع : pdf
بازدید : 10705
منتشرکننده : Ali m
|
راهنمای استفاده از رادیوپخش خودرو پژو 206 مدل CU2006BT
5 سال پیش
13.59 مگابایت
نوع : pdf
بازدید : 48308
منتشرکننده : shabgard
|
تعمیر و نگهداری نیسان پیکاپ
5 سال پیش
1.16 مگابایت
نوع : pdf
بازدید : 8885
منتشرکننده : reza,mk
|
کنترل موتور نیسان پیکاپ
5 سال پیش
2.11 مگابایت
نوع : pdf
بازدید : 6713
منتشرکننده : reza,mk
|
کلاچ نیسان پیکاپ
5 سال پیش
0.58 مگابایت
نوع : pdf
بازدید : 7495
منتشرکننده : reza,mk
|
عیب یابی نیسان پیکاپ
5 سال پیش
3.18 مگابایت
نوع : pdf
بازدید : 5886
منتشرکننده : reza,mk
|
راهنمای عمومی نیسان پیکاپ
5 سال پیش
1.68 مگابایت
نوع : pdf
بازدید : 11458
منتشرکننده : reza,mk
|
سوخت و اگزوز نیسان پیکاپ
5 سال پیش
0.23 مگابایت
نوع : pdf
بازدید : 6242
منتشرکننده : reza,mk
|
روغن و خنک کننده نیسان پیکاپ
5 سال پیش
0.98 مگابایت
نوع : pdf
بازدید : 7180
منتشرکننده : reza,mk
|
ترمز نیسان پیکاپ
5 سال پیش
1.33 مگابایت
نوع : pdf
بازدید : 6679
منتشرکننده : reza,mk
|
ابعاد سوپاپ کلیه موتورهای نیسان nissan
5 سال پیش
5.48 مگابایت
نوع : pdf
بازدید : 8522
منتشرکننده : حامد بیگی
|
راهنمای تعمیرات هایلوکس ۲۰۰۲
5 سال پیش
39.24 مگابایت
نوع : pdf
بازدید : 23078
منتشرکننده : حامد بیگی
|
لیست کدهای خطا در دیاگ به زبان فارسی
5 سال پیش
2.17 مگابایت
نوع : pdf
بازدید : 185953
منتشرکننده : Behzad_roohi
|
دفترچه راهنمای یوزرمنوال انگلیسی موسو (SsangYong Musso)
5 سال پیش
4.02 مگابایت
نوع : pdf
بازدید : 4590
منتشرکننده : eng_omidvar
|
مکمل کتابچه سرویس منوال موسو (SsangYong Musso)
5 سال پیش
21.37 مگابایت
نوع : pdf
بازدید : 5509
منتشرکننده : eng_omidvar
|
دفترچه سرویس منوال انگلیسی موسو (SsangYong Musso)
5 سال پیش
21.1 مگابایت
نوع : pdf
بازدید : 5055
منتشرکننده : eng_omidvar
|
دفترچه راهنمای یوزرمنوال فارسی موسو (SsangYong Musso)
5 سال پیش
11.44 مگابایت
نوع : pdf
بازدید : 12615
منتشرکننده : eng_omidvar
|
سیم کشی و ترمینالهای موسو (SsangYong Musso)
5 سال پیش
14.75 مگابایت
نوع : pdf
بازدید : 13129
منتشرکننده : eng_omidvar
|
راهنما موتور ba48c بنزینی هوا خنک کمپرسور mc-2 شرکت ویسکانزین امریکا
5 سال پیش
1.33 مگابایت
نوع : pdf
بازدید : 4411
منتشرکننده : A.rahmani
|
مجله آموزشی چراغ چک - شماره سوم
5 سال پیش
19.4 مگابایت
نوع : pdf
بازدید : 9818
منتشرکننده : چراغ چک
|
مجله آموزشی چراغ چک - شماره دوم
5 سال پیش
20.95 مگابایت
نوع : pdf
بازدید : 7894
منتشرکننده : چراغ چک
|
مجله آموزشی چراغ چک - شماره اول
5 سال پیش
20.59 مگابایت
نوع : pdf
بازدید : 10376
منتشرکننده : چراغ چک
|
جانمایی قطعات در ایسیو ریو
5 سال پیش
0.2 مگابایت
نوع : pdf
بازدید : 9027
منتشرکننده : چراغ چک
|
پين اوت و راهنماي کيلومتر ريو
5 سال پیش
2.29 مگابایت
نوع : pdf
بازدید : 8525
منتشرکننده : چراغ چک
|
جانمایی رله و فیوزها در خودروی تیگو 7
5 سال پیش
0.91 مگابایت
نوع : pdf
بازدید : 19779
منتشرکننده : چراغ چک
|
نقشه سیم کشی سیستم تهویه مطبوع LIFAN 820
5 سال پیش
2.75 مگابایت
نوع : pdf
بازدید : 6158
منتشرکننده : چراغ چک
|
جانمایی قطعات بر روی نود FN سمند ماکس
5 سال پیش
0.2 مگابایت
نوع : pdf
بازدید : 14995
منتشرکننده : چراغ چک
|
پين اوت ايسيو گيربکس اتوماتيک پارس با موتور TU5
5 سال پیش
0.17 مگابایت
نوع : pdf
بازدید : 7339
منتشرکننده : چراغ چک
|
جعبه فیوز و رله داخل اتاق لیفان 820
5 سال پیش
0.19 مگابایت
نوع : pdf
بازدید : 12530
منتشرکننده : چراغ چک
|
جعبه فیوز داخل اتاق Arrizo 5
5 سال پیش
0.12 مگابایت
نوع : pdf
بازدید : 19115
منتشرکننده : چراغ چک
|
فیوز و رله های محفظه موتور دنا پلاس
5 سال پیش
3.33 مگابایت
نوع : pdf
بازدید : 7482
منتشرکننده : چراغ چک
|
فیوز و رله های داخل اتاق دنا پلاس
5 سال پیش
3.53 مگابایت
نوع : pdf
بازدید : 15453
منتشرکننده : چراغ چک
|
پین اوت نود BCM خودروهای برلیانس H230 و H330
5 سال پیش
8.5 مگابایت
نوع : pdf
بازدید : 10389
منتشرکننده : چراغ چک
|
جعبه فیوز و رله محفظه موتور خودروی کوراندو
5 سال پیش
0.13 مگابایت
نوع : pdf
بازدید : 6699
منتشرکننده : چراغ چک
|
جعبه فيوز موتور خودروی زوتی S300
5 سال پیش
2.51 مگابایت
نوع : pdf
بازدید : 22800
منتشرکننده : چراغ چک
|
جعبه فيوز و رله محفظه موتور مزدا 3
5 سال پیش
1.86 مگابایت
نوع : pdf
بازدید : 28116
منتشرکننده : چراغ چک
|
نقشه شیشه بالابرهای برقی مزدا 3
5 سال پیش
3.36 مگابایت
نوع : pdf
بازدید : 7917
منتشرکننده : چراغ چک
|
فن زانتیا
5 سال پیش
1.29 مگابایت
نوع : pdf
بازدید : 28384
منتشرکننده : چراغ چک
|
جعبه فیوز محفظه موتور زانتیا
5 سال پیش
1.95 مگابایت
نوع : pdf
بازدید : 51763
منتشرکننده : چراغ چک
|
پین اوت ایسیو خودرو لیفان X70
5 سال پیش
1.14 مگابایت
نوع : pdf
بازدید : 6212
منتشرکننده : چراغ چک
|
پين اوت کانکتور OBD لیفان X70
5 سال پیش
0.72 مگابایت
نوع : pdf
بازدید : 5051
منتشرکننده : چراغ چک
|
پين اوت پنل پشت کیلومتر لیفان X70
5 سال پیش
0.86 مگابایت
نوع : pdf
بازدید : 4734
منتشرکننده : چراغ چک
|
فیوز و رله ها و پین اوت های سوکت جعبه فیوز داخل اتاق خودروی H30 Cross
5 سال پیش
2.73 مگابایت
نوع : pdf
بازدید : 8676
منتشرکننده : چراغ چک
|
پین اوت یونیت UCH خودرو L90
5 سال پیش
0.13 مگابایت
نوع : pdf
بازدید : 16739
منتشرکننده : چراغ چک
|
پین اوت و راهنمای کیلومتر برلیانس H320 H330
5 سال پیش
0.18 مگابایت
نوع : pdf
بازدید : 15360
منتشرکننده : چراغ چک
|
شیشه بالابر جلو SMS
5 سال پیش
0.16 مگابایت
نوع : pdf
بازدید : 10977
منتشرکننده : چراغ چک
|
شیشه بالابر جلو سمند ماکس
5 سال پیش
0.12 مگابایت
نوع : pdf
بازدید : 12009
منتشرکننده : چراغ چک
|
برف پاکن جلو مالتی پلکس فرانسه
5 سال پیش
0.11 مگابایت
نوع : pdf
بازدید : 10367
منتشرکننده : چراغ چک
|
نقشه سيستم کنترل دربها لیفان 820
5 سال پیش
0.14 مگابایت
نوع : pdf
بازدید : 7526
منتشرکننده : چراغ چک
|
سیستم سوخت رسانی و جرقه لیفان X60 ایسیو MT22.1
5 سال پیش
0.15 مگابایت
نوع : pdf
بازدید : 12321
منتشرکننده : چراغ چک
|
جعبه فیوز محفظه موتور برلیانس V5
5 سال پیش
1.07 مگابایت
نوع : pdf
بازدید : 5378
منتشرکننده : چراغ چک
|
جعبه فیوز و رله محفظه موتور برلیانس H220 & H230
5 سال پیش
0.15 مگابایت
نوع : pdf
بازدید : 41377
منتشرکننده : چراغ چک
|
پین اوت ایسیو چانگان ایدو Changan EADO
5 سال پیش
1.27 مگابایت
نوع : pdf
بازدید : 6323
منتشرکننده : چراغ چک
|
جعبه رله و فیوز محفظه موتور لیفان 620
5 سال پیش
0.11 مگابایت
نوع : pdf
بازدید : 43043
منتشرکننده : چراغ چک
|
پشت کیلومتر MVM550
5 سال پیش
0.12 مگابایت
نوع : pdf
بازدید : 16382
منتشرکننده : چراغ چک
|
جعبه فیوز و رله داخل اتاق خودروی کپچر
5 سال پیش
2.07 مگابایت
نوع : pdf
بازدید : 7652
منتشرکننده : فرشاد حسین پور
|
مدار فن تک موتوره(پراید،تندر ۹۰،پژو۲۰۶
5 سال پیش
0.99 مگابایت
نوع : pdf
بازدید : 21211
منتشرکننده : yasinsolgi
|
مایع ادبلو
5 سال پیش
1.26 مگابایت
نوع : pdf
بازدید : 7232
منتشرکننده : مهدی وظیفه
|
راهنما موتور mg550 زبان اصلی
5 سال پیش
1.12 مگابایت
نوع : pdf
بازدید : 11691
منتشرکننده : A.rahmani
|
راهنمای بدنه MVM 110
5 سال پیش
3.59 مگابایت
نوع : pdf
بازدید : 10173
منتشرکننده : عمار رضوی
|
کتاب درسی مولد قدرت خودروهای سواری جلد دوم
5 سال پیش
19.76 مگابایت
نوع : pdf
بازدید : 11644
منتشرکننده : کارگیک
|
کتاب درسی نقشه کشی و نقشه خوانی برای تعمیرکاران
5 سال پیش
4.9 مگابایت
نوع : pdf
بازدید : 16100
منتشرکننده : کارگیک
|
کتاب درسی مولد قدرت خودروهای سواری جلد اول
5 سال پیش
13.51 مگابایت
نوع : pdf
بازدید : 11549
منتشرکننده : کارگیک
|
کتاب درسی مبانی برق و الکترونیک در خودرو
5 سال پیش
16.22 مگابایت
نوع : pdf
بازدید : 19433
منتشرکننده : کارگیک
|
کتاب درسی مدارهای پایه در الکترونیک
5 سال پیش
29.8 مگابایت
نوع : pdf
بازدید : 6662
منتشرکننده : کارگیک
|
کتاب درسی مدارهای الکتریکی خودرو
5 سال پیش
27.11 مگابایت
نوع : pdf
بازدید : 14298
منتشرکننده : کارگیک
|
کتاب درسی مبانی الکتریسیته
5 سال پیش
36.44 مگابایت
نوع : pdf
بازدید : 5331
منتشرکننده : کارگیک
|
کتاب درسی کاربرد فناوری های نوین
5 سال پیش
6.9 مگابایت
نوع : pdf
بازدید : 4530
منتشرکننده : کارگیک
|
کتاب درسی فلزکاری عمومی درکشاورزی ۱
5 سال پیش
5.74 مگابایت
نوع : pdf
بازدید : 3933
منتشرکننده : کارگیک
|
کتاب درسی فلزکاری عمومی درکشاورزی ۲
5 سال پیش
2.93 مگابایت
نوع : pdf
بازدید : 4158
منتشرکننده : کارگیک
|
کتاب درسی فلزکاری جلد اول
5 سال پیش
10.97 مگابایت
نوع : pdf
بازدید : 4984
منتشرکننده : کارگیک
|
کتاب درسی فلزکاری جلد دوم
5 سال پیش
19.87 مگابایت
نوع : pdf
بازدید : 4395
منتشرکننده : کارگیک
|
کتاب درسی سیم پیچی الکتروموتورهای سه فاز
5 سال پیش
11.84 مگابایت
نوع : pdf
بازدید : 4586
منتشرکننده : کارگیک
|
کتاب درسی سیستم هدایت و کنترل خودرو
5 سال پیش
12.27 مگابایت
نوع : pdf
بازدید : 10087
منتشرکننده : کارگیک
|
کتاب درسی سیم پیچی الکترو موتورهای تکفاز
5 سال پیش
8.93 مگابایت
نوع : pdf
بازدید : 8474
منتشرکننده : کارگیک
|
کتاب درسی سیستم های روشنایی و ضد سرقت خودرو
5 سال پیش
17.65 مگابایت
نوع : pdf
بازدید : 10309
منتشرکننده : کارگیک
|
کتاب درسی سیستم های الکتریکی خودرو
5 سال پیش
23.47 مگابایت
نوع : pdf
بازدید : 12052
منتشرکننده : کارگیک
|
کتاب درسی سیستم سوخت رسانی و جرقه خودروهای سواری
5 سال پیش
12.49 مگابایت
نوع : pdf
بازدید : 13833
منتشرکننده : کارگیک
|
کتاب درسی رسم فنی ۱
5 سال پیش
9.68 مگابایت
نوع : pdf
بازدید : 4333
منتشرکننده : کارگیک
|
کتاب درسی رسم فنی ۲
5 سال پیش
5.69 مگابایت
نوع : pdf
بازدید : 5570
منتشرکننده : کارگیک
|
کتاب درسی رانندگی تراکتور و تیلر
5 سال پیش
14.27 مگابایت
نوع : pdf
بازدید : 7103
منتشرکننده : کارگیک
|
کتاب درسی تعمیر موتور دیزل
5 سال پیش
22.51 مگابایت
نوع : pdf
بازدید : 9158
منتشرکننده : کارگیک
|
کتاب درسی تراشکاری جلد دوم
5 سال پیش
17.35 مگابایت
نوع : pdf
بازدید : 4834
منتشرکننده : کارگیک
|
کتاب درسی تراشکاری جلد اول
5 سال پیش
18.6 مگابایت
نوع : pdf
بازدید : 4791
منتشرکننده : کارگیک
|
کتاب درسی برنامه نویسی CNC
5 سال پیش
2.57 مگابایت
نوع : pdf
بازدید : 5214
منتشرکننده : کارگیک
|
کتاب درسی انتقال قدرت خودروهای سواری
5 سال پیش
14.49 مگابایت
نوع : pdf
بازدید : 9264
منتشرکننده : کارگیک
|
کتاب درسی باز پیچی الکتروموتورها
5 سال پیش
10.2 مگابایت
نوع : pdf
بازدید : 4704
منتشرکننده : کارگیک
|
کتاب درسی الکترونیک پایه
5 سال پیش
19.12 مگابایت
نوع : pdf
بازدید : 6536
منتشرکننده : کارگیک
|
کتاب درسی اتصال ماشین های یدک کش
5 سال پیش
1.76 مگابایت
نوع : pdf
بازدید : 4601
منتشرکننده : کارگیک
|
کتاب درسی تعمیرات سیستم سوخت و جرقه
5 سال پیش
12.91 مگابایت
نوع : pdf
بازدید : 8359
منتشرکننده : کارگیک
|
کتاب درسی تعمیرات سیستم های برقی خودرو
5 سال پیش
12.35 مگابایت
نوع : pdf
بازدید : 14016
منتشرکننده : کارگیک
|
کتاب درسی تعمیرات سیستم تعلیق، فرمان و ترمز خودرو
5 سال پیش
7.14 مگابایت
نوع : pdf
بازدید : 9664
منتشرکننده : کارگیک
|
کتاب درسی تعمیرات جعبه دنده و دیفرانسیل
5 سال پیش
6.37 مگابایت
نوع : pdf
بازدید : 6744
منتشرکننده : کارگیک
|
کتاب درسی تعمیر موتور و سیستم های مکانیکی تراکتور
5 سال پیش
8.59 مگابایت
نوع : pdf
بازدید : 6528
منتشرکننده : کارگیک
|
کتاب درسی تعمیرات مکانیکی موتور
5 سال پیش
13.44 مگابایت
نوع : pdf
بازدید : 10667
منتشرکننده : کارگیک
|
کتاب درسی تعمیر و تنظیم ماشین های زراعی و باغی
5 سال پیش
10.34 مگابایت
نوع : pdf
بازدید : 4322
منتشرکننده : کارگیک
|
کتاب درسی تعمیر و مونتاژ تجهیزات کشاورزی
5 سال پیش
10.08 مگابایت
نوع : pdf
بازدید : 4063
منتشرکننده : کارگیک
|
کتاب درسی تعمیر و نگهداری سامانه رانشی کشتی
5 سال پیش
7.66 مگابایت
نوع : pdf
بازدید : 4855
منتشرکننده : کارگیک
|
کتاب درسی تعمیر و نگهداری ماشین آلات کشتی
5 سال پیش
12.48 مگابایت
نوع : pdf
بازدید : 4146
منتشرکننده : کارگیک
|
کتاب درسی تولید قطعات به روش تراشکاری (فرزکاری و سنگ زنی)
5 سال پیش
9.76 مگابایت
نوع : pdf
بازدید : 4655
منتشرکننده : کارگیک
|
کتاب درسی دانش فنی پایه - الکترونیک
5 سال پیش
18.89 مگابایت
نوع : pdf
بازدید : 5074
منتشرکننده : کارگیک
|
کتاب درسی تولید قطعات به روش تراشکاری و CNC
5 سال پیش
6.67 مگابایت
نوع : pdf
بازدید : 6062
منتشرکننده : کارگیک
|
کتاب درسی تولید به روش مونتاژکاری
5 سال پیش
8.96 مگابایت
نوع : pdf
بازدید : 4297
منتشرکننده : کارگیک
|
کتاب درسی تولید قطعات به روش تراشکاری
5 سال پیش
9.22 مگابایت
نوع : pdf
بازدید : 4291
منتشرکننده : کارگیک
|
کتاب درسی دانش فنی پایه - حمل و نقل
5 سال پیش
7.31 مگابایت
نوع : pdf
بازدید : 3819
منتشرکننده : کارگیک
|
کتاب درسی دانش فنی پایه مکاترونیک
5 سال پیش
15.76 مگابایت
نوع : pdf
بازدید : 3968
منتشرکننده : کارگیک
|
کتاب درسی دانش فنی پایه - ماشین ابزار
5 سال پیش
5.91 مگابایت
نوع : pdf
بازدید : 4155
منتشرکننده : کارگیک
|
کتاب درسی دانش فنی پایه - ماشین های کشاورزی
5 سال پیش
4.06 مگابایت
نوع : pdf
بازدید : 3668
منتشرکننده : کارگیک
|
کتاب درسی دانش فنی پایه - مکانیک خودرو
5 سال پیش
3.89 مگابایت
نوع : pdf
بازدید : 5621
منتشرکننده : کارگیک
|
کتاب درسی دانش فنی تخصصی - الکترونیک
5 سال پیش
7.18 مگابایت
نوع : pdf
بازدید : 5101
منتشرکننده : کارگیک
|
کتاب درسی دانش فنی تخصصی - حمل و نقل
5 سال پیش
6.05 مگابایت
نوع : pdf
بازدید : 3958
منتشرکننده : کارگیک
|
کتاب درسی دانش فنی تخصصی - ماشین های کشاورزی
5 سال پیش
12.29 مگابایت
نوع : pdf
بازدید : 3768
منتشرکننده : کارگیک
|
کتاب درسی دانش فنی تخصصی - ماشین ابزار
5 سال پیش
8.05 مگابایت
نوع : pdf
بازدید : 4312
منتشرکننده : کارگیک
|
کتاب درسی دانش فنی تخصصی - مکاترونیک
5 سال پیش
7.74 مگابایت
نوع : pdf
بازدید : 4689
منتشرکننده : کارگیک
|
کتاب درسی دانش فنی تخصصی - مکانیک خودرو
5 سال پیش
5.96 مگابایت
نوع : pdf
بازدید : 5409
منتشرکننده : کارگیک
|
کتاب درسی دانش فنی تخصصی - مکانیک موتورهای دریایی
5 سال پیش
8.95 مگابایت
نوع : pdf
بازدید : 4488
منتشرکننده : کارگیک
|
کتاب درسی ساخت تجهیزات مکاترونیکی
5 سال پیش
8.65 مگابایت
نوع : pdf
بازدید : 4558
منتشرکننده : کارگیک
|
کتاب درسی سرویس و نگهداری خودروهای سواری
5 سال پیش
6.01 مگابایت
نوع : pdf
بازدید : 7525
منتشرکننده : کارگیک
|
کتاب درسی عملیات ایمنی و امدادرسانی
5 سال پیش
11.79 مگابایت
نوع : pdf
بازدید : 4071
منتشرکننده : کارگیک
|
کتاب درسی کاربرد و سرویس ماشین های برداشت و پس از برداشت
5 سال پیش
13.41 مگابایت
نوع : pdf
بازدید : 4935
منتشرکننده : کارگیک
|
کتاب درسی عملیات راهداری و نگهداری راه
5 سال پیش
14.54 مگابایت
نوع : pdf
بازدید : 3747
منتشرکننده : کارگیک
|
کتاب درسی عملیات روی کشتی
5 سال پیش
8.46 مگابایت
نوع : pdf
بازدید : 4341
منتشرکننده : کارگیک
|
کتاب درسی کاربرد و سرویس ماشینهای کاشت و داشت
5 سال پیش
13.02 مگابایت
نوع : pdf
بازدید : 3678
منتشرکننده : کارگیک
|
کتاب درسی مونتاژ و دمونتاژ قطعات اس ام دی و مستندسازی
5 سال پیش
5.99 مگابایت
نوع : pdf
بازدید : 4763
منتشرکننده : کارگیک
|
کتاب درسی نصب و راه اندازی مصنوعات مکاترونیکی
5 سال پیش
17.46 مگابایت
نوع : pdf
بازدید : 4030
منتشرکننده : کارگیک
|
کتاب درسی نصب و راه ندازی سیستم های کنترلی مکاترونیک
5 سال پیش
17.46 مگابایت
نوع : pdf
بازدید : 5150
منتشرکننده : کارگیک
|
کتاب درسی نقشه کشی فنی رایانه ای - گروه مکانیک
5 سال پیش
10.14 مگابایت
نوع : pdf
بازدید : 4550
منتشرکننده : کارگیک
|
کتاب درسی نگهداری و تعمیر سیستم های هیدرولیک و پنوماتیک
5 سال پیش
10.72 مگابایت
نوع : pdf
بازدید : 7058
منتشرکننده : کارگیک
|
کتاب درسی نگهداری و کاربرد ماشین های کشاورزی
5 سال پیش
10.18 مگابایت
نوع : pdf
بازدید : 3996
منتشرکننده : کارگیک
|
کتاب درسی همراه هنرجو - الکترونیک
5 سال پیش
18.43 مگابایت
نوع : pdf
بازدید : 5278
منتشرکننده : کارگیک
|
کتاب درسی همراه هنرجو - ماشین ابزار
5 سال پیش
22.12 مگابایت
نوع : pdf
بازدید : 4039
منتشرکننده : کارگیک
|
کتاب درسی هدایت کشتی
5 سال پیش
6.16 مگابایت
نوع : pdf
بازدید : 4003
منتشرکننده : کارگیک
|
کتاب درسی همراه هنرجو - ماشین های کشاورزی
5 سال پیش
10.98 مگابایت
نوع : pdf
بازدید : 3864
منتشرکننده : کارگیک
|
کتاب درسی همراه هنرجو - مکانیک خودرو
5 سال پیش
11.73 مگابایت
نوع : pdf
بازدید : 6496
منتشرکننده : کارگیک
|
کتاب درسی همراه هنرجو - مکانیک موتورهای دریایی
5 سال پیش
9.9 مگابایت
نوع : pdf
بازدید : 5241
منتشرکننده : کارگیک
|
نقشه FN پژو 206 P6L
5 سال پیش
0.1 مگابایت
نوع : pdf
بازدید : 8692
منتشرکننده : کارگیک
|
نقشه FCM رانا و 206 صندوقدار P6L ECO MUX
5 سال پیش
0.07 مگابایت
نوع : pdf
بازدید : 5354
منتشرکننده : کارگیک
|
نقشه FCM رانا و 206 P6L SP MUX
5 سال پیش
0.13 مگابایت
نوع : pdf
بازدید : 13739
منتشرکننده : کارگیک
|
نقشه FCM پژو 206 هاچ بک P6L ECO MUX
5 سال پیش
0.07 مگابایت
نوع : pdf
بازدید : 5184
منتشرکننده : کارگیک
|
نقشه CCN پژو 206 P6L
5 سال پیش
0.17 مگابایت
نوع : pdf
بازدید : 5393
منتشرکننده : کارگیک
|
نقشه BCM پژو 206 صندوقدار P6L ECO MUX
5 سال پیش
0.26 مگابایت
نوع : pdf
بازدید : 11824
منتشرکننده : کارگیک
|
نقشه BCM رانا و پژو 206 P6L SP MUX
5 سال پیش
0.2 مگابایت
نوع : pdf
بازدید : 5313
منتشرکننده : کارگیک
|
نقشه BCM پژو 206 هاچ بک P6L ECO MUX
5 سال پیش
0.27 مگابایت
نوع : pdf
بازدید : 7216
منتشرکننده : کارگیک
|
نقشه Interior Relay Box پژو 206 صندوقدار P6L ECO MUX
5 سال پیش
0.1 مگابایت
نوع : pdf
بازدید : 3594
منتشرکننده : کارگیک
|
نقشه Interior Relay Box پژو 206 P6L SP MUX
5 سال پیش
0.1 مگابایت
نوع : pdf
بازدید : 3281
منتشرکننده : کارگیک
|
نقشه Interior Relay Box پژو 206 هاچ بک P6L ECO MUX
5 سال پیش
0.1 مگابایت
نوع : pdf
بازدید : 3851
منتشرکننده : کارگیک
|
نقشه FUSE BOX (INTERIOR) پژو 206 P6L SP MUX
5 سال پیش
0.06 مگابایت
نوع : pdf
بازدید : 5781
منتشرکننده : کارگیک
|
نقشه Fuse Box (Interior) پژو 206 P6L ECO MUX
5 سال پیش
0.09 مگابایت
نوع : pdf
بازدید : 3630
منتشرکننده : کارگیک
|
نقشه Fuse Box (Front Bracket) رانا و پژو 206 P6L ECO MUX
5 سال پیش
0.13 مگابایت
نوع : pdf
بازدید : 3834
منتشرکننده : کارگیک
|
نقشه FUSE BOX (FRONT BRACKET) پژو 206 P6L SP MUX
5 سال پیش
0.06 مگابایت
نوع : pdf
بازدید : 3778
منتشرکننده : کارگیک
|
نقشه FN Fuse Box پژو 206 P6L
5 سال پیش
0.06 مگابایت
نوع : pdf
بازدید : 4202
منتشرکننده : کارگیک
|
نقشه Engine Relay Box رانا و پژو 206 P6L ECO MUX
5 سال پیش
0.17 مگابایت
نوع : pdf
بازدید : 3723
منتشرکننده : کارگیک
|
نقشه Engine Relay Box پژو 206 P6L SP MUX
5 سال پیش
0.09 مگابایت
نوع : pdf
بازدید : 3408
منتشرکننده : کارگیک
|
نقشه Engine Relay Box (FN) پژو 206 P6L
5 سال پیش
0.08 مگابایت
نوع : pdf
بازدید : 4237
منتشرکننده : کارگیک
|
نقشه CCN Fuse Box پژو 206 P6L
5 سال پیش
0.06 مگابایت
نوع : pdf
بازدید : 3850
منتشرکننده : کارگیک
|
نقشه شیشه بالابر عقب پژو 206 P6L ECO
5 سال پیش
0.2 مگابایت
نوع : pdf
بازدید : 6289
منتشرکننده : کارگیک
|
نقشه شیشه بالابر عقب پژو 206 P6L SP MUX
5 سال پیش
0.12 مگابایت
نوع : pdf
بازدید : 3873
منتشرکننده : کارگیک
|
نقشه شیشه بالابر عقب پژو 206 P6L
5 سال پیش
0.14 مگابایت
نوع : pdf
بازدید : 10127
منتشرکننده : کارگیک
|
نقشه شیشه بالابر و آینه های پژو 206 P6L ECO
5 سال پیش
0.2 مگابایت
نوع : pdf
بازدید : 4501
منتشرکننده : کارگیک
|
نقشه شیشه بالابر و آینه های پژو 206 P6L SP MUX
5 سال پیش
0.12 مگابایت
نوع : pdf
بازدید : 4058
منتشرکننده : کارگیک
|
نقشه شیشه بالابر و آینه های پژو 206 P6L
5 سال پیش
0.16 مگابایت
نوع : pdf
بازدید : 20002
منتشرکننده : کارگیک
|
نقشه چراغ ترمز و استپ پژو 206 صندوقدار P6L ECO
5 سال پیش
0.16 مگابایت
نوع : pdf
بازدید : 9908
منتشرکننده : کارگیک
|
نقشه چراغ ترمز و استپ پژو 206 صندوقدار P6L
5 سال پیش
0.14 مگابایت
نوع : pdf
بازدید : 5800
منتشرکننده : کارگیک
|
نقشه چراغ ترمز و استپ پژو 206 P6L SP MUX
5 سال پیش
0.12 مگابایت
نوع : pdf
بازدید : 4214
منتشرکننده : کارگیک
|
نقشه چراغ ترمز و استپ پژو 206 هاچ بک P6L ECO
5 سال پیش
0.14 مگابایت
نوع : pdf
بازدید : 3824
منتشرکننده : کارگیک
|
نقشه چراغ ترمز و استپ پژو 206 هاچ بک P6L
5 سال پیش
0.14 مگابایت
نوع : pdf
بازدید : 6319
منتشرکننده : کارگیک
|
نقشه چراغ جانبی پژو 206 صندوقدار P6L ECO MUX
5 سال پیش
0.15 مگابایت
نوع : pdf
بازدید : 3580
منتشرکننده : کارگیک
|
نقشه چراغ جانبی پژو 206 صندوقدار P6L
5 سال پیش
0.14 مگابایت
نوع : pdf
بازدید : 3608
منتشرکننده : کارگیک
|
نقشه چراغ جانبی پژو 206 هاچ بک P6L ECO MUX
5 سال پیش
0.15 مگابایت
نوع : pdf
بازدید : 2962
منتشرکننده : کارگیک
|
نقشه چراغ جانبی پژو 206 هاچ بک P6L
5 سال پیش
0.15 مگابایت
نوع : pdf
بازدید : 3597
منتشرکننده : کارگیک
|
نقشه چراغ جانبی پژو 206 P6L SP MUX
5 سال پیش
0.12 مگابایت
نوع : pdf
بازدید : 3226
منتشرکننده : کارگیک
|
نقشه چراغ سقفی و کلید لادری پژو 206 P6L ECO MUX
5 سال پیش
0.18 مگابایت
نوع : pdf
بازدید : 10298
منتشرکننده : کارگیک
|
نقشه چراغ سقفی و کلید لادری پژو 206 P6L
5 سال پیش
0.16 مگابایت
نوع : pdf
بازدید : 4808
منتشرکننده : کارگیک
|
نقشه چراغ سقفی و کلید لادری پژو 206 P6L SP MUX
5 سال پیش
0.14 مگابایت
نوع : pdf
بازدید : 14708
منتشرکننده : کارگیک
|
نقشه چراغ دنده عقب پژو 206 صندوقدار P6L ECO MUX
5 سال پیش
0.13 مگابایت
نوع : pdf
بازدید : 5689
منتشرکننده : کارگیک
|
نقشه چراغ دنده عقب پژو 206 P6L SP MUX
5 سال پیش
0.13 مگابایت
نوع : pdf
بازدید : 3543
منتشرکننده : کارگیک
|
نقشه چراغ دنده عقب پژو 206 P6L
5 سال پیش
0.11 مگابایت
نوع : pdf
بازدید : 10686
منتشرکننده : کارگیک
|
نقشه چراغ دنده عقب پژو 206 هاچ بک P6L ECO MUX
5 سال پیش
0.13 مگابایت
نوع : pdf
بازدید : 5007
منتشرکننده : کارگیک
|
نقشه چراغ جلو پژو 206 P6L ECO MUX
5 سال پیش
0.17 مگابایت
نوع : pdf
بازدید : 5124
منتشرکننده : کارگیک
|
نقشه چراغ جلو پژو 206 P6L
5 سال پیش
0.16 مگابایت
نوع : pdf
بازدید : 16372
منتشرکننده : کارگیک
|
نقشه فلاشر پژو 206 صندوقدار P6L ECO MUX
5 سال پیش
0.18 مگابایت
نوع : pdf
بازدید : 3824
منتشرکننده : کارگیک
|
نقشه فلاشر پژو 206 هاچ بک P6L ECO MUX
5 سال پیش
0.18 مگابایت
نوع : pdf
بازدید : 3563
منتشرکننده : کارگیک
|
نقشه فلاشر پژو 206 P6L
5 سال پیش
0.17 مگابایت
نوع : pdf
بازدید : 5881
منتشرکننده : کارگیک
|
نقشه فلاشر پژو 206 P6L SP MUX
5 سال پیش
0.12 مگابایت
نوع : pdf
بازدید : 3828
منتشرکننده : کارگیک
|
نقشه مه شکن جلو و عقب پژو 206 P6L ECO MUX
5 سال پیش
0.14 مگابایت
نوع : pdf
بازدید : 4177
منتشرکننده : کارگیک
|
نقشه مه شکن جلو و عقب پژو 206 P6L
5 سال پیش
0.12 مگابایت
نوع : pdf
بازدید : 3530
منتشرکننده : کارگیک
|
نقشه مه شکن جلو و عقب پژو 206 P6L SP MUX
5 سال پیش
0.11 مگابایت
نوع : pdf
بازدید : 11453
منتشرکننده : کارگیک
|
نقشه چراغ جلو پژو 206 P6L SP
5 سال پیش
0.13 مگابایت
نوع : pdf
بازدید : 4130
منتشرکننده : کارگیک
|
نقشه سیمکشی 206 غرب استیل MAW
5 سال پیش
1.16 مگابایت
نوع : pdf
بازدید : 25742
منتشرکننده : HOCRIN_RAZAVI
|
نقشه نمایشگر چندمنظوره پژو 206 P6L SPMUX
5 سال پیش
0.18 مگابایت
نوع : pdf
بازدید : 3237
منتشرکننده : کارگیک
|
نقشه نمایشگر چندمنظوره پژو 206 P6L ECO MUX
5 سال پیش
0.14 مگابایت
نوع : pdf
بازدید : 5525
منتشرکننده : کارگیک
|
نقشه نمایشگر چندمنظوره پژو 206 P6L
5 سال پیش
0.13 مگابایت
نوع : pdf
بازدید : 3170
منتشرکننده : کارگیک
|
نقشه صفحه نمایشگر داشبورد جلوآمپر پژو 206 P6L SP MUX
5 سال پیش
0.14 مگابایت
نوع : pdf
بازدید : 5118
منتشرکننده : کارگیک
|
نقشه صفحه نمایشگر داشبورد جلوآمپر پژو 206 P6L
5 سال پیش
0.12 مگابایت
نوع : pdf
بازدید : 3895
منتشرکننده : کارگیک
|
نقشه صفحه نمایشگر داشبورد جلوآمپر پژو 206 P6L ECO MUX
5 سال پیش
0.16 مگابایت
نوع : pdf
بازدید : 4069
منتشرکننده : کارگیک
|
نقشه نشانگر سطح بنزین پژو 206 P6L SP MUX Bosch ME17
5 سال پیش
0.11 مگابایت
نوع : pdf
بازدید : 3336
منتشرکننده : کارگیک
|
نقشه نشانگر سطح بنزین پژو 206 ایزی یو P6L ECO MUX TU5 SIEMENS(Easy U)
5 سال پیش
0.12 مگابایت
نوع : pdf
بازدید : 4217
منتشرکننده : کارگیک
|
نقشه نشانگر سطح بنزین پژو 206 غرب استیل P6L ECO MUX GHARB STEEL
5 سال پیش
0.13 مگابایت
نوع : pdf
بازدید : 3187
منتشرکننده : کارگیک
|
نقشه نشانگر سطح بنزین پژو 206 غرب استیل P6L SP MUX Gharb Steel
5 سال پیش
0.12 مگابایت
نوع : pdf
بازدید : 3548
منتشرکننده : کارگیک
|
نقشه نشانگر سطح بنزین پژو 206 P6L SP MUX SSAT
5 سال پیش
0.11 مگابایت
نوع : pdf
بازدید : 3593
منتشرکننده : کارگیک
|
نقشه نشانگر سطح بنزین پژو 206 کروز P6L ECO MUX CRUOSE
5 سال پیش
0.13 مگابایت
نوع : pdf
بازدید : 3335
منتشرکننده : کارگیک
|
نقشه نشانگر سطح بنزین پژو 206 P6L
5 سال پیش
0.13 مگابایت
نوع : pdf
بازدید : 7544
منتشرکننده : کارگیک
|
نقشه نشانگر فشار روغن موتور پژو 206 P6L ECO MUX
5 سال پیش
0.12 مگابایت
نوع : pdf
بازدید : 5160
منتشرکننده : کارگیک
|
نقشه نشانگر فشار روغن موتور پژو 206 P6L
5 سال پیش
0.1 مگابایت
نوع : pdf
بازدید : 14146
منتشرکننده : کارگیک
|
نقشه نشانگر فشار روغن موتور پژو 206 P6L SPMUX
5 سال پیش
0.11 مگابایت
نوع : pdf
بازدید : 3734
منتشرکننده : کارگیک
|
نقشه نشانگر دمای آب پژو 206 P6L SP MUX Bosch ME17
5 سال پیش
0.09 مگابایت
نوع : pdf
بازدید : 4373
منتشرکننده : کارگیک
|
نقشه نشانگر دمای آب پژو 206 زیمنس ایزی یو P6L ECO MUX TU5 SIEMENS(Easy U)
5 سال پیش
0.11 مگابایت
نوع : pdf
بازدید : 4201
منتشرکننده : کارگیک
|
نقشه نشانگر دمای آب پژو 206 غرب استیل P6L ECO MUX GHARB STEEL
5 سال پیش
0.12 مگابایت
نوع : pdf
بازدید : 3465
منتشرکننده : کارگیک
|
نقشه نشانگر دمای آب پژو 206 کروز P6L ECO MUX CRUOSE
5 سال پیش
0.12 مگابایت
نوع : pdf
بازدید : 3260
منتشرکننده : کارگیک
|
نقشه نشانگر دمای آب پژو 206 P6L
5 سال پیش
0.12 مگابایت
نوع : pdf
بازدید : 8695
منتشرکننده : کارگیک
|
نقشه نشانگر دمای آب پژو 206 P6L SP MUX SSAT
5 سال پیش
0.11 مگابایت
نوع : pdf
بازدید : 3884
منتشرکننده : کارگیک
|
نقشه نشانگر دمای آب پژو 206 P6L SP MUX TU3
5 سال پیش
0.13 مگابایت
نوع : pdf
بازدید : 3506
منتشرکننده : کارگیک
|
نقشه نشانگر سطح روغن ترمز و لامپ اخطار ترمز پژو 206 P6L ECO MUX
5 سال پیش
0.14 مگابایت
نوع : pdf
بازدید : 5000
منتشرکننده : کارگیک
|
نقشه نشانگر سطح روغن ترمز و لامپ اخطار ترمز پژو 206 P6L
5 سال پیش
0.12 مگابایت
نوع : pdf
بازدید : 3570
منتشرکننده : کارگیک
|
نقشه نشانگر سطح روغن ترمز و لامپ اخطار ترمز پژو 206 P6L SP MUX
5 سال پیش
0.11 مگابایت
نوع : pdf
بازدید : 7176
منتشرکننده : کارگیک
|
نقشه سیستم سوخت رسانی پژو 206 غرب استیل P6L SP MUX Gharb Steel
5 سال پیش
0.26 مگابایت
نوع : pdf
بازدید : 7640
منتشرکننده : کارگیک
|
نقشه سیستم سوخت رسانی پژو 206 P6L SP Mux Bosch ME17
5 سال پیش
0.13 مگابایت
نوع : pdf
بازدید : 10461
منتشرکننده : کارگیک
|
نقشه سیستم سوخت رسانی پژو 206 P6L ECO MUX TU3
5 سال پیش
0.25 مگابایت
نوع : pdf
بازدید : 3935
منتشرکننده : کارگیک
|
نقشه سیستم سوخت رسانی پژو 206 غرب استیل P6L ECO MUX GHARB STEEL
5 سال پیش
0.28 مگابایت
نوع : pdf
بازدید : 3694
منتشرکننده : کارگیک
|
نقشه سیستم سوخت رسانی پژو 206 P6L SP MUX SSAT
5 سال پیش
0.15 مگابایت
نوع : pdf
بازدید : 8535
منتشرکننده : کارگیک
|
نقشه سیستم سوخت رسانی پژو 206 زیمنس ایزی یو P6L - ECO MUX TU5 SIEMENS (Easy U)
5 سال پیش
0.21 مگابایت
نوع : pdf
بازدید : 16005
منتشرکننده : کارگیک
|
نقشه سیستم سوخت رسانی پژو 206 کروز P6L MUX TU5 CROUSE
5 سال پیش
0.26 مگابایت
نوع : pdf
بازدید : 6783
منتشرکننده : کارگیک
|
نقشه سیستم سوخت رسانی پژو 206 P6L
5 سال پیش
0.24 مگابایت
نوع : pdf
بازدید : 4083
منتشرکننده : کارگیک
|
نقشه سیستم سوخت رسانی پژو 206 ECU VALEO J34P TU3A
5 سال پیش
0.69 مگابایت
نوع : pdf
بازدید : 11565
منتشرکننده : کارگیک
|
نقشه سیستم سوخت رسانی پژو 206 TU3A J34P
5 سال پیش
0.56 مگابایت
نوع : pdf
بازدید : 4028
منتشرکننده : کارگیک
|
نقشه سیمکشی ME17.9.71
5 سال پیش
0.47 مگابایت
نوع : pdf
بازدید : 30251
منتشرکننده : HOCRIN_RAZAVI
|
نقشه فن خنک کننده موتور پژو 206 P6L SP MUX SSAT
5 سال پیش
0.11 مگابایت
نوع : pdf
بازدید : 4993
منتشرکننده : کارگیک
|
نقشه فن خنک کننده موتور پژو 206 غرب استیل P6L ECO MUX GHARB STEEL
5 سال پیش
0.12 مگابایت
نوع : pdf
بازدید : 3411
منتشرکننده : کارگیک
|
نقشه فن خنک کننده موتور پژو 206 غرب استیل P6L SP MUX Gharb Steel
5 سال پیش
0.13 مگابایت
نوع : pdf
بازدید : 3399
منتشرکننده : کارگیک
|
نقشه فن خنک کننده موتور پژو 206 P6L
5 سال پیش
0.14 مگابایت
نوع : pdf
بازدید : 20902
منتشرکننده : کارگیک
|
نقشه فن خنک کننده موتور پژو 206 کروز P6L ECO MUX CROUSE
5 سال پیش
0.16 مگابایت
نوع : pdf
بازدید : 5656
منتشرکننده : کارگیک
|
نقشه فن خنک کننده موتور پژو 206 زیمنس ایزی یو P6L ECO MUX TU5 SIEMENS (Easy U)
5 سال پیش
0.12 مگابایت
نوع : pdf
بازدید : 6185
منتشرکننده : کارگیک
|
نقشه فن خنک کننده موتور پژو 206 P6L SP MUX Bosch ME17
5 سال پیش
0.09 مگابایت
نوع : pdf
بازدید : 4393
منتشرکننده : کارگیک
|
نقشه دزدگیر پژو 206 P6L SPMUX
5 سال پیش
0.16 مگابایت
نوع : pdf
بازدید : 3804
منتشرکننده : کارگیک
|
نقشه دزدگیر پژو 206 P6L ECO
5 سال پیش
0.15 مگابایت
نوع : pdf
بازدید : 5264
منتشرکننده : کارگیک
|
نقشه سنسور دنده عقب پژو 206 P6L SP MUX
5 سال پیش
0.17 مگابایت
نوع : pdf
بازدید : 5408
منتشرکننده : کارگیک
|
نقشه سنسور دنده عقب پژو 206 P6L ECO MUX
5 سال پیش
0.14 مگابایت
نوع : pdf
بازدید : 15992
منتشرکننده : کارگیک
|
نقشه سیستم ضد سرقت ایموبیلایزر پژو 206 P6L ECO MUX غرب استیل
5 سال پیش
0.1 مگابایت
نوع : pdf
بازدید : 5752
منتشرکننده : کارگیک
|
نقشه سیستم ضد سرقت ایموبیلایزر پژو 206 زیمنس ایزی یو ECO MUX TU5 SIEMENS (Easy U)
5 سال پیش
0.11 مگابایت
نوع : pdf
بازدید : 5013
منتشرکننده : کارگیک
|
نقشه سیستم ضد سرقت ایموبیلایزر پژو 206 P6L SP MUX TU3 غرب استیل
5 سال پیش
0.11 مگابایت
نوع : pdf
بازدید : 3464
منتشرکننده : کارگیک
|
نقشه سیستم ضد سرقت ایموبیلایزر پژو 206 P6L SP MUX SSAT
5 سال پیش
0.11 مگابایت
نوع : pdf
بازدید : 4325
منتشرکننده : کارگیک
|
نقشه سیستم ضد سرقت ایموبیلایزر پژو 206 P6L
5 سال پیش
0.12 مگابایت
نوع : pdf
بازدید : 3662
منتشرکننده : کارگیک
|
نقشه سیستم ضد سرقت ایموبیلایزر پژو 206 P6L SP MUX Bosch ME17
5 سال پیش
0.1 مگابایت
نوع : pdf
بازدید : 3917
منتشرکننده : کارگیک
|
نقشه سیستم ضد سرقت ایموبیلایزر پژو 206 P6L ECO MUX CROUSE
5 سال پیش
0.16 مگابایت
نوع : pdf
بازدید : 4113
منتشرکننده : کارگیک
|
نقشه بوق پژو 206 P6L SP MUX
5 سال پیش
0.11 مگابایت
نوع : pdf
بازدید : 3613
منتشرکننده : کارگیک
|
نقشه بوق پژو 206 P6L
5 سال پیش
0.1 مگابایت
نوع : pdf
بازدید : 17201
منتشرکننده : کارگیک
|
نقشه بوق پژو 206 P6L ECO MUX
5 سال پیش
0.1 مگابایت
نوع : pdf
بازدید : 6265
منتشرکننده : کارگیک
|
نقشه قفل مرکزی پژو 206 P6L SP MUX
5 سال پیش
0.15 مگابایت
نوع : pdf
بازدید : 4566
منتشرکننده : کارگیک
|
نقشه قفل مرکزی پژو 206 صندوقدار P6L
5 سال پیش
0.17 مگابایت
نوع : pdf
بازدید : 5671
منتشرکننده : کارگیک
|
نقشه قفل مرکزی پژو 206 صندوقدار P6L ECO MUX
5 سال پیش
0.18 مگابایت
نوع : pdf
بازدید : 3671
منتشرکننده : کارگیک
|
نقشه قفل مرکزی پژو 206 P6L
5 سال پیش
0.17 مگابایت
نوع : pdf
بازدید : 3994
منتشرکننده : کارگیک
|
نقشه قفل مرکزی پژو 206 P6L ECO MUX
5 سال پیش
0.18 مگابایت
نوع : pdf
بازدید : 15667
منتشرکننده : کارگیک
|
نقشه ایربگ پژو 206 P6L دو ایربگ
5 سال پیش
0.16 مگابایت
نوع : pdf
بازدید : 7400
منتشرکننده : کارگیک
|
نقشه ایربگ پژو 206 P6L تک ایربگ
5 سال پیش
0.17 مگابایت
نوع : pdf
بازدید : 3599
منتشرکننده : کارگیک
|
نقشه ایربگ پژو 206 P6L ECO MUX دو ایربگ
5 سال پیش
0.16 مگابایت
نوع : pdf
بازدید : 3403
منتشرکننده : کارگیک
|
نقشه ایربگ پژو 206 P6L ECO MUX تک ایربگ
5 سال پیش
0.17 مگابایت
نوع : pdf
بازدید : 4052
منتشرکننده : کارگیک
|
نقشه ایربگ پژو 206 P6L SP MUX
5 سال پیش
0.12 مگابایت
نوع : pdf
بازدید : 3401
منتشرکننده : کارگیک
|
نقشه ترمز ABS پژو 206 P6L
5 سال پیش
0.14 مگابایت
نوع : pdf
بازدید : 3524
منتشرکننده : کارگیک
|
نقشه ترمز ABS Mando mg60 پژو 206 P6L ECO MUX
5 سال پیش
0.16 مگابایت
نوع : pdf
بازدید : 6470
منتشرکننده : کارگیک
|
نقشه ترمز ABS Mando MG80 پژو 206 P6L ECO MUX
5 سال پیش
0.17 مگابایت
نوع : pdf
بازدید : 8109
منتشرکننده : کارگیک
|
نقشه ترمز ABS پژو 206 MOBIS - P6L ECO MUX
5 سال پیش
0.16 مگابایت
نوع : pdf
بازدید : 9329
منتشرکننده : کارگیک
|
نقشه ترمز ABS پژو 206 MOBIS - P6L SP MUX
5 سال پیش
0.13 مگابایت
نوع : pdf
بازدید : 3394
منتشرکننده : کارگیک
|
نقشه آینه برقی پژو 206 P6L
5 سال پیش
0.15 مگابایت
نوع : pdf
بازدید : 3549
منتشرکننده : کارگیک
|
نقشه فندک پژو 206 P6L
5 سال پیش
0.12 مگابایت
نوع : pdf
بازدید : 3967
منتشرکننده : کارگیک
|
نقشه گرم کننده آینه و شیشه عقب پژو 206 P6L
5 سال پیش
0.14 مگابایت
نوع : pdf
بازدید : 7612
منتشرکننده : کارگیک
|
نقشه رادیو و پخش CD پژو 206 P6L
5 سال پیش
0.13 مگابایت
نوع : pdf
بازدید : 17299
منتشرکننده : کارگیک
|
نقشه سیستم تهویه پژو 206 P6L
5 سال پیش
0.26 مگابایت
نوع : pdf
بازدید : 5626
منتشرکننده : کارگیک
|
نقشه رادیو و پخش CD پژو 206 P6L ECO MUX کروز
5 سال پیش
0.14 مگابایت
نوع : pdf
بازدید : 4309
منتشرکننده : کارگیک
|
نقشه گرم کننده آینه و شیشه عقب پژو 206 ECO MUX Mannual HVAC
5 سال پیش
0.15 مگابایت
نوع : pdf
بازدید : 3470
منتشرکننده : کارگیک
|
نقشه سیستم تهویه دستی پژو 206 P6L ECO MUX
5 سال پیش
0.11 مگابایت
نوع : pdf
بازدید : 9145
منتشرکننده : کارگیک
|
نقشه سیستم تهویه پژو 206 P6L ECO MUX کروز
5 سال پیش
0.33 مگابایت
نوع : pdf
بازدید : 16682
منتشرکننده : کارگیک
|
نقشه سیستم تهویه پژو 206 P6L SP MUX SSAT
5 سال پیش
0.15 مگابایت
نوع : pdf
بازدید : 9154
منتشرکننده : کارگیک
|
نقشه آینه برقی پژو 206 P6L SP MUX
5 سال پیش
0.12 مگابایت
نوع : pdf
بازدید : 3625
منتشرکننده : کارگیک
|
نقشه گرم کننده آینه و شیشه عقب پژو 206 P6L SP MUX
5 سال پیش
0.13 مگابایت
نوع : pdf
بازدید : 3433
منتشرکننده : کارگیک
|
نقشه فندک پژو 206 P6L SP MUX
5 سال پیش
0.12 مگابایت
نوع : pdf
بازدید : 9529
منتشرکننده : کارگیک
|
نقشه رادیو و پخش CD پژو 206 P6L SP MUX
5 سال پیش
0.12 مگابایت
نوع : pdf
بازدید : 5739
منتشرکننده : کارگیک
|
نقشه سیستم تهویه پژو 206 P6L ECO MUX TU5 غرب استیل
5 سال پیش
0.24 مگابایت
نوع : pdf
بازدید : 7758
منتشرکننده : کارگیک
|
نقشه سیستم تهویه پژو 206 ECO MUX TU5 زیمنس ایزی یو
5 سال پیش
0.2 مگابایت
نوع : pdf
بازدید : 4648
منتشرکننده : کارگیک
|
نقشه سیستم تهویه پژو 206 P6L SP MUX Bosch ME17
5 سال پیش
0.21 مگابایت
نوع : pdf
بازدید : 5292
منتشرکننده : کارگیک
|
نقشه سیستم تهویه پژو 206 P6L SP MUX TU3 غرب استیل
5 سال پیش
0.19 مگابایت
نوع : pdf
بازدید : 3730
منتشرکننده : کارگیک
|
نقشه گرم کننده آینه و شیشه عقب پژو 206 P6L SP MUX TU3
5 سال پیش
0.18 مگابایت
نوع : pdf
بازدید : 3569
منتشرکننده : کارگیک
|
نقشه سیستم تهویه پژو 206 P6L ECO MUX
5 سال پیش
0.33 مگابایت
نوع : pdf
بازدید : 3309
منتشرکننده : کارگیک
|
نقشه آینه برقی پژو 206 P6L ECO MUX
5 سال پیش
0.2 مگابایت
نوع : pdf
بازدید : 9952
منتشرکننده : کارگیک
|
نقشه گرم کننده آینه و شیشه عقب پژو 206 ECO MUX
5 سال پیش
0.24 مگابایت
نوع : pdf
بازدید : 3422
منتشرکننده : کارگیک
|
نقشه رادیو و پخش CD پژو 206 P6L ECO MUX
5 سال پیش
0.13 مگابایت
نوع : pdf
بازدید : 3365
منتشرکننده : کارگیک
|
نقشه فندک پژو 206 P6L ECO MUX
5 سال پیش
0.12 مگابایت
نوع : pdf
بازدید : 3087
منتشرکننده : کارگیک
|
جدول اینترکانکتورهای پژو 206 P6L
5 سال پیش
0.15 مگابایت
نوع : pdf
بازدید : 3805
منتشرکننده : کارگیک
|
جدول اینترکانکتورهای پژو 206 P6L SP MUX
5 سال پیش
0.13 مگابایت
نوع : pdf
بازدید : 3562
منتشرکننده : کارگیک
|
جدول اینترکانکتورهای پژو 206 SP MUX TU3
5 سال پیش
0.08 مگابایت
نوع : pdf
بازدید : 4292
منتشرکننده : کارگیک
|
جدول اینترکانکتورهای پژو 206 P6L ECO MUX
5 سال پیش
0.16 مگابایت
نوع : pdf
بازدید : 7635
منتشرکننده : کارگیک
|
جدول اینترکانکتورهای پژو 206 زیمنس ایزی یو P6L ECO MUX TU5 SIEMENS ETC(Easy U)
5 سال پیش
0.12 مگابایت
نوع : pdf
بازدید : 4214
منتشرکننده : کارگیک
|
نقشه برف پاک کن و شیشه شوی پژو 206 هاچ بک P6L SP MUX
5 سال پیش
0.12 مگابایت
نوع : pdf
بازدید : 4531
منتشرکننده : کارگیک
|
نقشه برف پاک کن و شیشه شوی پژو 206 صندوقدار P6L
5 سال پیش
0.11 مگابایت
نوع : pdf
بازدید : 3201
منتشرکننده : کارگیک
|
نقشه برف پاک کن و شیشه شوی پژو 206 صندوقدار P6L SP MUX
5 سال پیش
0.15 مگابایت
نوع : pdf
بازدید : 3308
منتشرکننده : کارگیک
|
نقشه برف پاک کن و شیشه شوی پژو 206 صندوقدار P6L ECO MUX
5 سال پیش
0.15 مگابایت
نوع : pdf
بازدید : 8267
منتشرکننده : کارگیک
|
نقشه برف پاک کن و شیشه شوی پژو 206 هاچ بک P6L
5 سال پیش
0.12 مگابایت
نوع : pdf
بازدید : 27898
منتشرکننده : کارگیک
|
نقشه برف پاک کن و شیشه شوی پژو 206 هاچ بک P6L ECO MUX
5 سال پیش
0.17 مگابایت
نوع : pdf
بازدید : 6188
منتشرکننده : کارگیک
|
نقشه آلترناتور و استارت پژو 206 P6L SP MUX
5 سال پیش
0.15 مگابایت
نوع : pdf
بازدید : 3696
منتشرکننده : کارگیک
|
نقشه آلترناتور و استارت پژو 206 P6L
5 سال پیش
0.12 مگابایت
نوع : pdf
بازدید : 11789
منتشرکننده : کارگیک
|
نقشه آلترناتور و استارت پژو 206 P6L ECO MUX
5 سال پیش
0.12 مگابایت
نوع : pdf
بازدید : 4055
منتشرکننده : کارگیک
|
جزوه آموزشی موتور پژو 405 XU7 JP L3 و XU7 JP L4 ایساکو
5 سال پیش
6.21 مگابایت
نوع : pdf
بازدید : 18351
منتشرکننده : Mohammad_Karaj
|
راهنمای آموزشی تعمیرات ماشین آلات سنگین کوماتسو
5 سال پیش
493.2 مگابایت
نوع : pdf
بازدید : 8871
منتشرکننده : CarGeek
|
دستورالعمل عیب یابی و تعویض کمپرسور کولر تیبا
5 سال پیش
0.89 مگابایت
نوع : pdf
بازدید : 13068
منتشرکننده : CarGeek
|
جزوه آموزشی دیفرانسیل آریسان
5 سال پیش
1.04 مگابایت
نوع : pdf
بازدید : 7068
منتشرکننده : CarGeek
|
راهنمای تعمیرات تزئینات و تجهیزات آریسان
5 سال پیش
2.91 مگابایت
نوع : pdf
بازدید : 6582
منتشرکننده : CarGeek
|
مقاله طراحی و ساخت یک مدل خودرانش جهت ارزیابی مانور شناورها در آبهای آزاد
5 سال پیش
0.65 مگابایت
نوع : pdf
بازدید : 2729
منتشرکننده : CarGeek
|
مقاله تاثیر بکارگیری کشتی های خودران بر حمل و نقل دریایی
5 سال پیش
0.2 مگابایت
نوع : pdf
بازدید : 3455
منتشرکننده : CarGeek
|
راهنمای کدهای خطای سیستم ABS لیفان 620
5 سال پیش
0.27 مگابایت
نوع : pdf
بازدید : 8719
منتشرکننده : CarGeek
|
جزوه آموزشی مبانی هیدرولیک
5 سال پیش
3.29 مگابایت
نوع : pdf
بازدید : 9114
منتشرکننده : CarGeek
|
کتاب راهنمای کارگاهی موتورهای دیزلی کوماتسو (سری102)
5 سال پیش
185.07 مگابایت
نوع : pdf
بازدید : 5579
منتشرکننده : CarGeek
|
دستورالعمل عیب یابی قطعات لاستیکی جلوبندی
5 سال پیش
1.92 مگابایت
نوع : pdf
بازدید : 7680
منتشرکننده : CarGeek
|
لیست و شرح کدهای خطای MVM 110
5 سال پیش
0.53 مگابایت
نوع : pdf
بازدید : 21650
منتشرکننده : CarGeek
|
لیست و شرح کدهای خطای MVM 530
5 سال پیش
0.27 مگابایت
نوع : pdf
بازدید : 25519
منتشرکننده : CarGeek
|
روش رفع خطای (Automatic transmission internal pressure (DF226 مگان
5 سال پیش
0.43 مگابایت
نوع : pdf
بازدید : 5791
منتشرکننده : CarGeek
|
اجزاء و مشخصات فنی مخزن سوخت (باک) خودرو- فایل 2
5 سال پیش
9.8 مگابایت
نوع : pdf
بازدید : 4091
منتشرکننده : CarGeek
|
اجزاء و مشخصات فنی مخزن سوخت (باک) خودرو
5 سال پیش
2.54 مگابایت
نوع : pdf
بازدید : 13522
منتشرکننده : CarGeek
|
بررسی عملکرد ECU ، سنسورها و عملگرهای خودرو
5 سال پیش
2.61 مگابایت
نوع : pdf
بازدید : 9351
منتشرکننده : CarGeek
|
دستورالعمل عیب یابی کویل پراید
5 سال پیش
0.66 مگابایت
نوع : pdf
بازدید : 40152
منتشرکننده : CarGeek
|
ارائه یک پروتکل جدید مسیریابی امن مبتنی بر موقعیت گره با استفاد ه از رمزنگاری داده ها در شبکه های موردی بین خودرویی
5 سال پیش
1.69 مگابایت
نوع : pdf
بازدید : 3453
منتشرکننده : CarGeek
|
توسعه استفاده از سیستم متغییر ترمز (EBD) جهت افزایش ایمنی خودروها
5 سال پیش
0.32 مگابایت
نوع : pdf
بازدید : 3300
منتشرکننده : CarGeek
|
کتاب Remarkable Engineers: From Riquet to Shannon
5 سال پیش
2.56 مگابایت
نوع : pdf
بازدید : 3572
منتشرکننده : CarGeek
|
راهنمای آموزشی برق بیل مکانیکی کوماتسو PC220-7
5 سال پیش
13.33 مگابایت
نوع : pdf
بازدید : 25031
منتشرکننده : CarGeek
|
راهنمای آموزشی Hyundai Genesis SRS System
5 سال پیش
0.93 مگابایت
نوع : pdf
بازدید : 7660
منتشرکننده : CarGeek
|
راهنمای آموزشی Hyundai ESP MGH-40
5 سال پیش
0.92 مگابایت
نوع : pdf
بازدید : 4337
منتشرکننده : CarGeek
|
راهنمای آموزشی Hyundai Electronically Controlled On-Demand 4WD System
5 سال پیش
1.36 مگابایت
نوع : pdf
بازدید : 4251
منتشرکننده : CarGeek
|
مقاله پروتکل مسیریابی ترکیبی انتشار داده های چندرسانه ای در محیط شبکه های بین خودرویی
5 سال پیش
0.71 مگابایت
نوع : pdf
بازدید : 3508
منتشرکننده : CarGeek
|
مقاله مرور چالش های خودروهای خودران مجهز به حسگر دید
5 سال پیش
0.73 مگابایت
نوع : pdf
بازدید : 3347
منتشرکننده : CarGeek
|
مقاله بررسی و ارزیابی عملکرد خودروهای خودران و نقش آن ها در سیستم حمل و نقل هوشمند
5 سال پیش
1.14 مگابایت
نوع : pdf
بازدید : 4970
منتشرکننده : CarGeek
|
مقاله مروری بر توانایی ها، ملزومات و امکانات مورد نیاز در خودروهای خودران
5 سال پیش
1.28 مگابایت
نوع : pdf
بازدید : 3251
منتشرکننده : CarGeek
|
مقاله تاثیر خودروهای خودران در کاهش مصرف سوخت و انتشار گازهای گلخانه ای
5 سال پیش
1.24 مگابایت
نوع : pdf
بازدید : 3364
منتشرکننده : CarGeek
|
مقاله تحلیل و بررسی عملکرد سیستم های خودروهای خودران
5 سال پیش
0.49 مگابایت
نوع : pdf
بازدید : 4613
منتشرکننده : CarGeek
|
مقاله کاربرد اینترنت اشیا در توسعه شهرهای هوشمند با تاکید بر سیستم حمل و نقل هوشمند
5 سال پیش
0.75 مگابایت
نوع : pdf
بازدید : 3649
منتشرکننده : CarGeek
|
مقاله بررسی نیازمندیهای سخت افزاری و نرم افزاری در تولید خودروهای خودران
5 سال پیش
0.47 مگابایت
نوع : pdf
بازدید : 3419
منتشرکننده : CarGeek
|
مقاله طراحی خودروهای هوشمند جهت افزایش ایمنی خودرو و پیش گیری از حوادث
5 سال پیش
0.16 مگابایت
نوع : pdf
بازدید : 3961
منتشرکننده : CarGeek
|
مقاله استفاده از خودروهای خودران در خودرهای اشتراکی
5 سال پیش
0.15 مگابایت
نوع : pdf
بازدید : 3131
منتشرکننده : CarGeek
|
میزان فشار باد تایرها در محصولات ایران خودرو
5 سال پیش
0.47 مگابایت
نوع : pdf
بازدید : 24686
منتشرکننده : CarGeek
|
راهنمای سرویس و اپراتوری گریدر HG180D1 هپکو
5 سال پیش
24.84 مگابایت
نوع : pdf
بازدید : 14201
منتشرکننده : CarGeek
|
راهنمای کامل تعمیرات بلدوزر کوماتسو D155A-2
5 سال پیش
13.5 مگابایت
نوع : pdf
بازدید : 20816
منتشرکننده : CarGeek
|
آشنایی با یاتاقان ها
5 سال پیش
8.14 مگابایت
نوع : pdf
بازدید : 4422
منتشرکننده : CarGeek
|
سیستم سوخت رسانی GDI- فایل 3
5 سال پیش
2.67 مگابایت
نوع : pdf
بازدید : 4241
منتشرکننده : CarGeek
|
سیستم سوخت رسانی GDI- فایل 2
5 سال پیش
0.21 مگابایت
نوع : pdf
بازدید : 3755
منتشرکننده : CarGeek
|
سیستم سوخت رسانی GDI
5 سال پیش
1.75 مگابایت
نوع : pdf
بازدید : 4840
منتشرکننده : CarGeek
|
Bearing Failure: Causes & Cures
5 سال پیش
2.59 مگابایت
نوع : pdf
بازدید : 3511
منتشرکننده : CarGeek
|
راهنمای آسیب دیدگی های یاتاقان های تخت
5 سال پیش
5.94 مگابایت
نوع : pdf
بازدید : 4265
منتشرکننده : CarGeek
|
راهنمای نصب سیستم esp روی ترمز پژو 206
5 سال پیش
1.73 مگابایت
نوع : pdf
بازدید : 16238
منتشرکننده : CarGeek
|
دستورالعمل رفع مشکل قطع نشدن کمپرسور کولر پژو 405
5 سال پیش
0.5 مگابایت
نوع : pdf
بازدید : 12917
منتشرکننده : CarGeek
|
راهنمای تعمیرات دامپ تراک معدنی بلاز 7513
5 سال پیش
8.63 مگابایت
نوع : pdf
بازدید : 11294
منتشرکننده : CarGeek
|
دایره المعارف قطعات الکترونیک- فایل 3
5 سال پیش
68.6 مگابایت
نوع : pdf
بازدید : 4078
منتشرکننده : CarGeek
|
دایره المعارف قطعات الکترونیک- فایل 2
5 سال پیش
73.18 مگابایت
نوع : pdf
بازدید : 4844
منتشرکننده : CarGeek
|
دایره المعارف قطعات الکترونیک
5 سال پیش
28.28 مگابایت
نوع : pdf
بازدید : 9430
منتشرکننده : CarGeek
|
راهنمای آموزشی تایر خودرو
5 سال پیش
6.19 مگابایت
نوع : pdf
بازدید : 4516
منتشرکننده : CarGeek
|
راهنمای آموزشی برق بدنه چری تیگو5
5 سال پیش
6.72 مگابایت
نوع : pdf
بازدید : 4935
منتشرکننده : CarGeek
|
راهنمای جامع یاتاقان ، بلبرینگ و رولبرینگ
5 سال پیش
19.35 مگابایت
نوع : pdf
بازدید : 7662
منتشرکننده : CarGeek
|
کتاب Aerospace Engineering Desk Reference
5 سال پیش
28.25 مگابایت
نوع : pdf
بازدید : 3290
منتشرکننده : CarGeek
|
راهنمای آموزشی موتور برقی و باتری ولتاژ بالای هیوندای سوناتا هیبرید- فایل 2
5 سال پیش
4.46 مگابایت
نوع : pdf
بازدید : 5962
منتشرکننده : CarGeek
|
راهنمای آموزشی موتور برقی و باتری ولتاژ بالای هیوندای سوناتا هیبرید
5 سال پیش
2.31 مگابایت
نوع : pdf
بازدید : 7741
منتشرکننده : CarGeek
|
راهنمای سریع سرویس بلدوزر کوماتسو D155A-2
5 سال پیش
3.3 مگابایت
نوع : pdf
بازدید : 5999
منتشرکننده : CarGeek
|
راهنمای تعمیرات موتور Volvo D7D
5 سال پیش
20.51 مگابایت
نوع : pdf
بازدید : 7098
منتشرکننده : CarGeek
|
راهنمای تعمیرات موتور DEUTZ 1012 1013 2012
5 سال پیش
9.35 مگابایت
نوع : pdf
بازدید : 11028
منتشرکننده : CarGeek
|
کتاب Automotive Paint from Prep to Final Coat
5 سال پیش
31.96 مگابایت
نوع : pdf
بازدید : 3628
منتشرکننده : CarGeek
|
راهنمای آموزشی موتور هیوندای Hyundai Theta GDI
5 سال پیش
2.67 مگابایت
نوع : pdf
بازدید : 6547
منتشرکننده : CarGeek
|
راهنمای آموزشی موتور تتا2 هیوندای Hyundai Theta-II Tucsun IX35
5 سال پیش
1.17 مگابایت
نوع : pdf
بازدید : 7734
منتشرکننده : CarGeek
|
راهنمای آموزشی موتور لامبدا هیوندای Hyundai Lambda
5 سال پیش
0.98 مگابایت
نوع : pdf
بازدید : 6228
منتشرکننده : CarGeek
|
راهنمای آموزشی موتور هیوندای Hyundai Lambda Centennial Equus
5 سال پیش
1.18 مگابایت
نوع : pdf
بازدید : 5161
منتشرکننده : CarGeek
|
راهنمای آموزشی هیوندای Hyundai i20 Kappa
5 سال پیش
1.43 مگابایت
نوع : pdf
بازدید : 12894
منتشرکننده : CarGeek
|
راهنمای آموزشی موتور سری PA هیوندای Hyundai Epsilon and Common Rail U
5 سال پیش
2.63 مگابایت
نوع : pdf
بازدید : 3740
منتشرکننده : CarGeek
|
راهنمای آموزشی موتور سری FD هیوندای Hyundai Gamma and Beta and U and D
5 سال پیش
2.78 مگابایت
نوع : pdf
بازدید : 4227
منتشرکننده : CarGeek
|
راهنمای آموزشی موتور سری TQ هیوندای Hyundai C/Rail A and D4BH TCI 2.5 and Theta 2.4
5 سال پیش
2.57 مگابایت
نوع : pdf
بازدید : 3811
منتشرکننده : CarGeek
|
راهنمای آموزشی موتور Tau هیوندای Hyundai Tau Engine Centennial Equus
5 سال پیش
2.42 مگابایت
نوع : pdf
بازدید : 4196
منتشرکننده : CarGeek
|
راهنمای آموزشی موتور U-II هیوندای Hyundai i-20 U-II
5 سال پیش
1.55 مگابایت
نوع : pdf
بازدید : 4034
منتشرکننده : CarGeek
|
راهنمای آموزشی موتور سری EN هیوندای Hyundai S v-6 3.0 CRDi and Lambda v6 3.8 MPI
5 سال پیش
7.36 مگابایت
نوع : pdf
بازدید : 4097
منتشرکننده : CarGeek
|
راهنمای باز کردن داشبورد پراید
5 سال پیش
2.75 مگابایت
نوع : pdf
بازدید : 103007
منتشرکننده : CarGeek
|
راهنمای آموزشی برق خودرو سابرینا
5 سال پیش
19.5 مگابایت
نوع : pdf
بازدید : 5857
منتشرکننده : CarGeek
|
راهنمای آموزشی سیستم برق گیربکس i-shift VI2412B ولوو
5 سال پیش
1.38 مگابایت
نوع : pdf
بازدید : 8374
منتشرکننده : CarGeek
|
Volvo Gearbox VT2412B I-shift Design and Function
5 سال پیش
6.95 مگابایت
نوع : pdf
بازدید : 4277
منتشرکننده : CarGeek
|
راهنمای سوخت رسانی MVM 110 اتوماتیک چهارسیلندر
5 سال پیش
4.99 مگابایت
نوع : pdf
بازدید : 5785
منتشرکننده : CarGeek
|
شبیه سازی عدد اسپری و احتراق و بررسی شکل گیری مخلوط لایه ای هوا و سوخت در موتور پاشش مستقیم بنزینی
5 سال پیش
2.14 مگابایت
نوع : pdf
بازدید : 3550
منتشرکننده : CarGeek
|
شبیه سازی 3بعدی عملکرد و آلایندگی احتراق هیدروژن-دیزل در موتور دیزل سنگین درحالت بار کامل
5 سال پیش
1.32 مگابایت
نوع : pdf
بازدید : 3592
منتشرکننده : CarGeek
|
بررسی تجربی مشخصه های عملکردی و آلایندگی موتور تک سیلندر پژوهشی CT300 ترکیب سوز استوکیومتری با نسبت جرمی سوخت 75%بنزین 25% گاز طبیعی
5 سال پیش
0.47 مگابایت
نوع : pdf
بازدید : 3226
منتشرکننده : CarGeek
|
راهنمای دانلود ECU Valeo J34
5 سال پیش
0.33 مگابایت
نوع : pdf
بازدید : 9580
منتشرکننده : CarGeek
|
راهنمای ECU Valeo J35
5 سال پیش
0.62 مگابایت
نوع : pdf
بازدید : 12844
منتشرکننده : CarGeek
|
راهنمای فنی گیربکس اتوماتیک DAEA6F5 ایران خودرو دنا توربو
5 سال پیش
8.29 مگابایت
نوع : pdf
بازدید : 34268
منتشرکننده : CarGeek
|
مدارها و کدهای خطای عیب یابی فن خنک کننده دو دور رادیاتور موتور پراید
5 سال پیش
1 مگابایت
نوع : pdf
بازدید : 18763
منتشرکننده : CarGeek
|
انواع سنسورها
5 سال پیش
0.97 مگابایت
نوع : pdf
بازدید : 5204
منتشرکننده : CarGeek
|
آشنایی با سیستم OBD و نحوه عملکرد آن
5 سال پیش
0.35 مگابایت
نوع : pdf
بازدید : 6409
منتشرکننده : CarGeek
|
راهنمای تعمیراتی جیپ آهو و شهباز قدیمی- فایل 2
5 سال پیش
23.77 مگابایت
نوع : pdf
بازدید : 5767
منتشرکننده : CarGeek
|
راهنمای تعمیراتی جیپ آهو و شهباز قدیمی
5 سال پیش
43.11 مگابایت
نوع : pdf
بازدید : 16020
منتشرکننده : CarGeek
|
کاربرد شبکه در خودرو
5 سال پیش
9.77 مگابایت
نوع : pdf
بازدید : 4384
منتشرکننده : CarGeek
|
راهنمای تعمیر و عیب یابی گیربکس اتوماتیک 4F16 برلیانس
5 سال پیش
2.42 مگابایت
نوع : pdf
بازدید : 5513
منتشرکننده : CarGeek
|
بررسی لنت و ضخامت دیسک ترمز هیوندای آزرا و سوناتا
5 سال پیش
0.1 مگابایت
نوع : pdf
بازدید : 4539
منتشرکننده : CarGeek
|
رفع ایراد لرزش موتور TU5 پژو 206 در زمان سرد بودن
5 سال پیش
0.38 مگابایت
نوع : pdf
بازدید : 12374
منتشرکننده : CarGeek
|
جزوه کلاس آموزشی برق و مالتی پلکس ایرانی
5 سال پیش
8.07 مگابایت
نوع : pdf
بازدید : 22867
منتشرکننده : CarGeek
|
نقشه الکتریکی سیستم سوخت رسانی و جرقه Bosch M7.4.4 پژو405 و پارس
5 سال پیش
0.87 مگابایت
نوع : pdf
بازدید : 30943
منتشرکننده : CarGeek
|
راهنمای باز و بست و تعیرات پمپ تغذیه هوا پژو پارس ELX
5 سال پیش
0.27 مگابایت
نوع : pdf
بازدید : 21400
منتشرکننده : CarGeek
|
جدول حجم و نوع روغن موتور و گیربکس انواع خودروهای سایپا
5 سال پیش
1.41 مگابایت
نوع : pdf
بازدید : 78954
منتشرکننده : CarGeek
|
نکات فنی امدادخودرو پژو 405 و پارس و سمند
5 سال پیش
0.55 مگابایت
نوع : pdf
بازدید : 7215
منتشرکننده : CarGeek
|
راهنمای فنی ECU Bosch M7.9.7 سایپا X100
5 سال پیش
0.47 مگابایت
نوع : pdf
بازدید : 7882
منتشرکننده : CarGeek
|
دستورالعمل اصلاح گردگیر (کپ) لاستیکی و ترمینال فلزی شیربرقی کولر تیبا2
5 سال پیش
1.52 مگابایت
نوع : pdf
بازدید : 3826
منتشرکننده : CarGeek
|
راهنمای تعمیرات کمربندایمنی و صندلی لیفان 820
5 سال پیش
1.07 مگابایت
نوع : pdf
بازدید : 10902
منتشرکننده : CarGeek
|
راهنمای تعمیرات و عیب یابی کلاچ لیفان 820
5 سال پیش
2.48 مگابایت
نوع : pdf
بازدید : 3825
منتشرکننده : CarGeek
|
عیب یابی و تعویض رینگ چرخ و تست صحت کالیبراسیون دستگاه بالانس رینگ
5 سال پیش
0.19 مگابایت
نوع : pdf
بازدید : 6935
منتشرکننده : CarGeek
|
راهنمای تعمیرات و عیب یابی گیربکس اتوماتیک لیفان 820- فایل 2
5 سال پیش
1.02 مگابایت
نوع : pdf
بازدید : 5130
منتشرکننده : CarGeek
|
راهنمای تعمیرات و عیب یابی گیربکس اتوماتیک لیفان 820
5 سال پیش
2.29 مگابایت
نوع : pdf
بازدید : 11303
منتشرکننده : CarGeek
|
بررسی و شبیه سازی پدیده آیرودینامیک خودرو در هنگام عبور از خودرو دیگر (مانور سبقت)
5 سال پیش
1.08 مگابایت
نوع : pdf
بازدید : 3278
منتشرکننده : CarGeek
|
راهنمای تعمیرات نشانگرها، اطلاعات راننده و بوق سوزوکی کیزاشی
5 سال پیش
3.04 مگابایت
نوع : pdf
بازدید : 3368
منتشرکننده : CarGeek
|
دستورالعمل عیب یابی و تعویض نوار دور درب پراید
5 سال پیش
1.41 مگابایت
نوع : pdf
بازدید : 32660
منتشرکننده : CarGeek
|
راهنمای تعمیرات سوخت رسانی و جرقه و سیستم الکتریکی موتور سوزکی کیزاشی
5 سال پیش
6.64 مگابایت
نوع : pdf
بازدید : 3431
منتشرکننده : CarGeek
|
راهنمای فنی یونیت فن کنترل دما پژو 405
5 سال پیش
2.43 مگابایت
نوع : pdf
بازدید : 70139
منتشرکننده : CarGeek
|
روش بازدید، تخلیه و شارژ روغن گیربکس اتوماتیک
5 سال پیش
1.98 مگابایت
نوع : pdf
بازدید : 14955
منتشرکننده : CarGeek
|
نمونه سئوالات آزمون قطعه شناسی خودرو
5 سال پیش
0.22 مگابایت
نوع : pdf
بازدید : 7987
منتشرکننده : CarGeek
|
نمونه سئوالات آزمون تعمیرکار موتورسیکلت درجه 1
5 سال پیش
0.14 مگابایت
نوع : pdf
بازدید : 4819
منتشرکننده : CarGeek
|
نمونه سئوالات آزمون تعمیرکار موتورسیکلت درجه 2
5 سال پیش
0.68 مگابایت
نوع : pdf
بازدید : 5369
منتشرکننده : CarGeek
|
نمونه سئوالات ترمزهای پنوماتیکی
5 سال پیش
0.56 مگابایت
نوع : pdf
بازدید : 96938
منتشرکننده : CarGeek
|
نمونه سئوالات آزمون سیستم تعلیق خودرو (جلوبندی سازی)- فایل 3
5 سال پیش
0.41 مگابایت
نوع : pdf
بازدید : 7641
منتشرکننده : CarGeek
|
نمونه سئوالات آزمون سیستم تعلیق خودرو (جلوبندی سازی)- فایل 2
5 سال پیش
0.4 مگابایت
نوع : pdf
بازدید : 4130
منتشرکننده : CarGeek
|
نمونه سئوالات آزمون سیستم تعلیق خودرو (جلوبندی سازی)
5 سال پیش
0.4 مگابایت
نوع : pdf
بازدید : 6955
منتشرکننده : CarGeek
|
راهنمای راننده کامیون Axor 1843
5 سال پیش
7.22 مگابایت
نوع : pdf
بازدید : 32603
منتشرکننده : CarGeek
|
دفترچه راهنمای کامیون کشنده البرز T375
5 سال پیش
4.62 مگابایت
نوع : pdf
بازدید : 43046
منتشرکننده : CarGeek
|
راهنمای کامل تعمیرات فوتون تونلند
5 سال پیش
83.44 مگابایت
نوع : pdf
بازدید : 43226
منتشرکننده : CarGeek
|
نمونه سئوالات تئوری و عملی مسابقات علمی-کاربردی تعمیر موتور و برق خودرو
5 سال پیش
0.12 مگابایت
نوع : pdf
بازدید : 5122
منتشرکننده : CarGeek
|
نمونه سئوالات آزمون برق خودرو درجه 1
5 سال پیش
0.42 مگابایت
نوع : pdf
بازدید : 14664
منتشرکننده : CarGeek
|
نمونه سئوالات آزمون دوگانه سوز- فایل 4
5 سال پیش
0.12 مگابایت
نوع : pdf
بازدید : 3505
منتشرکننده : CarGeek
|
نمونه سئوالات آزمون دوگانه سوز- فایل 3
5 سال پیش
0.35 مگابایت
نوع : pdf
بازدید : 3502
منتشرکننده : CarGeek
|
نمونه سئوالات آزمون دوگانه سوز- فایل 2
5 سال پیش
0.34 مگابایت
نوع : pdf
بازدید : 3686
منتشرکننده : CarGeek
|
نمونه سئوالات آزمون دوگانه سوز
5 سال پیش
0.35 مگابایت
نوع : pdf
بازدید : 11593
منتشرکننده : CarGeek
|
آموزش استفاده از اسیلوسکوپ در تعمیرات برق خودرو
5 سال پیش
1.89 مگابایت
نوع : pdf
بازدید : 5336
منتشرکننده : CarGeek
|
جزوه تکنیک های آموزش عملی رانندگی
5 سال پیش
2.06 مگابایت
نوع : pdf
بازدید : 4847
منتشرکننده : CarGeek
|
دستورالعمل نظارت بر چگونگی فعالیت تاکسیهای اینترنتی
5 سال پیش
0.76 مگابایت
نوع : pdf
بازدید : 3152
منتشرکننده : CarGeek
|
راهنمای تعمیرات قفل مرکزی و ایموبلایزر لیفان 820
5 سال پیش
0.67 مگابایت
نوع : pdf
بازدید : 7861
منتشرکننده : CarGeek
|
راهنمای تعمیرات سیستم اطلاعات راننده (پشت آمپر و نمایشگر چندمنظوره) لیفان 820
5 سال پیش
1.66 مگابایت
نوع : pdf
بازدید : 6259
منتشرکننده : CarGeek
|
راهنمای تعمیرات سیستم صوتی و سرگرمی لیفان 820
5 سال پیش
1.03 مگابایت
نوع : pdf
بازدید : 5174
منتشرکننده : CarGeek
|
راهنمای کامل تعمیرات آریزو5
5 سال پیش
161.38 مگابایت
نوع : pdf
بازدید : 36222
منتشرکننده : CarGeek
|
فیلم و دفترچه راهنمای آموزشی مشتری هایما S7
5 سال پیش
0 مگابایت
نوع : pdf
بازدید : 3733
منتشرکننده : CarGeek
|
فیلم و دفترچه راهنمای آموزشی مشتری هایما S5
5 سال پیش
0 مگابایت
نوع : pdf
بازدید : 4301
منتشرکننده : CarGeek
|
فیلم و دفترچه راهنمای آموزشی مشتری رانا
5 سال پیش
0 مگابایت
نوع : pdf
بازدید : 3662
منتشرکننده : CarGeek
|
فیلم و دفترچه راهنمای آموزشی مشتری دنا پلاس
5 سال پیش
0 مگابایت
نوع : pdf
بازدید : 4414
منتشرکننده : CarGeek
|
فیلم و دفترچه راهنمای آموزشی مشتری H30 Cross
5 سال پیش
3.28 مگابایت
نوع : pdf
بازدید : 4524
منتشرکننده : CarGeek
|
دستورالعمل رفع ایراد عدم انطباق کانکتور کیلومتر شمار تیبا2 و روشن شدن چراغ EBD بجای ABS
5 سال پیش
2.2 مگابایت
نوع : pdf
بازدید : 8817
منتشرکننده : CarGeek
|
دستورالعمل رفع ایراد نفوذ آب به داخل CCN سمند مالتی پلکس
5 سال پیش
0.69 مگابایت
نوع : pdf
بازدید : 9072
منتشرکننده : CarGeek
|
راهنمای کنترل و اصلاح پیکربندی سمند مالتی پلکس SMS
5 سال پیش
0.34 مگابایت
نوع : pdf
بازدید : 5271
منتشرکننده : CarGeek
|
معرفی نودهای سیستم مالتی پلکس SMS سمند و سورن
5 سال پیش
0.42 مگابایت
نوع : pdf
بازدید : 7542
منتشرکننده : CarGeek
|
راهنمای پیکربندی نوع ECU در خودرو Dena SMS MUX Bosch ME17
5 سال پیش
0.3 مگابایت
نوع : pdf
بازدید : 5272
منتشرکننده : CarGeek
|
اصول عملکرد سیستم کروزکنترل ایران خودرو
5 سال پیش
2.09 مگابایت
نوع : pdf
بازدید : 6856
منتشرکننده : CarGeek
|
راهنمای تعریف کلید خودرو H30 Cross
5 سال پیش
0.76 مگابایت
نوع : pdf
بازدید : 6514
منتشرکننده : CarGeek
|
بررسی سیستم های VVT و VIS در خودرو
5 سال پیش
4.88 مگابایت
نوع : pdf
بازدید : 9321
منتشرکننده : CarGeek
|
راهنمای تعمیرات ECU زیمنس ریو
5 سال پیش
1.93 مگابایت
نوع : pdf
بازدید : 17477
منتشرکننده : CarGeek
|
معرفی سیستم ترمز ABS با مدل Bosch ABS8 و مدل TEVES MK70 پراید
5 سال پیش
0.24 مگابایت
نوع : pdf
بازدید : 9826
منتشرکننده : CarGeek
|
معرفی قطعات EMS جدید SSAT سازه پویش سایپا X100 (پراید)
5 سال پیش
1.47 مگابایت
نوع : pdf
بازدید : 7053
منتشرکننده : CarGeek
|
دستورالعمل شستشوی ریل سوخت وانت نیسان دوگانه سوز
5 سال پیش
1.21 مگابایت
نوع : pdf
بازدید : 12911
منتشرکننده : CarGeek
|
اطلاعیه جابجایی سوکت های انژکتور در دسته سیم انژکتور جهت رفع ایراد MisFiring
5 سال پیش
0.56 مگابایت
نوع : pdf
بازدید : 39113
منتشرکننده : CarGeek
|
راهنمای تعمیرات سیستم خنک کاری موتور لیفان 820
5 سال پیش
1.56 مگابایت
نوع : pdf
بازدید : 7788
منتشرکننده : CarGeek
|
راهنمای تعمیرات سیستم روغنکاری لیفان 820
5 سال پیش
0.9 مگابایت
نوع : pdf
بازدید : 3225
منتشرکننده : CarGeek
|
راهنمای تعمیرات مکانیکی موتور لیفان 820
5 سال پیش
6.03 مگابایت
نوع : pdf
بازدید : 7501
منتشرکننده : CarGeek
|
اطلاعات عمومی تعمیرات لیفان 820
5 سال پیش
1.01 مگابایت
نوع : pdf
بازدید : 3614
منتشرکننده : CarGeek
|
راهنمای تنظیمات خودرو پژو 206 مالتی پلکس
5 سال پیش
0.25 مگابایت
نوع : pdf
بازدید : 14991
منتشرکننده : CarGeek
|
Lithium-Ion Batteries A Machine-Generated Summary of Current Research
5 سال پیش
4.99 مگابایت
نوع : pdf
بازدید : 3085
منتشرکننده : CarGeek
|
پاسخ به 20 سئوال متداول درباره شمع خودرو
5 سال پیش
7.02 مگابایت
نوع : pdf
بازدید : 4867
منتشرکننده : CarGeek
|
نحوه نصب ایکودیاگ در ویندوز7
5 سال پیش
1.7 مگابایت
نوع : pdf
بازدید : 10847
منتشرکننده : CarGeek
|
چک لیست روزانه کامیون- فایل 2
5 سال پیش
0.3 مگابایت
نوع : pdf
بازدید : 4116
منتشرکننده : CarGeek
|
چک لیست روزانه کامیون
5 سال پیش
0.1 مگابایت
نوع : pdf
بازدید : 8589
منتشرکننده : CarGeek
|
مشخصات فنی و دفرچه راهنمای کامیونت های الوند 6.5 و 8.5 تن (فوتون)
5 سال پیش
2.56 مگابایت
نوع : pdf
بازدید : 40715
منتشرکننده : CarGeek
|
مشخصات فنی و دفترچه راهنمای راننده کامیون کمپرسی KD420 و کشنده KT420 کاوه- فایل 2
5 سال پیش
3.83 مگابایت
نوع : pdf
بازدید : 13046
منتشرکننده : CarGeek
|
مشخصات فنی و دفترچه راهنمای راننده کامیون کمپرسی KD420 و کشنده KT420 کاوه
5 سال پیش
3.62 مگابایت
نوع : pdf
بازدید : 13575
منتشرکننده : CarGeek
|
راهنمای تعمیرات و عیب یابی سیستم ترمز ABS آریسان
5 سال پیش
0.99 مگابایت
نوع : pdf
بازدید : 10792
منتشرکننده : CarGeek
|
راهنمای تعمیرات سیستم کویل و جرقه لیفان 820
5 سال پیش
0.57 مگابایت
نوع : pdf
بازدید : 4453
منتشرکننده : CarGeek
|
راهنمای تعمیرات مسیر سوخت رسانی (باک،پمپ بنزین،فیلتر،لوله ها،کنیستر) لیفان 820
5 سال پیش
1.76 مگابایت
نوع : pdf
بازدید : 7166
منتشرکننده : CarGeek
|
راهنمای تعمیرات سیستم کنترل آلایندگی لیفان 820
5 سال پیش
1.71 مگابایت
نوع : pdf
بازدید : 4853
منتشرکننده : CarGeek
|
راهنمای تعمیرات سیستم کنترل موتور لیفان 820
5 سال پیش
2.82 مگابایت
نوع : pdf
بازدید : 5828
منتشرکننده : CarGeek
|
راهنمای تعمیرات سیستم سوخت رسانی لیفان 820
5 سال پیش
1.35 مگابایت
نوع : pdf
بازدید : 4061
منتشرکننده : CarGeek
|
راهنمای آموزشی موتور XU7 هشت و 16سوپاپ پژو 405 و سمند و پارس
5 سال پیش
2.55 مگابایت
نوع : pdf
بازدید : 28241
منتشرکننده : CarGeek
|
آموزش نحوه استفاده از ابزار مخصوص در تعمیرات گیربکس اتوماتیک خودروهای کوییک و ساینا
5 سال پیش
4.59 مگابایت
نوع : pdf
بازدید : 8411
منتشرکننده : CarGeek
|
TIBA Injection repair manual
5 سال پیش
4.91 مگابایت
نوع : pdf
بازدید : 3676
منتشرکننده : CarGeek
|
لیست، تصویر و شماره فنی قطعات تیبا
5 سال پیش
8.07 مگابایت
نوع : pdf
بازدید : 25519
منتشرکننده : CarGeek
|
جدول زوایای فرمان و نوع سیستم تعلیق خودروهای سایپا
5 سال پیش
1.08 مگابایت
نوع : pdf
بازدید : 6140
منتشرکننده : CarGeek
|
دفترچه راهنمای تویوتا C-HR هیبرید
5 سال پیش
14.56 مگابایت
نوع : pdf
بازدید : 7396
منتشرکننده : CarGeek
|
دستورالعمل بازدید و تعویض رولبرینگ عقب تیبا
5 سال پیش
0.49 مگابایت
نوع : pdf
بازدید : 3920
منتشرکننده : CarGeek
|
دستورالعمل عیب یابی و تعویض ریموت و رسیور سایپا 132 و تیبا و تیبا2
5 سال پیش
2.11 مگابایت
نوع : pdf
بازدید : 16956
منتشرکننده : CarGeek
|
راهنمای آموزشی سیستم های الکترونیکی ترمز رنو
5 سال پیش
21.3 مگابایت
نوع : pdf
بازدید : 4950
منتشرکننده : CarGeek
|
معرفی سیستم سوخت رسانی بوش بنزینی و بوش پایه گازسوز پراید
5 سال پیش
0.54 مگابایت
نوع : pdf
بازدید : 9452
منتشرکننده : CarGeek
|
راهنمای سیستم مدیریت موتور UAES خودرو MVM315
5 سال پیش
24.66 مگابایت
نوع : pdf
بازدید : 11789
منتشرکننده : CarGeek
|
راهنمای سیستم سوخت رسانی و انژکتور H30 Cross
5 سال پیش
2.31 مگابایت
نوع : pdf
بازدید : 7733
منتشرکننده : CarGeek
|
آشنایی با قطعات و سیستم مدیریت موتور BOSCH ME 17.9.71 موتور TU5 پژو 206 و پژو207 و پژو405 و پژو پارس
5 سال پیش
2.74 مگابایت
نوع : pdf
بازدید : 9971
منتشرکننده : CarGeek
|
معرفی و نحوه استفاده از دستگاه آنالیز گازهای خروجی اگزوز (چهارگاز و پنج گاز)
5 سال پیش
0.36 مگابایت
نوع : pdf
بازدید : 4459
منتشرکننده : CarGeek
|
معرفی سیستم MGH-60 ترمز ABS پراید
5 سال پیش
0.2 مگابایت
نوع : pdf
بازدید : 9386
منتشرکننده : CarGeek
|
دستورالعمل استفاده از واشر صداگیر پلوس برای رفع ایراد صدای تقه در شروع حرکت
5 سال پیش
0.89 مگابایت
نوع : pdf
بازدید : 17356
منتشرکننده : CarGeek
|
راهنمای تعویض پیچ براکت اکسل عقب تیبا و ساینا
5 سال پیش
1.64 مگابایت
نوع : pdf
بازدید : 12393
منتشرکننده : CarGeek
|
راهنمای درجه بندی روغن موتور
5 سال پیش
1.25 مگابایت
نوع : pdf
بازدید : 4032
منتشرکننده : CarGeek
|
جزئیات تغییرات گیربکس های جدید (طرح دوبل برنجی ND1) در تیبا ، ساینا و کوییک (X200)
5 سال پیش
0.64 مگابایت
نوع : pdf
بازدید : 6318
منتشرکننده : CarGeek
|
راهنمای عیب یابی و تعویض تایر برلیانس
5 سال پیش
0.64 مگابایت
نوع : pdf
بازدید : 8394
منتشرکننده : CarGeek
|
راهنمای تعویض مجموعه صندلی برلیانس
5 سال پیش
1.06 مگابایت
نوع : pdf
بازدید : 8773
منتشرکننده : CarGeek
|
راهنمای سیستم سوخت رسانی بوش پایه گازسوز پراید
5 سال پیش
7.26 مگابایت
نوع : pdf
بازدید : 9008
منتشرکننده : CarGeek
|
رفع ایراد جوش آوردن خودرو با اصلاح دسته سیم باتری کوییک و ساینا اتوماتیک
5 سال پیش
2.59 مگابایت
نوع : pdf
بازدید : 6707
منتشرکننده : CarGeek
|
شناسایی و رفع ایراد اخلال در عملکرد ساعت (نمایشگر چندمنظوره) ساخت کروز ساینا
5 سال پیش
2.74 مگابایت
نوع : pdf
بازدید : 36806
منتشرکننده : CarGeek
|
Securing Self Driving Cars
5 سال پیش
1.78 مگابایت
نوع : pdf
بازدید : 3295
منتشرکننده : CarGeek
|
OCTANE: An Extensible Open Source Car Security Testbed
5 سال پیش
0.47 مگابایت
نوع : pdf
بازدید : 3596
منتشرکننده : CarGeek
|
راهنمای مدارات الکتریکی سمند معمولی
5 سال پیش
23.54 مگابایت
نوع : pdf
بازدید : 52120
منتشرکننده : CarGeek
|
عیب یابی و رگلاژ سوئیچ پدال ترمز ساینا و کوییک اتوماتیک (چراغ چک با کدخطا P0504)
5 سال پیش
0.84 مگابایت
نوع : pdf
بازدید : 15306
منتشرکننده : CarGeek
|
روش بروزرسانی دستگاه عیب یابی سیار سایپا
5 سال پیش
0.21 مگابایت
نوع : pdf
بازدید : 5404
منتشرکننده : CarGeek
|
راهنمای مدارات الکتریکی پراید
5 سال پیش
20.14 مگابایت
نوع : pdf
بازدید : 31960
منتشرکننده : CarGeek
|
راهنمای میل فرمان عمودی پراید
5 سال پیش
0.24 مگابایت
نوع : pdf
بازدید : 8357
منتشرکننده : CarGeek
|
راهنمای سیلندر ترمز (کالیپر) پراید
5 سال پیش
0.62 مگابایت
نوع : pdf
بازدید : 24452
منتشرکننده : CarGeek
|
راهنمای بوستر و پمپ ترمز پراید
5 سال پیش
1.09 مگابایت
نوع : pdf
بازدید : 23958
منتشرکننده : CarGeek
|
راهنمای مدارات الکتریکی فن خنک کننده دو دور و تک دور پراید
5 سال پیش
1.22 مگابایت
نوع : pdf
بازدید : 55313
منتشرکننده : CarGeek
|
راهنمای عیب یابی و تعویض شیشه بالابر برقی پراید
5 سال پیش
0.68 مگابایت
نوع : pdf
بازدید : 58813
منتشرکننده : CarGeek
|
راهنمای عیب یابی و تعویض رادیاتور پراید
5 سال پیش
0.61 مگابایت
نوع : pdf
بازدید : 12923
منتشرکننده : CarGeek
|
دستورالعمل عیب یابی و تعویض کمک فنر عقب (تک جداره گازی) پراید
5 سال پیش
0.72 مگابایت
نوع : pdf
بازدید : 7147
منتشرکننده : CarGeek
|
راهنمای کولر پراید
5 سال پیش
0.56 مگابایت
نوع : pdf
بازدید : 14915
منتشرکننده : CarGeek
|
راهنمای تجهیزات تعمیرگاهی و روش اجرایی نگه داری و تعمیرات
5 سال پیش
11.05 مگابایت
نوع : pdf
بازدید : 4902
منتشرکننده : CarGeek
|
دستورالعمل تطبیق کلاچ های گیربکس CVT کوییک و ساینا اتوماتیک
5 سال پیش
0.52 مگابایت
نوع : pdf
بازدید : 9526
منتشرکننده : CarGeek
|
دستورالعمل تعویض ترموستات و رفع یخ زدگی هسته اواپراتور کولر ساینا
5 سال پیش
1.21 مگابایت
نوع : pdf
بازدید : 41301
منتشرکننده : CarGeek
|
معرفی تغییرات و بهبود عملکرد سیستم گیربکس دوبل برنجی (ND1) و گیربکس بهبودیافته (ND2)
5 سال پیش
6.77 مگابایت
نوع : pdf
بازدید : 6501
منتشرکننده : CarGeek
|
کتاب راهنمای آتش نشان داوطلب
5 سال پیش
2.5 مگابایت
نوع : pdf
بازدید : 6229
منتشرکننده : CarGeek
|
آشنایی با کیسه هوا خودرو (Airbag)
5 سال پیش
0.56 مگابایت
نوع : pdf
بازدید : 3615
منتشرکننده : CarGeek
|
راهنمای تصویری لیست و شماره فنی قطعات نیسان سرانزا
5 سال پیش
24.85 مگابایت
نوع : pdf
بازدید : 8076
منتشرکننده : CarGeek
|
طریقه تست قطعات الکترونیکی
5 سال پیش
0.44 مگابایت
نوع : pdf
بازدید : 6709
منتشرکننده : CarGeek
|
آشنایی با تغییرات گیربکس جدید (طرح بهبود کلاچ ND2) در خودروهای گروه X200 (تیبا،ساینا،کوییک)
5 سال پیش
1.17 مگابایت
نوع : pdf
بازدید : 24957
منتشرکننده : CarGeek
|
کتاب درسی تعمیر سیستم ترمز، تعلیق و فرمان
5 سال پیش
5.9 مگابایت
نوع : pdf
بازدید : 8990
منتشرکننده : CarGeek
|
راهنمای آموزشی مدیریت موتور، سوخت رسانی، جرقه و کنترل آلایندگی رنو
5 سال پیش
19.89 مگابایت
نوع : pdf
بازدید : 4910
منتشرکننده : CarGeek
|
راهنمای کدهای خطا ECU غرب استیل
5 سال پیش
0.78 مگابایت
نوع : pdf
بازدید : 19740
منتشرکننده : CarGeek
|
عیب یابی صحیح سنسور اکسیژن پراید و تیبا و ساینا و کوییک و زامیاد
5 سال پیش
0.59 مگابایت
نوع : pdf
بازدید : 23860
منتشرکننده : CarGeek
|
فیلم آموزشی و کتاب تکنولوژی انتقال قدرت
5 سال پیش
4.25 مگابایت
نوع : pdf
بازدید : 4041
منتشرکننده : CarGeek
|
جزوه آموزشی سیستم CNG پراید
5 سال پیش
3.22 مگابایت
نوع : pdf
بازدید : 13022
منتشرکننده : CarGeek
|
راهنمای تعمیرات و عیب یابی ترمز ABS MANDO پژو405، پارس، سمند، دنا و دنا پلاس
5 سال پیش
11.26 مگابایت
نوع : pdf
بازدید : 13270
منتشرکننده : CarGeek
|
راهنمای ارتباط با صفحه کیلومتر از طریق پروتکل MBUS با TNM
5 سال پیش
3.21 مگابایت
نوع : pdf
بازدید : 12707
منتشرکننده : CarGeek
|
راهنمای تعمیرات بدنه و تزئینات ساینا اتوماتیک
5 سال پیش
20.99 مگابایت
نوع : pdf
بازدید : 12701
منتشرکننده : CarGeek
|
دستورالعمل تنظیم و رگلاژ کابل کلاچ پراید، تیبا، ساینا، کوییک
5 سال پیش
3.29 مگابایت
نوع : pdf
بازدید : 47959
منتشرکننده : CarGeek
|
لیست قطعات اواپراتور و بخاری سایپا پراید ، تیبا ، ساینا ، کوییک
5 سال پیش
0.29 مگابایت
نوع : pdf
بازدید : 15987
منتشرکننده : CarGeek
|
راهنمای آموزشی انبارگردانی، کنترل موجودی و سفارشات
5 سال پیش
0.76 مگابایت
نوع : pdf
بازدید : 5509
منتشرکننده : CarGeek
|
عیوب شمع و دلایل آن ها
5 سال پیش
3.84 مگابایت
نوع : pdf
بازدید : 4658
منتشرکننده : CarGeek
|
Design of Automotive Engines (Kolchin-Demidov)
5 سال پیش
18.3 مگابایت
نوع : pdf
بازدید : 3734
منتشرکننده : CarGeek
|
راهنمای آموزشی بازرسی مراحل پیش و پس از تبدیل CNG
5 سال پیش
1.04 مگابایت
نوع : pdf
بازدید : 3649
منتشرکننده : CarGeek
|
راهنمای آموزشی بازرسی مخازن CNG
5 سال پیش
1.92 مگابایت
نوع : pdf
بازدید : 5276
منتشرکننده : CarGeek
|
راهنمای کامل پایه های BSI و BM34 پژو 206- فایل 2
5 سال پیش
0.36 مگابایت
نوع : pdf
بازدید : 71097
منتشرکننده : CarGeek
|
راهنمای کامل پایه های BSI و BM34 پژو 206
5 سال پیش
0.56 مگابایت
نوع : pdf
بازدید : 7804
منتشرکننده : CarGeek
|
راهنمای آموزشی سیستم عیب یاب Borneo3 و CLIP رنو
5 سال پیش
6.79 مگابایت
نوع : pdf
بازدید : 4678
منتشرکننده : CarGeek
|
راهنمای اطلاعات عمومی تعمیرات سراتو
5 سال پیش
1.93 مگابایت
نوع : pdf
بازدید : 4671
منتشرکننده : CarGeek
|
راهنمای تعمیرات و سرویس سیستم SRS و پیش کشنده سراتو
5 سال پیش
3.88 مگابایت
نوع : pdf
بازدید : 3594
منتشرکننده : CarGeek
|
راهنمای نگه داری پیکاپ ریچ
5 سال پیش
13.2 مگابایت
نوع : pdf
بازدید : 5147
منتشرکننده : CarGeek
|
راهنمای تعمیرات و سرویس فرمان الکتریکی چانگان CS35
5 سال پیش
2.03 مگابایت
نوع : pdf
بازدید : 8335
منتشرکننده : CarGeek
|
راهنمای تکمیلی تعمیرات موتور خودرو چانگان CS35 و EADO
5 سال پیش
7.08 مگابایت
نوع : pdf
بازدید : 11070
منتشرکننده : CarGeek
|
نحوه بررسی دقیق و اصلاح علت خطای Miss Fire
5 سال پیش
2.62 مگابایت
نوع : pdf
بازدید : 15250
منتشرکننده : CarGeek
|
معرفی سیستم انتقال قدرت دابل کلاچ
5 سال پیش
0.46 مگابایت
نوع : pdf
بازدید : 6074
منتشرکننده : CarGeek
|
راهنمای عیب یابی و تعویض فنرلول و کمک فنر عقب برلیانس H200/H300/Cross- فایل 2
5 سال پیش
0.15 مگابایت
نوع : pdf
بازدید : 3660
منتشرکننده : CarGeek
|
راهنمای عیب یابی و تعویض فنرلول و کمک فنر عقب برلیانس H200/H300/Cross
5 سال پیش
0.22 مگابایت
نوع : pdf
بازدید : 7469
منتشرکننده : CarGeek
|
دیکشنری لغات و اصطلاحات پرکاربرد انگلیسی/فارسی مکانیک
5 سال پیش
0.55 مگابایت
نوع : pdf
بازدید : 11672
منتشرکننده : CarGeek
|
راهنمای عیب یابی و پیکربندی سیستم مالتی پلکس SMS سمند با ایکودیاگ
5 سال پیش
2.63 مگابایت
نوع : pdf
بازدید : 6291
منتشرکننده : CarGeek
|
راهنمای تعمیرات و کدهای خطای سیستم های الکتریکی مزدا3- فایل 2
5 سال پیش
12.89 مگابایت
نوع : pdf
بازدید : 9544
منتشرکننده : CarGeek
|
راهنمای تعمیرات و کدهای خطای سیستم های الکتریکی مزدا3
5 سال پیش
7.29 مگابایت
نوع : pdf
بازدید : 13695
منتشرکننده : CarGeek
|
جزوه دوره آموزش گارانتی ایساکو- فایل 2
5 سال پیش
0.71 مگابایت
نوع : pdf
بازدید : 3138
منتشرکننده : CarGeek
|
جزوه دوره آموزش گارانتی ایساکو
5 سال پیش
0.73 مگابایت
نوع : pdf
بازدید : 6127
منتشرکننده : CarGeek
|
راهنمای تعمیرات موتور دوو سیلو
5 سال پیش
8.59 مگابایت
نوع : pdf
بازدید : 47050
منتشرکننده : CarGeek
|
دستورالعمل عیب یابی و تعویض قطعات کولر برلیانس
5 سال پیش
0.99 مگابایت
نوع : pdf
بازدید : 11268
منتشرکننده : CarGeek
|
دستورالعمل عیب یابی و تعویض دینام آلترناتور برلیانس
5 سال پیش
0.6 مگابایت
نوع : pdf
بازدید : 6312
منتشرکننده : CarGeek
|
دستورالعمل عیب یابی و تعویض استارتر برلیانس
5 سال پیش
0.73 مگابایت
نوع : pdf
بازدید : 4893
منتشرکننده : CarGeek
|
مقدمه ای بر سیستم انتقال قدرت دستی اتوماتیک شده (AMT)
5 سال پیش
0.32 مگابایت
نوع : pdf
بازدید : 6825
منتشرکننده : CarGeek
|
جزوه آموزشی سیستم صفحه نمایش Head Up Display پژو 508
5 سال پیش
1.22 مگابایت
نوع : pdf
بازدید : 4059
منتشرکننده : CarGeek
|
راهنمای تعمیرات و عیب یابی موتور TU5-JP4 پژو405، پارس و سمند
5 سال پیش
9.37 مگابایت
نوع : pdf
بازدید : 14438
منتشرکننده : CarGeek
|
کتاب درسی کاربرد و سرویس تراکتور
5 سال پیش
4.05 مگابایت
نوع : pdf
بازدید : 4120
منتشرکننده : CarGeek
|
راهنمای تعمیرات و عیب یابی تهویه مطبوع H30 Cross
5 سال پیش
2.56 مگابایت
نوع : pdf
بازدید : 14756
منتشرکننده : CarGeek
|
چک لیست عیب یابی کلاچ و گیربکس دستی
5 سال پیش
0.19 مگابایت
نوع : pdf
بازدید : 5401
منتشرکننده : CarGeek
|
کتاب تعمیر موتور و سیستم های مکانیکی تراکتور
5 سال پیش
13.08 مگابایت
نوع : pdf
بازدید : 18259
منتشرکننده : CarGeek
|
کتاب راهنمای تراکتورهای New Holland
5 سال پیش
34.38 مگابایت
نوع : pdf
بازدید : 18143
منتشرکننده : CarGeek
|
دفترچه راهنمای ون گلدن دراگون نارون
5 سال پیش
1.75 مگابایت
نوع : pdf
بازدید : 19765
منتشرکننده : CarGeek
|
معرفی اجزاء و سیستم جذب بخارات بنزین (کنیستر) روآ OHV
5 سال پیش
1.05 مگابایت
نوع : pdf
بازدید : 20763
منتشرکننده : CarGeek
|
راهنمای تعمیرات سیستم بخاری و کولر خودروی چیرمن
5 سال پیش
12.72 مگابایت
نوع : pdf
بازدید : 5136
منتشرکننده : CarGeek
|
راهنمای تعمیرات ترمز هیدرولیکی و ضدقفل خودروی چیرمن
5 سال پیش
15.6 مگابایت
نوع : pdf
بازدید : 4017
منتشرکننده : CarGeek
|
راهنمای تعمیرات فرمان هیدرولیک خودروی چیرمن
5 سال پیش
11.55 مگابایت
نوع : pdf
بازدید : 3881
منتشرکننده : CarGeek
|
راهنمای تعمیرات تعلیق، جلوبندی رینگ و لاستیک خودروی چیرمن
5 سال پیش
26.42 مگابایت
نوع : pdf
بازدید : 5762
منتشرکننده : CarGeek
|
راهنمای تعمیرات اکسل عقب و میل گاردان خودروی چیرمن
5 سال پیش
2.7 مگابایت
نوع : pdf
بازدید : 4263
منتشرکننده : CarGeek
|
راهنمای تعمیرات کمربند ایمنی و کیسه هوای خودرو چیرمن
5 سال پیش
16.52 مگابایت
نوع : pdf
بازدید : 8326
منتشرکننده : CarGeek
|
راهنمای تعمیرات گاردان کاروان
5 سال پیش
0.38 مگابایت
نوع : pdf
بازدید : 4304
منتشرکننده : CarGeek
|
راهنمای تعمیرات سیستم سوخت رسانی کاروان
5 سال پیش
1.33 مگابایت
نوع : pdf
بازدید : 7070
منتشرکننده : CarGeek
|
راهنمای تعمیرات سیستم فرمان کاروان
5 سال پیش
0.77 مگابایت
نوع : pdf
بازدید : 4955
منتشرکننده : CarGeek
|
راهنمای تعمیرات موتور کاروان
5 سال پیش
2.71 مگابایت
نوع : pdf
بازدید : 9264
منتشرکننده : CarGeek
|
راهنمای تعمیرات دیفرانسیل کاروان
5 سال پیش
1.22 مگابایت
نوع : pdf
بازدید : 5631
منتشرکننده : CarGeek
|
راهنمای تعمیرات کلاچ و گیربکس کاروان
5 سال پیش
1.93 مگابایت
نوع : pdf
بازدید : 4628
منتشرکننده : CarGeek
|
راهنمای تعمیرات سیستم خنک کاری، روغن کاری و اگزوز کاروان
5 سال پیش
1.08 مگابایت
نوع : pdf
بازدید : 4695
منتشرکننده : CarGeek
|
راهنمای تعمیرات سیستم تهویه مطبوع کاروان
5 سال پیش
2.75 مگابایت
نوع : pdf
بازدید : 6766
منتشرکننده : CarGeek
|
راهنمای تعمیرات ترمز کاروان
5 سال پیش
1.87 مگابایت
نوع : pdf
بازدید : 5549
منتشرکننده : CarGeek
|
راهنمای تعمیرات بخاری دوم (درجا) کاروان
5 سال پیش
0.63 مگابایت
نوع : pdf
بازدید : 9147
منتشرکننده : CarGeek
|
راهنمای تعمیرات بدنه کاروان
5 سال پیش
4.83 مگابایت
نوع : pdf
بازدید : 3548
منتشرکننده : CarGeek
|
راهنمای تعمیرات تزئینات داخلی کاروان
5 سال پیش
1.85 مگابایت
نوع : pdf
بازدید : 5795
منتشرکننده : CarGeek
|
راهنمای تعمیرات تعلیق جلو و عقب کاروان
5 سال پیش
2.17 مگابایت
نوع : pdf
بازدید : 8504
منتشرکننده : CarGeek
|
جزوه آموزشی مشتری مداری و مهارت های ارتباطی
5 سال پیش
0.9 مگابایت
نوع : pdf
بازدید : 6063
منتشرکننده : CarGeek
|
جزوه آموزشی ISO 9001 - 2015
5 سال پیش
12.56 مگابایت
نوع : pdf
بازدید : 10851
منتشرکننده : CarGeek
|
جزوه آموزشی اصول و فنون مذاکره
5 سال پیش
2.17 مگابایت
نوع : pdf
بازدید : 6656
منتشرکننده : CarGeek
|
دستورالعمل عیب یابی و تعویض سیبک بیرونی فرمان سایپا X100وX200
5 سال پیش
1.16 مگابایت
نوع : pdf
بازدید : 7004
منتشرکننده : CarGeek
|
راهنمای آموزشی نظام آراستگی تعمیرگاه
5 سال پیش
1.11 مگابایت
نوع : pdf
بازدید : 4216
منتشرکننده : CarGeek
|
دفترچه راهنمای راننده کامیون های ولوو
5 سال پیش
5.64 مگابایت
نوع : pdf
بازدید : 15806
منتشرکننده : CarGeek
|
راهنمای آموزشی سیستم ترمزگیری ضدقفل ABS
5 سال پیش
10.58 مگابایت
نوع : pdf
بازدید : 9527
منتشرکننده : CarGeek
|
معرفی سیستم های ایمنی غیرفعال گروه پراید X100
5 سال پیش
0.57 مگابایت
نوع : pdf
بازدید : 4083
منتشرکننده : CarGeek
|
راهنمای تعمیرات و وسرویس کیسه هوا (ایربگ) پراید X100
5 سال پیش
8.69 مگابایت
نوع : pdf
بازدید : 6535
منتشرکننده : CarGeek
|
فلوچارت عیب یابی گیرکردن کلید داخل مغزی سوئیچ
5 سال پیش
0.55 مگابایت
نوع : pdf
بازدید : 10059
منتشرکننده : CarGeek
|
جزوه آموزشی سوزوکی گرندویتارا فیس لیفت
5 سال پیش
1.43 مگابایت
نوع : pdf
بازدید : 3206
منتشرکننده : CarGeek
|
Turbocharger Matching Methodology for Improved Exhaust Energy Recovery
5 سال پیش
0.51 مگابایت
نوع : pdf
بازدید : 3198
منتشرکننده : CarGeek
|
راهنمای آموزشی ایمنی و بهداشت محیط کار
5 سال پیش
0.88 مگابایت
نوع : pdf
بازدید : 4148
منتشرکننده : CarGeek
|
فلوچارت عیب یابی ترک شیشه جلو خودرو
5 سال پیش
0.52 مگابایت
نوع : pdf
بازدید : 7712
منتشرکننده : CarGeek
|
فلوچارت عیب یابی زوزه فن بخاری
5 سال پیش
0.43 مگابایت
نوع : pdf
بازدید : 11155
منتشرکننده : CarGeek
|
راهنمای تعمیرات و سرویس تجهیزات الکتریکی سایپا 132
5 سال پیش
3.05 مگابایت
نوع : pdf
بازدید : 5066
منتشرکننده : CarGeek
|
راهنمای تعمیرات تجهیزات الکتریکی پراید 141
5 سال پیش
3.08 مگابایت
نوع : pdf
بازدید : 6376
منتشرکننده : CarGeek
|
راهنمای تعمیرات مدارهای الکتریکی پراید 141
5 سال پیش
6.38 مگابایت
نوع : pdf
بازدید : 16805
منتشرکننده : CarGeek
|
راهنمای گیربکس اتوماتیک AL4 پژو 206
5 سال پیش
2.1 مگابایت
نوع : pdf
بازدید : 10857
منتشرکننده : CarGeek
|
فلوچارت عیب یابی برف پاک کن خودرو خوب عمل نمی کند
5 سال پیش
0.68 مگابایت
نوع : pdf
بازدید : 10346
منتشرکننده : CarGeek
|
جزوه معرفی انواع پمپ
5 سال پیش
2.94 مگابایت
نوع : pdf
بازدید : 6284
منتشرکننده : CarGeek
|
لغت نامه انگلیسی اصطلاحات صنعت خودرو
5 سال پیش
0.52 مگابایت
نوع : pdf
بازدید : 8506
منتشرکننده : CarGeek
|
جزوه درسی سوخت و احتراق
5 سال پیش
2.78 مگابایت
نوع : pdf
بازدید : 10489
منتشرکننده : CarGeek
|
جزوه آموزشی برق چری تیگو5
5 سال پیش
7.28 مگابایت
نوع : pdf
بازدید : 19866
منتشرکننده : CarGeek
|
جزوه آموزشی برق 405 ، پارس ، RD ، سمند و سورن ، CEC ، آریسان
5 سال پیش
36.52 مگابایت
نوع : pdf
بازدید : 25575
منتشرکننده : CarGeek
|
روش نصب سنسور دنده عقب سراتو
5 سال پیش
2.45 مگابایت
نوع : pdf
بازدید : 5738
منتشرکننده : CarGeek
|
راهنمای فن خنک کننده و فلپ های کنترلی رنو کپچر
5 سال پیش
0.85 مگابایت
نوع : pdf
بازدید : 6702
منتشرکننده : CarGeek
|
نحوه رگلاژ ترمزدستی خودروهای برلیانس H300
5 سال پیش
0.71 مگابایت
نوع : pdf
بازدید : 10181
منتشرکننده : CarGeek
|
روش رفع ایراد کپ کردن موتور در خودروهای با EMS SSAT
5 سال پیش
0.57 مگابایت
نوع : pdf
بازدید : 8533
منتشرکننده : CarGeek
|
راهنمای تعمیرات اکسل جلو تندر90
5 سال پیش
2.54 مگابایت
نوع : pdf
بازدید : 5147
منتشرکننده : CarGeek
|
راهنمای تعمیرات موتور 4G6 میتسوبیشی گالانت و لنسر
5 سال پیش
4.75 مگابایت
نوع : pdf
بازدید : 21591
منتشرکننده : CarGeek
|
تحقیق گازسوز کردن خودرو
5 سال پیش
1.45 مگابایت
نوع : pdf
بازدید : 4669
منتشرکننده : CarGeek
|
جزوه سیستم سوخت رسانی و برق و انژکتور خودرو
5 سال پیش
4.08 مگابایت
نوع : pdf
بازدید : 17873
منتشرکننده : CarGeek
|
جزوه راهنمای سیستم سوخت رسانی بنزینی کاربراتوری
5 سال پیش
6.23 مگابایت
نوع : pdf
بازدید : 9156
منتشرکننده : CarGeek
|
ساختار ایستگاه های سوخت رسانی CNG
5 سال پیش
1.14 مگابایت
نوع : pdf
بازدید : 4249
منتشرکننده : CarGeek
|
تشریح ریمپ ECU و شرح Remap ایسیو ساژم S2000
5 سال پیش
5.74 مگابایت
نوع : pdf
بازدید : 18618
منتشرکننده : CarGeek
|
دستورالعمل بازدید دستکاری صفحه کیلومتر در خودروهای X100 و X200
5 سال پیش
0.47 مگابایت
نوع : pdf
بازدید : 4178
منتشرکننده : CarGeek
|
دستورالعمل عیب یابی و تعویض مجموعه کویل ، وایر و شمع انواع پراید
5 سال پیش
2.39 مگابایت
نوع : pdf
بازدید : 52292
منتشرکننده : CarGeek
|
Classroom Manual for Automotive Electricity And Electronics
5 سال پیش
53.56 مگابایت
نوع : pdf
بازدید : 3367
منتشرکننده : CarGeek
|
تحلیل سیستم های تعلیق خودرو سمند
5 سال پیش
2.43 مگابایت
نوع : pdf
بازدید : 7577
منتشرکننده : CarGeek
|
راهنمای ایراد شتاب گیری و گاز خوردن ضعیف موتور و گاهاً خاموش شدن آن
5 سال پیش
4.1 مگابایت
نوع : pdf
بازدید : 8362
منتشرکننده : CarGeek
|
راهنمای تعمیرات گیربکس اتوماتیک تندر90
5 سال پیش
3.88 مگابایت
نوع : pdf
بازدید : 5230
منتشرکننده : CarGeek
|
راهنمای تعمیرات گیربکس پادرا
5 سال پیش
4.58 مگابایت
نوع : pdf
بازدید : 4347
منتشرکننده : CarGeek
|
راهنمای تعمیرات و سرویس سیستم تعلیق سراتو
5 سال پیش
8.15 مگابایت
نوع : pdf
بازدید : 5628
منتشرکننده : CarGeek
|
A Security Analysis of Radio Remote Controllers
5 سال پیش
5.2 مگابایت
نوع : pdf
بازدید : 3335
منتشرکننده : CarGeek
|
دستورالعمل عیب یابی و رفع ایراد دیسک و صفحه کلاچ زامیاد
5 سال پیش
2.82 مگابایت
نوع : pdf
بازدید : 7482
منتشرکننده : CarGeek
|
راهنمای تعمیرات اساسی گیربکس تندر90
5 سال پیش
5.5 مگابایت
نوع : pdf
بازدید : 9702
منتشرکننده : CarGeek
|
کتاب تعمیرکار برق خودرو براساس استاندارد درجه2 فنی و حرفه ای (باتری سازی)
5 سال پیش
9.31 مگابایت
نوع : pdf
بازدید : 74999
منتشرکننده : CarGeek
|
راهنمای تعمیرات اکسل جلو رنو ساندرو
5 سال پیش
3.08 مگابایت
نوع : pdf
بازدید : 4143
منتشرکننده : CarGeek
|
راهنمای سیستم انتقال قدرت و پلوس ساندرو
5 سال پیش
2.73 مگابایت
نوع : pdf
بازدید : 3319
منتشرکننده : CarGeek
|
جزوه امداد خودروهای مدیران خودرو
5 سال پیش
4.75 مگابایت
نوع : pdf
بازدید : 6180
منتشرکننده : CarGeek
|
راهنمای کامل تعمیرات جیلی امرگرند EC7
5 سال پیش
50.02 مگابایت
نوع : pdf
بازدید : 39425
منتشرکننده : CarGeek
|
دستورالعمل عیب یابی مجموعه جلو آمپر X100 و X200 (بجز کوئیک و ساینا AT)
5 سال پیش
0.47 مگابایت
نوع : pdf
بازدید : 7310
منتشرکننده : CarGeek
|
جزوه آموزشی سیستم برق خودروی Arizzo5
5 سال پیش
6.57 مگابایت
نوع : pdf
بازدید : 8337
منتشرکننده : CarGeek
|
جزوه برق تیگو 7 موتور 1.5TC و گیربکس DCT
5 سال پیش
19.64 مگابایت
نوع : pdf
بازدید : 14734
منتشرکننده : CarGeek
|
راهنمای تعویض دیسک چرخ عقب برلیانس H300
5 سال پیش
3.06 مگابایت
نوع : pdf
بازدید : 7017
منتشرکننده : CarGeek
|
راهنمای تعویض سنسور نقطه مرگ بالای خودرو وانت زامیاد
5 سال پیش
2.84 مگابایت
نوع : pdf
بازدید : 23262
منتشرکننده : CarGeek
|
راهنمای تعویض موتور پله ای (استپ موتور) دریچه گاز خودرو زامیاد
5 سال پیش
2.74 مگابایت
نوع : pdf
بازدید : 10385
منتشرکننده : CarGeek
|
راهنمای آموزشی دلکو و کویل- فایل 2
5 سال پیش
1.69 مگابایت
نوع : pdf
بازدید : 10800
منتشرکننده : CarGeek
|
راهنمای آموزشی دلکو و کویل
5 سال پیش
2.19 مگابایت
نوع : pdf
بازدید : 71451
منتشرکننده : CarGeek
|
راهنمای تعمیرات و عیب یابی ایربگ راننده و کمربند پیش کشنده خانواده خودرو سورن
5 سال پیش
1.99 مگابایت
نوع : pdf
بازدید : 8170
منتشرکننده : CarGeek
|
راهنمای تعمیرات ، عیب یابی و نقشه های ایربگ سرنشین سمند
5 سال پیش
1.43 مگابایت
نوع : pdf
بازدید : 7077
منتشرکننده : CarGeek
|
کتاب Gasoline Engine Management Systems and Components
5 سال پیش
10.56 مگابایت
نوع : pdf
بازدید : 4147
منتشرکننده : CarGeek
|
راهنمای تعمیرات سیستم تعلیق جلو تیبا
5 سال پیش
5.15 مگابایت
نوع : pdf
بازدید : 7697
منتشرکننده : CarGeek
|
فراخوان عیب یابی ، تعویض و تنظیم سوئیچ پدال ترمز در خودروهای کوئیک و ساینا اتوماتیک (کدخطای P0504)
5 سال پیش
0.82 مگابایت
نوع : pdf
بازدید : 16955
منتشرکننده : CarGeek
|
نحوه رفع ایراد عدم عملکرد فن بخاری بعلت خرابی رزیستور در خودروهای خانواده X200
5 سال پیش
0.33 مگابایت
نوع : pdf
بازدید : 21475
منتشرکننده : CarGeek
|
راهنمای تعمیرات مکانیکی موتور TU5 پژو 206
5 سال پیش
6.9 مگابایت
نوع : pdf
بازدید : 10376
منتشرکننده : CarGeek
|
راهنمای تعمیرات داشبورد دو ایربگ پژو 405 و پارس
5 سال پیش
2.24 مگابایت
نوع : pdf
بازدید : 14708
منتشرکننده : CarGeek
|
راهنمای تعمیرات و عیب یابی ایربگ و کمربند ایمنی خودرو رانا
5 سال پیش
1.61 مگابایت
نوع : pdf
بازدید : 9308
منتشرکننده : CarGeek
|
راهنمای سیستم ایموبیلایزر ضدسرقت رنو کپچر
5 سال پیش
3.25 مگابایت
نوع : pdf
بازدید : 4234
منتشرکننده : CarGeek
|
راهنمای تعمیرات سیستم کلاچ نیسان پاترول
5 سال پیش
0.84 مگابایت
نوع : pdf
بازدید : 20023
منتشرکننده : CarGeek
|
راهنمای تعمیرات سیستم فرمان نیسان پاترول
5 سال پیش
1.33 مگابایت
نوع : pdf
بازدید : 19604
منتشرکننده : CarGeek
|
راهنمای تعمیرات ترمز نیسان پاترول
5 سال پیش
1.18 مگابایت
نوع : pdf
بازدید : 17674
منتشرکننده : CarGeek
|
نقشه ها و تصاویر قطعات یدکی پراید صبا
5 سال پیش
42.12 مگابایت
نوع : pdf
بازدید : 63457
منتشرکننده : CarGeek
|
نقشه های الکتریکی کیا سراتو (2009–2007)
5 سال پیش
12.57 مگابایت
نوع : pdf
بازدید : 11064
منتشرکننده : CarGeek
|
راهنمای سیستم شبکه LAN نیسان مورانو
5 سال پیش
2.13 مگابایت
نوع : pdf
بازدید : 5388
منتشرکننده : CarGeek
|
راهنمای تعمیرات مکانیکی موتور نیسان مورانو
5 سال پیش
2 مگابایت
نوع : pdf
بازدید : 6305
منتشرکننده : CarGeek
|
راهنمای کامل تعمیرات چری تیگو5
5 سال پیش
144.04 مگابایت
نوع : pdf
بازدید : 33169
منتشرکننده : CarGeek
|
راهنمای تعمیرات بخاری و کولر نیسان پاترول
5 سال پیش
1.74 مگابایت
نوع : pdf
بازدید : 24417
منتشرکننده : CarGeek
|
راهنمای تعمیرات شاسی و بدنه نیسان پاترول
5 سال پیش
1.6 مگابایت
نوع : pdf
بازدید : 12267
منتشرکننده : CarGeek
|
راهنمای کامل تعمیرات MVM315
5 سال پیش
167.62 مگابایت
نوع : pdf
بازدید : 59292
منتشرکننده : CarGeek
|
معرفی و راهنمای تعمیرات ایربگ سمند، سورن، پژو405 و پارس
5 سال پیش
6.46 مگابایت
نوع : pdf
بازدید : 14837
منتشرکننده : CarGeek
|
اندازه گیری و مقایسه پارامترهای آلایندگی دود اگزوز و عملکرد در خودرو پراید مجهز به هدرز و بدون آن
5 سال پیش
0.42 مگابایت
نوع : pdf
بازدید : 3392
منتشرکننده : CarGeek
|
راهنمای تعمیرات ایربگ آریسان
5 سال پیش
5.56 مگابایت
نوع : pdf
بازدید : 5130
منتشرکننده : CarGeek
|
دستورالعمل عیب یابی صدای غیرعادی تسمه ها و پولی ها
5 سال پیش
1.49 مگابایت
نوع : pdf
بازدید : 24817
منتشرکننده : CarGeek
|
راهنمای دوره سوخت رسانی CNG سایپا
5 سال پیش
10.47 مگابایت
نوع : pdf
بازدید : 10699
منتشرکننده : CarGeek
|
دستورالعمل نصب مه شکن جلو برای خانواده پژو 405 RDوROA
5 سال پیش
3.01 مگابایت
نوع : pdf
بازدید : 64680
منتشرکننده : CarGeek
|
کتابچه راهنمای نقشه های الکتریکی 206 فرانسوی
5 سال پیش
19.89 مگابایت
نوع : pdf
بازدید : 30122
منتشرکننده : CarGeek
|
مجموعه سئوالات نظری و عملی ارزشیابی مهارت تعمیرکار برق خودرو درجه2
5 سال پیش
26.51 مگابایت
نوع : pdf
بازدید : 7351
منتشرکننده : CarGeek
|
راهنمای تعمیرات COM2000
5 سال پیش
1.27 مگابایت
نوع : pdf
بازدید : 6966
منتشرکننده : CarGeek
|
نمونه سئوالات آزمون سیستم سوخت رسانی و جرقه انژکتوری- فایل 5
5 سال پیش
0.32 مگابایت
نوع : pdf
بازدید : 5131
منتشرکننده : CarGeek
|
نمونه سئوالات آزمون سیستم سوخت رسانی و جرقه انژکتوری- فایل 4
5 سال پیش
0.33 مگابایت
نوع : pdf
بازدید : 3965
منتشرکننده : CarGeek
|
نمونه سئوالات آزمون سیستم سوخت رسانی و جرقه انژکتوری- فایل 3
5 سال پیش
0.33 مگابایت
نوع : pdf
بازدید : 4103
منتشرکننده : CarGeek
|
نمونه سئوالات آزمون سیستم سوخت رسانی و جرقه انژکتوری- فایل 2
5 سال پیش
0.32 مگابایت
نوع : pdf
بازدید : 4400
منتشرکننده : CarGeek
|
نمونه سئوالات آزمون سیستم سوخت رسانی و جرقه انژکتوری
5 سال پیش
0.1 مگابایت
نوع : pdf
بازدید : 12535
منتشرکننده : CarGeek
|
نمونه سئوالات آزمون کار با دستگاه عیب یاب (دیاگ)
5 سال پیش
0.16 مگابایت
نوع : pdf
بازدید : 7805
منتشرکننده : CarGeek
|
نمونه سئوالات آزمون کتبی مهارت کاربراتور
5 سال پیش
0.44 مگابایت
نوع : pdf
بازدید : 4781
منتشرکننده : CarGeek
|
نمونه سئوالات پرتکرار برق خودرو درجه2 فنی و حرفه ای- فایل 6
5 سال پیش
0.21 مگابایت
نوع : pdf
بازدید : 4482
منتشرکننده : CarGeek
|
نمونه سئوالات پرتکرار برق خودرو درجه2 فنی و حرفه ای- فایل 5
5 سال پیش
0.13 مگابایت
نوع : pdf
بازدید : 4455
منتشرکننده : CarGeek
|
نمونه سئوالات پرتکرار برق خودرو درجه2 فنی و حرفه ای- فایل 4
5 سال پیش
1.1 مگابایت
نوع : pdf
بازدید : 4537
منتشرکننده : CarGeek
|
نمونه سئوالات پرتکرار برق خودرو درجه2 فنی و حرفه ای- فایل 3
5 سال پیش
0.38 مگابایت
نوع : pdf
بازدید : 4154
منتشرکننده : CarGeek
|
نمونه سئوالات پرتکرار برق خودرو درجه2 فنی و حرفه ای- فایل 2
5 سال پیش
0.38 مگابایت
نوع : pdf
بازدید : 4725
منتشرکننده : CarGeek
|
نمونه سئوالات پرتکرار برق خودرو درجه2 فنی و حرفه ای
5 سال پیش
0.73 مگابایت
نوع : pdf
بازدید : 24063
منتشرکننده : CarGeek
|
مقدار گاز کولر سایپا X100 و X200 (خانواده پراید و تیبا)
5 سال پیش
0.91 مگابایت
نوع : pdf
بازدید : 43940
منتشرکننده : CarGeek
|
راهنمای تعمیرات موتور 1MZ-FE تویوتا (کمری 6سیلندر)
5 سال پیش
27.81 مگابایت
نوع : pdf
بازدید : 11980
منتشرکننده : CarGeek
|
راهنمای عیب یابی و تعویض سوئیچ و شیشه بالابر برقی پراید و تیبا
5 سال پیش
3.11 مگابایت
نوع : pdf
بازدید : 23470
منتشرکننده : CarGeek
|
تشخیص ایراد از روی دود اگزوز در وانت زامیاد دیزل
5 سال پیش
0.13 مگابایت
نوع : pdf
بازدید : 4529
منتشرکننده : CarGeek
|
نمونه سئوالات آزمون اتومکانیک درجه2
5 سال پیش
0.81 مگابایت
نوع : pdf
بازدید : 16334
منتشرکننده : CarGeek
|
راهنمای تعمیرات موتور چری
5 سال پیش
27.83 مگابایت
نوع : pdf
بازدید : 9734
منتشرکننده : CarGeek
|
دستورالعمل عیب یابی و تعویض تایر خودرو
5 سال پیش
2.44 مگابایت
نوع : pdf
بازدید : 4130
منتشرکننده : CarGeek
|
مشخصات روانکارهای خودروهای سایپا
5 سال پیش
1.85 مگابایت
نوع : pdf
بازدید : 3463
منتشرکننده : CarGeek
|
دستورالعمل عیب یابی و تعویض کیت کامل کلاچ
5 سال پیش
3.75 مگابایت
نوع : pdf
بازدید : 8139
منتشرکننده : CarGeek
|
جزوه سیستم سوخت رسانی انژکتوری سایپا
5 سال پیش
5.31 مگابایت
نوع : pdf
بازدید : 8652
منتشرکننده : CarGeek
|
کتاب موتور جت ، اصول تئوری ، طراحی و عملکرد
5 سال پیش
16.29 مگابایت
نوع : pdf
بازدید : 7782
منتشرکننده : CarGeek
|
راهنمای هیدرولیک فرمان در پژو RD
5 سال پیش
1.06 مگابایت
نوع : pdf
بازدید : 31565
منتشرکننده : CarGeek
|
راهنمای مدارات الکتریکی سمند با موتور TU5
5 سال پیش
46.43 مگابایت
نوع : pdf
بازدید : 6699
منتشرکننده : CarGeek
|
لیست سرویس های ادواری سایپا کوییک
5 سال پیش
1.26 مگابایت
نوع : pdf
بازدید : 55989
منتشرکننده : CarGeek
|
جزوه بازرسی و ایمنی لیفتراک
5 سال پیش
4.34 مگابایت
نوع : pdf
بازدید : 10711
منتشرکننده : CarGeek
|
راهنمای تعقیب و مراقبت خودرو CIA
5 سال پیش
1.56 مگابایت
نوع : pdf
بازدید : 6169
منتشرکننده : CarGeek
|
کاتالوگ قطعات پژو پارس ELX موتور زانتیا
5 سال پیش
27.39 مگابایت
نوع : pdf
بازدید : 22898
منتشرکننده : CarGeek
|
اطلاعات مربوط به دمونتاژ اسکانیا سری S, R, G وP
5 سال پیش
8.93 مگابایت
نوع : pdf
بازدید : 15653
منتشرکننده : CarGeek
|
راهنمای کامل تعمیرات MG GS
5 سال پیش
82.43 مگابایت
نوع : pdf
بازدید : 15212
منتشرکننده : CarGeek
|
معرفی و راهنمای تعمیرات الکتریکال سیستم ECO-MUX سورن ELX
5 سال پیش
2.71 مگابایت
نوع : pdf
بازدید : 3867
منتشرکننده : CarGeek
|
راهنمای باز و بست و عیب یابی گاردان 2تکه روآ سال
5 سال پیش
0.32 مگابایت
نوع : pdf
بازدید : 31100
منتشرکننده : CarGeek
|
کتاب Gears and Gear Drives
5 سال پیش
11.7 مگابایت
نوع : pdf
بازدید : 3520
منتشرکننده : CarGeek
|
راهنمای تعمیرات بدنه و تزئینات آریو S300
5 سال پیش
8.57 مگابایت
نوع : pdf
بازدید : 8727
منتشرکننده : CarGeek
|
راهنمای دسته سیم های و نقشه های الکتریکی هایما S7 توربوشارژ
5 سال پیش
19.42 مگابایت
نوع : pdf
بازدید : 6714
منتشرکننده : CarGeek
|
راهنمای دسته سیم های و نقشه های الکتریکی هایما S5 توربوشارژ
5 سال پیش
22.87 مگابایت
نوع : pdf
بازدید : 9812
منتشرکننده : CarGeek
|
دستورالعمل عیب یابی و تعویض مدولاتور ABS پراید و تیبا و ساینا و کوییک
5 سال پیش
2.43 مگابایت
نوع : pdf
بازدید : 20503
منتشرکننده : CarGeek
|
دستورالعمل تعویض مجموعه درب سوپاپ و واشر موتور تیبا
5 سال پیش
1.3 مگابایت
نوع : pdf
بازدید : 31092
منتشرکننده : CarGeek
|
جزوه آموزشی تعمیر موتور XU7 پژو پارس ، 405 و سمند
5 سال پیش
6.21 مگابایت
نوع : pdf
بازدید : 38500
منتشرکننده : CarGeek
|
تحقیق بررسی خودروهای هیبریدی
5 سال پیش
3.56 مگابایت
نوع : pdf
بازدید : 4816
منتشرکننده : CarGeek
|
راهنمای تعمیرات داشبورد و تزئینات دنا و دناپلاس
5 سال پیش
5.36 مگابایت
نوع : pdf
بازدید : 33001
منتشرکننده : CarGeek
|
لیست سرویس های دوره ای وانت پادرا
5 سال پیش
0.79 مگابایت
نوع : pdf
بازدید : 4769
منتشرکننده : CarGeek
|
جزوه آموزشی سیستم گیربکس دستی سوزوکی گرندویتارا
5 سال پیش
2.04 مگابایت
نوع : pdf
بازدید : 5695
منتشرکننده : CarGeek
|
راهنمای تعمیرات سیستم ایربگ ساندرو
5 سال پیش
1.52 مگابایت
نوع : pdf
بازدید : 4954
منتشرکننده : CarGeek
|
دستورالعمل عیب یابی و تعویض مجموعه گیربکس بهبودیافته دوبل برنجی خودروهای X100 و X200 سایپا (ND1-ND2)
5 سال پیش
5.72 مگابایت
نوع : pdf
بازدید : 9628
منتشرکننده : CarGeek
|
مقدمه ای بر خودروهای هیبرید و پلاگین
5 سال پیش
4.06 مگابایت
نوع : pdf
بازدید : 6196
منتشرکننده : CarGeek
|
آشنایی با سیستم ایمنی فعال ایربگ
5 سال پیش
7.44 مگابایت
نوع : pdf
بازدید : 4006
منتشرکننده : CarGeek
|
راهنمای تعمیرات و سرویس مدارهای الکتریکی کوییک
5 سال پیش
48.03 مگابایت
نوع : pdf
بازدید : 8825
منتشرکننده : CarGeek
|
راهنمای پارامترها و عیب یابی تندر90
5 سال پیش
0.39 مگابایت
نوع : pdf
بازدید : 19217
منتشرکننده : CarGeek
|
روش های بیکد و خام کردن ECUها
5 سال پیش
0.74 مگابایت
نوع : pdf
بازدید : 28915
منتشرکننده : CarGeek
|
لیست کدهای خطا کوییک و ساینا اتوماتیک و روش رفع آن ها- فایل 2
5 سال پیش
0.83 مگابایت
نوع : pdf
بازدید : 17378
منتشرکننده : CarGeek
|
لیست کدهای خطا کوییک و ساینا اتوماتیک و روش رفع آن ها
5 سال پیش
1.37 مگابایت
نوع : pdf
بازدید : 73344
منتشرکننده : CarGeek
|
راهنمای مشخصات و فرآیند تعمیرات و نرم افزار دیالوژیس رنو
5 سال پیش
22.53 مگابایت
نوع : pdf
بازدید : 3501
منتشرکننده : CarGeek
|
راهنمای تعمیرات موتور زوتی Z300 کد TNN4G15&16A
5 سال پیش
6.11 مگابایت
نوع : pdf
بازدید : 13003
منتشرکننده : CarGeek
|
راهنمای نقشه های الکتریکی ولوو FH و FM- فایل 2
5 سال پیش
14.58 مگابایت
نوع : pdf
بازدید : 8478
منتشرکننده : CarGeek
|
راهنمای نقشه های الکتریکی ولوو FH و FM
5 سال پیش
29.68 مگابایت
نوع : pdf
بازدید : 35200
منتشرکننده : CarGeek
|
راهنمای تعمیرات مجموعه موتور 1.65 برلیانس (BM16LB)
5 سال پیش
10.63 مگابایت
نوع : pdf
بازدید : 13250
منتشرکننده : CarGeek
|
راهنما و نقشه های مدارات الکتریکی سایپا کوییک
5 سال پیش
5.72 مگابایت
نوع : pdf
بازدید : 74617
منتشرکننده : CarGeek
|
معرفی و اطلاعات میتسوبیشی پاجرو تولید ایران
5 سال پیش
5.82 مگابایت
نوع : pdf
بازدید : 15602
منتشرکننده : CarGeek
|
راهنمای تعمیرات سیستم کلاچ جیپ صحرا
5 سال پیش
1.45 مگابایت
نوع : pdf
بازدید : 9299
منتشرکننده : CarGeek
|
راهنمای تعمیرات سیستم سوخت و اگزوز جیپ صحرا
5 سال پیش
1.53 مگابایت
نوع : pdf
بازدید : 6613
منتشرکننده : CarGeek
|
راهنمای اطلاعات عمومی تعمیرات جیپ صحرا
5 سال پیش
1.54 مگابایت
نوع : pdf
بازدید : 11801
منتشرکننده : CarGeek
|
راهنمای تعمیرات سیستم ترمز جیپ صحرا
5 سال پیش
2.13 مگابایت
نوع : pdf
بازدید : 11584
منتشرکننده : CarGeek
|
راهنمای تعمیرات سیستم فرمان جیپ صحرا
5 سال پیش
1.84 مگابایت
نوع : pdf
بازدید : 9587
منتشرکننده : CarGeek
|
راهنمای درها و درعقب(هاچ بک) مزدا3
5 سال پیش
1.27 مگابایت
نوع : pdf
بازدید : 3274
منتشرکننده : CarGeek
|
راهنمای باز و بست شیشه ها ، پنجره ها و آینه های مزدا3
5 سال پیش
6.84 مگابایت
نوع : pdf
بازدید : 7333
منتشرکننده : CarGeek
|
راهنمای باز و بست تجهیزات بدنه مزدا3
5 سال پیش
3.87 مگابایت
نوع : pdf
بازدید : 16526
منتشرکننده : CarGeek
|
راهنمای اطلاعات عمومی تعمیرات بدنه مزدا3
5 سال پیش
12.28 مگابایت
نوع : pdf
بازدید : 4325
منتشرکننده : CarGeek
|
راهنمای عیب یابی تهویه مطبوع اتوماتیک مزدا3
5 سال پیش
1.14 مگابایت
نوع : pdf
بازدید : 5867
منتشرکننده : CarGeek
|
راهنمای سیستم عیب یابی هوشمند جعبه دنده اتوماتیک مزدا3 جدید
5 سال پیش
7.99 مگابایت
نوع : pdf
بازدید : 5077
منتشرکننده : CarGeek
|
راهنمای تعمیرات سیستم تهویه مطبوع اتوماتیک مزدا3
5 سال پیش
2.38 مگابایت
نوع : pdf
بازدید : 9016
منتشرکننده : CarGeek
|
راهنمای نحوه نصب روکش صندلی برلیانس سری H300
5 سال پیش
2.05 مگابایت
نوع : pdf
بازدید : 5569
منتشرکننده : CarGeek
|
راهنمای عیب یابی الکتریکی و دودهای خروجی موتور 4HE1-TC کامیونت ایسوزو
5 سال پیش
2.86 مگابایت
نوع : pdf
بازدید : 4344
منتشرکننده : CarGeek
|
راهنمای تعمیرات سیستم کلاچ کامیونت ایسوزو
5 سال پیش
0.49 مگابایت
نوع : pdf
بازدید : 14420
منتشرکننده : CarGeek
|
چک لیست نمونه کارشناسی خودرو
5 سال پیش
0.18 مگابایت
نوع : pdf
بازدید : 14220
منتشرکننده : CarGeek
|
معرفی پژو 405 SLX
5 سال پیش
4.9 مگابایت
نوع : pdf
بازدید : 7254
منتشرکننده : CarGeek
|
راهنمای عیب یابی پشت آمپر مزدا3 جدید
5 سال پیش
0.27 مگابایت
نوع : pdf
بازدید : 21529
منتشرکننده : CarGeek
|
راهنمای عیب یابی صفحه نمایش چندمنظوره مزدا3 جدید
5 سال پیش
0.94 مگابایت
نوع : pdf
بازدید : 5110
منتشرکننده : CarGeek
|
راهنمای عیب یابی پخش و تعویض CD مزدا3 جدید
5 سال پیش
0.26 مگابایت
نوع : pdf
بازدید : 5369
منتشرکننده : CarGeek
|
راهنمای تعمیرات سیستم سوخت رسانی جیپ صحرا
5 سال پیش
1.91 مگابایت
نوع : pdf
بازدید : 10524
منتشرکننده : CarGeek
|
راهنمای تعمیرات گیربکس و کمک گیربکس جیپ صحرا
5 سال پیش
1.91 مگابایت
نوع : pdf
بازدید : 16171
منتشرکننده : CarGeek
|
راهنمای نگه داری و تعمیرات جیپ صحرا
5 سال پیش
1.75 مگابایت
نوع : pdf
بازدید : 12517
منتشرکننده : CarGeek
|
نکاتی درباره کارشناسی فنی ، رنگ و بدنه خودرو
5 سال پیش
0.84 مگابایت
نوع : pdf
بازدید : 5817
منتشرکننده : CarGeek
|
جزوه آموزش سیستم تهویه مطبوع ایساکو
5 سال پیش
10.29 مگابایت
نوع : pdf
بازدید : 12423
منتشرکننده : CarGeek
|
راهنمای نصب سیستم پاورویندوز تندر90 و ساندرو
5 سال پیش
2.67 مگابایت
نوع : pdf
بازدید : 4036
منتشرکننده : CarGeek
|
راهنمای تعریف کلید پژو 206 با ECU غرب استیل
5 سال پیش
1.26 مگابایت
نوع : pdf
بازدید : 8626
منتشرکننده : CarGeek
|
راهنمای تعمیرات سیستم فرمان برقی ،تعلیق و اکسل ها سایپا کوییک
5 سال پیش
3.1 مگابایت
نوع : pdf
بازدید : 10113
منتشرکننده : CarGeek
|
راهنمای تعمیرات و سرویس سیستم ترمز سایپا کوییک
5 سال پیش
7.3 مگابایت
نوع : pdf
بازدید : 8854
منتشرکننده : CarGeek
|
راهنمای نصب سنسور دنده عقب مگان-پراید-تندر-ریو-تیبا-X100
5 سال پیش
1.31 مگابایت
نوع : pdf
بازدید : 14286
منتشرکننده : CarGeek
|
نحوه رفع لرزش و یا صدای غیرعادی فرمان تندر90،پارس تندر و ساندرو
5 سال پیش
1.1 مگابایت
نوع : pdf
بازدید : 7691
منتشرکننده : CarGeek
|
راهنمای تعمیرات بدنه و تزئینات سایپا کوییک
5 سال پیش
17.3 مگابایت
نوع : pdf
بازدید : 7744
منتشرکننده : CarGeek
|
راهنمای تعمیرات Clock Spring (رابط هرزگرد یا سوئیچ چرخشی) پراید و تیبا
5 سال پیش
3.68 مگابایت
نوع : pdf
بازدید : 24121
منتشرکننده : CarGeek
|
راهنمای عیب یابی سیستم ترمز نیسان زامیاد
5 سال پیش
1.21 مگابایت
نوع : pdf
بازدید : 22378
منتشرکننده : CarGeek
|
راهنمای تعمیرات و سرویس الکتریکی موتور سراتو 2000
5 سال پیش
3.77 مگابایت
نوع : pdf
بازدید : 3905
منتشرکننده : CarGeek
|
راهنمای تعمیرات و سرویس الکتریکی موتور سراتو 1600
5 سال پیش
4.72 مگابایت
نوع : pdf
بازدید : 3479
منتشرکننده : CarGeek
|
راهنمای تعمیرات و سرویس تهویه مطبوع سایپا کوییک
5 سال پیش
1.6 مگابایت
نوع : pdf
بازدید : 26678
منتشرکننده : CarGeek
|
راهنمای تعمیرات و سرویس تجهیزات الکتریکی سایپا کوییک
5 سال پیش
3.28 مگابایت
نوع : pdf
بازدید : 11712
منتشرکننده : CarGeek
|
دستورالعمل عیب یابی و تعویض مجموعه دسته راهنما زامیاد یورو4
5 سال پیش
3.13 مگابایت
نوع : pdf
بازدید : 11465
منتشرکننده : CarGeek
|
راهنمای مصور تعمیرات و سرویس گیربکس 5سرعته نیسان وانت زامیاد دیزل و بنزینی
5 سال پیش
5.34 مگابایت
نوع : pdf
بازدید : 23862
منتشرکننده : CarGeek
|
راهنمای تعمیرات و سرویس گیربکس اتوماتیک CVT سایپا کوییک
5 سال پیش
9.79 مگابایت
نوع : pdf
بازدید : 12402
منتشرکننده : CarGeek
|
راهنمای تعمیرات و سرویس سیستم سوخت رسانی سایپا کوییک
5 سال پیش
2.22 مگابایت
نوع : pdf
بازدید : 26502
منتشرکننده : CarGeek
|
راهنمای تعمیرات و سرویس مجموعه موتور سایپا کوییک
5 سال پیش
4.66 مگابایت
نوع : pdf
بازدید : 18900
منتشرکننده : CarGeek
|
راهنمای تعمیرات تعلیق پیکاپ ریچ
5 سال پیش
2.62 مگابایت
نوع : pdf
بازدید : 7713
منتشرکننده : CarGeek
|
راهنمای تعمیرات فرمان پیکاپ ریچ
5 سال پیش
11.22 مگابایت
نوع : pdf
بازدید : 6937
منتشرکننده : CarGeek
|
راهنمای تعمیرات سیستم جعبه دنده و انتقال قدرت پیکاپ ریچ
5 سال پیش
16.15 مگابایت
نوع : pdf
بازدید : 7172
منتشرکننده : CarGeek
|
راهنمای تعمیرات تزئینات داخلی سورن ELX
5 سال پیش
0.8 مگابایت
نوع : pdf
بازدید : 20419
منتشرکننده : CarGeek
|
راهنمای تعمیرات و سرویس بدنه و متعلقات چانگان CS35
5 سال پیش
4.77 مگابایت
نوع : pdf
بازدید : 8847
منتشرکننده : CarGeek
|
راهنمای عیب یابی موتورهای کوماتسو
5 سال پیش
8.58 مگابایت
نوع : pdf
بازدید : 10711
منتشرکننده : CarGeek
|
دستورالعمل عیب یابی و رفع ایراد گیربکس دستی BE پژو 405، پارس ، سمند، سورن و دنا
5 سال پیش
1.26 مگابایت
نوع : pdf
بازدید : 8840
منتشرکننده : CarGeek
|
راهنمای تعمیرات موتور پیکاپ ریچ
5 سال پیش
5.99 مگابایت
نوع : pdf
بازدید : 19760
منتشرکننده : CarGeek
|
اطلاعیه فنی معرفی هایما S5
5 سال پیش
0.52 مگابایت
نوع : pdf
بازدید : 6229
منتشرکننده : CarGeek
|
راهنمای آموزشی سیستم فرمان الکتروهیدرولیکی هیوندای
5 سال پیش
1 مگابایت
نوع : pdf
بازدید : 6639
منتشرکننده : CarGeek
|
طرح پروژه طراحی و تولید محصول دنا (NX7)
5 سال پیش
7 مگابایت
نوع : pdf
بازدید : 3679
منتشرکننده : CarGeek
|
نحوه نصب سیستم صوتی/تصویری ، دوربین دنده عقب و رهیاب GPS برلیانس H320وH330
5 سال پیش
4.26 مگابایت
نوع : pdf
بازدید : 8777
منتشرکننده : CarGeek
|
راهنمای تعمیرات و سرویس سیستم ترمز ساینا اتوماتیک
5 سال پیش
7.34 مگابایت
نوع : pdf
بازدید : 7121
منتشرکننده : CarGeek
|
راهنمای تعمیرات و سرویس سیستم سوخت رسانی رنو کپچر
5 سال پیش
3.28 مگابایت
نوع : pdf
بازدید : 7014
منتشرکننده : CarGeek
|
راهنمای تعمیرات و سرویس توربوشارژر رنو کپچر
5 سال پیش
1.26 مگابایت
نوع : pdf
بازدید : 4755
منتشرکننده : CarGeek
|
دستورالعمل عیب یابی و تعویض قطعات زیرمجموعه صندلی تیبا2 و X100
5 سال پیش
3.36 مگابایت
نوع : pdf
بازدید : 105889
منتشرکننده : CarGeek
|
جزوه آموزش فنی خودرو سراتو
5 سال پیش
23.62 مگابایت
نوع : pdf
بازدید : 11441
منتشرکننده : CarGeek
|
راهنمای تعمیرات و سرویس تهویه مطبوع ساینا اتوماتیک
5 سال پیش
4.74 مگابایت
نوع : pdf
بازدید : 8618
منتشرکننده : CarGeek
|
راهنمای ساختار مولتی پلکس در خودروهای رنو (کپچر)
5 سال پیش
2.3 مگابایت
نوع : pdf
بازدید : 5103
منتشرکننده : CarGeek
|
کلیات و دانستنیهای کاتالیزور خودرو
5 سال پیش
0.5 مگابایت
نوع : pdf
بازدید : 3952
منتشرکننده : CarGeek
|
معرفی و آشنایی با سیستم شبکه های مالتی پلکس
5 سال پیش
3.03 مگابایت
نوع : pdf
بازدید : 9306
منتشرکننده : CarGeek
|
معرفی سیستم ایموبیلایزر و نحوه معرفی کدسوئیچ خودروها
5 سال پیش
0.77 مگابایت
نوع : pdf
بازدید : 6613
منتشرکننده : CarGeek
|
راهنمای تعمیرات و سرویس سیستم سوخت رسانی ساینا اتوماتیک
5 سال پیش
6.37 مگابایت
نوع : pdf
بازدید : 6469
منتشرکننده : CarGeek
|
دستورالعمل تست جعبه فرمان هیدرولیک پژو405 ، پارس ، سمند و دنا
5 سال پیش
1.18 مگابایت
نوع : pdf
بازدید : 11228
منتشرکننده : CarGeek
|
راهنمای عیب یابی و تعویض مجموعه بخاری و اواپراتور تیبا
5 سال پیش
2.5 مگابایت
نوع : pdf
بازدید : 35155
منتشرکننده : CarGeek
|
2018s Top 10 Tech Cars - IEEE Spectrum
5 سال پیش
14.9 مگابایت
نوع : pdf
بازدید : 3416
منتشرکننده : CarGeek
|
راهنمای نصب سیستم صوتی/تصویری سراتو
5 سال پیش
1.53 مگابایت
نوع : pdf
بازدید : 7534
منتشرکننده : CarGeek
|
راهنمای رله و فیوزهای دنا پلاس اکوماکس
5 سال پیش
0.43 مگابایت
نوع : pdf
بازدید : 17899
منتشرکننده : CarGeek
|
رفع مشکل گیرکردن اهرم تعویض دنده در وضعیت P خودروهای برلیانس سری 300
5 سال پیش
0.69 مگابایت
نوع : pdf
بازدید : 18689
منتشرکننده : CarGeek
|
راهنمای مدارهای الکتریکی چانگان ایدو (EADO)
5 سال پیش
8.72 مگابایت
نوع : pdf
بازدید : 8352
منتشرکننده : CarGeek
|
راهنمای تعمیرات و سرویس گیربکس CVT ساینا اتوماتیک
5 سال پیش
9.83 مگابایت
نوع : pdf
بازدید : 10171
منتشرکننده : CarGeek
|
راهنمای تعمیرات موتور ساینا
5 سال پیش
19.97 مگابایت
نوع : pdf
بازدید : 14004
منتشرکننده : CarGeek
|
راهنمای H30 Cross امدادخودرو
5 سال پیش
3.47 مگابایت
نوع : pdf
بازدید : 4927
منتشرکننده : CarGeek
|
راهنمای امدادخودرو در مورد سیستم توربوشارژر محصولات ایران خودرو
5 سال پیش
2.59 مگابایت
نوع : pdf
بازدید : 5233
منتشرکننده : CarGeek
|
دستورالعمل تعویض شیشه جلو و عقب پراید و تیبا و ساینا
5 سال پیش
2.2 مگابایت
نوع : pdf
بازدید : 30325
منتشرکننده : CarGeek
|
راهنمای مصور تعمیراتی گیربکس 5سرعته زامیاد دیزل و بنزین
5 سال پیش
15.98 مگابایت
نوع : pdf
بازدید : 5039
منتشرکننده : CarGeek
|
معرفی فنی و راهنمای امداد پژو 2008 ، 301 و 508
5 سال پیش
5.75 مگابایت
نوع : pdf
بازدید : 11909
منتشرکننده : CarGeek
|
راهنمای دوره آموزشی CNG پژو 206SD دوگانه سوز
5 سال پیش
18.65 مگابایت
نوع : pdf
بازدید : 9202
منتشرکننده : CarGeek
|
راهنمای تعمیرات مدیریت موتور بسترن B50
5 سال پیش
8.44 مگابایت
نوع : pdf
بازدید : 5949
منتشرکننده : CarGeek
|
راهنمای تعمیرات موتور بسترن B50
5 سال پیش
5.6 مگابایت
نوع : pdf
بازدید : 9562
منتشرکننده : CarGeek
|
جزوه تخصصی تعمیرات نرم افزاری ECU
5 سال پیش
6.44 مگابایت
نوع : pdf
بازدید : 10684
منتشرکننده : CarGeek
|
راهنمای تعمیرات سیستم سوخت رسانی ، اگزوز و سیستم های کنترلی مزدا323
5 سال پیش
103.19 مگابایت
نوع : pdf
بازدید : 5021
منتشرکننده : CarGeek
|
راهنمای جعبه فیوز داخل موتور بسترن B30
5 سال پیش
0.41 مگابایت
نوع : pdf
بازدید : 11838
منتشرکننده : CarGeek
|
Security Analysis of Ethernet in Cars
5 سال پیش
2.44 مگابایت
نوع : pdf
بازدید : 3625
منتشرکننده : CarGeek
|
Ethernet in Automotive Networks
5 سال پیش
1.34 مگابایت
نوع : pdf
بازدید : 3720
منتشرکننده : CarGeek
|
Automotive Ethernet
5 سال پیش
10.78 مگابایت
نوع : pdf
بازدید : 3507
منتشرکننده : CarGeek
|
Automotive Ethernet:An Overview
5 سال پیش
1.89 مگابایت
نوع : pdf
بازدید : 3907
منتشرکننده : CarGeek
|
کتابچه نقشه های خودروهای انژکتوری ایرانی
5 سال پیش
44.52 مگابایت
نوع : pdf
بازدید : 66617
منتشرکننده : CarGeek
|
کتاب The Science of Vehicle Dynamics
5 سال پیش
8.06 مگابایت
نوع : pdf
بازدید : 3267
منتشرکننده : CarGeek
|
راهنمای عیب یابی و نقشه های ترمز سراتو
5 سال پیش
10.18 مگابایت
نوع : pdf
بازدید : 8553
منتشرکننده : CarGeek
|
راهنمای تعمیرات و سرویس ترمز سراتو
5 سال پیش
9.96 مگابایت
نوع : pdf
بازدید : 6896
منتشرکننده : CarGeek
|
راهنمای تعمیرات کلاچ هیدرولیک سراتو
5 سال پیش
2.48 مگابایت
نوع : pdf
بازدید : 5306
منتشرکننده : CarGeek
|
راهنمای اورهال گیربکس دستی سراتو
5 سال پیش
2.3 مگابایت
نوع : pdf
بازدید : 3579
منتشرکننده : CarGeek
|
راهنمای استفاده از ایکودیاگ در عیب یابی خودروها
5 سال پیش
6.35 مگابایت
نوع : pdf
بازدید : 14364
منتشرکننده : CarGeek
|
راهنمای آموزشی سیستم ایمنی تکمیلی SRS هیوندای- فایل 2
5 سال پیش
2.56 مگابایت
نوع : pdf
بازدید : 3729
منتشرکننده : CarGeek
|
راهنمای آموزشی سیستم ایمنی تکمیلی SRS هیوندای
5 سال پیش
1.63 مگابایت
نوع : pdf
بازدید : 3988
منتشرکننده : CarGeek
|
دفترچه راهنمای رنو تالیسمان
5 سال پیش
26.71 مگابایت
نوع : pdf
بازدید : 19034
منتشرکننده : CarGeek
|
دستورالعمل عیب یابی و تعویض ریموت پراید132 و تیبا
5 سال پیش
2.11 مگابایت
نوع : pdf
بازدید : 21147
منتشرکننده : CarGeek
|
راهنمای تعمیرات و عیب یابی سیستم کروزکنترل پژو پارس و سمند
5 سال پیش
8.75 مگابایت
نوع : pdf
بازدید : 5763
منتشرکننده : CarGeek
|
راهنمای آموزشی آشنایی با الکتریسیته و الکترونیک آسان موتور- فایل 2
5 سال پیش
3.28 مگابایت
نوع : pdf
بازدید : 4502
منتشرکننده : CarGeek
|
راهنمای آموزشی آشنایی با الکتریسیته و الکترونیک آسان موتور
5 سال پیش
2.32 مگابایت
نوع : pdf
بازدید : 4758
منتشرکننده : CarGeek
|
راهنمای ایمنی و سرویس سیستم CNG
5 سال پیش
1.72 مگابایت
نوع : pdf
بازدید : 6128
منتشرکننده : CarGeek
|
راهنمای عیب یابی الکتریکی موتور سراتو 2000- فایل 2
5 سال پیش
15.67 مگابایت
نوع : pdf
بازدید : 3571
منتشرکننده : CarGeek
|
راهنمای عیب یابی الکتریکی موتور سراتو 2000
5 سال پیش
20.37 مگابایت
نوع : pdf
بازدید : 4938
منتشرکننده : CarGeek
|
راهنمای عیب یابی الکتریکی موتور سراتو 1600- فایل 2
5 سال پیش
18.05 مگابایت
نوع : pdf
بازدید : 3444
منتشرکننده : CarGeek
|
راهنمای عیب یابی الکتریکی موتور سراتو 1600
5 سال پیش
18.9 مگابایت
نوع : pdf
بازدید : 3797
منتشرکننده : CarGeek
|
راهنمای آموزشی سیستم مدیریت موتور هیوندای- فایل 2
5 سال پیش
2.22 مگابایت
نوع : pdf
بازدید : 4200
منتشرکننده : CarGeek
|
راهنمای آموزشی سیستم مدیریت موتور هیوندای
5 سال پیش
9.1 مگابایت
نوع : pdf
بازدید : 8604
منتشرکننده : CarGeek
|
راهنمای آموزشی سیستم تعلیق با کنترل الکترونیکی هیوندای
5 سال پیش
2.13 مگابایت
نوع : pdf
بازدید : 6099
منتشرکننده : CarGeek
|
راهنمای گیربکس اتوماتیک 6سرعته AISIN F21-450 هیوندای
5 سال پیش
3.3 مگابایت
نوع : pdf
بازدید : 9887
منتشرکننده : CarGeek
|
نقشه های الکتریکی خودرو H30 Cross
5 سال پیش
17.19 مگابایت
نوع : pdf
بازدید : 28460
منتشرکننده : CarGeek
|
راهنمای کامل مدارهای الکتریکی تیبا- فایل 2
5 سال پیش
17.13 مگابایت
نوع : pdf
بازدید : 6222
منتشرکننده : CarGeek
|
راهنمای کامل مدارهای الکتریکی تیبا
5 سال پیش
21.1 مگابایت
نوع : pdf
بازدید : 13218
منتشرکننده : CarGeek
|
جزوات آموزشی نقاشی خودرو- فایل 3
5 سال پیش
0.27 مگابایت
نوع : pdf
بازدید : 4122
منتشرکننده : CarGeek
|
جزوات آموزشی نقاشی خودرو- فایل 2
5 سال پیش
3.82 مگابایت
نوع : pdf
بازدید : 4281
منتشرکننده : CarGeek
|
جزوات آموزشی نقاشی خودرو
5 سال پیش
10.56 مگابایت
نوع : pdf
بازدید : 17807
منتشرکننده : CarGeek
|
راهنمای تعمیرات و سرویس سیستم الکتریکی ایربگ سراتو
5 سال پیش
9.7 مگابایت
نوع : pdf
بازدید : 4761
منتشرکننده : CarGeek
|
Accelerating C-V2X Commercialization
5 سال پیش
3.38 مگابایت
نوع : pdf
بازدید : 3525
منتشرکننده : CarGeek
|
Cellular Vehicle-to-everything (C-V2X) , enabling intelligent transport
5 سال پیش
8.85 مگابایت
نوع : pdf
بازدید : 3577
منتشرکننده : CarGeek
|
راهنمای آموزشی CNG تندر90
5 سال پیش
1.77 مگابایت
نوع : pdf
بازدید : 7913
منتشرکننده : CarGeek
|
راهنمای تعمیرات و سرویس سیستم خنک کننده موتور هایما
5 سال پیش
0.45 مگابایت
نوع : pdf
بازدید : 6224
منتشرکننده : CarGeek
|
جزوه دوره آموزش فنی کپچر
5 سال پیش
32.15 مگابایت
نوع : pdf
بازدید : 3584
منتشرکننده : CarGeek
|
راهنمای آموزشی ایموبلایزر (سیستم ضدسرقت) تندر90
5 سال پیش
10.46 مگابایت
نوع : pdf
بازدید : 9369
منتشرکننده : CarGeek
|
اطلاعیه معرفی خودرو ساینا اتوماتیک
5 سال پیش
1.78 مگابایت
نوع : pdf
بازدید : 3998
منتشرکننده : CarGeek
|
جزوه مونتاژ موتور EF7
5 سال پیش
10.67 مگابایت
نوع : pdf
بازدید : 24421
منتشرکننده : CarGeek
|
راهنمای عیب یابی و تعویض مجموعه کمک فنر پراید و تیبا و ساینا و کوییک
5 سال پیش
2.36 مگابایت
نوع : pdf
بازدید : 13642
منتشرکننده : CarGeek
|
راهنمای تعمیرات و سرویس سیستم ضدقفل ترمز ABS و پایداری ESP هایما
5 سال پیش
5.1 مگابایت
نوع : pdf
بازدید : 11141
منتشرکننده : CarGeek
|
راهنمای تعمیرات تزئینات داخل و داشبورد خودرو دنا- فایل 2
5 سال پیش
1.97 مگابایت
نوع : pdf
بازدید : 6797
منتشرکننده : CarGeek
|
راهنمای تعمیرات تزئینات داخل و داشبورد خودرو دنا
5 سال پیش
6.68 مگابایت
نوع : pdf
بازدید : 12292
منتشرکننده : CarGeek
|
راهنمای مدارات الکتریکی سوزوکی گرندویتارا 2000 و 2400- فایل 2
5 سال پیش
15.19 مگابایت
نوع : pdf
بازدید : 3076
منتشرکننده : CarGeek
|
راهنمای مدارات الکتریکی سوزوکی گرندویتارا 2000 و 2400
5 سال پیش
5.98 مگابایت
نوع : pdf
بازدید : 12451
منتشرکننده : CarGeek
|
راهنمای تعمیرات و سرویس مجموعه فرمان تیبا
5 سال پیش
2.77 مگابایت
نوع : pdf
بازدید : 9265
منتشرکننده : CarGeek
|
دفترچه راهنمای نصب پیستون ،رینگ و شاتون
5 سال پیش
1.38 مگابایت
نوع : pdf
بازدید : 52798
منتشرکننده : CarGeek
|
راهنمای تعمیرات تعلیق جلو و عقب تیبا- فایل 2
5 سال پیش
1.03 مگابایت
نوع : pdf
بازدید : 4234
منتشرکننده : CarGeek
|
راهنمای تعمیرات تعلیق جلو و عقب تیبا
5 سال پیش
2.8 مگابایت
نوع : pdf
بازدید : 9657
منتشرکننده : CarGeek
|
راهنمای مجموعه پمپ بنزین و درجه باک پراید و تیبا
5 سال پیش
1.33 مگابایت
نوع : pdf
بازدید : 47392
منتشرکننده : CarGeek
|
گزارش صنعت خودروسازی ترکیه
5 سال پیش
2.36 مگابایت
نوع : pdf
بازدید : 3651
منتشرکننده : CarGeek
|
راهنمای عیب یابی سیستم انتقال قدرت اتوماتیک مگان
5 سال پیش
1.71 مگابایت
نوع : pdf
بازدید : 4056
منتشرکننده : CarGeek
|
راهنمای سیستم های کنترل اجزاء مکانیکی مگان
5 سال پیش
2.85 مگابایت
نوع : pdf
بازدید : 4808
منتشرکننده : CarGeek
|
راهنمای تعمیرات جلو و بالای موتورهای مگان
5 سال پیش
4.81 مگابایت
نوع : pdf
بازدید : 4045
منتشرکننده : CarGeek
|
راهنمای تعمیرات اساسی جعبه دنده معمولی مگان
5 سال پیش
10.82 مگابایت
نوع : pdf
بازدید : 3916
منتشرکننده : CarGeek
|
راهنمای تعمیرات اساسی موتور سری K4 مگان
5 سال پیش
11.41 مگابایت
نوع : pdf
بازدید : 6938
منتشرکننده : CarGeek
|
راهنمای مخلوط سوخت و هوا موتور مگان
5 سال پیش
3.37 مگابایت
نوع : pdf
بازدید : 5882
منتشرکننده : CarGeek
|
شمای الکتریکی کلی مگان
5 سال پیش
1.46 مگابایت
نوع : pdf
بازدید : 14812
منتشرکننده : CarGeek
|
اطلاعات فنی عمومی موتورهای بنزینی مگان
5 سال پیش
1.08 مگابایت
نوع : pdf
بازدید : 6322
منتشرکننده : CarGeek
|
راهنمای عیب یابی جعبه دنده معمولی مگان
5 سال پیش
1.02 مگابایت
نوع : pdf
بازدید : 5572
منتشرکننده : CarGeek
|
جزوه آشنایی با سرویس و نگه داری خودرو ایساکو
5 سال پیش
4.6 مگابایت
نوع : pdf
بازدید : 5074
منتشرکننده : CarGeek
|
راهنمای تعمیرات مکانیزم ها و تجهیزات تندر90 و ساندرو
5 سال پیش
5.56 مگابایت
نوع : pdf
بازدید : 4444
منتشرکننده : CarGeek
|
راهنمای استفاده از ابزار انهدام ایربگ و پیش کشنده کمربند
5 سال پیش
0.41 مگابایت
نوع : pdf
بازدید : 3992
منتشرکننده : CarGeek
|
جدول سرویس های ادواری چانگان CS35 و ایدو
5 سال پیش
1.03 مگابایت
نوع : pdf
بازدید : 11484
منتشرکننده : CarGeek
|
راهنمای مدارات الکتریکی وانت زامیاد NI-NIB
5 سال پیش
3.61 مگابایت
نوع : pdf
بازدید : 48526
منتشرکننده : CarGeek
|
دستورالعمل بررسی و تعویض بوش و طبق پراید
5 سال پیش
1.21 مگابایت
نوع : pdf
بازدید : 19631
منتشرکننده : CarGeek
|
راهنمای عیب یابی و تعمیر کدهای خطای هایما S7 توربو
5 سال پیش
6.24 مگابایت
نوع : pdf
بازدید : 55247
منتشرکننده : CarGeek
|
راهنمای عیب یابی سیستم کنترل موتور نیسان پیکاپ و رونیز
5 سال پیش
7.52 مگابایت
نوع : pdf
بازدید : 18952
منتشرکننده : CarGeek
|
راهنمای تعمیرات اساسی گیربکس اتوماتیک تندر90 و ساندرو
5 سال پیش
11.68 مگابایت
نوع : pdf
بازدید : 5189
منتشرکننده : CarGeek
|
راهنمای کامل تعمیر و نگه داری لودر L120D ولوو
5 سال پیش
38.82 مگابایت
نوع : pdf
بازدید : 17491
منتشرکننده : CarGeek
|
راهنمای سیستم تهویه مطبوع و بخاری کوراندو
5 سال پیش
9.36 مگابایت
نوع : pdf
بازدید : 3842
منتشرکننده : CarGeek
|
راهنمای عیب یابی UCH مگان
5 سال پیش
5.32 مگابایت
نوع : pdf
بازدید : 7477
منتشرکننده : CarGeek
|
راهنمای سیستم کیسه هوا SRS نیسان قشقایی
5 سال پیش
0.71 مگابایت
نوع : pdf
بازدید : 3667
منتشرکننده : CarGeek
|
راهنمای سیستم امنیتی نیسان قشقایی
5 سال پیش
2.15 مگابایت
نوع : pdf
بازدید : 3242
منتشرکننده : CarGeek
|
راهنمای سیستم روغن کاری موتور نیسان قشقایی
5 سال پیش
1.02 مگابایت
نوع : pdf
بازدید : 4085
منتشرکننده : CarGeek
|
راهنمای سیستم گیربکس و دیفرانسیل نیسان قشقایی
5 سال پیش
5.44 مگابایت
نوع : pdf
بازدید : 5530
منتشرکننده : CarGeek
|
راهنمای سیستم خنک کننده موتور نیسان قشقایی
5 سال پیش
1.66 مگابایت
نوع : pdf
بازدید : 4971
منتشرکننده : CarGeek
|
راهنمای سیستم سوخت رسانی نیسان قشقایی
5 سال پیش
0.87 مگابایت
نوع : pdf
بازدید : 4821
منتشرکننده : CarGeek
|
راهنمای سیستم کنترل موتور نیسان قشقایی
5 سال پیش
8.45 مگابایت
نوع : pdf
بازدید : 3759
منتشرکننده : CarGeek
|
راهنمای سیستم انتقال قدرت نیسان قشقایی
5 سال پیش
3.05 مگابایت
نوع : pdf
بازدید : 3464
منتشرکننده : CarGeek
|
راهنمای مکانیک موتور نیسان قشقایی
5 سال پیش
11.25 مگابایت
نوع : pdf
بازدید : 4919
منتشرکننده : CarGeek
|
راهنمای برق و مدارهای نیسان قشقایی
5 سال پیش
1.74 مگابایت
نوع : pdf
بازدید : 6615
منتشرکننده : CarGeek
|
راهنمای الکتریک H30 Cross امدادخودرو
5 سال پیش
8.01 مگابایت
نوع : pdf
بازدید : 3814
منتشرکننده : CarGeek
|
راهنمای تعمیرات و سرویس تهویه مطبوع آریو
5 سال پیش
4.52 مگابایت
نوع : pdf
بازدید : 13159
منتشرکننده : CarGeek
|
راهنمای تعمیرات و سرویس تهویه مطبوع برلیانس H220 و H230
5 سال پیش
4.06 مگابایت
نوع : pdf
بازدید : 9996
منتشرکننده : CarGeek
|
راهنمای تعمیرات و سرویس تهویه مطبوع برلیانس H320 و H330
5 سال پیش
3.65 مگابایت
نوع : pdf
بازدید : 21647
منتشرکننده : CarGeek
|
قانون رسیدگی به تخلفات رانندگی + آئین نامه های مرتبط
5 سال پیش
1.13 مگابایت
نوع : pdf
بازدید : 3341
منتشرکننده : CarGeek
|
روش رفع صدای اضافی از سقف ساندرو
5 سال پیش
2.83 مگابایت
نوع : pdf
بازدید : 4004
منتشرکننده : CarGeek
|
روش رفع صدای اضافی از جلوبندی ساندرو
5 سال پیش
2.38 مگابایت
نوع : pdf
بازدید : 4952
منتشرکننده : CarGeek
|
راهنمای باز و بست اجزاء سیستم ترمز و کلاچ هیدرولیک تندر90
5 سال پیش
3.88 مگابایت
نوع : pdf
بازدید : 14558
منتشرکننده : CarGeek
|
راهنمای تعمیرات اکسل و پلوس سراتو
5 سال پیش
2.85 مگابایت
نوع : pdf
بازدید : 4033
منتشرکننده : CarGeek
|
راهنمای تعمیرات موتورهای سانگ یانگ کوراندو- فایل 2
5 سال پیش
10.63 مگابایت
نوع : pdf
بازدید : 5010
منتشرکننده : CarGeek
|
راهنمای تعمیرات موتورهای سانگ یانگ کوراندو
5 سال پیش
10.05 مگابایت
نوع : pdf
بازدید : 8262
منتشرکننده : CarGeek
|
راهنمای تجهیزات و تزئینات خارجی نیسان تیانا
5 سال پیش
4.15 مگابایت
نوع : pdf
بازدید : 5861
منتشرکننده : CarGeek
|
راهنمای تجهیزات و تزئینات داخلی نیسان تیانا
5 سال پیش
6.03 مگابایت
نوع : pdf
بازدید : 5580
منتشرکننده : CarGeek
|
راهنمای عملگرهای موتور دیزل زامیاد
5 سال پیش
0.38 مگابایت
نوع : pdf
بازدید : 6114
منتشرکننده : CarGeek
|
راهنمای اورهال گیربکس اتوماتیک سراتو
5 سال پیش
3.09 مگابایت
نوع : pdf
بازدید : 6365
منتشرکننده : CarGeek
|
راهنمای برق بدنه سراتو
5 سال پیش
20.38 مگابایت
نوع : pdf
بازدید : 12147
منتشرکننده : CarGeek
|
راهنمای عمومی نگه داری نیسان ماکسیما
5 سال پیش
0.94 مگابایت
نوع : pdf
بازدید : 11753
منتشرکننده : CarGeek
|
راهنمای عیب یابی سیستم تغییر فاز میل سوپاپ مگان
5 سال پیش
0.71 مگابایت
نوع : pdf
بازدید : 6325
منتشرکننده : CarGeek
|
راهنمای عیب یابی کلی مگان
5 سال پیش
0.61 مگابایت
نوع : pdf
بازدید : 20885
منتشرکننده : CarGeek
|
اطلاعیه ایراد قطعات دیسک و صفحه کلاچ 405،پارس،رانا و 206 با موتور TU5
5 سال پیش
0.41 مگابایت
نوع : pdf
بازدید : 5755
منتشرکننده : CarGeek
|
راهنمای تعمیرات میل گاردان و دیفرانسیل پادرا
5 سال پیش
4.77 مگابایت
نوع : pdf
بازدید : 8307
منتشرکننده : CarGeek
|
راهنمای تعمیرات شاسی و بدنه پادرا
5 سال پیش
1.54 مگابایت
نوع : pdf
بازدید : 3155
منتشرکننده : CarGeek
|
راهنمای تعویض قفل های سوئیچی سمند،پارس و 405
5 سال پیش
1.22 مگابایت
نوع : pdf
بازدید : 46131
منتشرکننده : CarGeek
|
راهنمای نصب روکش صندلی برلیانس سری H300
5 سال پیش
2.04 مگابایت
نوع : pdf
بازدید : 7224
منتشرکننده : CarGeek
|
راهنمای نصب سیستم اتولایت برلیانس سری H300
5 سال پیش
1.74 مگابایت
نوع : pdf
بازدید : 4529
منتشرکننده : CarGeek
|
آشنایی با سیستم ترمز EBD
5 سال پیش
0.25 مگابایت
نوع : pdf
بازدید : 3570
منتشرکننده : CarGeek
|
راهنمای نصب سیستم مالتی مدیا ، دوربین دنده عقب و GPS تندر90
5 سال پیش
3.14 مگابایت
نوع : pdf
بازدید : 10636
منتشرکننده : CarGeek
|
راهنمای تعمیرات پلوس و اکسل جلو H30 Cross
5 سال پیش
3.4 مگابایت
نوع : pdf
بازدید : 7061
منتشرکننده : CarGeek
|
راهنمای نصب کروزکنترل برلیانس سری H300
5 سال پیش
2.8 مگابایت
نوع : pdf
بازدید : 5956
منتشرکننده : CarGeek
|
فلوچارت عیب یابی بدکار کردن موتور در حالت گاز در زامیاد
5 سال پیش
1.32 مگابایت
نوع : pdf
بازدید : 5990
منتشرکننده : CarGeek
|
راهنمای نصب دزدگیر تصویری پراید ، تیبا ، ساینا- فایل 2
5 سال پیش
1.67 مگابایت
نوع : pdf
بازدید : 5200
منتشرکننده : CarGeek
|
راهنمای نصب دزدگیر تصویری پراید ، تیبا ، ساینا
5 سال پیش
4.09 مگابایت
نوع : pdf
بازدید : 20604
منتشرکننده : CarGeek
|
راهنمای نصب سیستم مالتی مدیا تیبا
5 سال پیش
5.51 مگابایت
نوع : pdf
بازدید : 9667
منتشرکننده : CarGeek
|
راهنمای کامل تعمیرات موتور H30 Cross و S30
5 سال پیش
40.23 مگابایت
نوع : pdf
بازدید : 8798
منتشرکننده : CarGeek
|
راهنمای تعمیر و نگه داری H30 Cross و S30
5 سال پیش
12.81 مگابایت
نوع : pdf
بازدید : 5412
منتشرکننده : CarGeek
|
راهنمای سیستم های الکتریکی اتاق و بدنه ریو
5 سال پیش
1.87 مگابایت
نوع : pdf
بازدید : 9968
منتشرکننده : CarGeek
|
راهنمای سیستم سوخت رسانی ریو
5 سال پیش
1.91 مگابایت
نوع : pdf
بازدید : 7027
منتشرکننده : CarGeek
|
راهنمای سیستم جرقه ، شارژ و استارت ریو
5 سال پیش
1.3 مگابایت
نوع : pdf
بازدید : 8128
منتشرکننده : CarGeek
|
فلوچارت عیب یابی روغن کم کردن موتور
5 سال پیش
0.8 مگابایت
نوع : pdf
بازدید : 6455
منتشرکننده : CarGeek
|
راهنمای تعمیرات سیستم سوخت رسانی بنزین تندر90 و ساندرو
5 سال پیش
4.63 مگابایت
نوع : pdf
بازدید : 7102
منتشرکننده : CarGeek
|
راهنمای تعمیرات و سرویس تجهیزات الکتریکی تندر90 و ساندرو
5 سال پیش
10.76 مگابایت
نوع : pdf
بازدید : 9004
منتشرکننده : CarGeek
|
رویه نصب دزدگیر ساده و تصویری آپکو پژو206 و رانا
5 سال پیش
1.83 مگابایت
نوع : pdf
بازدید : 11383
منتشرکننده : CarGeek
|
دستورالعمل تعویض حباب گیر بنزین پراید
5 سال پیش
0.53 مگابایت
نوع : pdf
بازدید : 48821
منتشرکننده : CarGeek
|
راهنمای کامل تعمیرات سوزوکی گرندویتارا
5 سال پیش
78.39 مگابایت
نوع : pdf
بازدید : 16052
منتشرکننده : CarGeek
|
نقشه های الکتریکی سمند مالتی پلکس
5 سال پیش
22.35 مگابایت
نوع : pdf
بازدید : 35261
منتشرکننده : CarGeek
|
راهنمای نصب پاورویندوز تندر90 و ساندرو
5 سال پیش
2.66 مگابایت
نوع : pdf
بازدید : 7007
منتشرکننده : CarGeek
|
راهنمای مکانیک H30 Cross امدادخودرو
5 سال پیش
5.24 مگابایت
نوع : pdf
بازدید : 4969
منتشرکننده : CarGeek
|
Shunt حالت Park Mode و Client Mode در پژو 2008 ، 301 ، 508
5 سال پیش
1.01 مگابایت
نوع : pdf
بازدید : 4186
منتشرکننده : CarGeek
|
راهنمای تعمیرات سیستم فرمان برلیانس H220وH230
5 سال پیش
5.2 مگابایت
نوع : pdf
بازدید : 13840
منتشرکننده : CarGeek
|
راهنمای تعمیرات اکسل جلو و عقب برلیانس H220وH230
5 سال پیش
5.29 مگابایت
نوع : pdf
بازدید : 5533
منتشرکننده : CarGeek
|
راهنمای تعمیرات و سرویس سیستم انتقال قدرت اتوماتیک چانگان CS35 و EADO
5 سال پیش
12 مگابایت
نوع : pdf
بازدید : 8404
منتشرکننده : CarGeek
|
راهنمای تعمیرات و سرویس کلاچ و گیربکس دستی H30 Cross
5 سال پیش
14.37 مگابایت
نوع : pdf
بازدید : 4032
منتشرکننده : CarGeek
|
راهنمای تعمیرات و سرویس گیربکس اتوماتیک H30 Cross
5 سال پیش
9.08 مگابایت
نوع : pdf
بازدید : 15060
منتشرکننده : CarGeek
|
راهنمای سیم کشی های الکتریکی جیلی امگرند X7
5 سال پیش
13.43 مگابایت
نوع : pdf
بازدید : 15905
منتشرکننده : CarGeek
|
راهنمای آموزشی ابزار و تجهیزات اندازه گیری و روش اجرایی کالیبراسیون ایساکو- فایل 2
5 سال پیش
6.85 مگابایت
نوع : pdf
بازدید : 3687
منتشرکننده : CarGeek
|
راهنمای آموزشی ابزار و تجهیزات اندازه گیری و روش اجرایی کالیبراسیون ایساکو
5 سال پیش
9.92 مگابایت
نوع : pdf
بازدید : 4143
منتشرکننده : CarGeek
|
راهنمای تعمیرات و عیب یابی سیستم هوای ورودی و سوخت رسانی هایما S7- فایل 2
5 سال پیش
2.5 مگابایت
نوع : pdf
بازدید : 4392
منتشرکننده : CarGeek
|
راهنمای تعمیرات و عیب یابی سیستم هوای ورودی و سوخت رسانی هایما S7
5 سال پیش
2.2 مگابایت
نوع : pdf
بازدید : 6614
منتشرکننده : CarGeek
|
راهنمای پیاده و سوار کردن کمک فنر ساندرو و تندر90
5 سال پیش
2.3 مگابایت
نوع : pdf
بازدید : 5785
منتشرکننده : CarGeek
|
راهنمای تعمیرات جعبه دنده دستی کامیونت ایسوزو
5 سال پیش
1.06 مگابایت
نوع : pdf
بازدید : 8171
منتشرکننده : CarGeek
|
راهنمای تنظیم جلوبندی و میزان فرمان کامیونت ایسوزو
5 سال پیش
0.29 مگابایت
نوع : pdf
بازدید : 11026
منتشرکننده : CarGeek
|
راهنمای تعمیرات مجموعه اکسل جلو کامیونت ایسوزو
5 سال پیش
0.5 مگابایت
نوع : pdf
بازدید : 9879
منتشرکننده : CarGeek
|
راهنمای تعمیرات میل گاردان کامیونت ایسوزو
5 سال پیش
0.26 مگابایت
نوع : pdf
بازدید : 5783
منتشرکننده : CarGeek
|
اطلاعات کلی تعمیرات میل گاردان و اکسل کامیونت ایسوزو
5 سال پیش
0.32 مگابایت
نوع : pdf
بازدید : 7483
منتشرکننده : CarGeek
|
لیست ایرادات نرم افزاری و رویه رفع آن ها در خانواده خودروی پژو206
5 سال پیش
0.35 مگابایت
نوع : pdf
بازدید : 6344
منتشرکننده : CarGeek
|
اطلاعیه نشتی گازهای خروجی سورن و دنا EF7 توربو
5 سال پیش
0.37 مگابایت
نوع : pdf
بازدید : 6473
منتشرکننده : CarGeek
|
راهنمای تعمیرات جعبه دنده دستی برلیانس سری H300
5 سال پیش
4.92 مگابایت
نوع : pdf
بازدید : 4262
منتشرکننده : CarGeek
|
راهنمای تعمیرات جعبه دنده دستی برلیانس سری H200
5 سال پیش
11.97 مگابایت
نوع : pdf
بازدید : 3952
منتشرکننده : CarGeek
|
راهنمای تعمیرات سیستم تعلیق برلیانس سری H200
5 سال پیش
11.64 مگابایت
نوع : pdf
بازدید : 4966
منتشرکننده : CarGeek
|
راهنمای بررسی و عیب یابی مگان تصادف کرده
5 سال پیش
1.08 مگابایت
نوع : pdf
بازدید : 4780
منتشرکننده : CarGeek
|
دستورالعمل عیب یابی و تعویض مجموعه کمک فنر تیبا
5 سال پیش
1.37 مگابایت
نوع : pdf
بازدید : 20113
منتشرکننده : CarGeek
|
راهنمای تعمیرات برق و الکتریک سپند
5 سال پیش
8.88 مگابایت
نوع : pdf
بازدید : 24456
منتشرکننده : CarGeek
|
راهنمای تعمیرات موتور سپند
5 سال پیش
21.88 مگابایت
نوع : pdf
بازدید : 9576
منتشرکننده : CarGeek
|
راهنمای تعمیرات انتقال قدرت سپند
5 سال پیش
11.77 مگابایت
نوع : pdf
بازدید : 6361
منتشرکننده : CarGeek
|
آشنایی با سیستم HAC و DAC
5 سال پیش
0.34 مگابایت
نوع : pdf
بازدید : 3901
منتشرکننده : CarGeek
|
دستورالعمل عیب یابی روغن سوزی موتور پراید و تیبا
5 سال پیش
1.43 مگابایت
نوع : pdf
بازدید : 12678
منتشرکننده : CarGeek
|
راهنمای عیب یابی و تعویض شیرانبساط پراید
5 سال پیش
1.59 مگابایت
نوع : pdf
بازدید : 31649
منتشرکننده : CarGeek
|
راهنمای تعمیرات سیستم فرمان سراتو
5 سال پیش
8.35 مگابایت
نوع : pdf
بازدید : 8112
منتشرکننده : CarGeek
|
دستورالعمل عیب یابی و تعویض جعبه فرمان هیدرولیک پراید و تیبا
5 سال پیش
3.38 مگابایت
نوع : pdf
بازدید : 18392
منتشرکننده : CarGeek
|
راهنمای مباحث عیب یابی گیربکس اتوماتیک نیسان ماکسیما
5 سال پیش
5.46 مگابایت
نوع : pdf
بازدید : 7875
منتشرکننده : CarGeek
|
راهنمای تعمیرات اکسل عقب کامیونت ایسوزو
5 سال پیش
0.69 مگابایت
نوع : pdf
بازدید : 8787
منتشرکننده : CarGeek
|
راهنمای تعمیرات الکتریک اتاق و شاسی کامیونت ایسوزو- فایل 2
5 سال پیش
1.41 مگابایت
نوع : pdf
بازدید : 4691
منتشرکننده : CarGeek
|
راهنمای تعمیرات الکتریک اتاق و شاسی کامیونت ایسوزو
5 سال پیش
2.9 مگابایت
نوع : pdf
بازدید : 12043
منتشرکننده : CarGeek
|
راهنمای تعمیرات عمومی موتور کامیونت ایسوزو
5 سال پیش
1.96 مگابایت
نوع : pdf
بازدید : 24277
منتشرکننده : CarGeek
|
راهنمای تعمیرات بدنه و تزئینات ساینا
5 سال پیش
20.54 مگابایت
نوع : pdf
بازدید : 9162
منتشرکننده : CarGeek
|
راهنمای تعمیرات اساسی گیربکس اتوماتیک چیرمن
5 سال پیش
15.17 مگابایت
نوع : pdf
بازدید : 5148
منتشرکننده : CarGeek
|
راهنمای تعمیرات اساسی موتور 6سیلندر چیرمن
5 سال پیش
4.47 مگابایت
نوع : pdf
بازدید : 6391
منتشرکننده : CarGeek
|
دستورالعمل رفع عیب نوسان دور موتور در دور آرام تندر90
5 سال پیش
0.41 مگابایت
نوع : pdf
بازدید : 9309
منتشرکننده : CarGeek
|
راهنمای کامل تعمیرات موتور EF7
5 سال پیش
8.65 مگابایت
نوع : pdf
بازدید : 34751
منتشرکننده : CarGeek
|
راهنمای عیب یابی تجهیزات و آپشن های سراتو
5 سال پیش
19.05 مگابایت
نوع : pdf
بازدید : 29406
منتشرکننده : CarGeek
|
فلوچارت عیب یابی صدای فرمان هنگام چرخش
5 سال پیش
0.72 مگابایت
نوع : pdf
بازدید : 6872
منتشرکننده : CarGeek
|
راهنمای نقشه خوانی مدارهای الکتریکی JAC
5 سال پیش
2.31 مگابایت
نوع : pdf
بازدید : 8673
منتشرکننده : CarGeek
|
راهنمای تعمیرات و عیب یابی سیستم انتقال قدرت دستی چانگان CS35 و EADO
5 سال پیش
11.26 مگابایت
نوع : pdf
بازدید : 4682
منتشرکننده : CarGeek
|
راهنمای تعمیرات و عیب یابی سیستم ترمز برلیانس H220 و H230
5 سال پیش
16.75 مگابایت
نوع : pdf
بازدید : 10065
منتشرکننده : CarGeek
|
دستورالعمل تعویض مفصل فرمان (سیبک درونی فرمان) پراید و تیبا
5 سال پیش
1.77 مگابایت
نوع : pdf
بازدید : 14880
منتشرکننده : CarGeek
|
راهنمای پایه های نگه دارنده موتور ساندرو
5 سال پیش
0.54 مگابایت
نوع : pdf
بازدید : 3470
منتشرکننده : CarGeek
|
راهنمای تعمیرات و سرویس سیستم استارتر و شارژ ساندرو
5 سال پیش
1.59 مگابایت
نوع : pdf
بازدید : 6751
منتشرکننده : CarGeek
|
راهنمای تعمیرات و سرویس کیسه هوا و پیش کشنده کمربند ایمنی ساندرو
5 سال پیش
1.52 مگابایت
نوع : pdf
بازدید : 4828
منتشرکننده : CarGeek
|
راهنمای تعمیرات و سرویس سیستم تهویه مطبوع (کولر و بخاری) ساندرو
5 سال پیش
4.36 مگابایت
نوع : pdf
بازدید : 10297
منتشرکننده : CarGeek
|
راهنمای تعمیرات و سرویس تزئینات خارجی برلیانس H320
5 سال پیش
2.24 مگابایت
نوع : pdf
بازدید : 3722
منتشرکننده : CarGeek
|
راهنمای تعمیرات و سرویس تزئینات داخلی و خارجی برلیانس H220
5 سال پیش
11.2 مگابایت
نوع : pdf
بازدید : 5937
منتشرکننده : CarGeek
|
راهنمای تعمیرات و سرویس تزئینات داخلی و خارجی برلیانس H230
5 سال پیش
11.92 مگابایت
نوع : pdf
بازدید : 4939
منتشرکننده : CarGeek
|
راهنمای تعمیرات و سرویس تزئینات داخلی برلیانس H320
5 سال پیش
8.22 مگابایت
نوع : pdf
بازدید : 7285
منتشرکننده : CarGeek
|
راهنمای تعمیرات و سرویس سیستم الکتریکی موتور چانگان EADO و CS35
5 سال پیش
18.29 مگابایت
نوع : pdf
بازدید : 5141
منتشرکننده : CarGeek
|
راهنمای مدارهای الکتریکی آریو S300
5 سال پیش
9.13 مگابایت
نوع : pdf
بازدید : 20247
منتشرکننده : CarGeek
|
راهنمای تعمیرات سیستم تعلیق برلیانس v5
5 سال پیش
7.56 مگابایت
نوع : pdf
بازدید : 3957
منتشرکننده : CarGeek
|
نقشه های الکتریکی هایما S7 توربو
5 سال پیش
19.83 مگابایت
نوع : pdf
بازدید : 15666
منتشرکننده : CarGeek
|
جزوه دوره آموزش فنی هایما
5 سال پیش
4.74 مگابایت
نوع : pdf
بازدید : 6596
منتشرکننده : CarGeek
|
راهنمای تعمیرات بدنه و تجهیزات برلیانس H220
5 سال پیش
7.85 مگابایت
نوع : pdf
بازدید : 5695
منتشرکننده : CarGeek
|
دفترچه راهنمای تویوتا پریوس
5 سال پیش
10.5 مگابایت
نوع : pdf
بازدید : 18842
منتشرکننده : CarGeek
|
دفترچه راهنمای تویوتا CH-R توربو
5 سال پیش
18.24 مگابایت
نوع : pdf
بازدید : 11961
منتشرکننده : CarGeek
|
راهنمای کارگاهی سیستم استارت دکمه ای سراتو
5 سال پیش
6.12 مگابایت
نوع : pdf
بازدید : 7787
منتشرکننده : CarGeek
|
راهنمای تعمیرات و سرویس سیستم تعلیق چانگان CS35
5 سال پیش
4.12 مگابایت
نوع : pdf
بازدید : 4959
منتشرکننده : CarGeek
|
راهنمای آموزش سیستم فرمان هیوندای- فایل 2
5 سال پیش
2 مگابایت
نوع : pdf
بازدید : 6054
منتشرکننده : CarGeek
|
راهنمای آموزش سیستم فرمان هیوندای
5 سال پیش
0.47 مگابایت
نوع : pdf
بازدید : 8928
منتشرکننده : CarGeek
|
راهنمای پیکربندی نودهای دنا اکوماکس
5 سال پیش
0.5 مگابایت
نوع : pdf
بازدید : 12493
منتشرکننده : CarGeek
|
راهنمای تعمیرات و سرویس سیستم سوخت رسانی برلیانس سری H200-H300
5 سال پیش
4.79 مگابایت
نوع : pdf
بازدید : 9299
منتشرکننده : CarGeek
|
راهنمای کارگاهی سیستم کلید هوشمند سراتو
5 سال پیش
8.41 مگابایت
نوع : pdf
بازدید : 6606
منتشرکننده : CarGeek
|
دستورالعمل عیب یابی و تعویض بلوک سیلندر تیبا
5 سال پیش
1.31 مگابایت
نوع : pdf
بازدید : 19292
منتشرکننده : CarGeek
|
دستورالعمل عیب یابی و تعویض سرسیلندر تیبا
5 سال پیش
1.65 مگابایت
نوع : pdf
بازدید : 11802
منتشرکننده : CarGeek
|
راهنمای فارسی آموزشی ترمز هیوندای- فایل 2
5 سال پیش
0.77 مگابایت
نوع : pdf
بازدید : 4550
منتشرکننده : CarGeek
|
راهنمای فارسی آموزشی ترمز هیوندای
5 سال پیش
0.81 مگابایت
نوع : pdf
بازدید : 9222
منتشرکننده : CarGeek
|
راهنمای مدارهای الکتریکی ساینا
5 سال پیش
25.55 مگابایت
نوع : pdf
بازدید : 42350
منتشرکننده : CarGeek
|
راهنمای تجهیزات الکتریکی ساینا
5 سال پیش
8.46 مگابایت
نوع : pdf
بازدید : 16109
منتشرکننده : CarGeek
|
راهنمای فارسی آموزشی مکانیک موتور هیوندای
5 سال پیش
2.09 مگابایت
نوع : pdf
بازدید : 17903
منتشرکننده : CarGeek
|
اطلاعیه فنی معرفی دنا پلاس
5 سال پیش
8.62 مگابایت
نوع : pdf
بازدید : 7513
منتشرکننده : CarGeek
|
معرفی و نکات نگه داری صحیح تایرهای راهسازی و معدن
5 سال پیش
6.22 مگابایت
نوع : pdf
بازدید : 5268
منتشرکننده : CarGeek
|
راهنما و نقشه دسته سیم EKS تیبا
5 سال پیش
5.03 مگابایت
نوع : pdf
بازدید : 25760
منتشرکننده : CarGeek
|
راهنمای سرویس های عمومی و ادواری برلیانس V5
5 سال پیش
21.22 مگابایت
نوع : pdf
بازدید : 4317
منتشرکننده : CarGeek
|
لیست سرویس های ادواری و تکمیلی برلیانس V5
5 سال پیش
0.33 مگابایت
نوع : pdf
بازدید : 2987
منتشرکننده : CarGeek
|
راهنمای تعمیرات و سرویس سیستم فرمان هیدرولیک چانگان ایدو (EADO)
5 سال پیش
7.89 مگابایت
نوع : pdf
بازدید : 3701
منتشرکننده : CarGeek
|
راهنمای تعمیرات سیستم انژکتوری پادرا
5 سال پیش
5.71 مگابایت
نوع : pdf
بازدید : 3655
منتشرکننده : CarGeek
|
نقشه شماتیک کروزکنترل دنا
5 سال پیش
0.25 مگابایت
نوع : pdf
بازدید : 7527
منتشرکننده : CarGeek
|
نقشه های الکتریکی خودروهای CNG با کیت گازسوز OMVL و ECUبنزین S2000
5 سال پیش
0.38 مگابایت
نوع : pdf
بازدید : 25057
منتشرکننده : CarGeek
|
جزوه آموزشی پژو207 اتوماتیک P7L
5 سال پیش
2.75 مگابایت
نوع : pdf
بازدید : 6217
منتشرکننده : CarGeek
|
اطلاعیه رفع مشکل خالی شدن باتری در کیلومتر پائین سری X200
5 سال پیش
3.01 مگابایت
نوع : pdf
بازدید : 5524
منتشرکننده : CarGeek
|
راهنمای تعمیرات صفحه نشانگرهای مگان
5 سال پیش
1.29 مگابایت
نوع : pdf
بازدید : 7806
منتشرکننده : CarGeek
|
جزوه آموزشی و عیب یابی سیستم صوتی و تصویری (مالتی مدیا) خودرو دنا
5 سال پیش
5.46 مگابایت
نوع : pdf
بازدید : 29036
منتشرکننده : CarGeek
|
راهنمای فیوزها و رله های پژو 301 و 508
5 سال پیش
1.92 مگابایت
نوع : pdf
بازدید : 6076
منتشرکننده : CarGeek
|
معرفی مشخصات فنی خودرو پژو 301
5 سال پیش
0.5 مگابایت
نوع : pdf
بازدید : 4140
منتشرکننده : CarGeek
|
راهنمای استفاده از میکرومتر
5 سال پیش
1.78 مگابایت
نوع : pdf
بازدید : 3878
منتشرکننده : CarGeek
|
راهنمای کامل مدارهای الکتریکی چانگان CS35- فایل 2
5 سال پیش
4.03 مگابایت
نوع : pdf
بازدید : 3949
منتشرکننده : CarGeek
|
راهنمای کامل مدارهای الکتریکی چانگان CS35
5 سال پیش
17.95 مگابایت
نوع : pdf
بازدید : 18107
منتشرکننده : CarGeek
|
راهنمای سیستم الکتریکی بدنه چانگان CS35
5 سال پیش
7.48 مگابایت
نوع : pdf
بازدید : 4114
منتشرکننده : CarGeek
|
راهنمای تعمیرات کیسه هوا چانگان CS35
5 سال پیش
2.93 مگابایت
نوع : pdf
بازدید : 6086
منتشرکننده : CarGeek
|
جزوه آموزشی معرفی فنی رنو کپچر
5 سال پیش
1.91 مگابایت
نوع : pdf
بازدید : 3488
منتشرکننده : CarGeek
|
سرویس های ادواری و تکمیلی خودروهای برلیانس گروه H200 و H300
5 سال پیش
0.36 مگابایت
نوع : pdf
بازدید : 6401
منتشرکننده : CarGeek
|
جزوه آموزشی ویژگی های مکانیکی و الکترونیکی پژو 407
5 سال پیش
1.12 مگابایت
نوع : pdf
بازدید : 3931
منتشرکننده : CarGeek
|
عیب یابی ایراد روشن نشدن موتور دیزل زامیاد- فایل 2
5 سال پیش
0.44 مگابایت
نوع : pdf
بازدید : 4026
منتشرکننده : CarGeek
|
عیب یابی ایراد روشن نشدن موتور دیزل زامیاد
5 سال پیش
0.35 مگابایت
نوع : pdf
بازدید : 7850
منتشرکننده : CarGeek
|
کدهای خطای دیاگ زامیاد دیزل
5 سال پیش
0.07 مگابایت
نوع : pdf
بازدید : 12622
منتشرکننده : CarGeek
|
راهنمای تعمیرات گیربکس نیسان زامیاد
5 سال پیش
3.37 مگابایت
نوع : pdf
بازدید : 24731
منتشرکننده : CarGeek
|
راهنمای تعمیرات کنترل موتور ،سیستم سوخت و اگزوز نیسان زامیاد
5 سال پیش
1.67 مگابایت
نوع : pdf
بازدید : 9162
منتشرکننده : CarGeek
|
راهنمای تعمیرات سیستم سوخت موتور و کاربراتور نیسان زامیاد
5 سال پیش
1.2 مگابایت
نوع : pdf
بازدید : 47252
منتشرکننده : CarGeek
|
راهنمای تعمیرات اکسل و فنربندی جلو نیسان زامیاد
5 سال پیش
1.75 مگابایت
نوع : pdf
بازدید : 16622
منتشرکننده : CarGeek
|
راهنمای تعمیرات و سرویس موتور نیسان زامیاد
5 سال پیش
6.1 مگابایت
نوع : pdf
بازدید : 38725
منتشرکننده : CarGeek
|
راهنمای تعمیرات الکتریک بدنه نیسان زامیاد
5 سال پیش
7.89 مگابایت
نوع : pdf
بازدید : 5934
منتشرکننده : CarGeek
|
راهنمای تعمیرات اکسل و فنربندی عقب نیسان زامیاد
5 سال پیش
1.76 مگابایت
نوع : pdf
بازدید : 15154
منتشرکننده : CarGeek
|
راهنمای تعمیرات و سرویس سیستم سوخت رسانی چانگان CS35
5 سال پیش
9.91 مگابایت
نوع : pdf
بازدید : 6585
منتشرکننده : CarGeek
|
راهنمای تعمیرات سیستم تهویه مطبوع چانگان CS35
5 سال پیش
6.91 مگابایت
نوع : pdf
بازدید : 9961
منتشرکننده : CarGeek
|
راهنمای اطلاعات عمومی تعمیر و نگه داری چانگان CS35
5 سال پیش
3.77 مگابایت
نوع : pdf
بازدید : 9592
منتشرکننده : CarGeek
|
راهنمای تعمیرات و سرویس سیستم الکتریکی موتور چانگان CS35
5 سال پیش
19.28 مگابایت
نوع : pdf
بازدید : 4058
منتشرکننده : CarGeek
|
نقشه های سیم کشی برلیانس C3
5 سال پیش
14.84 مگابایت
نوع : pdf
بازدید : 6041
منتشرکننده : CarGeek
|
چیدمان رله و فیوزهای پژو 207 جدید P7L
5 سال پیش
0.48 مگابایت
نوع : pdf
بازدید : 34101
منتشرکننده : CarGeek
|
راهنمای تعمیرات موتور پژو روآ سال
5 سال پیش
2.06 مگابایت
نوع : pdf
بازدید : 37885
منتشرکننده : CarGeek
|
کاتالوگ رسمی پژو 508 ایکاپ
5 سال پیش
4.85 مگابایت
نوع : pdf
بازدید : 3582
منتشرکننده : CarGeek
|
لیست سرویس های دوره ای و تکمیلی تندر90 ، مگان و ساندرو
5 سال پیش
3 مگابایت
نوع : pdf
بازدید : 7961
منتشرکننده : CarGeek
|
راهنمای تعمیرات موتورهای X33
5 سال پیش
27.99 مگابایت
نوع : pdf
بازدید : 19739
منتشرکننده : CarGeek
|
کتاب Automotive Science and Mathematics
5 سال پیش
4.87 مگابایت
نوع : pdf
بازدید : 3637
منتشرکننده : CarGeek
|
کتاب Repair of Vehicle Bodies
5 سال پیش
26.68 مگابایت
نوع : pdf
بازدید : 3499
منتشرکننده : CarGeek
|
کتاب Springer Handbook of Mechanical Engineering
5 سال پیش
66.77 مگابایت
نوع : pdf
بازدید : 3714
منتشرکننده : CarGeek
|
کتاب Automotive Engineering: Powertrain, Chassis System and Vehicle Body
5 سال پیش
52.53 مگابایت
نوع : pdf
بازدید : 3561
منتشرکننده : CarGeek
|
کتاب Two-Stroke Engine Repair & Maintenance
5 سال پیش
5.33 مگابایت
نوع : pdf
بازدید : 3313
منتشرکننده : CarGeek
|
راهنمای عیب یابی موتور دیزل زامیاد
5 سال پیش
0.25 مگابایت
نوع : pdf
بازدید : 19467
منتشرکننده : CarGeek
|
راهنمای عیب یابی بدنه و آزمون های آب بندی مگان
5 سال پیش
0.82 مگابایت
نوع : pdf
بازدید : 3619
منتشرکننده : CarGeek
|
راهنمای سوخت رسانی و کنترل موتور ون غزال
5 سال پیش
2.7 مگابایت
نوع : pdf
بازدید : 9154
منتشرکننده : CarGeek
|
جزوه آموزشی برق خودرو کپچر
5 سال پیش
6.79 مگابایت
نوع : pdf
بازدید : 6338
منتشرکننده : CarGeek
|
راهنمای عیب یابی سوخت رسانی مگان- فایل 2
5 سال پیش
1.38 مگابایت
نوع : pdf
بازدید : 4126
منتشرکننده : CarGeek
|
راهنمای عیب یابی سوخت رسانی مگان
5 سال پیش
1.69 مگابایت
نوع : pdf
بازدید : 8129
منتشرکننده : CarGeek
|
راهنمای قطعات و مدارهای الکتریکی وانت ریچ
5 سال پیش
13.41 مگابایت
نوع : pdf
بازدید : 19517
منتشرکننده : CarGeek
|
علل آتش سوزی تانکرهای سوخت در جایگاه های پمپ بنزین
5 سال پیش
1.02 مگابایت
نوع : pdf
بازدید : 4046
منتشرکننده : CarGeek
|
راهنمای عیب یابی بخاری و ایرکاندیشن ماکسیما
5 سال پیش
3.91 مگابایت
نوع : pdf
بازدید : 8528
منتشرکننده : CarGeek
|
راهنمای عیب یابی و شرح کدهای خطای سیستم کنترل موتور ماکسیما
5 سال پیش
14.64 مگابایت
نوع : pdf
بازدید : 8546
منتشرکننده : CarGeek
|
راهنمای عیب یابی سیستم الکتریکی ماکسیما
5 سال پیش
3.27 مگابایت
نوع : pdf
بازدید : 8562
منتشرکننده : CarGeek
|
مروری بر مشخصات فنی موتور پژو 2008
5 سال پیش
1.14 مگابایت
نوع : pdf
بازدید : 4784
منتشرکننده : CarGeek
|
راهنمای حوادث و سوانح حمل و نقل جاده ای
5 سال پیش
8.75 مگابایت
نوع : pdf
بازدید : 3613
منتشرکننده : CarGeek
|
جزوه دوره عمومی امداد و نجات در تصادفات
5 سال پیش
12.44 مگابایت
نوع : pdf
بازدید : 11630
منتشرکننده : CarGeek
|
راهنمای آموزش عمومی اطفاء حریق
5 سال پیش
53.96 مگابایت
نوع : pdf
بازدید : 3337
منتشرکننده : CarGeek
|
عیب یابی باد گرم کولر خودرو
5 سال پیش
0.84 مگابایت
نوع : pdf
بازدید : 31526
منتشرکننده : CarGeek
|
تحلیل روش های مختلف جهت بهبود آیرودینامیک خودرو
5 سال پیش
1.31 مگابایت
نوع : pdf
بازدید : 3611
منتشرکننده : CarGeek
|
معرفی و آشنایی با موتور M13 GS Euro4 خودروهای گروه X100
5 سال پیش
3 مگابایت
نوع : pdf
بازدید : 19928
منتشرکننده : CarGeek
|
دستورالعمل عیب یابی پمپ هیدرولیک فرمان پژو 206 و 405
5 سال پیش
0.58 مگابایت
نوع : pdf
بازدید : 19201
منتشرکننده : CarGeek
|
ویژگی های گیربکس اتوماتیک AL4
5 سال پیش
2.94 مگابایت
نوع : pdf
بازدید : 5617
منتشرکننده : CarGeek
|
دستورالعمل تعویض موتور فن رادیاتور 2 دور
5 سال پیش
2.34 مگابایت
نوع : pdf
بازدید : 78306
منتشرکننده : CarGeek
|
دستورالعمل بازکردن و دانلود پنل پژو 206 P6L
5 سال پیش
1.34 مگابایت
نوع : pdf
بازدید : 41165
منتشرکننده : CarGeek
|
دستورالعمل شناسایی و عیب یابی تایر برای گارانتی
5 سال پیش
1.24 مگابایت
نوع : pdf
بازدید : 3885
منتشرکننده : CarGeek
|
دستورالعمل فراخوان نصب تسمه های نگه دارنده باک خودرو 151 (پراید وانت)
5 سال پیش
1.57 مگابایت
نوع : pdf
بازدید : 3780
منتشرکننده : CarGeek
|
دستورالعمل عیب یابی داغ شدن چرخ های عقب خودروهای برلیانس سری H300
5 سال پیش
0.76 مگابایت
نوع : pdf
بازدید : 4803
منتشرکننده : CarGeek
|
اطلاعیه نحو رفع ایراد یکسره شدن گرمکن صندلی لیفان 820
5 سال پیش
0.98 مگابایت
نوع : pdf
بازدید : 4572
منتشرکننده : CarGeek
|
راهنمای آموزشی مبانی الکتریک خودرو KIA
5 سال پیش
8.94 مگابایت
نوع : pdf
بازدید : 4313
منتشرکننده : CarGeek
|
راهنمای BM34 پژو 206
5 سال پیش
1.46 مگابایت
نوع : pdf
بازدید : 47658
منتشرکننده : CarGeek
|
کتابچه اطلاعات تعمیراتی لیفان X60
5 سال پیش
1.89 مگابایت
نوع : pdf
بازدید : 4370
منتشرکننده : CarGeek
|
راهنمای کلی تعمیر و نگه داری مکانیکی و الکتریکی پژو 407
5 سال پیش
1.17 مگابایت
نوع : pdf
بازدید : 8943
منتشرکننده : CarGeek
|
راهنمای تعمیرات تجهیزات الکتریکی سایپا 151 (وانت پراید)
5 سال پیش
11.92 مگابایت
نوع : pdf
بازدید : 5208
منتشرکننده : CarGeek
|
راهنمای تعمیرات مدارهای الکتریکی سایپا 151 (وانت پراید)
5 سال پیش
6.46 مگابایت
نوع : pdf
بازدید : 15171
منتشرکننده : CarGeek
|
راهنمای تعمیرات بدنه و تزئینات سایپا 151 (وانت پراید)
5 سال پیش
6.69 مگابایت
نوع : pdf
بازدید : 19393
منتشرکننده : CarGeek
|
راهنمای تعمیرات فرمان ، تعلیق و اکسل های سایپا 151 (وانت پراید)
5 سال پیش
16.87 مگابایت
نوع : pdf
بازدید : 8175
منتشرکننده : CarGeek
|
راهنمای تعمیرات انتقال قدرت سایپا 151 (وانت پراید)
5 سال پیش
22.66 مگابایت
نوع : pdf
بازدید : 6147
منتشرکننده : CarGeek
|
راهنمای تعمیرات سیستم سوخت رسانی سایپا 151 (وانت پراید)
5 سال پیش
6.84 مگابایت
نوع : pdf
بازدید : 30233
منتشرکننده : CarGeek
|
راهنمای تعمیرات موتور سایپا 151 (وانت پراید)
5 سال پیش
16.78 مگابایت
نوع : pdf
بازدید : 9846
منتشرکننده : CarGeek
|
فلوچارت عیب یابی خودرو استارت نمی زند
5 سال پیش
0.5 مگابایت
نوع : pdf
بازدید : 8120
منتشرکننده : CarGeek
|
راهنمای عیب یابی سیستم تهویه مطبوع خودروی تیبا
5 سال پیش
3.94 مگابایت
نوع : pdf
بازدید : 17780
منتشرکننده : CarGeek
|
کتابچه راهنمای تعمیرات لندمارک و کاپرا
5 سال پیش
19.4 مگابایت
نوع : pdf
بازدید : 35177
منتشرکننده : CarGeek
|
راهنمای تعمیرات سیستم ضدسرقت مجهز به استارت دکمه ای برلیانس v5
5 سال پیش
3.56 مگابایت
نوع : pdf
بازدید : 4994
منتشرکننده : CarGeek
|
راهنمای تعمیرات تزئینات خارجی برلیانس v5
5 سال پیش
3.56 مگابایت
نوع : pdf
بازدید : 3597
منتشرکننده : CarGeek
|
راهنمای تعمیرات تزئینات داخلی برلیانس v5
5 سال پیش
8.4 مگابایت
نوع : pdf
بازدید : 4233
منتشرکننده : CarGeek
|
دیاگرام های سیم کشی برلیانس v5
5 سال پیش
16.41 مگابایت
نوع : pdf
بازدید : 4610
منتشرکننده : CarGeek
|
معرفی و آشنایی با خودرو برلیانس v5
5 سال پیش
0.67 مگابایت
نوع : pdf
بازدید : 3714
منتشرکننده : CarGeek
|
جزوه کارگاه اتومکانیک موتور
5 سال پیش
2.06 مگابایت
نوع : pdf
بازدید : 9874
منتشرکننده : CarGeek
|
آشنایی با قطعات پرکاربرد در الکترونیک
5 سال پیش
2.1 مگابایت
نوع : pdf
بازدید : 5570
منتشرکننده : CarGeek
|
راهنمای آموزشی برق پژو پارس،405 و RD (مبانی برق و اصول نقشه خوانی)
5 سال پیش
41.22 مگابایت
نوع : pdf
بازدید : 23794
منتشرکننده : CarGeek
|
راهنمای تعمیرات و عیب یابی گیربکس اتوماتیک برلیانس H230 وH330
5 سال پیش
5.7 مگابایت
نوع : pdf
بازدید : 15027
منتشرکننده : CarGeek
|
آموزش تعویض فوم صندلی پژو 206
5 سال پیش
0.91 مگابایت
نوع : pdf
بازدید : 6508
منتشرکننده : CarGeek
|
معرفی و آشنایی با خودرو سایپا 212 (سایپا کوییک)
5 سال پیش
1.34 مگابایت
نوع : pdf
بازدید : 15281
منتشرکننده : CarGeek
|
معرفی و آشنایی به خودرو برلیانس H320 کراس
5 سال پیش
1.12 مگابایت
نوع : pdf
بازدید : 5372
منتشرکننده : CarGeek
|
گزارش راهنمای کارگاه عیب یابی خودرو
5 سال پیش
0.37 مگابایت
نوع : pdf
بازدید : 4250
منتشرکننده : CarGeek
|
نحوه تبدیل اعداد هگز به دسیمال بدون ماشین حساب
5 سال پیش
0.24 مگابایت
نوع : pdf
بازدید : 3233
منتشرکننده : CarGeek
|
اطلاعیه معرفی خودرو سراتو آپشنال
5 سال پیش
1.43 مگابایت
نوع : pdf
بازدید : 3648
منتشرکننده : CarGeek
|
دستورالعمل فراخوان اصلاح دسته سيم کنار رله باکس تیبا و ساینا
5 سال پیش
1.65 مگابایت
نوع : pdf
بازدید : 14120
منتشرکننده : CarGeek
|
نقشه های برق رنو میدلام
5 سال پیش
2.28 مگابایت
نوع : pdf
بازدید : 23323
منتشرکننده : CarGeek
|
جزوه دوره آموزشی مکانیک عمومی خودرو
5 سال پیش
3.15 مگابایت
نوع : pdf
بازدید : 9589
منتشرکننده : CarGeek
|
جزوه آموزشی تعلیق و فرمان
5 سال پیش
2.27 مگابایت
نوع : pdf
بازدید : 19143
منتشرکننده : CarGeek
|
راهنمای آموزشی دوره تعمیرات ECU
5 سال پیش
5.13 مگابایت
نوع : pdf
بازدید : 13966
منتشرکننده : CarGeek
|
جزوه فلزکاری و اندازه گیری تعمیرات مکانیکی
5 سال پیش
2.08 مگابایت
نوع : pdf
بازدید : 8425
منتشرکننده : CarGeek
|
راهنمای تعمیرات بدنه تندر90
5 سال پیش
11.86 مگابایت
نوع : pdf
بازدید : 4107
منتشرکننده : CarGeek
|
راهنمای شستشوی استکان تایپیت های موتور TU5
5 سال پیش
1.35 مگابایت
نوع : pdf
بازدید : 8185
منتشرکننده : CarGeek
|
راهنمای باز کردن گیربکس پژو 206 از روی خودرو
5 سال پیش
1.46 مگابایت
نوع : pdf
بازدید : 25184
منتشرکننده : CarGeek
|
راهنمای دسته سیم های جک S5
5 سال پیش
5.73 مگابایت
نوع : pdf
بازدید : 7677
منتشرکننده : CarGeek
|
راهنمای تصویری عیب یابی روشن نشدن خودرو و چراغ چک برلیانس H300
5 سال پیش
1.43 مگابایت
نوع : pdf
بازدید : 13893
منتشرکننده : CarGeek
|
جزوه آموزشی خودرو هایما S7 توربو
5 سال پیش
3.9 مگابایت
نوع : pdf
بازدید : 18117
منتشرکننده : CarGeek
|
راهنمای مدارهای الکتریکی و تجهیزات جانبی الکتریکی زانتیا
5 سال پیش
8.68 مگابایت
نوع : pdf
بازدید : 39744
منتشرکننده : CarGeek
|
راهنمای عیب یابی گیربکس اتوماتیک ماکسیما
5 سال پیش
9.05 مگابایت
نوع : pdf
بازدید : 8200
منتشرکننده : CarGeek
|
راهنمای آموزشی گیربکس اتوماتیک 8سرعته A8LR1 کیا
5 سال پیش
4.1 مگابایت
نوع : pdf
بازدید : 5134
منتشرکننده : CarGeek
|
راهنمای تبدیل ECU
5 سال پیش
0.28 مگابایت
نوع : pdf
بازدید : 12135
منتشرکننده : CarGeek
|
نقشه های الکتریکی سمند
5 سال پیش
22.38 مگابایت
نوع : pdf
بازدید : 84622
منتشرکننده : CarGeek
|
شماتیک دیاگرام ECU VALEO J34P موتورهای TU3A پژو206
5 سال پیش
0.84 مگابایت
نوع : pdf
بازدید : 8747
منتشرکننده : CarGeek
|
نقشه سوخت رسانی زامیاد بنزینی یورو4
5 سال پیش
0.15 مگابایت
نوع : pdf
بازدید : 15729
منتشرکننده : CarGeek
|
بررسی و عیب یابی مشکلات متداول گیربکس های پژو
5 سال پیش
1.13 مگابایت
نوع : pdf
بازدید : 7621
منتشرکننده : CarGeek
|
دستورالعمل نحوه انجام و صدور برگه معاینه فنی خودروهای سنگین
5 سال پیش
0.8 مگابایت
نوع : pdf
بازدید : 8151
منتشرکننده : CarGeek
|
دستورالعمل شرایط،ضوابط و ارزیابی خدمات پس از فروش صنعت خودرو
5 سال پیش
1.76 مگابایت
نوع : pdf
بازدید : 6679
منتشرکننده : CarGeek
|
راهنمای تعمیرات تجهیزات الکتریکی و رفاهی مزدا3
5 سال پیش
19.25 مگابایت
نوع : pdf
بازدید : 4630
منتشرکننده : CarGeek
|
Hydraulics Study Guide
5 سال پیش
3.37 مگابایت
نوع : pdf
بازدید : 3216
منتشرکننده : CarGeek
|
راهنمای تعمیرات پلوس JAC S5
5 سال پیش
1.6 مگابایت
نوع : pdf
بازدید : 4994
منتشرکننده : CarGeek
|
دیتاشیت و مسیرهای ECU SSAT
5 سال پیش
59.61 مگابایت
نوع : pdf
بازدید : 20809
منتشرکننده : CarGeek
|
راهنمای سیستم انژکتور لیفان 520
5 سال پیش
3.15 مگابایت
نوع : pdf
بازدید : 8161
منتشرکننده : CarGeek
|
راهنمای تجهیزات و نقشه های الکتریکی لیفان 520
5 سال پیش
1.51 مگابایت
نوع : pdf
بازدید : 24941
منتشرکننده : CarGeek
|
راهنمای تعمیر و نگه داری موتور و گیربکس لیفان 520
5 سال پیش
10.52 مگابایت
نوع : pdf
بازدید : 9980
منتشرکننده : CarGeek
|
راهنمای تعمیرات،معرفی و جانمایی دسته سیم های رانا فاز صفر،یک و LX- فایل 2
5 سال پیش
1.7 مگابایت
نوع : pdf
بازدید : 3714
منتشرکننده : CarGeek
|
راهنمای تعمیرات،معرفی و جانمایی دسته سیم های رانا فاز صفر،یک و LX
5 سال پیش
2.04 مگابایت
نوع : pdf
بازدید : 7120
منتشرکننده : CarGeek
|
لیست و قیمت IC های موجود در انواع ECU
5 سال پیش
0.96 مگابایت
نوع : pdf
بازدید : 14350
منتشرکننده : CarGeek
|
راهنمای تعمیرات،معرفی و جانمایی دسته سیم های الکتریکی سمند، سورن و دنا
5 سال پیش
4.37 مگابایت
نوع : pdf
بازدید : 24752
منتشرکننده : CarGeek
|
اصول عملکرد و راهنمای عیب یابی استپر موتور
5 سال پیش
6.67 مگابایت
نوع : pdf
بازدید : 14862
منتشرکننده : CarGeek
|
راهنمای تعمیراتو عیب یابی سیستم تهویه اتوماتیک سورن ELX و پارس
5 سال پیش
1.46 مگابایت
نوع : pdf
بازدید : 40311
منتشرکننده : CarGeek
|
جزوه آموزشی وانت تندر90
5 سال پیش
2.63 مگابایت
نوع : pdf
بازدید : 7308
منتشرکننده : CarGeek
|
راهنمای تعمیرات داشبورد جدید با دو ایربگ پژو پارس
5 سال پیش
1.32 مگابایت
نوع : pdf
بازدید : 23388
منتشرکننده : CarGeek
|
راهنمای تعمیرات سریع H30 کراس
5 سال پیش
3.89 مگابایت
نوع : pdf
بازدید : 21424
منتشرکننده : CarGeek
|
آشنایی با نحوه استفاده از ترکمتر و ترکرنج
5 سال پیش
0.28 مگابایت
نوع : pdf
بازدید : 7433
منتشرکننده : CarGeek
|
راهنمای سیستم پخش و رادیو مگان
5 سال پیش
1.63 مگابایت
نوع : pdf
بازدید : 19223
منتشرکننده : CarGeek
|
نحوه رفع صدای غیرعادی فرمان خودروی برلیانس H300
5 سال پیش
0.94 مگابایت
نوع : pdf
بازدید : 10576
منتشرکننده : CarGeek
|
راهنمای تعمیرات بلوک هیدرولیک گیربکس اتوماتیک تندر90
5 سال پیش
1.09 مگابایت
نوع : pdf
بازدید : 6387
منتشرکننده : CarGeek
|
راهنمای عیب یابی کلاچ خودرو
5 سال پیش
2.05 مگابایت
نوع : pdf
بازدید : 4608
منتشرکننده : CarGeek
|
نقشه های الکتریکی تجهیزات دنا
5 سال پیش
10.24 مگابایت
نوع : pdf
بازدید : 21947
منتشرکننده : CarGeek
|
راهنمای عیب یابی سیستم انژکتور زیمنس جدید پراید
5 سال پیش
4.68 مگابایت
نوع : pdf
بازدید : 7434
منتشرکننده : CarGeek
|
راهنمای صداگیری ستون و قاب فرمان سمند
5 سال پیش
5.54 مگابایت
نوع : pdf
بازدید : 8197
منتشرکننده : CarGeek
|
آموزش نصب IC فلش روی ایسیو SSAT
5 سال پیش
0.3 مگابایت
نوع : pdf
بازدید : 4553
منتشرکننده : CarGeek
|
آشنایی با گاز طبیعی فشرده CNG و قطعات کیت گازسوز
5 سال پیش
2.8 مگابایت
نوع : pdf
بازدید : 5554
منتشرکننده : CarGeek
|
دستورالعمل عیب یابی و تعویض انباره اگزوز عقب تیبا
5 سال پیش
1.44 مگابایت
نوع : pdf
بازدید : 16462
منتشرکننده : CarGeek
|
فلوچارت عیب یابی صدای اگزوز خودرو
5 سال پیش
0.54 مگابایت
نوع : pdf
بازدید : 4871
منتشرکننده : CarGeek
|
فلوچارت عیب یابی صدای شدید خودرو در دست اندازها
5 سال پیش
0.64 مگابایت
نوع : pdf
بازدید : 13151
منتشرکننده : CarGeek
|
قیمت فروش و مجموع ارزش گمرکی و حقوق ورودی انواع خودرو تولید داخل و وارداتی
5 سال پیش
2.09 مگابایت
نوع : pdf
بازدید : 2773
منتشرکننده : CarGeek
|
معرفی فنی سایپا سراتو
5 سال پیش
0.45 مگابایت
نوع : pdf
بازدید : 4165
منتشرکننده : CarGeek
|
راهنمای تعمیرات موتور سراتو 1600
5 سال پیش
16.36 مگابایت
نوع : pdf
بازدید : 6986
منتشرکننده : CarGeek
|
راهنمای تعمیرات موتور سراتو 2000
5 سال پیش
21.76 مگابایت
نوع : pdf
بازدید : 12523
منتشرکننده : CarGeek
|
جزوه سیستم های الکتریکی و تهویه مطبوع مزدا2
5 سال پیش
15.84 مگابایت
نوع : pdf
بازدید : 3351
منتشرکننده : CarGeek
|
راهنمای تعمیرات سیستم تهویه مطبوع(بخاری و کولر) پژو405 ،پارس ،سمند ،روآ ،وانت پیکان
5 سال پیش
3.81 مگابایت
نوع : pdf
بازدید : 142495
منتشرکننده : CarGeek
|
دفترچه راهنمای ولوو FH- فایل 2
5 سال پیش
10.47 مگابایت
نوع : pdf
بازدید : 12827
منتشرکننده : CarGeek
|
دفترچه راهنمای ولوو FH
5 سال پیش
1.84 مگابایت
نوع : pdf
بازدید : 98998
منتشرکننده : CarGeek
|
راهنمای برنامه ریزی ECU با TNM5000 ECU-KIT
5 سال پیش
6.73 مگابایت
نوع : pdf
بازدید : 14479
منتشرکننده : CarGeek
|
جزوه مکانیک استاتیک مرکز آموزش ایران خودرو
5 سال پیش
10.16 مگابایت
نوع : pdf
بازدید : 8391
منتشرکننده : CarGeek
|
دفترچه معرفی سیستم انژکتوری وانت زامیاد
5 سال پیش
5.24 مگابایت
نوع : pdf
بازدید : 7679
منتشرکننده : CarGeek
|
راهنمای سرویس و نگه داری موتور دیزل بنز سری OM 300
5 سال پیش
3.13 مگابایت
نوع : pdf
بازدید : 22592
منتشرکننده : CarGeek
|
راهنمای تعمیرات سوئیچ JAC S5
5 سال پیش
5.1 مگابایت
نوع : pdf
بازدید : 10928
منتشرکننده : CarGeek
|
راهنمای تعمیرات تعلیق جلو و عقب JAC S5- فایل 2
5 سال پیش
2.08 مگابایت
نوع : pdf
بازدید : 5843
منتشرکننده : CarGeek
|
راهنمای تعمیرات تعلیق جلو و عقب JAC S5
5 سال پیش
1.89 مگابایت
نوع : pdf
بازدید : 8382
منتشرکننده : CarGeek
|
راهنمای باز و بست داشبورد زانتیا
5 سال پیش
2.44 مگابایت
نوع : pdf
بازدید : 11990
منتشرکننده : CarGeek
|
فلوچارت عیب یابی لرزش دسته دنده
5 سال پیش
0.77 مگابایت
نوع : pdf
بازدید : 7554
منتشرکننده : CarGeek
|
فلوچارت عیب یابی روغن ریزی گیربکس
5 سال پیش
0.65 مگابایت
نوع : pdf
بازدید : 6041
منتشرکننده : CarGeek
|
فلوچارت عیب یابی بد جا رفتن دنده
5 سال پیش
1.08 مگابایت
نوع : pdf
بازدید : 7888
منتشرکننده : CarGeek
|
نقشه های الکتریکی رانا فاز صفر
5 سال پیش
3.41 مگابایت
نوع : pdf
بازدید : 9079
منتشرکننده : CarGeek
|
نقشه های الکتریکی خودرو رانا ECO MUX و LX
5 سال پیش
2.13 مگابایت
نوع : pdf
بازدید : 12390
منتشرکننده : CarGeek
|
کاتالوگ خودروهای سنگین هپکو
5 سال پیش
34.39 مگابایت
نوع : pdf
بازدید : 20624
منتشرکننده : CarGeek
|
راهنمای تعمیرات مجموعه صفحه نمایشگر JAC S5
5 سال پیش
2.34 مگابایت
نوع : pdf
بازدید : 16754
منتشرکننده : CarGeek
|
دفترچه راهنمای نیسان رونیز
5 سال پیش
12.99 مگابایت
نوع : pdf
بازدید : 32703
منتشرکننده : CarGeek
|
راهنمای تعمیرات و سرویس موتور پژو RD
5 سال پیش
9.65 مگابایت
نوع : pdf
بازدید : 16918
منتشرکننده : CarGeek
|
رویه نصب و تبدیل خودروی RD انژکتوری به سیستم دوگانه سوز
5 سال پیش
1.86 مگابایت
نوع : pdf
بازدید : 6927
منتشرکننده : CarGeek
|
دفترچه راهنمای عیب یابی پراید دوگانه سوز
5 سال پیش
3.82 مگابایت
نوع : pdf
بازدید : 9418
منتشرکننده : CarGeek
|
Komatsu Specification & Application Handbook
5 سال پیش
50.79 مگابایت
نوع : pdf
بازدید : 4810
منتشرکننده : CarGeek
|
راهنمای تغییر کیلومتر سمند مالتی پلکس از پشت آمپر ، ECU و نود FN
5 سال پیش
0.85 مگابایت
نوع : pdf
بازدید : 33442
منتشرکننده : CarGeek
|
راهنمای تعمیر موتورهای زانتیا
5 سال پیش
17.59 مگابایت
نوع : pdf
بازدید : 31649
منتشرکننده : CarGeek
|
راهنمای عیب یابی و ایرادات انژکتور
5 سال پیش
0.98 مگابایت
نوع : pdf
بازدید : 5066
منتشرکننده : CarGeek
|
پارامترهای استاندارد دیاگ انواع خودرو
5 سال پیش
0.87 مگابایت
نوع : pdf
بازدید : 79603
منتشرکننده : CarGeek
|
جزوه آموزشی درس موتورهای احتراق داخلی
5 سال پیش
9.25 مگابایت
نوع : pdf
بازدید : 4815
منتشرکننده : CarGeek
|
راهنمای تعمیرات گیربکس HAVECO لیفان 620 1.6
5 سال پیش
8.99 مگابایت
نوع : pdf
بازدید : 5478
منتشرکننده : CarGeek
|
نقشه جعبه فیوز سمند،سورن، پژو405 و پارس غیرماکس
5 سال پیش
1.69 مگابایت
نوع : pdf
بازدید : 22865
منتشرکننده : CarGeek
|
راهنمای تعمیرات گیربکس دستی جک توجوی
5 سال پیش
8.92 مگابایت
نوع : pdf
بازدید : 3704
منتشرکننده : CarGeek
|
راهنمای سیستم قفل مرکزی JAC S5
5 سال پیش
1 مگابایت
نوع : pdf
بازدید : 23100
منتشرکننده : CarGeek
|
توصیه های فنی رنو ساندرو
5 سال پیش
0.13 مگابایت
نوع : pdf
بازدید : 3975
منتشرکننده : CarGeek
|
راهنمای سیستم های ضدسرقت خودرو (ایموبیلایزر) سایپا یدک
5 سال پیش
5.97 مگابایت
نوع : pdf
بازدید : 11059
منتشرکننده : CarGeek
|
اصلاح کیلومتر پراید SPCO با TNM از پشت آمپر
5 سال پیش
0.45 مگابایت
نوع : pdf
بازدید : 8144
منتشرکننده : CarGeek
|
راهنمای برنامه ریزی یونیت ها و ECU با پروگرامر
5 سال پیش
4.01 مگابایت
نوع : pdf
بازدید : 11653
منتشرکننده : CarGeek
|
راهنمای دیاگرام های الکتریکی تویوتا هایلوکس سری KUN
5 سال پیش
4.7 مگابایت
نوع : pdf
بازدید : 20109
منتشرکننده : CarGeek
|
جزوه آموزشی گیربکس 6سرعته اتوماتیک هیوندای
5 سال پیش
8.35 مگابایت
نوع : pdf
بازدید : 23758
منتشرکننده : CarGeek
|
راهنمای تعمیرات سیستم خنک کاری موتور جک S5
5 سال پیش
2.08 مگابایت
نوع : pdf
بازدید : 28315
منتشرکننده : CarGeek
|
جزوه و راهنمای آموزشی برق خودرو تندر90- فایل 2
5 سال پیش
3.78 مگابایت
نوع : pdf
بازدید : 3395
منتشرکننده : CarGeek
|
جزوه و راهنمای آموزشی برق خودرو تندر90
5 سال پیش
4.8 مگابایت
نوع : pdf
بازدید : 8847
منتشرکننده : CarGeek
|
آموزش تغییر کیلومتر پارس داشبورد سوناتایی از روی صفحه کیلومتر
5 سال پیش
0.43 مگابایت
نوع : pdf
بازدید : 23858
منتشرکننده : CarGeek
|
کاتالوگ قطعات موتور وانت دیزل زامیاد
5 سال پیش
12.12 مگابایت
نوع : pdf
بازدید : 20323
منتشرکننده : CarGeek
|
دستورالعمل تعویض رولبرینگ داخلی و خارجی چرخ عقب تیبا
5 سال پیش
1.08 مگابایت
نوع : pdf
بازدید : 16747
منتشرکننده : CarGeek
|
دستورالعمل تعویض پلوس چپ و راست تیبا
5 سال پیش
0.93 مگابایت
نوع : pdf
بازدید : 21555
منتشرکننده : CarGeek
|
جزوه آموزشی موتور و گیربکس رنو کپچر
5 سال پیش
6.48 مگابایت
نوع : pdf
بازدید : 9100
منتشرکننده : CarGeek
|
جزوه آموزشی سیستم های ایمنی/آسایشی هایما S7
5 سال پیش
0.74 مگابایت
نوع : pdf
بازدید : 5184
منتشرکننده : CarGeek
|
نقشه های کامل سیم کشی و دسته سیم های لیفان X50
5 سال پیش
12.12 مگابایت
نوع : pdf
بازدید : 18328
منتشرکننده : CarGeek
|
راهنمای کامل تعمیرات لیفان X50
5 سال پیش
109.97 مگابایت
نوع : pdf
بازدید : 37231
منتشرکننده : CarGeek
|
راهنمای تعمیرات سیستم سوخت رسانی CNG تیبا
5 سال پیش
5.57 مگابایت
نوع : pdf
بازدید : 10147
منتشرکننده : CarGeek
|
راهنمای تعمیرات و سرویس سیستم کنترل الکترونیکی موتور برلیانس سری H200و H300
5 سال پیش
3.92 مگابایت
نوع : pdf
بازدید : 4413
منتشرکننده : CarGeek
|
معرفی خودروی پژو پارس با سیستم هوشمند CEC
5 سال پیش
0.88 مگابایت
نوع : pdf
بازدید : 7034
منتشرکننده : CarGeek
|
راهنمای باز و بست توربوشارژر سورن توربو
5 سال پیش
1 مگابایت
نوع : pdf
بازدید : 14171
منتشرکننده : CarGeek
|
Pin Layout و نقشه ECU موتور و ECU گیربکس اتوماتیک پژو پارس اتوماتیک
5 سال پیش
0.73 مگابایت
نوع : pdf
بازدید : 26873
منتشرکننده : CarGeek
|
دستورالعمل حذف مخزن کوچک خودروهای دوگانه سوز زامیاد
5 سال پیش
1.22 مگابایت
نوع : pdf
بازدید : 4938
منتشرکننده : CarGeek
|
راهنمای جعبه فیوز داخل اتاق (SJB) جک S5
5 سال پیش
1.33 مگابایت
نوع : pdf
بازدید : 62284
منتشرکننده : CarGeek
|
راهنمای تعمیرات و عیب یابی ماژول کنترل بدنه (BCM) جک S5
5 سال پیش
5.06 مگابایت
نوع : pdf
بازدید : 8339
منتشرکننده : CarGeek
|
مرجع سریع سامانه مدیریت هوشمند موتور EF7
5 سال پیش
5.67 مگابایت
نوع : pdf
بازدید : 4281
منتشرکننده : CarGeek
|
راهنمای تعمیرات موتور 1.6 لیفان 620
5 سال پیش
13.01 مگابایت
نوع : pdf
بازدید : 10958
منتشرکننده : CarGeek
|
راهنمای نصب موتور لودر ولوو (L60F-L70F-L90F)
5 سال پیش
3.09 مگابایت
نوع : pdf
بازدید : 8779
منتشرکننده : CarGeek
|
راهنمای تعمیرات تعلیق ،ترمز و فرمان رنو کلئوس
5 سال پیش
2.31 مگابایت
نوع : pdf
بازدید : 4912
منتشرکننده : CarGeek
|
راهنمای تعمیرات اکسل عقب و پلوس های رنو کلئوس
5 سال پیش
0.97 مگابایت
نوع : pdf
بازدید : 3519
منتشرکننده : CarGeek
|
راهنمای تعمیرات تهویه مطبوع و بخاری رنو کلئوس
5 سال پیش
1.63 مگابایت
نوع : pdf
بازدید : 5367
منتشرکننده : CarGeek
|
دفترچه راهنمای کلیه مدل های زانتیا
5 سال پیش
21.94 مگابایت
نوع : pdf
بازدید : 44646
منتشرکننده : CarGeek
|
آموزش نصب صندوق پران تندر 90
5 سال پیش
0.75 مگابایت
نوع : pdf
بازدید : 6640
منتشرکننده : CarGeek
|
دستورالعمل عیب یابی اختلاط آب و روغن موتور
5 سال پیش
0.99 مگابایت
نوع : pdf
بازدید : 7131
منتشرکننده : CarGeek
|
دستورالعمل عیب یابی جوش آوردن موتور
5 سال پیش
2.38 مگابایت
نوع : pdf
بازدید : 8270
منتشرکننده : CarGeek
|
راهنمای تعمیرات و تفاوت های موتور EF7 TC (توربوشارژ)
5 سال پیش
9.17 مگابایت
نوع : pdf
بازدید : 23185
منتشرکننده : CarGeek
|
جزوه دوره آموزش CNG رنو
5 سال پیش
1.83 مگابایت
نوع : pdf
بازدید : 4021
منتشرکننده : CarGeek
|
راهنمای تعمیرات تعلیق ،فرمان و ترمز ABS لیفان 620
5 سال پیش
8.13 مگابایت
نوع : pdf
بازدید : 8565
منتشرکننده : CarGeek
|
جزوه آموزشی برق خانواده خودروهای 206 ، سمند مالتی پلکس ، رانا ، دنا و پارس مالتی پلکس + نقشه ها
5 سال پیش
32.48 مگابایت
نوع : pdf
بازدید : 20959
منتشرکننده : CarGeek
|
معرفی خودرو P7L (پژو 207 داخلی)
5 سال پیش
0.73 مگابایت
نوع : pdf
بازدید : 5169
منتشرکننده : CarGeek
|
راهنمای تعمیرات و سرویس کیسه هوا(ایربگ) پراید
5 سال پیش
5.05 مگابایت
نوع : pdf
بازدید : 18418
منتشرکننده : CarGeek
|
راهنمای تعمیرات سیستم سوخت رسانی خودرو چری دوگانه سوز (سیستم OMEGAS)
5 سال پیش
3.29 مگابایت
نوع : pdf
بازدید : 4675
منتشرکننده : CarGeek
|
لیست و پارت نامبر قطعات اختصاصی پژو 206 SD
5 سال پیش
1.33 مگابایت
نوع : pdf
بازدید : 7425
منتشرکننده : CarGeek
|
جزوه آموزش مبانی فنی خودرو برای پرسنل فروش
5 سال پیش
0.71 مگابایت
نوع : pdf
بازدید : 3711
منتشرکننده : CarGeek
|
آلبوم نقشه های سوخت رسانی انواع پژو 405 و پارس
5 سال پیش
2.9 مگابایت
نوع : pdf
بازدید : 55694
منتشرکننده : CarGeek
|
راهنمای ابزارمخصوص زانتیا
5 سال پیش
1.9 مگابایت
نوع : pdf
بازدید : 7192
منتشرکننده : CarGeek
|
تاثیر برخی پارامترها بر مصرف سوخت موتور بنزینی خودرو
5 سال پیش
1.54 مگابایت
نوع : pdf
بازدید : 3699
منتشرکننده : CarGeek
|
راهنمای تعمیرات گیربکس دستی BE خانواده پژو 206
5 سال پیش
7.01 مگابایت
نوع : pdf
بازدید : 8028
منتشرکننده : CarGeek
|
کتاب سیستم انژکتوری و مبانی الکترونیک خودرو
5 سال پیش
13.95 مگابایت
نوع : pdf
بازدید : 21345
منتشرکننده : CarGeek
|
نحوه عیب یابی کنترل یونیت سیستم خنک کننده موتور
5 سال پیش
1.64 مگابایت
نوع : pdf
بازدید : 25435
منتشرکننده : CarGeek
|
راهنمای تعمیرات گیربکس اتوماتیک AL4 پژو 206
5 سال پیش
18.93 مگابایت
نوع : pdf
بازدید : 12515
منتشرکننده : CarGeek
|
کتاب Automotive Embedded Systems Handbook
5 سال پیش
8.66 مگابایت
نوع : pdf
بازدید : 3704
منتشرکننده : CarGeek
|
کتاب Hybrid Vehicles: and the Future of Personal Transportation
5 سال پیش
11.99 مگابایت
نوع : pdf
بازدید : 4018
منتشرکننده : CarGeek
|
بررسی عملکرد و روش انتقال اطلاعات در سیستم مالتی پلکس پژو 206 فرانسوی
5 سال پیش
3.54 مگابایت
نوع : pdf
بازدید : 4984
منتشرکننده : CarGeek
|
عیب یابی روشن نشدن زانتیا
5 سال پیش
0.63 مگابایت
نوع : pdf
بازدید : 22634
منتشرکننده : CarGeek
|
جزوه آموزشی تعمیرات ECU
5 سال پیش
4.75 مگابایت
نوع : pdf
بازدید : 5681
منتشرکننده : CarGeek
|
کتاب Clutches and Brakes: Design and Selection
5 سال پیش
7.32 مگابایت
نوع : pdf
بازدید : 3519
منتشرکننده : CarGeek
|
مقاله پایش وضعیت سنسور پدال گاز خودروهای با دریچه گازبرقی
5 سال پیش
0.57 مگابایت
نوع : pdf
بازدید : 6781
منتشرکننده : CarGeek
|
راهنمای تعمیرات سری موتور 6G7 تا مدل 2011
5 سال پیش
6.31 مگابایت
نوع : pdf
بازدید : 5391
منتشرکننده : CarGeek
|
راهنمای تعمیرات موتور سیتروئن C5
5 سال پیش
4.93 مگابایت
نوع : pdf
بازدید : 9162
منتشرکننده : CarGeek
|
اصول عملکرد و راهنمای عیب یابی سنسور اکسیژن
5 سال پیش
6.73 مگابایت
نوع : pdf
بازدید : 18064
منتشرکننده : CarGeek
|
راهنمای مدارها و سیم کشی های لیفان X60 اتوماتیک و دستی
5 سال پیش
8.29 مگابایت
نوع : pdf
بازدید : 9670
منتشرکننده : CarGeek
|
کتاب ابزارمخصوص ایران خودرو
5 سال پیش
1.5 مگابایت
نوع : pdf
بازدید : 9742
منتشرکننده : CarGeek
|
راهنمای تعمیرات موتور TU5-JP4 رانا
5 سال پیش
10.87 مگابایت
نوع : pdf
بازدید : 7973
منتشرکننده : CarGeek
|
کتاب Automotive Engines: Diagnosis, Repair, Rebuilding
5 سال پیش
103.76 مگابایت
نوع : pdf
بازدید : 3947
منتشرکننده : CarGeek
|
معرفی فنی هیوندای سوناتا YF
5 سال پیش
2.42 مگابایت
نوع : pdf
بازدید : 7721
منتشرکننده : CarGeek
|
تغییرات الکتریکی خودرو سمند با موتور EF7
5 سال پیش
0.93 مگابایت
نوع : pdf
بازدید : 5383
منتشرکننده : CarGeek
|
راهنمای سیستم ایموبیلایزر زیمنس پراید
5 سال پیش
5.21 مگابایت
نوع : pdf
بازدید : 13144
منتشرکننده : CarGeek
|
چگونگی عملکرد سیستم ایمنی غیرفعال و حسگرهای سنجش شتاب در کیسه های هوای هوشمند
5 سال پیش
7.83 مگابایت
نوع : pdf
بازدید : 3204
منتشرکننده : CarGeek
|
معرفی سیستم های ایمنی غیرفعال در خودروهای گروه X100 سایپا
5 سال پیش
1.1 مگابایت
نوع : pdf
بازدید : 3395
منتشرکننده : CarGeek
|
مروری بر گیربکس و انواع آن در خودرو
5 سال پیش
3.37 مگابایت
نوع : pdf
بازدید : 3592
منتشرکننده : CarGeek
|
جزوه آموزشی تعمیرات موتور زامیاد وانت دیزل Z28ND
5 سال پیش
6.99 مگابایت
نوع : pdf
بازدید : 17357
منتشرکننده : CarGeek
|
آشنایی با سیستم های ایمنی فعال و سیستم های کمکی ترمز
5 سال پیش
1.71 مگابایت
نوع : pdf
بازدید : 3307
منتشرکننده : CarGeek
|
سیستم دفیا (Dephia) در سیستم جرقه پژو 206
5 سال پیش
0.33 مگابایت
نوع : pdf
بازدید : 5500
منتشرکننده : CarGeek
|
شناخت سیستم ترمز ABS
5 سال پیش
5.63 مگابایت
نوع : pdf
بازدید : 101138
منتشرکننده : CarGeek
|
جزوه دوره آموزشی ترمز ABS ماندو
5 سال پیش
2.12 مگابایت
نوع : pdf
بازدید : 19604
منتشرکننده : CarGeek
|
جزوه خودآموز گیربکس اتوماتیک AL4 پژو 206
5 سال پیش
1.3 مگابایت
نوع : pdf
بازدید : 18169
منتشرکننده : CarGeek
|
الزامات ارائه خدمت در مراکز تماس با مشتری براساس استاندارد BS EN 15838:2009 + معرفی مرکز تماس امدادخودرو ایران
5 سال پیش
6.52 مگابایت
نوع : pdf
بازدید : 4008
منتشرکننده : CarGeek
|
مروری بر خدمات امدادخودرویی انگلستان
5 سال پیش
2.54 مگابایت
نوع : pdf
بازدید : 3367
منتشرکننده : CarGeek
|
عملکرد گرمکن شیشه، شیشه شور و برف پاک کن در شبکه مالتی پلکس پژو 206
5 سال پیش
1.01 مگابایت
نوع : pdf
بازدید : 7528
منتشرکننده : CarGeek
|
عملکرد سیستم های ایمنی و حفاظت و ضدسرقت در شبکه مالتی پلکس پژو 206
5 سال پیش
1.59 مگابایت
نوع : pdf
بازدید : 3975
منتشرکننده : CarGeek
|
نحوه عملکرد ABS در شبکه مالتی پلکس پژو 206
5 سال پیش
2.16 مگابایت
نوع : pdf
بازدید : 6034
منتشرکننده : CarGeek
|
قطعات اصلی در شبکه مالتی پلکس پژو 206
5 سال پیش
3.38 مگابایت
نوع : pdf
بازدید : 5677
منتشرکننده : CarGeek
|
ساختار الکتریکی پژو 206 مالتی پلکس
5 سال پیش
1.28 مگابایت
نوع : pdf
بازدید : 5559
منتشرکننده : CarGeek
|
جزوه دوره آموزشی موتور سایپا شامل موتورهای پراید،ریو،زانتیا
5 سال پیش
9.34 مگابایت
نوع : pdf
بازدید : 10620
منتشرکننده : CarGeek
|
آشنایی با اصول و مفاهیم سیستم مولتی پلکس پژو 206
5 سال پیش
14.38 مگابایت
نوع : pdf
بازدید : 5424
منتشرکننده : CarGeek
|
خودروهای انژکتوری - روش های پیشرفته عیب یابی با دستگاه دیاگ-اسکنر
5 سال پیش
30.52 مگابایت
نوع : pdf
بازدید : 20994
منتشرکننده : CarGeek
|
راهنمای ساختار بدنه سوزوکی کیزاشی
5 سال پیش
40.47 مگابایت
نوع : pdf
بازدید : 3528
منتشرکننده : CarGeek
|
راهنمای سیستم جرقه زنی موتور سوزوکی کیزاشی
5 سال پیش
0.59 مگابایت
نوع : pdf
بازدید : 3531
منتشرکننده : CarGeek
|
راهنمای تعمیرات سیستم های کنترل الکترونیکی سوزوکی کیزاشی
5 سال پیش
8.45 مگابایت
نوع : pdf
بازدید : 5182
منتشرکننده : CarGeek
|
راهنمای مدارات الکتریکی وانت پادرا
5 سال پیش
6.66 مگابایت
نوع : pdf
بازدید : 11971
منتشرکننده : CarGeek
|
راهنمای تعمیرات سیستم ترمز دنا
5 سال پیش
2.77 مگابایت
نوع : pdf
بازدید : 14155
منتشرکننده : CarGeek
|
راهنمای تعمیرات و سرویس موتور چانگان CS35
5 سال پیش
4.8 مگابایت
نوع : pdf
بازدید : 10461
منتشرکننده : CarGeek
|
راهنمای تعمیرات انتقال قدرت آریسان (گیربکس/کلاچ/گاردان/دیفرانسیل)
5 سال پیش
10.17 مگابایت
نوع : pdf
بازدید : 12691
منتشرکننده : CarGeek
|
راهنمای تعمیرات میل پلوس/اکسل سوزوکی کیزاشی
5 سال پیش
2.07 مگابایت
نوع : pdf
بازدید : 3865
منتشرکننده : CarGeek
|
دستورالعمل عیب یابی روشن شدن چراغ چک
5 سال پیش
5.32 مگابایت
نوع : pdf
بازدید : 14349
منتشرکننده : CarGeek
|
راهنمای تعمیرات قطعات الکتریکی دنا
5 سال پیش
4.43 مگابایت
نوع : pdf
بازدید : 5378
منتشرکننده : CarGeek
|
راهنمای تعمیرات تزئینات داخلی و خارجی سوزوکی کیزاشی
5 سال پیش
3.31 مگابایت
نوع : pdf
بازدید : 2953
منتشرکننده : CarGeek
|
معرفی و جانمایی دسته سیم های خودرو آریسان
5 سال پیش
1.1 مگابایت
نوع : pdf
بازدید : 12310
منتشرکننده : CarGeek
|
معرفی خودروهای B90 و B90 Cross (رنو ساندرو و ساندرو استپ وی)
5 سال پیش
3.35 مگابایت
نوع : pdf
بازدید : 3943
منتشرکننده : CarGeek
|
دستورالعمل عیب یابی لرزش موتور
5 سال پیش
2.48 مگابایت
نوع : pdf
بازدید : 10173
منتشرکننده : CarGeek
|
راهنمای تعمیرات قطعات الکتریکی آریسان
5 سال پیش
1.85 مگابایت
نوع : pdf
بازدید : 5492
منتشرکننده : CarGeek
|
راهنمای تعمیرات سیستم سوخت رسانی آریسان
5 سال پیش
2.63 مگابایت
نوع : pdf
بازدید : 20830
منتشرکننده : CarGeek
|
راهنمای تعمیرات سیستم تعلیق خودرو دنا
5 سال پیش
4.27 مگابایت
نوع : pdf
بازدید : 8652
منتشرکننده : CarGeek
|
راهنمای تعمیرات و عیب یابی ایربگ راننده و سرنشین خودرو دنا
5 سال پیش
4.38 مگابایت
نوع : pdf
بازدید : 12297
منتشرکننده : CarGeek
|
راهنمای تعمیرات سیستم گازسوز خودرو آریسان
5 سال پیش
1.74 مگابایت
نوع : pdf
بازدید : 10989
منتشرکننده : CarGeek
|
راهنمای تعمیرات گیربکس اتوماتیک مزدا 323
5 سال پیش
6.91 مگابایت
نوع : pdf
بازدید : 7777
منتشرکننده : CarGeek
|
راهنمای تعمیرات موتور خودرو دنا (موتور EF7)
5 سال پیش
9.93 مگابایت
نوع : pdf
بازدید : 13196
منتشرکننده : CarGeek
|
راهنمای تعمیرات بدنه وانت آریسان
5 سال پیش
6.38 مگابایت
نوع : pdf
بازدید : 15245
منتشرکننده : CarGeek
|
راهنمای نقشه های الکتریکی سوزوکی کیزاشی
5 سال پیش
32.02 مگابایت
نوع : pdf
بازدید : 10536
منتشرکننده : CarGeek
|
راهنمای اطلاعات عمومی تعمیرات سوزوکی کیزاشی
5 سال پیش
4.21 مگابایت
نوع : pdf
بازدید : 3749
منتشرکننده : CarGeek
|
راهنمای تعمیرات سانروف سوزوکی کیزاشی
5 سال پیش
1.26 مگابایت
نوع : pdf
بازدید : 4645
منتشرکننده : CarGeek
|
آشنایی با ترمزهای هوشمند ESP و EBD- فایل 3
5 سال پیش
0.25 مگابایت
نوع : pdf
بازدید : 3404
منتشرکننده : CarGeek
|
آشنایی با ترمزهای هوشمند ESP و EBD- فایل 2
5 سال پیش
0.26 مگابایت
نوع : pdf
بازدید : 3346
منتشرکننده : CarGeek
|
آشنایی با ترمزهای هوشمند ESP و EBD
5 سال پیش
1.69 مگابایت
نوع : pdf
بازدید : 3198
منتشرکننده : CarGeek
|
راهنمای نحوه کار با مولتی متر
5 سال پیش
4.87 مگابایت
نوع : pdf
بازدید : 4047
منتشرکننده : CarGeek
|
کاتالوگ قطعات و پارت نامبر جیلی EC7
5 سال پیش
10.38 مگابایت
نوع : pdf
بازدید : 7368
منتشرکننده : CarGeek
|
نحوه تغییر کیلومتر خودرو دنا
5 سال پیش
2.9 مگابایت
نوع : pdf
بازدید : 23009
منتشرکننده : CarGeek
|
دیاگرام سیستم های برق خودروهای سمند
5 سال پیش
17.45 مگابایت
نوع : pdf
بازدید : 6727
منتشرکننده : CarGeek
|
راهنمای تعمیرات سیستم های الکتریکی بدنه چری A15
5 سال پیش
2.25 مگابایت
نوع : pdf
بازدید : 15563
منتشرکننده : CarGeek
|
رویه نصب و تبدیل خودرو نیسان انژکتور به سیستم دوگانه سوز CNG
5 سال پیش
7.42 مگابایت
نوع : pdf
بازدید : 7921
منتشرکننده : CarGeek
|
دستورالعمل تکمیل رویه نصب سیستم دوگانه سوز (بنزین-CNG) پیکان وانت
5 سال پیش
2.9 مگابایت
نوع : pdf
بازدید : 17531
منتشرکننده : CarGeek
|
راهنمای سیستم الکتریکی کامیون های C&C
5 سال پیش
2.58 مگابایت
نوع : pdf
بازدید : 18150
منتشرکننده : CarGeek
|
راهنمای سیستم کنترل موتور JAC S5 و شرح خطاها و عیب یابی
5 سال پیش
6.56 مگابایت
نوع : pdf
بازدید : 68597
منتشرکننده : CarGeek
|
راهنمای تعمیرات گیربکس معمولی JAC S5
5 سال پیش
4.86 مگابایت
نوع : pdf
بازدید : 7464
منتشرکننده : CarGeek
|
راهنمای ایموبیلایزر، تعریف کلید و ریموت انواع خودرو
5 سال پیش
5.17 مگابایت
نوع : pdf
بازدید : 30451
منتشرکننده : CarGeek
|
جزوه آموزشی سیستم های تعلیق هیوندای
5 سال پیش
5.77 مگابایت
نوع : pdf
بازدید : 8173
منتشرکننده : CarGeek
|
راهنمای آموزشی امدادخودرو در مورد مکانیک هایما S7
5 سال پیش
13.54 مگابایت
نوع : pdf
بازدید : 7529
منتشرکننده : CarGeek
|
راهنمای آموزشی امدادخودرو در مورد الکتریکال هایما S7
5 سال پیش
6.22 مگابایت
نوع : pdf
بازدید : 5127
منتشرکننده : CarGeek
|
راهنمای کاربردی طراحی و ساخت سیستم های هیدرولیک
5 سال پیش
2.8 مگابایت
نوع : pdf
بازدید : 3533
منتشرکننده : CarGeek
|
راهنمای آموزشی CVVT Systems کیاموتورز
5 سال پیش
1.96 مگابایت
نوع : pdf
بازدید : 9453
منتشرکننده : CarGeek
|
راهنمای تعمیرات و عیب یابی سیستم گازسوز پژو 405
5 سال پیش
7.52 مگابایت
نوع : pdf
بازدید : 36759
منتشرکننده : CarGeek
|
دستورالعمل ایمنی ابزار
5 سال پیش
0.25 مگابایت
نوع : pdf
بازدید : 3328
منتشرکننده : CarGeek
|
معرفی و راهنمای عیب یابی سیستم های ترمز امدادخودرو
5 سال پیش
1.61 مگابایت
نوع : pdf
بازدید : 5274
منتشرکننده : CarGeek
|
راهنمای تعمیرات سیستم های الکتریکی و تزئینات لیفان 620
5 سال پیش
23.28 مگابایت
نوع : pdf
بازدید : 13329
منتشرکننده : CarGeek
|
نقشه های الکتریکی سمند ماکس و دنا
5 سال پیش
2.77 مگابایت
نوع : pdf
بازدید : 15549
منتشرکننده : CarGeek
|
راهنمای امدادخودرو درخصوص مکانیک رنو کپچر
5 سال پیش
7.9 مگابایت
نوع : pdf
بازدید : 9163
منتشرکننده : CarGeek
|
راهنمای تعمیرات گیربکس دستی و CVT سوزوکی کیزاشی
5 سال پیش
17.72 مگابایت
نوع : pdf
بازدید : 4725
منتشرکننده : CarGeek
|
کتاب مبانی دینامیک خودرو
5 سال پیش
17.09 مگابایت
نوع : pdf
بازدید : 8137
منتشرکننده : CarGeek
|
جزوه آموزش فنی معرفی رانا
5 سال پیش
12.16 مگابایت
نوع : pdf
بازدید : 8294
منتشرکننده : CarGeek
|
جزوه آموزشی سیستم فرمان و جلوبندی کیا اپتیما
5 سال پیش
1.28 مگابایت
نوع : pdf
بازدید : 7958
منتشرکننده : CarGeek
|
جزوه راهنمای عیب یابی خودرو امدادخودرو- فایل 2
5 سال پیش
3.58 مگابایت
نوع : pdf
بازدید : 8753
منتشرکننده : CarGeek
|
جزوه راهنمای عیب یابی خودرو امدادخودرو
5 سال پیش
2.44 مگابایت
نوع : pdf
بازدید : 19470
منتشرکننده : CarGeek
|
جزوه آموزشی باطری/استارتر/آلترناتور کیا اسپورتیج SL
5 سال پیش
2.72 مگابایت
نوع : pdf
بازدید : 10450
منتشرکننده : CarGeek
|
جزوه آموزشی سیستم ضدسرقت PIC
5 سال پیش
2.66 مگابایت
نوع : pdf
بازدید : 6028
منتشرکننده : CarGeek
|
جزوه دوره آموزشی کارشناس فنی خودرو مدیران خودرو (انواع MVM)
5 سال پیش
3.75 مگابایت
نوع : pdf
بازدید : 15151
منتشرکننده : CarGeek
|
جزوه آموزشی مدیریت موتور خودروهای هیوندای
5 سال پیش
3.29 مگابایت
نوع : pdf
بازدید : 9096
منتشرکننده : CarGeek
|
راهنمای تعمیرات گیربکس BE3 دنا
5 سال پیش
18.13 مگابایت
نوع : pdf
بازدید : 7557
منتشرکننده : CarGeek
|
راهنمای تعمیرات و سرویس سیستم سوخت رسانی دنا
5 سال پیش
3.17 مگابایت
نوع : pdf
بازدید : 10128
منتشرکننده : CarGeek
|
کاتالوگ قطعات و پارت نامبر نیسان ماکسیما
5 سال پیش
25.36 مگابایت
نوع : pdf
بازدید : 9400
منتشرکننده : CarGeek
|
راهنمای تعمیرات و عیب یابی و پیکربندی سیستم مالتی پلکس SMS دنا و سمند با ایکو دیاگ
5 سال پیش
3.55 مگابایت
نوع : pdf
بازدید : 11800
منتشرکننده : CarGeek
|
راهنمای تعمیرات و معرفی الکتریکال سیستم مالتی پلکس SMS دنا
5 سال پیش
2.92 مگابایت
نوع : pdf
بازدید : 11583
منتشرکننده : CarGeek
|
راهنمای واحد کنترل الکتریکی (ECU) زامیاد دیزل
5 سال پیش
0.39 مگابایت
نوع : pdf
بازدید : 10302
منتشرکننده : CarGeek
|
راهنمای سیستم برق کامیون کاوه (دانگ فنگ)
5 سال پیش
1.7 مگابایت
نوع : pdf
بازدید : 37349
منتشرکننده : CarGeek
|
راهنمای عمومی برق اتوبوس یوتانگ
5 سال پیش
1.23 مگابایت
نوع : pdf
بازدید : 12654
منتشرکننده : CarGeek
|
رویه نصب و تبدیل خودرو پراید انژکتوری به سیستم دوگانه سوز
5 سال پیش
3.44 مگابایت
نوع : pdf
بازدید : 8587
منتشرکننده : CarGeek
|
معرفی سیستم VVT
5 سال پیش
0.44 مگابایت
نوع : pdf
بازدید : 6323
منتشرکننده : CarGeek
|
راهنمای تعمیرات و سرویس میتسوبیشی لنسر
5 سال پیش
51.39 مگابایت
نوع : pdf
بازدید : 11283
منتشرکننده : CarGeek
|
معرفی کوتاه انواع مبردها و معرفی مبرد R134a
5 سال پیش
1.75 مگابایت
نوع : pdf
بازدید : 2885
منتشرکننده : CarGeek
|
نودها و فیوزها در خودروهای مالتی پلکس سمند،سورن،دنا،رانا و 206
5 سال پیش
5.21 مگابایت
نوع : pdf
بازدید : 25545
منتشرکننده : CarGeek
|
معرفی قطعات الکترونیک
5 سال پیش
2.26 مگابایت
نوع : pdf
بازدید : 5771
منتشرکننده : CarGeek
|
دفترچه راهنمای هایما S7
5 سال پیش
3.18 مگابایت
نوع : pdf
بازدید : 85340
منتشرکننده : CarGeek
|
راهنمای تعمیرات موتور OM457LA اتوبوس o457
5 سال پیش
4.69 مگابایت
نوع : pdf
بازدید : 20080
منتشرکننده : CarGeek
|
راهنمای تعمیرات موتور OHVG2 وانت آریسان
5 سال پیش
5.06 مگابایت
نوع : pdf
بازدید : 12354
منتشرکننده : CarGeek
|
راهنمای کاربری و سرویس های ادواری سیستم برق وانت زامیاد دیزل
5 سال پیش
4.96 مگابایت
نوع : pdf
بازدید : 9025
منتشرکننده : CarGeek
|
جزوه آموزشی سیستم گیربکس اتوماتیک سوزوکی گرندویتارا
5 سال پیش
1.78 مگابایت
نوع : pdf
بازدید : 9576
منتشرکننده : CarGeek
|
کتاب تکنولوژی سوخت رسانی دانشگاه سایپا
5 سال پیش
12.4 مگابایت
نوع : pdf
بازدید : 8022
منتشرکننده : CarGeek
|
جزوه دوره پراید CNG انژکتوری
5 سال پیش
1.21 مگابایت
نوع : pdf
بازدید : 4683
منتشرکننده : CarGeek
|
راهنمای امدادخودرو سیستم مالتی پلکس رانا و 206 جدید
5 سال پیش
1.12 مگابایت
نوع : pdf
بازدید : 14188
منتشرکننده : CarGeek
|
Vehicle Diagnostics with Oscilloscope FAQ
5 سال پیش
1.89 مگابایت
نوع : pdf
بازدید : 4459
منتشرکننده : CarGeek
|
راهنمای تعمیرات گیربکس 5YM ون دلیکا
5 سال پیش
0.84 مگابایت
نوع : pdf
بازدید : 7849
منتشرکننده : CarGeek
|
راهنمای سیم کشی و الکتریکی دوو سیلو و ریسر
5 سال پیش
1.26 مگابایت
نوع : pdf
بازدید : 67876
منتشرکننده : CarGeek
|
جزوه آموزشی و نقشه های برق خودرو دانگ فنگ H30 و S30
5 سال پیش
17.79 مگابایت
نوع : pdf
بازدید : 9290
منتشرکننده : CarGeek
|
راهنمای کامل تعمیرات لیفان 820
5 سال پیش
111.25 مگابایت
نوع : pdf
بازدید : 23761
منتشرکننده : CarGeek
|
لیست قطعات یدکی و Part Number مزدا 3
5 سال پیش
0.51 مگابایت
نوع : pdf
بازدید : 7342
منتشرکننده : CarGeek
|
ابزارشناسی و عملیات کارگاهی
5 سال پیش
3.72 مگابایت
نوع : pdf
بازدید : 11544
منتشرکننده : CarGeek
|
پیاده و سوارکردن و عیب یابی انواع دلکو خودرو
5 سال پیش
0.95 مگابایت
نوع : pdf
بازدید : 17886
منتشرکننده : CarGeek
|
آموزش تعویض ترموستات و هواگیری مدار گردش آب پژو 206
5 سال پیش
1.61 مگابایت
نوع : pdf
بازدید : 30530
منتشرکننده : CarGeek
|
کتاب Advanced Automotive Fault Diagnosis
5 سال پیش
8.17 مگابایت
نوع : pdf
بازدید : 5552
منتشرکننده : CarGeek
|
کتاب Handbook of Automobiles 1919
5 سال پیش
16.26 مگابایت
نوع : pdf
بازدید : 3737
منتشرکننده : CarGeek
|
کتاب Automotive Development Processes
5 سال پیش
10.45 مگابایت
نوع : pdf
بازدید : 3471
منتشرکننده : CarGeek
|
جزوه آموزشی Basic Machines نیروی دریایی آمریکا
5 سال پیش
8.59 مگابایت
نوع : pdf
بازدید : 4256
منتشرکننده : CarGeek
|
کتاب Automotive Lubricant Testing and Advanced Additive Development
5 سال پیش
6.99 مگابایت
نوع : pdf
بازدید : 3613
منتشرکننده : CarGeek
|
کتاب تکنولوژی دستگاه های الکتریکی خودرو
5 سال پیش
20.77 مگابایت
نوع : pdf
بازدید : 8421
منتشرکننده : CarGeek
|
جزوه آموزشی امداد خودرو چری A15
5 سال پیش
1.48 مگابایت
نوع : pdf
بازدید : 16986
منتشرکننده : CarGeek
|
جزوه آموزشی تعمیرات و سرویس خودرو دانگ فنگ H30 و S30
5 سال پیش
10.92 مگابایت
نوع : pdf
بازدید : 5890
منتشرکننده : CarGeek
|
معرفی فنی سیستم شاسی ، تعلیق ، فرمان و ترمز پراید
5 سال پیش
0.8 مگابایت
نوع : pdf
بازدید : 6466
منتشرکننده : CarGeek
|
راهنمای سرویس و عیب یابی مجموعه گیربکس اتوماتیک رنو ساندرو
5 سال پیش
5.28 مگابایت
نوع : pdf
بازدید : 8430
منتشرکننده : CarGeek
|
آشنایی با بیماری های شغلی
5 سال پیش
0.76 مگابایت
نوع : pdf
بازدید : 3175
منتشرکننده : CarGeek
|
راهنمای تعمیرات و سرویس بسترن B50
5 سال پیش
18.73 مگابایت
نوع : pdf
بازدید : 19299
منتشرکننده : CarGeek
|
راهنمای کامل تعمیرات هوندا آکورد نسل چهارم (1989–1993)
5 سال پیش
69.68 مگابایت
نوع : pdf
بازدید : 21692
منتشرکننده : CarGeek
|
راهنمای کامل تعمیرات هوندا سیویک نسل پنجم (1991–1995)
5 سال پیش
106.62 مگابایت
نوع : pdf
بازدید : 12960
منتشرکننده : CarGeek
|
راهنمای تعمیرات موتور JAC S5- فایل 2
5 سال پیش
3.41 مگابایت
نوع : pdf
بازدید : 5812
منتشرکننده : CarGeek
|
راهنمای تعمیرات موتور JAC S5
5 سال پیش
13.1 مگابایت
نوع : pdf
بازدید : 24354
منتشرکننده : CarGeek
|
راهنمای مدارات الکتریکی سیستم دوگانه سوز پراید
5 سال پیش
10.54 مگابایت
نوع : pdf
بازدید : 22115
منتشرکننده : CarGeek
|
راهنمای استاندارد عاملیت مجاز تعمیراتی سایپا
5 سال پیش
11.46 مگابایت
نوع : pdf
بازدید : 5505
منتشرکننده : CarGeek
|
راهنمای مشخصات و عیب یابی موتور سوزوکی کیزاشی
5 سال پیش
3.29 مگابایت
نوع : pdf
بازدید : 3072
منتشرکننده : CarGeek
|
راهنمای تعمیرات سیستم تعلیق سوزوکی کیزاشی
5 سال پیش
6.45 مگابایت
نوع : pdf
بازدید : 3299
منتشرکننده : CarGeek
|
راهنمای تعمیرات ترمز سوزوکی کیزاشی
5 سال پیش
12.47 مگابایت
نوع : pdf
بازدید : 3328
منتشرکننده : CarGeek
|
دستورالعمل تعمیرات بنزهای C240 پلیس
5 سال پیش
122.47 مگابایت
نوع : pdf
بازدید : 24009
منتشرکننده : CarGeek
|
راهنمای تعمیرات پلوس (ساندرو - تندر90)
5 سال پیش
3.77 مگابایت
نوع : pdf
بازدید : 7554
منتشرکننده : CarGeek
|
کاربرد فناوری نانو و نانومواد در صنعت خودرو
5 سال پیش
4.1 مگابایت
نوع : pdf
بازدید : 3060
منتشرکننده : CarGeek
|
خلاصه گزارش آسیب شناسی صنعت خودرو
5 سال پیش
0.38 مگابایت
نوع : pdf
بازدید : 3513
منتشرکننده : CarGeek
|
راهنمای تجهیزات سیستم الکتریکی موتور سوزوکی کیزاشی
5 سال پیش
1.3 مگابایت
نوع : pdf
بازدید : 3449
منتشرکننده : CarGeek
|
راهنمای تعمیرات سیستم تهویه مطبوع سوزوکی کیزاشی
5 سال پیش
6.95 مگابایت
نوع : pdf
بازدید : 3272
منتشرکننده : CarGeek
|
جزوه آموزشی سیستم سوخت رسانی و جرقه انژکتوری خودرو
5 سال پیش
9.51 مگابایت
نوع : pdf
بازدید : 7658
منتشرکننده : CarGeek
|
راهنمای تعمیرات سیستم ایموبیلایزر پژو 405، پارس، سمند، روآ و دنا
5 سال پیش
2.47 مگابایت
نوع : pdf
بازدید : 15504
منتشرکننده : CarGeek
|
راهنمای تعمیرات جعبه دنده و سیستم تقسیم نیرو سوزوکی گرندویتارا
5 سال پیش
11.08 مگابایت
نوع : pdf
بازدید : 6688
منتشرکننده : CarGeek
|
راهنمای مدارهای الکتریکی MVM 530
5 سال پیش
12.55 مگابایت
نوع : pdf
بازدید : 22626
منتشرکننده : CarGeek
|
راهنمای برق MVM 530
5 سال پیش
4.55 مگابایت
نوع : pdf
بازدید : 75215
منتشرکننده : CarGeek
|
ساختار تهویه مطبوع خودرو
5 سال پیش
9.72 مگابایت
نوع : pdf
بازدید : 7749
منتشرکننده : CarGeek
|
معرفی و جانمایی دسته سیم ها و نقشه های الکتریکی هایما S7
5 سال پیش
18.89 مگابایت
نوع : pdf
بازدید : 5508
منتشرکننده : CarGeek
|
راهنمای تصویری نصب توربوشارژر و اینترکولر
5 سال پیش
2.8 مگابایت
نوع : pdf
بازدید : 7438
منتشرکننده : CarGeek
|
انواع مکانیزم های سیستم تعلیق
5 سال پیش
1.55 مگابایت
نوع : pdf
بازدید : 3528
منتشرکننده : CarGeek
|
راهنمای تعمیرات و سرویس کلاچ JAC S5
5 سال پیش
1.91 مگابایت
نوع : pdf
بازدید : 11550
منتشرکننده : CarGeek
|
جزوه بخش تامین و حفظ فشار سیستم تعلیق و هیدرولیک زانتیا
5 سال پیش
2.5 مگابایت
نوع : pdf
بازدید : 6211
منتشرکننده : CarGeek
|
معرفی و عیب یابی سمند میکروهیبرید با موتور XU7
5 سال پیش
0.95 مگابایت
نوع : pdf
بازدید : 6108
منتشرکننده : CarGeek
|
راهنمای کامل تعمیرات مدارهای الکتریکی پژو 405 و پارس
5 سال پیش
28.33 مگابایت
نوع : pdf
بازدید : 56440
منتشرکننده : CarGeek
|
راهنمای تعمیرات موتور و سیستم سوخت رسانی لیفان X60
5 سال پیش
7.72 مگابایت
نوع : pdf
بازدید : 9628
منتشرکننده : CarGeek
|
کاتالوگ قطعات لیفان X60- فایل 2
5 سال پیش
7.22 مگابایت
نوع : pdf
بازدید : 4484
منتشرکننده : CarGeek
|
کاتالوگ قطعات لیفان X60
5 سال پیش
7.96 مگابایت
نوع : pdf
بازدید : 12649
منتشرکننده : CarGeek
|
دانستنیهای یدکی خودرو ایساکو
5 سال پیش
6.86 مگابایت
نوع : pdf
بازدید : 4053
منتشرکننده : CarGeek
|
سیستم های الکتریکی خودروهای سنگین ATEGO و ACTROS
5 سال پیش
3.71 مگابایت
نوع : pdf
بازدید : 14406
منتشرکننده : CarGeek
|
دستورالعمل عیب یابی کلاچ
5 سال پیش
4.93 مگابایت
نوع : pdf
بازدید : 5027
منتشرکننده : CarGeek
|
راهنمای تعمیرات گیربکس گتراگ پیکان و پژو R.D
5 سال پیش
10.18 مگابایت
نوع : pdf
بازدید : 29862
منتشرکننده : CarGeek
|
راهنمای تعمیرات و عیب یابی دیفرانسیل طرح تالبوتی پیکان و پژو R.D
5 سال پیش
4.2 مگابایت
نوع : pdf
بازدید : 30678
منتشرکننده : CarGeek
|
دستورالعمل معرفی و عیب یابی سیستم کروز کنترل خودرو پژو پارس
5 سال پیش
8.75 مگابایت
نوع : pdf
بازدید : 7771
منتشرکننده : CarGeek
|
راهنمای تعمیرات مجموعه موتور و سیستم سوخت رسانی کلئوس
5 سال پیش
3.72 مگابایت
نوع : pdf
بازدید : 2613
منتشرکننده : CarGeek
|
اطلاعیه معرفی و آشنایی با خودرو رنو کلئوس
5 سال پیش
0.82 مگابایت
نوع : pdf
بازدید : 2691
منتشرکننده : CarGeek
|
راهنمای تعمیرات تزئینات داخلی و خارجی سراتو
5 سال پیش
12.04 مگابایت
نوع : pdf
بازدید : 4288
منتشرکننده : CarGeek
|
دستورالعمل تعمیر اکسل عقب پیکان و پژو R.D
5 سال پیش
4.53 مگابایت
نوع : pdf
بازدید : 18496
منتشرکننده : CarGeek
|
تعمیرات اساسی گیربکس پیکان مدل آرژانتینی
5 سال پیش
2.07 مگابایت
نوع : pdf
بازدید : 9303
منتشرکننده : CarGeek
|
راهنمای تعمیرات اساسی دیفرانسیل پیکان مدل ترکیه ای اژه
5 سال پیش
0.65 مگابایت
نوع : pdf
بازدید : 5113
منتشرکننده : CarGeek
|
فلوچارت عیب یابی "موتور خودرو هنگام رانندگی خاموش می شود"
5 سال پیش
0.77 مگابایت
نوع : pdf
بازدید : 7764
منتشرکننده : CarGeek
|
فلوچارت عیب یابی "خودرو استارت می خورد اما روشن نمی شود" پراید
5 سال پیش
1.28 مگابایت
نوع : pdf
بازدید : 9202
منتشرکننده : CarGeek
|
راهنمای تعمیر و نگهداری نیسان قشقایی
5 سال پیش
11.17 مگابایت
نوع : pdf
بازدید : 6552
منتشرکننده : CarGeek
|
معرفی سیستم گازسوز CNG در خودرو
5 سال پیش
2.75 مگابایت
نوع : pdf
بازدید : 7824
منتشرکننده : CarGeek
|
راهنمای تست قطعات مدار الکترونیکی با اهم متر
5 سال پیش
0.44 مگابایت
نوع : pdf
بازدید : 4586
منتشرکننده : CarGeek
|
معرفی و عیب یابی انواع کیتهای دوگانه سوز خودرو پژو پارس
5 سال پیش
4.83 مگابایت
نوع : pdf
بازدید : 4570
منتشرکننده : CarGeek
|
راهنمای تعمیرات موتور پژو 407
5 سال پیش
6.98 مگابایت
نوع : pdf
بازدید : 12763
منتشرکننده : CarGeek
|
راهنمای تعمیرات گیربکس پژو 407
5 سال پیش
5.76 مگابایت
نوع : pdf
بازدید : 5958
منتشرکننده : CarGeek
|
راهنمای آموزشی قطعه شناسی پژو 206
5 سال پیش
5.91 مگابایت
نوع : pdf
بازدید : 29632
منتشرکننده : CarGeek
|
راهنمای تعمیرات و سرویس موتور XUM پژو پارس ELX جدید
5 سال پیش
7.32 مگابایت
نوع : pdf
بازدید : 7103
منتشرکننده : CarGeek
|
مسیرهای برق رسانی در محصولات ایران خودرو
5 سال پیش
5.07 مگابایت
نوع : pdf
بازدید : 21257
منتشرکننده : CarGeek
|
مسیر و روش تعویض تسمه های دینام،هیدرولیک و کولر در محصولات ایران خودرو
5 سال پیش
4.22 مگابایت
نوع : pdf
بازدید : 110241
منتشرکننده : CarGeek
|
رویه تکمیل خودروی پژو 405 کلاس 4 گازسوز (نصب CNG)
5 سال پیش
9.16 مگابایت
نوع : pdf
بازدید : 6013
منتشرکننده : CarGeek
|
راهنمای نقشه خوانی مدارات الکتریکی خودرو
5 سال پیش
0.95 مگابایت
نوع : pdf
بازدید : 13089
منتشرکننده : CarGeek
|
معرفی سامانه تهویه محفظه لنگ موتور EF7
5 سال پیش
1.72 مگابایت
نوع : pdf
بازدید : 5086
منتشرکننده : CarGeek
|
لیست فارسی خطاهای OBD-II
5 سال پیش
0.55 مگابایت
نوع : pdf
بازدید : 61513
منتشرکننده : CarGeek
|
مبانی سیستم های انتقال قدرت در خودروهای سواری
5 سال پیش
4.42 مگابایت
نوع : pdf
بازدید : 3659
منتشرکننده : CarGeek
|
راهنمای تعمیرات تزئینات و تجهیزات جانبی پژو 407
5 سال پیش
33.78 مگابایت
نوع : pdf
بازدید : 6032
منتشرکننده : CarGeek
|
راهنمای عیب یابی واحد اتصالات محفظه موتور (UPC) مگان
5 سال پیش
0.69 مگابایت
نوع : pdf
بازدید : 7730
منتشرکننده : CarGeek
|
دستورالعمل پیاده و سوارکردن سیستم تعلیق نیمه مستقل ژامبونی
5 سال پیش
0.73 مگابایت
نوع : pdf
بازدید : 5610
منتشرکننده : CarGeek
|
گزارش کارآموزی کارگاه صنعتی لیفتراک
5 سال پیش
1.11 مگابایت
نوع : pdf
بازدید : 4536
منتشرکننده : CarGeek
|
امکان سنجی مهار آلاینده های اتوبوس های پایانه های داخل شهری در حالت کار درجا
5 سال پیش
2.93 مگابایت
نوع : pdf
بازدید : 4447
منتشرکننده : CarGeek
|
راهنمای تعمیرات و عیب یابی ایربگ سرنشین خودرو سورن و سمند
5 سال پیش
6.47 مگابایت
نوع : pdf
بازدید : 3880
منتشرکننده : CarGeek
|
معرفی سیستم های الکتریکال و آپشن ها در خودرو دنا
5 سال پیش
8.49 مگابایت
نوع : pdf
بازدید : 9228
منتشرکننده : CarGeek
|
جزوه آموزشی سامانه مدیریت موتور ملی EF7
5 سال پیش
1.21 مگابایت
نوع : pdf
بازدید : 7202
منتشرکننده : CarGeek
|
پروژه طراحی بالابر 2ستونه اتومبیل
5 سال پیش
1.1 مگابایت
نوع : pdf
بازدید : 3997
منتشرکننده : CarGeek
|
راهنمای گیربکس اتوماتیک امدادخودرو ایران
5 سال پیش
2.96 مگابایت
نوع : pdf
بازدید : 9124
منتشرکننده : CarGeek
|
راهنمای تعمیرات تعلیق ، فرمان و سیستم ترمز ضدقفل تندر90 و ساندرو
5 سال پیش
10.15 مگابایت
نوع : pdf
بازدید : 7454
منتشرکننده : CarGeek
|
راهنمای تعمیرات سیستم سوخت رسانی گاز طبیعی تندر90
5 سال پیش
2.37 مگابایت
نوع : pdf
بازدید : 3405
منتشرکننده : CarGeek
|
راهنمای تعمیرات سیستم سوخت رسانی بنزینی تندر90
5 سال پیش
3.73 مگابایت
نوع : pdf
بازدید : 11968
منتشرکننده : CarGeek
|
طراحی و ساخت موتور احتراق داخلی بدون میل بادامک با سوپاپ هوشمند
5 سال پیش
0.4 مگابایت
نوع : pdf
بازدید : 4168
منتشرکننده : CarGeek
|
راهنمای دودهای خروجی و عیب یابی الکتریکی کامیونت ایسوزو
5 سال پیش
2.92 مگابایت
نوع : pdf
بازدید : 8121
منتشرکننده : CarGeek
|
راهنمای تعمیرات توربوشارژ کامیونت ایسوزو
5 سال پیش
0.34 مگابایت
نوع : pdf
بازدید : 8449
منتشرکننده : CarGeek
|
روش تایمینگ موتور K4M تندر90
5 سال پیش
0.4 مگابایت
نوع : pdf
بازدید : 6238
منتشرکننده : CarGeek
|
اطلاعیه فنی معرفی خودرو سراتو
5 سال پیش
0.45 مگابایت
نوع : pdf
بازدید : 4022
منتشرکننده : CarGeek
|
طراحی شاسی خودرو هیبرید شهری کم مصرف
5 سال پیش
2.98 مگابایت
نوع : pdf
بازدید : 3640
منتشرکننده : CarGeek
|
مقدمه ای بر آیرودینامیک خودرو
5 سال پیش
2.87 مگابایت
نوع : pdf
بازدید : 3438
منتشرکننده : CarGeek
|
پایان نامه تحلیل و بررسی ساختار واحد کنترل الکترونیک (ECU) خودرو
5 سال پیش
4.34 مگابایت
نوع : pdf
بازدید : 6783
منتشرکننده : CarGeek
|
پروژه ایجاد و طراحی صنایع کوچک ، طرح توجیهی تولید سیستم کنترل الکتریکی خودرو
5 سال پیش
2.25 مگابایت
نوع : pdf
بازدید : 3925
منتشرکننده : CarGeek
|
راهنمای نصب قطعات آپشن تندر90،تیبا و X100
5 سال پیش
2.31 مگابایت
نوع : pdf
بازدید : 5046
منتشرکننده : CarGeek
|
راهنمای عیب یابی واحد اتصالات داخلی محفظه سرنشین (UCH) تندر90
5 سال پیش
0.39 مگابایت
نوع : pdf
بازدید : 5094
منتشرکننده : CarGeek
|
راهنمای عیب یابی سیستم ایربگ تندر90
5 سال پیش
0.35 مگابایت
نوع : pdf
بازدید : 7482
منتشرکننده : CarGeek
|
دستورالعمل عیب یابی سیستم ترمز ABS مدل های MGH-25وMGH-60 پژو 405،پارس و سمند
5 سال پیش
1.28 مگابایت
نوع : pdf
بازدید : 4780
منتشرکننده : CarGeek
|
لیست لغات فنی مطابق با استاندارد SAE J1930 و معادل فارسی آن ها
5 سال پیش
0.1 مگابایت
نوع : pdf
بازدید : 2805
منتشرکننده : CarGeek
|
راهنمای تعمیرات قسمت های الکتریکی اتاق و شاسی کامیونت ایسوزو
5 سال پیش
4.41 مگابایت
نوع : pdf
بازدید : 44644
منتشرکننده : CarGeek
|
راهنمای تعمیرات تجهیزات قسمت الکتریکی موتور کامیونت ایسوزو
5 سال پیش
1.17 مگابایت
نوع : pdf
بازدید : 33508
منتشرکننده : CarGeek
|
راهنمای نگه داری و روغن کاری کامیونت ایسوزو
5 سال پیش
0.35 مگابایت
نوع : pdf
بازدید : 29484
منتشرکننده : CarGeek
|
راهنمای تعمیرات و سرویس کولر ایسوزو 6تن
5 سال پیش
0.82 مگابایت
نوع : pdf
بازدید : 15056
منتشرکننده : CarGeek
|
راهنمای تعمیرات اتاق و شاسی ایسوزو 6تن
5 سال پیش
2.85 مگابایت
نوع : pdf
بازدید : 11794
منتشرکننده : CarGeek
|
راهنمای سیم کشی های الکتریکی برلیانس H330
5 سال پیش
5.06 مگابایت
نوع : pdf
بازدید : 16128
منتشرکننده : CarGeek
|
راهنمای تعمیرات و سرویس مدارهای الکتریکی برلیانس H330
5 سال پیش
5.56 مگابایت
نوع : pdf
بازدید : 8521
منتشرکننده : CarGeek
|
راهنمای سیم کشی های الکتریکی برلیانس H320
5 سال پیش
1.55 مگابایت
نوع : pdf
بازدید : 8361
منتشرکننده : CarGeek
|
راهنمای تعمیرات و سرویس مدارهای الکتریکی برلیانس H320- فایل 2
5 سال پیش
4.59 مگابایت
نوع : pdf
بازدید : 4280
منتشرکننده : CarGeek
|
راهنمای تعمیرات و سرویس مدارهای الکتریکی برلیانس H320
5 سال پیش
9.79 مگابایت
نوع : pdf
بازدید : 6018
منتشرکننده : CarGeek
|
کتاب Modern Electric,Hybrid Electric & Fuel Cell Vehicles
5 سال پیش
11.39 مگابایت
نوع : pdf
بازدید : 4013
منتشرکننده : CarGeek
|
راهنمای تغییر کیلومتر کارکرد خودرو
5 سال پیش
1.13 مگابایت
نوع : pdf
بازدید : 4806
منتشرکننده : CarGeek
|
راهنمای سیستم انژکتور بوش 7.4.4 پژو 206
5 سال پیش
3.1 مگابایت
نوع : pdf
بازدید : 8924
منتشرکننده : CarGeek
|
راهنمای مدارها و سیم کشی های الکتریکی لیفان 820
5 سال پیش
6.34 مگابایت
نوع : pdf
بازدید : 9368
منتشرکننده : CarGeek
|
راهنمای تعمیرات و سرویس تهویه مطبوع ساینا
5 سال پیش
5.56 مگابایت
نوع : pdf
بازدید : 44957
منتشرکننده : CarGeek
|
راهنمای تعمیرات سیستم سوخت رسانی آریو
5 سال پیش
4.76 مگابایت
نوع : pdf
بازدید : 10768
منتشرکننده : CarGeek
|
راهنمای تعمیرات موتور سایپا آریو (موتور 4A91S)
5 سال پیش
9.35 مگابایت
نوع : pdf
بازدید : 17292
منتشرکننده : CarGeek
|
راهنمای عیب یابی سیستم های زانتیا
5 سال پیش
1.33 مگابایت
نوع : pdf
بازدید : 36166
منتشرکننده : CarGeek
|
کتاب Engine Testing: Theory and Practice
5 سال پیش
4.3 مگابایت
نوع : pdf
بازدید : 3717
منتشرکننده : CarGeek
|
راهنمای تعمیرات و عیب یابی 405SLC-CNG ساکس500(SAX500)
5 سال پیش
4.81 مگابایت
نوع : pdf
بازدید : 16785
منتشرکننده : CarGeek
|
راهنمای تعمیرات سیستم سوخت رسانی ایسوزو 6تن مدل NPR70 (موتور4HE توربودیزل)
5 سال پیش
1.24 مگابایت
نوع : pdf
بازدید : 23410
منتشرکننده : CarGeek
|
راهنمای تعمیرات موتور ایسوزو 6تن مدل NPR70 (موتور4HE توربودیزل)
5 سال پیش
4.03 مگابایت
نوع : pdf
بازدید : 25733
منتشرکننده : CarGeek
|
راهنمای تعمیر و نگه داری سیتروئن C5 New
5 سال پیش
3.19 مگابایت
نوع : pdf
بازدید : 5990
منتشرکننده : CarGeek
|
راهنمای عیب یابی سیستم تهویه مطبوع سراتو
5 سال پیش
9.51 مگابایت
نوع : pdf
بازدید : 8028
منتشرکننده : CarGeek
|
راهنمای تعمیرات و سرویس سیستم تهویه مطبوع سراتو
5 سال پیش
6.12 مگابایت
نوع : pdf
بازدید : 9518
منتشرکننده : CarGeek
|
راهنمای تعمیرات و سرویس تجهیزات الکتریکی ساینا (سایپا 232)
5 سال پیش
8.46 مگابایت
نوع : pdf
بازدید : 10268
منتشرکننده : CarGeek
|
اطلاعیه معرفی خودرو ساینا (سایپا 232)
5 سال پیش
0.83 مگابایت
نوع : pdf
بازدید : 5278
منتشرکننده : CarGeek
|
نکاتی درباره تعمیرات ECU خودروهای ایرانی
5 سال پیش
0.45 مگابایت
نوع : pdf
بازدید : 4945
منتشرکننده : CarGeek
|
دستورالعمل معرفی و عیب یابی سیستم ABS روآ و وانت
5 سال پیش
1.53 مگابایت
نوع : pdf
بازدید : 9838
منتشرکننده : CarGeek
|
معرفی سیستم یورو4 وانت پیکان
5 سال پیش
1.32 مگابایت
نوع : pdf
بازدید : 8222
منتشرکننده : CarGeek
|
راهنمای تعمیرات سیستم موتور پراید (موتور B3)
5 سال پیش
6.57 مگابایت
نوع : pdf
بازدید : 23181
منتشرکننده : CarGeek
|
راهنمای تعمیرات مدارهای الکتریکی سمند با موتور XU7
5 سال پیش
21.58 مگابایت
نوع : pdf
بازدید : 7763
منتشرکننده : CarGeek
|
راهنمای تعمیرات قطعات الکتریکی پژو پارس + دیاگرام دسته سیم ها
5 سال پیش
3.92 مگابایت
نوع : pdf
بازدید : 12513
منتشرکننده : CarGeek
|
راهنمای تعمیرات موتور TU5JP4 پژو 206 و پژو 207
5 سال پیش
10.2 مگابایت
نوع : pdf
بازدید : 37499
منتشرکننده : CarGeek
|
جزوه آموزشی اپراتوری دامپ تراک کوماتسو
5 سال پیش
3.4 مگابایت
نوع : pdf
بازدید : 34780
منتشرکننده : CarGeek
|
راهنمای تعمیرات سیستم ترمز پژو 405، پارس و سمند
5 سال پیش
4.41 مگابایت
نوع : pdf
بازدید : 36443
منتشرکننده : CarGeek
|
آشنایی با دریچه گاز در خودرو
5 سال پیش
2.05 مگابایت
نوع : pdf
بازدید : 9916
منتشرکننده : CarGeek
|
راهنمای تعمیرات سیستم تعلیق جلو و عقب پژو 405 وپارس و سمند و دنا
5 سال پیش
2.68 مگابایت
نوع : pdf
بازدید : 48060
منتشرکننده : CarGeek
|
راهنمای تعمیرات ECUهای ساژم ،زیمنس و بوش
5 سال پیش
2.07 مگابایت
نوع : pdf
بازدید : 7593
منتشرکننده : CarGeek
|
راهنمای تعمیر و نگه داری نیسان مورانو (Z50-Z51)
5 سال پیش
5.98 مگابایت
نوع : pdf
بازدید : 7020
منتشرکننده : CarGeek
|
راهنمای تعمیرات مواد پلاستیکی خودرو
5 سال پیش
8.1 مگابایت
نوع : pdf
بازدید : 2669
منتشرکننده : CarGeek
|
آموزش تعویض تسمه تایم موتور K4M رنو (تندر90،مگان،داستر،ساندرو)
5 سال پیش
3.1 مگابایت
نوع : pdf
بازدید : 5426
منتشرکننده : CarGeek
|
راهنمای کامل تعمیرات دوو ماتیز
5 سال پیش
20.27 مگابایت
نوع : pdf
بازدید : 43971
منتشرکننده : CarGeek
|
راهنمای تعمیرات گیربکس دوکلاچه اتوماتیک جک S5
5 سال پیش
3.63 مگابایت
نوع : pdf
بازدید : 16655
منتشرکننده : CarGeek
|
معرفی سامانه روانکاری موتور EF7
5 سال پیش
0.66 مگابایت
نوع : pdf
بازدید : 8731
منتشرکننده : CarGeek
|
راهنمای تعمیرات و سرویس گیربکس و انتقال قدرت CVT مورانو جدید
5 سال پیش
5.37 مگابایت
نوع : pdf
بازدید : 4152
منتشرکننده : CarGeek
|
راهنمای عیب یابی گیربکس CVT نیسان مورانو
5 سال پیش
1.98 مگابایت
نوع : pdf
بازدید : 5874
منتشرکننده : CarGeek
|
راهنمای تعمیرات گیربکس CVT نیسان مورانو
5 سال پیش
5.28 مگابایت
نوع : pdf
بازدید : 7084
منتشرکننده : CarGeek
|
راهنمای تعمیرات گیربکس CVT نیسان تیانا
5 سال پیش
9.58 مگابایت
نوع : pdf
بازدید : 7771
منتشرکننده : CarGeek
|
راهنمای تعمیرات وسرویس سیستم روانکاری موتور نیسان تیانا
5 سال پیش
1.65 مگابایت
نوع : pdf
بازدید : 4408
منتشرکننده : CarGeek
|
راهنمای تعمیرات و سرویس سیستم خنک کننده موتور نیسان تیانا
5 سال پیش
2.07 مگابایت
نوع : pdf
بازدید : 6744
منتشرکننده : CarGeek
|
راهنمای تعمیرات تجهیزات الکتریکی چانگان CS35
5 سال پیش
29.63 مگابایت
نوع : pdf
بازدید : 5561
منتشرکننده : CarGeek
|
راهنمای تعمیرات بدنه درب های جانبی تندر90
5 سال پیش
1.93 مگابایت
نوع : pdf
بازدید : 8882
منتشرکننده : CarGeek
|
راهنمای بازکردن-نصب مجدد تجهیزات داخلی مگان
5 سال پیش
5.41 مگابایت
نوع : pdf
بازدید : 25072
منتشرکننده : CarGeek
|
کتاب راهنمای تعمیر و نگه داری سیستم های الکتریکی اتومبیل های صبا و نسیم (پراید)
5 سال پیش
31.65 مگابایت
نوع : pdf
بازدید : 14348
منتشرکننده : CarGeek
|
راهنمای تعمیرات سیستم سوخت رسانی نیسان تیانا
5 سال پیش
0.75 مگابایت
نوع : pdf
بازدید : 4939
منتشرکننده : CarGeek
|
راهنمای تعمیرات واحد کنترل هشدار دهنده (ACU) سمند
5 سال پیش
6.07 مگابایت
نوع : pdf
بازدید : 118061
منتشرکننده : CarGeek
|
راهنمای آموزشی رنو : تجهیزات الکترونیکی خودرو- فایل 2
5 سال پیش
24.33 مگابایت
نوع : pdf
بازدید : 3827
منتشرکننده : CarGeek
|
راهنمای آموزشی رنو : تجهیزات الکترونیکی خودرو
5 سال پیش
22.35 مگابایت
نوع : pdf
بازدید : 7221
منتشرکننده : CarGeek
|
راهنمای تعمیر و نگه داری نیسان تیانا (نیسان J32)
5 سال پیش
3.58 مگابایت
نوع : pdf
بازدید : 9247
منتشرکننده : CarGeek
|
راهنمای تعمیرات مکانیکی موتور نیسان تیانا (موتورVQ35DE-VQ25DE)
5 سال پیش
21.28 مگابایت
نوع : pdf
بازدید : 5578
منتشرکننده : CarGeek
|
راهنما و دیاگرام های سیم کشی ها و دسته سیم های مزدا3
5 سال پیش
33.18 مگابایت
نوع : pdf
بازدید : 6308
منتشرکننده : CarGeek
|
راهنمای کامل تعمیرات لیفان X60
5 سال پیش
25.9 مگابایت
نوع : pdf
بازدید : 37697
منتشرکننده : CarGeek
|
نقشه ها و راهنمای سیستم های الکتریکی MVM 110
5 سال پیش
4.76 مگابایت
نوع : pdf
بازدید : 84079
منتشرکننده : CarGeek
|
راهنمای تعمیرات سیستم سوخت رسانی MVM X33
5 سال پیش
4.51 مگابایت
نوع : pdf
بازدید : 14485
منتشرکننده : CarGeek
|
کتاب آموزشی سیستم گازسوز CNG سایپا
5 سال پیش
3.05 مگابایت
نوع : pdf
بازدید : 20849
منتشرکننده : CarGeek
|
راهنمای تعمیرات و اورهال موتور F4 رنو مگان 2000- فایل 2
5 سال پیش
22.43 مگابایت
نوع : pdf
بازدید : 3664
منتشرکننده : CarGeek
|
راهنمای تعمیرات و اورهال موتور F4 رنو مگان 2000
5 سال پیش
20.5 مگابایت
نوع : pdf
بازدید : 9269
منتشرکننده : CarGeek
|
راهنمای تعمیرات سیستم ضدسرقت (ایموبیلایزر) سراتو
5 سال پیش
5.71 مگابایت
نوع : pdf
بازدید : 5306
منتشرکننده : CarGeek
|
راهنمای تعمیرات نقشه های الکتریکی خودروی دنا
5 سال پیش
2.5 مگابایت
نوع : pdf
بازدید : 26258
منتشرکننده : CarGeek
|
راهنمای تعمیرات مدارهای الکتریکی تیبا2
5 سال پیش
5.45 مگابایت
نوع : pdf
بازدید : 6688
منتشرکننده : CarGeek
|
شناسایی و نحوه تعویض قطعات سیستم ضدسرقت (ایموبیلایزر) پراید و خانواده X100 و X200 سایپا
5 سال پیش
2.63 مگابایت
نوع : pdf
بازدید : 6275
منتشرکننده : CarGeek
|
راهنمای فنی شمع خودرو
5 سال پیش
7.78 مگابایت
نوع : pdf
بازدید : 7388
منتشرکننده : CarGeek
|
راهنمای جامع استفاده از ابزار مخصوص پراید
5 سال پیش
9.59 مگابایت
نوع : pdf
بازدید : 7044
منتشرکننده : CarGeek
|
راهنمای کارگاه مبانی الکتریسیته خودرو مقدماتی رنو
5 سال پیش
16.61 مگابایت
نوع : pdf
بازدید : 3884
منتشرکننده : CarGeek
|
راهنمای عیب یابی سیستم سوخت رسانی جانسون کنترلز پراید
5 سال پیش
7.14 مگابایت
نوع : pdf
بازدید : 4404
منتشرکننده : CarGeek
|
راهنمای عیب یابی سیستم سوخت رسانی زیمنس قدیم پراید
5 سال پیش
5.93 مگابایت
نوع : pdf
بازدید : 23151
منتشرکننده : CarGeek
|
راهنمای عیب یابی سیستم انتقال قدرت اتوماتیک رنو مگان (راهنمای اصلی)
5 سال پیش
1.22 مگابایت
نوع : pdf
بازدید : 4073
منتشرکننده : CarGeek
|
دستورالعمل تشخیص عیب بوستر ترمز پراید
5 سال پیش
0.73 مگابایت
نوع : pdf
بازدید : 9582
منتشرکننده : CarGeek
|
رویه نصب و تبدیل خودرو مزدا2000 کاربراتوری به سیستم دوگانه سوز
5 سال پیش
1.4 مگابایت
نوع : pdf
بازدید : 6709
منتشرکننده : CarGeek
|
دفترچه راهنمای مرسدس بنز اسپرینتر 314 (Mercedes-Benz Sprinter)
5 سال پیش
2.11 مگابایت
نوع : pdf
بازدید : 23213
منتشرکننده : CarGeek
|
راهنمای سرویس و نگه داری مرسدس بنز اسپرینتر 314 (Mercedes-Benz Sprinter)
5 سال پیش
1.21 مگابایت
نوع : pdf
بازدید : 6005
منتشرکننده : CarGeek
|
اطلاعات فنی موتوری مرسدس بنز اسپرینتر (Mercedes-Benz Sprinter)
5 سال پیش
7.87 مگابایت
نوع : pdf
بازدید : 9588
منتشرکننده : CarGeek
|
جزوه آموزشی تندر90 ویژه مشتریان
5 سال پیش
2.33 مگابایت
نوع : pdf
بازدید : 6633
منتشرکننده : CarGeek
|
جزوه آموزشی گیربکس دستی MA5 خودرو پژو 206
5 سال پیش
3.69 مگابایت
نوع : pdf
بازدید : 17894
منتشرکننده : CarGeek
|
جزوه آموزشی گیربکس BE3 خودروهای پژو 405 ، پارس و سمند
5 سال پیش
4.66 مگابایت
نوع : pdf
بازدید : 30598
منتشرکننده : CarGeek
|
راهنمای تعمیرات و سرویس سیستم گازسوز CNG پراید
5 سال پیش
1.72 مگابایت
نوع : pdf
بازدید : 14352
منتشرکننده : CarGeek
|
دستورالعمل تشخیص عیب میل فرمان عمودی (تلسکوپی) پراید و تعویض آن
5 سال پیش
0.4 مگابایت
نوع : pdf
بازدید : 10273
منتشرکننده : CarGeek
|
عیب یابی صدا ، لرزش و تکان در خودرو
5 سال پیش
1.07 مگابایت
نوع : pdf
بازدید : 3739
منتشرکننده : CarGeek
|
فرهنگ لغت تصویری انگلیسی خودرو
5 سال پیش
2.42 مگابایت
نوع : pdf
بازدید : 17110
منتشرکننده : CarGeek
|
راهنمای سیم کشی های الکتریکی برلیانس H220-H230
5 سال پیش
11.23 مگابایت
نوع : pdf
بازدید : 12285
منتشرکننده : CarGeek
|
راهنمای تعمیرات تجهیزات الکتریکی برلیانس H220-H230
5 سال پیش
6.99 مگابایت
نوع : pdf
بازدید : 6039
منتشرکننده : CarGeek
|
راهنمای مدارات الکتریکی سیستم سوخت رسانی ساژم و ولئو پراید
5 سال پیش
10.57 مگابایت
نوع : pdf
بازدید : 25538
منتشرکننده : CarGeek
|
راهنمای مدارات الکتریکی سیستم سوخت رسانی زیمنس پراید
5 سال پیش
10.52 مگابایت
نوع : pdf
بازدید : 29751
منتشرکننده : CarGeek
|
راهنمای تعمیرات و سرویس اکسل های جلو و عقب سراتو
5 سال پیش
8.26 مگابایت
نوع : pdf
بازدید : 5777
منتشرکننده : CarGeek
|
راهنمای تعمیرات گیربکس اتوماتیک برلیانس H220وH230 (جعبه دنده 452ASG)
5 سال پیش
20.18 مگابایت
نوع : pdf
بازدید : 11657
منتشرکننده : CarGeek
|
راهنمای عیب یابی سیستم های CPH زانتیا
5 سال پیش
3.93 مگابایت
نوع : pdf
بازدید : 10499
منتشرکننده : CarGeek
|
راهنمای آموزشی سیستم انژکتور خودرو سوزوکی گرندویتارا
5 سال پیش
2.33 مگابایت
نوع : pdf
بازدید : 3973
منتشرکننده : CarGeek
|
راهنمای آموزشی برق خودرو سوزوکی گرندویتارا
5 سال پیش
5.94 مگابایت
نوع : pdf
بازدید : 6913
منتشرکننده : CarGeek
|
راهنمای تعمیرات سیستم انتقال قدرت زانتیا (گیربکس ، دیفرانسیل ، کلاچ ، پلوس)
5 سال پیش
12.26 مگابایت
نوع : pdf
بازدید : 10755
منتشرکننده : CarGeek
|
راهنمای کامل تعمیرات مجموعه موتور و متعلقات موتور K4M رنو
5 سال پیش
19.78 مگابایت
نوع : pdf
بازدید : 7585
منتشرکننده : CarGeek
|
جزوه دوره تخصصی برق و انژکتور مگان دانشگاه صنعتی شریف
5 سال پیش
8.48 مگابایت
نوع : pdf
بازدید : 9316
منتشرکننده : CarGeek
|
آشنایی با سیستم برق خودرو پژو 206 مالتی پلکس
5 سال پیش
0.12 مگابایت
نوع : pdf
بازدید : 5060
منتشرکننده : CarGeek
|
عوامل موثر بر صدای لنت اتومبیل و راههای حذف صدا
5 سال پیش
0.16 مگابایت
نوع : pdf
بازدید : 3905
منتشرکننده : CarGeek
|
جزوه آموزشی روش شناسایی ایرادات خودرو سمند با موتور ملی EF7
5 سال پیش
1.21 مگابایت
نوع : pdf
بازدید : 11845
منتشرکننده : CarGeek
|
جزوه امدادخودرو درخصوص موتورملیef7 خودروهای سمند و دنا
5 سال پیش
5.05 مگابایت
نوع : pdf
بازدید : 7858
منتشرکننده : CarGeek
|
EF7 Engine Integration On Samand
5 سال پیش
7.31 مگابایت
نوع : pdf
بازدید : 7170
منتشرکننده : CarGeek
|
نقشه کامل سیم کشی و دسته سیم های لیفان 620
5 سال پیش
18.04 مگابایت
نوع : pdf
بازدید : 29199
منتشرکننده : CarGeek
|
جزوه دوره آموزشی کولر پراید
5 سال پیش
6.18 مگابایت
نوع : pdf
بازدید : 55888
منتشرکننده : CarGeek
|
راهنمای تعمیرات سیستم الکتریکی سیتروئن C5
5 سال پیش
1.97 مگابایت
نوع : pdf
بازدید : 10072
منتشرکننده : CarGeek
|
کنترل خشم در رانندگی
5 سال پیش
0.29 مگابایت
نوع : pdf
بازدید : 3077
منتشرکننده : CarGeek
|
دستورالعمل رفع روغن ریزی جعبه فرمان پیکان وانت
5 سال پیش
2.11 مگابایت
نوع : pdf
بازدید : 21535
منتشرکننده : CarGeek
|
راهنمای تعمیرات و سرویس سیستم سوخت رسانی انژکتوری KIA طرح زیمنس سایپا 141
5 سال پیش
10.63 مگابایت
نوع : pdf
بازدید : 4395
منتشرکننده : CarGeek
|
شرح کامل خروجی سوکت های BSM,BSI و ECUهای بوش پژو 206
5 سال پیش
1.25 مگابایت
نوع : pdf
بازدید : 133783
منتشرکننده : CarGeek
|
جزوه آموزشی سیستم دوگانه سوز CNG ایساکو
5 سال پیش
42.95 مگابایت
نوع : pdf
بازدید : 9953
منتشرکننده : CarGeek
|
راهنمای امدادخودرو درخصوص برق رنو کپچر
5 سال پیش
4.26 مگابایت
نوع : pdf
بازدید : 4431
منتشرکننده : CarGeek
|
دیاگرام های برق و سیم کشی تویوتا کمری 2007
5 سال پیش
7.7 مگابایت
نوع : pdf
بازدید : 18647
منتشرکننده : CarGeek
|
راهنمای تعمیرات گیربکس اتوماتیک پراید
5 سال پیش
15.09 مگابایت
نوع : pdf
بازدید : 11267
منتشرکننده : CarGeek
|
راهنمای تعمیرات و صافکاری بدنه رانا
5 سال پیش
43.18 مگابایت
نوع : pdf
بازدید : 5967
منتشرکننده : CarGeek
|
راهنمای صافکاری پژو 206
5 سال پیش
7.7 مگابایت
نوع : pdf
بازدید : 8544
منتشرکننده : CarGeek
|
راهنمای تعمیرات تزئینات سایپا 141
5 سال پیش
6.69 مگابایت
نوع : pdf
بازدید : 7094
منتشرکننده : CarGeek
|
راهنمای تعمیرات بدنه سایپا 141
5 سال پیش
23.91 مگابایت
نوع : pdf
بازدید : 5926
منتشرکننده : CarGeek
|
راهنمای کامل برق و الکترونیک زامیاد دیزل (وانت نیسان)
5 سال پیش
7.69 مگابایت
نوع : pdf
بازدید : 62456
منتشرکننده : CarGeek
|
راهنمای تعمیرات سیستم سوخت رسانی سراتو 2000
5 سال پیش
7.27 مگابایت
نوع : pdf
بازدید : 7630
منتشرکننده : CarGeek
|
راهنمای تعمیرات سیستم سوخت رسانی سراتو 1600
5 سال پیش
17.7 مگابایت
نوع : pdf
بازدید : 4019
منتشرکننده : CarGeek
|
راهنمای تعمیرات سیستم سوخت رسانی بوش (Bosch) پراید
5 سال پیش
3.95 مگابایت
نوع : pdf
بازدید : 8188
منتشرکننده : CarGeek
|
راهنمای تعمیرات گیربکس اتوماتیک MVM X33 - CHERY Tiggo
5 سال پیش
7.46 مگابایت
نوع : pdf
بازدید : 17255
منتشرکننده : CarGeek
|
اطلاعیه معرفی و آشنایی فنی با خودرو رنو ساندرو
5 سال پیش
1.87 مگابایت
نوع : pdf
بازدید : 4227
منتشرکننده : CarGeek
|
راهنمای تعمیرات و سرویس بدنه برلیانس H320
5 سال پیش
8.36 مگابایت
نوع : pdf
بازدید : 7630
منتشرکننده : CarGeek
|
راهنمای تعمیرات و سرویس بدنه برلیانس H330
5 سال پیش
9.92 مگابایت
نوع : pdf
بازدید : 6140
منتشرکننده : CarGeek
|
راهنمای تعمیرات سیستم خنک کننده و اگزوز موتور XU7 پژو 405 ، پارس و سمند
5 سال پیش
4.25 مگابایت
نوع : pdf
بازدید : 22505
منتشرکننده : CarGeek
|
راهنمای تعمیرات شاسی و بدنه نیسان جونیور (نیسان وانت)
5 سال پیش
2.26 مگابایت
نوع : pdf
بازدید : 27052
منتشرکننده : CarGeek
|
راهنمای تعمیرات موتور فیات سی ینا (Siena)
5 سال پیش
4.95 مگابایت
نوع : pdf
بازدید : 15172
منتشرکننده : CarGeek
|
راهنمای تعمیرات تزئینات خارجی ریو
5 سال پیش
1.04 مگابایت
نوع : pdf
بازدید : 8167
منتشرکننده : CarGeek
|
راهنمای تعمیرات تزئینات داخلی ریو
5 سال پیش
2.21 مگابایت
نوع : pdf
بازدید : 15483
منتشرکننده : CarGeek
|
راهنمای تعمیرات و عیب یابی جعبه دنده خودکار (گیربکس اتوماتیک) سراتو- فایل 2
5 سال پیش
22.95 مگابایت
نوع : pdf
بازدید : 3944
منتشرکننده : CarGeek
|
راهنمای تعمیرات و عیب یابی جعبه دنده خودکار (گیربکس اتوماتیک) سراتو
5 سال پیش
8.45 مگابایت
نوع : pdf
بازدید : 8188
منتشرکننده : CarGeek
|
راهنمای تعمیرات گیربکس دستی سراتو
5 سال پیش
4.66 مگابایت
نوع : pdf
بازدید : 4128
منتشرکننده : CarGeek
|
راهنمای الکتریکال و تعمیرات قطعات الکتریکی موتور سمند (EFP-EF7 EMS Siemens Petrol MUX)
5 سال پیش
5.46 مگابایت
نوع : pdf
بازدید : 11825
منتشرکننده : CarGeek
|
راهنمای دانلود ECU خودروهای داخلی با دستگاه دیاگ
5 سال پیش
0.41 مگابایت
نوع : pdf
بازدید : 8164
منتشرکننده : CarGeek
|
راهنمای تعمیرات تعلیق ، انتقال نیرو/اکسل ، ترمز و فرمان مزدا3
5 سال پیش
11.72 مگابایت
نوع : pdf
بازدید : 6837
منتشرکننده : CarGeek
|
راهنمای تعمیرات و سرویس مدارهای الکتریکی سراتو
5 سال پیش
22.72 مگابایت
نوع : pdf
بازدید : 9473
منتشرکننده : CarGeek
|
راهنمای تعمیرات موتور سواری مزدا 323 GLX
5 سال پیش
15.66 مگابایت
نوع : pdf
بازدید : 9988
منتشرکننده : CarGeek
|
راهنمای تعمیرات گیربکس اتوماتیک ریو (F4E-K)
5 سال پیش
13.94 مگابایت
نوع : pdf
بازدید : 7401
منتشرکننده : CarGeek
|
راهنمای تعمیرات تجهیزات الکتریکی ریو
5 سال پیش
4.27 مگابایت
نوع : pdf
بازدید : 7532
منتشرکننده : CarGeek
|
راهنمای عیب یابی مجموعه موتور ریو
5 سال پیش
1.02 مگابایت
نوع : pdf
بازدید : 7132
منتشرکننده : CarGeek
|
راهنمای تعمیرات سیستم موتور ریو
5 سال پیش
4.59 مگابایت
نوع : pdf
بازدید : 11233
منتشرکننده : CarGeek
|
راهنمای تعمیرات و سرویس موتور CNG تیبا
5 سال پیش
9.61 مگابایت
نوع : pdf
بازدید : 7288
منتشرکننده : CarGeek
|
راهنمای تعمیرات سیستم هیدرولیک تعلیق زانتیا
5 سال پیش
9.46 مگابایت
نوع : pdf
بازدید : 12562
منتشرکننده : CarGeek
|
راهنمای تعمیرات سیستم هیدرولیک ترمز زانتیا
5 سال پیش
5.17 مگابایت
نوع : pdf
بازدید : 19202
منتشرکننده : CarGeek
|
راهنمای تعمیرات مدارها و تجهیزات جانبی الکتریکی زانتیا
5 سال پیش
8.68 مگابایت
نوع : pdf
بازدید : 9672
منتشرکننده : CarGeek
|
راهنمای تعمیرات تزئینات زانتیا
5 سال پیش
10.06 مگابایت
نوع : pdf
بازدید : 13857
منتشرکننده : CarGeek
|
راهنمای تعمیرات بدنه زانتیا
5 سال پیش
20.75 مگابایت
نوع : pdf
بازدید : 12852
منتشرکننده : CarGeek
|
راهنمای سیستم جرقه زنی و انژکتور Magneti Marelli 6LPA
5 سال پیش
0.7 مگابایت
نوع : pdf
بازدید : 8128
منتشرکننده : CarGeek
|
راهنمای سیستم سوخت رسانی و استراتژی ECU موتور مگنت مارلی MM6LPB موتور EW10Aو EW7A پژو 407
5 سال پیش
1.7 مگابایت
نوع : pdf
بازدید : 4346
منتشرکننده : CarGeek
|
راهنمای تعمیرات و عیب یابی گیرکس اتوماتیک و سیستم کلاچ هیدرولیک پژو 407
5 سال پیش
4.64 مگابایت
نوع : pdf
بازدید : 3887
منتشرکننده : CarGeek
|
راهنمای کامل تعمیرات خودرو گل
5 سال پیش
32.79 مگابایت
نوع : pdf
بازدید : 37302
منتشرکننده : CarGeek
|
جزوه آموزشی سیستم تعلیق پژو405 ،پژو پارس ،سمند و پژو206
5 سال پیش
4.84 مگابایت
نوع : pdf
بازدید : 20782
منتشرکننده : CarGeek
|
راهنمای کامل تعمیرات مزدا 323 FL
5 سال پیش
41.92 مگابایت
نوع : pdf
بازدید : 25593
منتشرکننده : CarGeek
|
راهنمای سرویس و تعمیرات سیستم فرمان هیدرولیک پراید
5 سال پیش
1.95 مگابایت
نوع : pdf
بازدید : 21508
منتشرکننده : CarGeek
|
سیستم جرقه زنی الکتریکی خودرو
5 سال پیش
3.1 مگابایت
نوع : pdf
بازدید : 5410
منتشرکننده : CarGeek
|
اساس کار و اصول تعمیر موتورهای دیزل
5 سال پیش
5.04 مگابایت
نوع : pdf
بازدید : 11633
منتشرکننده : CarGeek
|
راهنمای تعمیرات موتور لیفان 620
5 سال پیش
11.58 مگابایت
نوع : pdf
بازدید : 19018
منتشرکننده : CarGeek
|
راهنمای تعمیرات گیربکس لیفان 620
5 سال پیش
3.85 مگابایت
نوع : pdf
بازدید : 10923
منتشرکننده : CarGeek
|
راهنمای امدادخودرو سمند و سورن مالتی پلکس
5 سال پیش
19.49 مگابایت
نوع : pdf
بازدید : 54648
منتشرکننده : CarGeek
|
آشنایی با سیستم دوگانه سوز Continentalکروز (Bi-Fuel)
5 سال پیش
1.37 مگابایت
نوع : pdf
بازدید : 6560
منتشرکننده : CarGeek
|
راهنمای کنترل یونیت ها و جعبه فیوزهای محصولات ایران خودرو
5 سال پیش
6.56 مگابایت
نوع : pdf
بازدید : 34129
منتشرکننده : CarGeek
|
دیاگرام های سیستم های برق خودروهای پژو پارس ، 405 و آردی
5 سال پیش
6.52 مگابایت
نوع : pdf
بازدید : 19548
منتشرکننده : CarGeek
|
دستورالعمل عیب یابی گیربکس BE
5 سال پیش
0.63 مگابایت
نوع : pdf
بازدید : 6495
منتشرکننده : CarGeek
|
معرفی اجزاء و انواع عملگرها در سیستم انژکتوری خودرو
5 سال پیش
3.06 مگابایت
نوع : pdf
بازدید : 4523
منتشرکننده : CarGeek
|
اصول عملکرد توربوشارژ
5 سال پیش
3.61 مگابایت
نوع : pdf
بازدید : 7886
منتشرکننده : CarGeek
|
راهنمای انواع ECU نصب شده روی خودروهای ایرانی
5 سال پیش
3.37 مگابایت
نوع : pdf
بازدید : 64345
منتشرکننده : CarGeek
|
جزوه دوره آموزشی تعمیرات ECU
5 سال پیش
11.47 مگابایت
نوع : pdf
بازدید : 5555
منتشرکننده : CarGeek
|
جزوه کلاس تعمیرات ECU
5 سال پیش
4.52 مگابایت
نوع : pdf
بازدید : 8173
منتشرکننده : CarGeek
|
جزوه کلاس تعمیر ECU
5 سال پیش
3.31 مگابایت
نوع : pdf
بازدید : 9047
منتشرکننده : CarGeek
|
معرفی و راهنمای فنی موتورهای پژو 206
5 سال پیش
5.16 مگابایت
نوع : pdf
بازدید : 6372
منتشرکننده : CarGeek
|
فلوچارت عیب یابی "کیلومترشمار کار نمی کند"
5 سال پیش
1.03 مگابایت
نوع : pdf
بازدید : 53182
منتشرکننده : CarGeek
|
نقشه شماتیک مولتی پلکس (Node CCN - SMS MUX)
5 سال پیش
17.47 مگابایت
نوع : pdf
بازدید : 29011
منتشرکننده : CarGeek
|
همه چیز راجع به روغن موتور و روانکار موتوری
5 سال پیش
0.98 مگابایت
نوع : pdf
بازدید : 3771
منتشرکننده : CarGeek
|
نحوه صحیح درآوردن و جازدن بلبرینگ چرخ جلو پژو 405 ، پارس ، سمند و دنا
5 سال پیش
0.53 مگابایت
نوع : pdf
بازدید : 24999
منتشرکننده : CarGeek
|
مکانیزم عملکرد و راهنمای تعمیرات موتور 4سیلندر MVM110 (موتور SQR 472)
5 سال پیش
0.94 مگابایت
نوع : pdf
بازدید : 5693
منتشرکننده : CarGeek
|
نقشه سوخت و جرقه ECU مگنت مارلی
5 سال پیش
0.21 مگابایت
نوع : pdf
بازدید : 11011
منتشرکننده : CarGeek
|
نقشه شماتیک ECU Bosch ME 7.4.9 SMS MUX موتور EF7
5 سال پیش
14.65 مگابایت
نوع : pdf
بازدید : 26969
منتشرکننده : CarGeek
|
معرفی گیربکس CVT سوزوکی کیزاشی
5 سال پیش
3.4 مگابایت
نوع : pdf
بازدید : 3774
منتشرکننده : CarGeek
|
سیستم های انژکتوری دیزل بوش
5 سال پیش
0.72 مگابایت
نوع : pdf
بازدید : 5288
منتشرکننده : CarGeek
|
نقشه کامل برق ECU Bosch MP 7.3
5 سال پیش
1.04 مگابایت
نوع : pdf
بازدید : 42852
منتشرکننده : CarGeek
|
معرفی فرمان برقی سوزوکی کیزاشی
5 سال پیش
1.6 مگابایت
نوع : pdf
بازدید : 3769
منتشرکننده : CarGeek
|
معرفی خودرو پژو 206 مالتی پلکس سازه پویش
5 سال پیش
0.72 مگابایت
نوع : pdf
بازدید : 7014
منتشرکننده : CarGeek
|
جزوه راهنمای تعمیرات ECU زیمنس
5 سال پیش
2.85 مگابایت
نوع : pdf
بازدید : 7033
منتشرکننده : CarGeek
|
راهنمای تعمیرات گاردان و دیفرانسیل نیسان پاترول
5 سال پیش
1.79 مگابایت
نوع : pdf
بازدید : 14894
منتشرکننده : CarGeek
|
جزوه مبانی اصلی آموزش موتور رنو
5 سال پیش
22.54 مگابایت
نوع : pdf
بازدید : 5445
منتشرکننده : CarGeek
|
راهنمای تعمیرات سیستم های الکتریکی و تزیینات خودرو جک توجوی
5 سال پیش
41.39 مگابایت
نوع : pdf
بازدید : 10430
منتشرکننده : CarGeek
|
راهنمای تعمیرات سیستم ضدسرقت (ایموبیلایزر) پراید
5 سال پیش
3.49 مگابایت
نوع : pdf
بازدید : 6749
منتشرکننده : CarGeek
|
راهنمای تعمیرات گیربکس اتوماتیک پروتون Gen-2
5 سال پیش
17.4 مگابایت
نوع : pdf
بازدید : 6971
منتشرکننده : CarGeek
|
معرفی و عیب یابی سیستم سوخت رسانی و جرقه Bosch ME 7.4.4 پژو 206
5 سال پیش
4.5 مگابایت
نوع : pdf
بازدید : 6288
منتشرکننده : CarGeek
|
راهنما و عیب یابی اجزاء سیستم سوخت رسانی انژکتوری جدید پراید
5 سال پیش
16.26 مگابایت
نوع : pdf
بازدید : 16230
منتشرکننده : CarGeek
|
معرفی سیستم جدید انژکتوری خودروی پراید (زیمنس)
5 سال پیش
35.65 مگابایت
نوع : pdf
بازدید : 10013
منتشرکننده : CarGeek
|
نقشه های الکتریکی پژو 207i
5 سال پیش
1.15 مگابایت
نوع : pdf
بازدید : 41672
منتشرکننده : CarGeek
|
کتابچه راهنمای تعمیرات لیفان X60 (گیربکس،تعلیق،فرمان و ترمز ABS)
5 سال پیش
14.13 مگابایت
نوع : pdf
بازدید : 19386
منتشرکننده : CarGeek
|
راهنمای تعمیرات و عیب یابی صندلی برقی پژو پارس ELX
5 سال پیش
10.34 مگابایت
نوع : pdf
بازدید : 25638
منتشرکننده : CarGeek
|
دستورالعمل معرفی و عیب یابی گیربکس اتوماتیک با موتور TU5 پژو پارس
5 سال پیش
1.64 مگابایت
نوع : pdf
بازدید : 10829
منتشرکننده : CarGeek
|
راهنمای تعمیرات مدارها و سیستم های الکتریکی پژو پارس ELX
5 سال پیش
10.36 مگابایت
نوع : pdf
بازدید : 25803
منتشرکننده : CarGeek
|
راهنمای تعمیرات کیسه هوای محافظ (ایربگ) و کمربند ایمنی پژو 206
5 سال پیش
2.17 مگابایت
نوع : pdf
بازدید : 11010
منتشرکننده : CarGeek
|
راهنمای تعمیرات هیوندای آوانته (الانترا نسل سوم)
5 سال پیش
58.49 مگابایت
نوع : pdf
بازدید : 20846
منتشرکننده : CarGeek
|
جزوه آموزشی نقشه خوانی برق کیا و هیوندای
5 سال پیش
0.92 مگابایت
نوع : pdf
بازدید : 53715
منتشرکننده : CarGeek
|
راهنمای نقشه های سیستم های الکتریکی جک S5
5 سال پیش
5 مگابایت
نوع : pdf
بازدید : 32813
منتشرکننده : CarGeek
|
راهنمای تعمیرات مدارهای الکتریکی پژو RD
5 سال پیش
5.25 مگابایت
نوع : pdf
بازدید : 39659
منتشرکننده : CarGeek
|
راهنمای تعمیرات موتور TU3 خودرو پژو 206
5 سال پیش
9.72 مگابایت
نوع : pdf
بازدید : 32931
منتشرکننده : CarGeek
|
معرفی رله ها و فیوزها در خودروهای مجهز به سیستم الکتریکی CEC (پژو پارس)
5 سال پیش
0.87 مگابایت
نوع : pdf
بازدید : 105849
منتشرکننده : CarGeek
|
نقشه های کامل سیم کشی و دسته سیم های لیفان X60
5 سال پیش
27.51 مگابایت
نوع : pdf
بازدید : 33909
منتشرکننده : CarGeek
|
راهنمای کامل تعمیرات تجهیزات الکترونیکی و برق مگان
5 سال پیش
3.79 مگابایت
نوع : pdf
بازدید : 10130
منتشرکننده : CarGeek
|
راهنمای تعمیرات تعلیق، سیستم فرمان و ترمز پژو 206
5 سال پیش
13.67 مگابایت
نوع : pdf
بازدید : 11093
منتشرکننده : CarGeek
|
دسته سیم ها و محل نصب قطعات تندر90 + لیست قطعات برقی- فایل 2
5 سال پیش
0.06 مگابایت
نوع : pdf
بازدید : 4023
منتشرکننده : CarGeek
|
دسته سیم ها و محل نصب قطعات تندر90 + لیست قطعات برقی
5 سال پیش
0.77 مگابایت
نوع : pdf
بازدید : 18539
منتشرکننده : CarGeek
|
جزوه آموزشی تعمیر موتور ملی EF7 ایساکو
5 سال پیش
3.02 مگابایت
نوع : pdf
بازدید : 11033
منتشرکننده : CarGeek
|
راهنمای تعمیرات خودرو سمند با موتور ملی EF7
5 سال پیش
7.45 مگابایت
نوع : pdf
بازدید : 10915
منتشرکننده : CarGeek
|
جزوه مهارت گیربکس اتوماتیک و نیمه اتوماتیک رنو
5 سال پیش
21.5 مگابایت
نوع : pdf
بازدید : 6801
منتشرکننده : CarGeek
|
راهنمای تعمیرات وانت مزدا B2000i
5 سال پیش
31.04 مگابایت
نوع : pdf
بازدید : 114068
منتشرکننده : CarGeek
|
راهنمای تعریف و کددهی انواع ریموت های دستی ایرانخودرو و سایپا بدون دستگاه
5 سال پیش
2.61 مگابایت
نوع : pdf
بازدید : 71626
منتشرکننده : CarGeek
|
راهنمای تعمیرات مدارات الکتریکی و نقشه های پارس LX با موتور TU5
5 سال پیش
17.4 مگابایت
نوع : pdf
بازدید : 32458
منتشرکننده : CarGeek
|
راهنمای تعمیرات سیستم کنترل آلایندگی هیوندای آزرا نسل چهارم
5 سال پیش
0.65 مگابایت
نوع : pdf
بازدید : 3672
منتشرکننده : CarGeek
|
راهنمای تعمیرات سیستم سوخت رسانی هیوندای آزرا نسل چهارم
5 سال پیش
9.51 مگابایت
نوع : pdf
بازدید : 9239
منتشرکننده : CarGeek
|
راهنمای اطلاعات عمومی تعمیرات هیوندای آزرا نسل چهارم
5 سال پیش
0.68 مگابایت
نوع : pdf
بازدید : 12825
منتشرکننده : CarGeek
|
راهنمای تعمیرات سیستم الکتریکی موتور Lambda MPi G6DB3.3,G6DA3.8 هیوندای و کیا (آزرا/سانتافه/سوناتا/سورنتو/اپیروس...)
5 سال پیش
1.74 مگابایت
نوع : pdf
بازدید : 8971
منتشرکننده : CarGeek
|
راهنمای تعمیرات موتور Lambda MPi G6DB3.3,G6DA3.8 هیوندای و کیا (آزرا/سانتافه/سوناتا/سورنتو/اپیروس...)
5 سال پیش
11.14 مگابایت
نوع : pdf
بازدید : 18467
منتشرکننده : CarGeek
|
راهنمای سیستم کنترل موتور نیسان ماکسیما- فایل 2
5 سال پیش
3.42 مگابایت
نوع : pdf
بازدید : 6628
منتشرکننده : CarGeek
|
راهنمای سیستم کنترل موتور نیسان ماکسیما
5 سال پیش
5.63 مگابایت
نوع : pdf
بازدید : 11954
منتشرکننده : CarGeek
|
راهنمای تعمیرات گیربکس معمولی ماکسیما
5 سال پیش
1.75 مگابایت
نوع : pdf
بازدید : 6027
منتشرکننده : CarGeek
|
راهنمای تعمیرات سیستم کنترل گاز،سوخت و اگزوز ماکسیما
5 سال پیش
0.34 مگابایت
نوع : pdf
بازدید : 7154
منتشرکننده : CarGeek
|
راهنمای تعمیرات ترمز نیسان ماکسیما
5 سال پیش
1.83 مگابایت
نوع : pdf
بازدید : 6560
منتشرکننده : CarGeek
|
راهنمای تعمیرات اکسل جلو و عقب نیسان ماکسیما
5 سال پیش
0.71 مگابایت
نوع : pdf
بازدید : 5262
منتشرکننده : CarGeek
|
راهنمای تعمیرات سیستم فرمان نیسان ماکسیما
5 سال پیش
0.86 مگابایت
نوع : pdf
بازدید : 8537
منتشرکننده : CarGeek
|
راهنمای تعمیرات و سرویس موتورسیکلت CG125 و CG110
5 سال پیش
0.96 مگابایت
نوع : pdf
بازدید : 31619
منتشرکننده : CarGeek
|
راهنمای گشتاور پیچ های خودرو رانا
5 سال پیش
9.51 مگابایت
نوع : pdf
بازدید : 18493
منتشرکننده : CarGeek
|
راهنمای عیب یابی و رفع عیب گاردان پژو روآ OHV و وانت 1600
5 سال پیش
0.34 مگابایت
نوع : pdf
بازدید : 7999
منتشرکننده : CarGeek
|
راهنمای تعمیرات بدنه وانت پیکان
5 سال پیش
8.68 مگابایت
نوع : pdf
بازدید : 18666
منتشرکننده : CarGeek
|
راهنمای تعمیرات سیستم سوخت رسانی و جرقه پژو RD و پیکان (SAGEM SL96 , S2000 و Siemens)
5 سال پیش
4.15 مگابایت
نوع : pdf
بازدید : 110269
منتشرکننده : CarGeek
|
راهنمای تعمیرات موتور پایه گازسوز OHVG2 پژو روآ و وانت پیکان یورو4
5 سال پیش
8.52 مگابایت
نوع : pdf
بازدید : 11310
منتشرکننده : CarGeek
|
راهنمای تعمیرات و عیب یابی سیستم ABS MANDO پژو405 ، پارس و سمند
5 سال پیش
5.06 مگابایت
نوع : pdf
بازدید : 23216
منتشرکننده : CarGeek
|
راهنمای تزئینات (داشبورد ،صندلی،پنجره ها و ...) پیکان و وانت پیکان
5 سال پیش
1.54 مگابایت
نوع : pdf
بازدید : 18302
منتشرکننده : CarGeek
|
راهنمای تعمیرات سیستم کنترل آلایندگی (کاتالیست/سنسور اکسیژن/کنیستر) خودروهای پژو405 ،پارس ،سمند- فایل 2
5 سال پیش
29.2 مگابایت
نوع : pdf
بازدید : 4562
منتشرکننده : CarGeek
|
راهنمای تعمیرات سیستم کنترل آلایندگی (کاتالیست/سنسور اکسیژن/کنیستر) خودروهای پژو405 ،پارس ،سمند
5 سال پیش
4.21 مگابایت
نوع : pdf
بازدید : 10561
منتشرکننده : CarGeek
|
راهنمای تعمیرات و باز و بست قطعات گازسوز پژو RD، روآ و وانت پیکان
5 سال پیش
3.72 مگابایت
نوع : pdf
بازدید : 21720
منتشرکننده : CarGeek
|
راهنمای تعمیرات سیستم الکتریکی موتور ریو
5 سال پیش
2.06 مگابایت
نوع : pdf
بازدید : 5288
منتشرکننده : CarGeek
|
راهنمای مکانیزم ها و تجهیزات ، آب بندی و صداگیری و پوشش داخلی و تودوزی تندر90
5 سال پیش
5.25 مگابایت
نوع : pdf
بازدید : 5266
منتشرکننده : CarGeek
|
راهنمای تعمیرات تجهیزات الکتریکی وانت پیکان
5 سال پیش
2.5 مگابایت
نوع : pdf
بازدید : 61891
منتشرکننده : CarGeek
|
راهنمای کامل تعمیر مدارات الکتریکی سورن
5 سال پیش
21.76 مگابایت
نوع : pdf
بازدید : 3867
منتشرکننده : CarGeek
|
راهنمای تعمیرات JAC J5 (جک جی5)
5 سال پیش
14.04 مگابایت
نوع : pdf
بازدید : 62166
منتشرکننده : CarGeek
|
راهنمای سیستم سوخت رسانی انژکتوری زانتیا (MP 5.2 و MP 7.3)
5 سال پیش
10.94 مگابایت
نوع : pdf
بازدید : 13299
منتشرکننده : CarGeek
|
نقشه های الکتریکی خودرو رانا ECO MUX
5 سال پیش
3.06 مگابایت
نوع : pdf
بازدید : 25814
منتشرکننده : CarGeek
|
راهنمای تعمیرات و عیب یابی سیستم تهویه اتوماتیک سورن ELX
5 سال پیش
1.57 مگابایت
نوع : pdf
بازدید : 36308
منتشرکننده : CarGeek
|
اصول کمک های اولیه و احیاء
5 سال پیش
8.53 مگابایت
نوع : pdf
بازدید : 4165
منتشرکننده : CarGeek
|
راهنمای تعمیرات سیستم تعلیق ریو
5 سال پیش
8.89 مگابایت
نوع : pdf
بازدید : 7248
منتشرکننده : CarGeek
|
راهنمای تعمیرات و سرویس ترمز ABS پژو 405 ، پارس و سمند
5 سال پیش
5.08 مگابایت
نوع : pdf
بازدید : 48596
منتشرکننده : CarGeek
|
راهنمای تعمیرات مجموعه موتور تیبا
5 سال پیش
8.53 مگابایت
نوع : pdf
بازدید : 29430
منتشرکننده : CarGeek
|
راهنمای تعمیرات سیستم سوخت رسانی نیسان پاترول
5 سال پیش
0.87 مگابایت
نوع : pdf
بازدید : 26739
منتشرکننده : CarGeek
|
راهنمای تعمیرات سیستم برق نیسان پاترول
5 سال پیش
2.54 مگابایت
نوع : pdf
بازدید : 35095
منتشرکننده : CarGeek
|
کتابچه همراه تعمیرکاران سایپا تیبا
5 سال پیش
7.41 مگابایت
نوع : pdf
بازدید : 11132
منتشرکننده : CarGeek
|
راهنمای کامل تعمیرات موسو (SsangYong Musso)
5 سال پیش
24.32 مگابایت
نوع : pdf
بازدید : 26219
منتشرکننده : CarGeek
|
آموزش تصویری نصب و راه اندازی کروزکنترل پژو 206
5 سال پیش
0.65 مگابایت
نوع : pdf
بازدید : 24001
منتشرکننده : CarGeek
|
جزوه دوره آموزشی سیستم موبایل هندزفری مخصوص خودروهای سفارشی ایرانخودرو
5 سال پیش
1.16 مگابایت
نوع : pdf
بازدید : 5295
منتشرکننده : CarGeek
|
کتاب آشنایی با تعمیر و نگه داری خودرو برای مبتدیان (The Crawford�s Auto Repair Guide to Beginner�s Auto Maintenance & Repair)
5 سال پیش
4.6 مگابایت
نوع : pdf
بازدید : 3977
منتشرکننده : CarGeek
|
راهنمای رنو برای عیب یابی صدای خودرو
5 سال پیش
5.01 مگابایت
نوع : pdf
بازدید : 4164
منتشرکننده : CarGeek
|
معرفی موتور EW10A پژو 407
5 سال پیش
4.89 مگابایت
نوع : pdf
بازدید : 8722
منتشرکننده : CarGeek
|
مشخصات (دیتاشیت) موتور EW10A پژو 407
5 سال پیش
1.6 مگابایت
نوع : pdf
بازدید : 4030
منتشرکننده : CarGeek
|
عیب یابی راهنما و فلاشر پژو 206 و 207i
5 سال پیش
0.61 مگابایت
نوع : pdf
بازدید : 49830
منتشرکننده : CarGeek
|
راهنمای کامل BSI پژو 206
5 سال پیش
6.67 مگابایت
نوع : pdf
بازدید : 56233
منتشرکننده : CarGeek
|
آشنایی با سیستم انژکتوری و سنسورها و عملگرهای آن
5 سال پیش
0.85 مگابایت
نوع : pdf
بازدید : 7490
منتشرکننده : CarGeek
|
مراحل تشخیص صحت عملکرد BSI در کامپیوتر سفری پژو 206
5 سال پیش
0.52 مگابایت
نوع : pdf
بازدید : 5283
منتشرکننده : CarGeek
|
آشنایی با سنسور سرعت خودرو
5 سال پیش
0.93 مگابایت
نوع : pdf
بازدید : 6063
منتشرکننده : CarGeek
|
راهنمای تعمیرات و سرویس بدنه و تزئینات تیبا
5 سال پیش
22.1 مگابایت
نوع : pdf
بازدید : 13792
منتشرکننده : CarGeek
|
آشنایی با سنسور دور موتور
5 سال پیش
0.9 مگابایت
نوع : pdf
بازدید : 5089
منتشرکننده : CarGeek
|
روش عیب یابی سنسور اکسیژن پژو 206 و 207i
5 سال پیش
0.27 مگابایت
نوع : pdf
بازدید : 16788
منتشرکننده : CarGeek
|
نحوه بررسی و عیب یابی کویل پژو 206و 207i
5 سال پیش
0.33 مگابایت
نوع : pdf
بازدید : 44739
منتشرکننده : CarGeek
|
راهنمای تعمیرات و سرویس سیستم سوخت رسانی سایپا تیبا
5 سال پیش
11.28 مگابایت
نوع : pdf
بازدید : 7297
منتشرکننده : CarGeek
|
راهنمای سیستم سوخت رسانی تیبا یورو4 (مگاموتور)
5 سال پیش
1.63 مگابایت
نوع : pdf
بازدید : 14755
منتشرکننده : CarGeek
|
راهنمای تعمیرات و سرویس مجموعه موتور BM15L خودروهای گروه H200وH300 سایپا
5 سال پیش
6.56 مگابایت
نوع : pdf
بازدید : 7924
منتشرکننده : CarGeek
|
کتاب Automotive Microelectronics شرکت Bosch
5 سال پیش
1.55 مگابایت
نوع : pdf
بازدید : 3506
منتشرکننده : CarGeek
|
راهنمای تشخیص صحت عملکرد BSI در عیب یابی آمپر پژو 206 و 207i
5 سال پیش
0.61 مگابایت
نوع : pdf
بازدید : 12640
منتشرکننده : CarGeek
|
راهنمای عیب یابی سیستم انتقال قدرت اتوماتیک رنو مگان
5 سال پیش
1.98 مگابایت
نوع : pdf
بازدید : 6631
منتشرکننده : CarGeek
|
شرح دیود و آلترناتور در سیستم های الکتریکی خودرو
5 سال پیش
3.21 مگابایت
نوع : pdf
بازدید : 3996
منتشرکننده : CarGeek
|
اطلاعیه فنی بالا نرفتن دور موتور در خودروهای MG
5 سال پیش
0.74 مگابایت
نوع : pdf
بازدید : 6663
منتشرکننده : CarGeek
|
آشنایی با مونتاژ،عیب یابی و رفع عیب سیستم سوخت رسانی سوزوکی گرندویتارا
5 سال پیش
0.55 مگابایت
نوع : pdf
بازدید : 4382
منتشرکننده : CarGeek
|
عیب یابی لرزش های خودرو
5 سال پیش
0.71 مگابایت
نوع : pdf
بازدید : 5625
منتشرکننده : CarGeek
|
نقشه BCM رانا ECO MUX
5 سال پیش
1.57 مگابایت
نوع : pdf
بازدید : 13285
منتشرکننده : CarGeek
|
اطلاعات عمومی تعمیرات و راهنمای تعمیر موتور مزدا2
5 سال پیش
13.19 مگابایت
نوع : pdf
بازدید : 5525
منتشرکننده : CarGeek
|
اطلاعیه رسمی روش ریست نمودن BSI پژو 206 و 207
5 سال پیش
0.25 مگابایت
نوع : pdf
بازدید : 37761
منتشرکننده : CarGeek
|
معرفی و راهنمای موتورهای پژو206 (TU3وTU5)
5 سال پیش
5.1 مگابایت
نوع : pdf
بازدید : 7146
منتشرکننده : CarGeek
|
راهنمای نقشه های شماتیک الکتریکی سورن ELX
5 سال پیش
0.97 مگابایت
نوع : pdf
بازدید : 15504
منتشرکننده : CarGeek
|
راهنمای تعمیرات و سرویس سیستم انتقال قدرت تیبا (کلاچ،گیربکس،پلوس)
5 سال پیش
21.55 مگابایت
نوع : pdf
بازدید : 11185
منتشرکننده : CarGeek
|
راهنمای تعمیرات مدارهای الکتریکی تندر90
5 سال پیش
2.53 مگابایت
نوع : pdf
بازدید : 13953
منتشرکننده : CarGeek
|
جزوه آموزشی سیستم دوگانه سوز CNG
5 سال پیش
17.83 مگابایت
نوع : pdf
بازدید : 20648
منتشرکننده : CarGeek
|
راهنمای تعمیرات لیفان X60 (سیستم های الکتریکی،بدنه،تزئینات)
5 سال پیش
9.51 مگابایت
نوع : pdf
بازدید : 60334
منتشرکننده : CarGeek
|
معرفی و آشنایی گیربکس اتوماتیک(مزدا یدک)
5 سال پیش
2.35 مگابایت
نوع : pdf
بازدید : 4446
منتشرکننده : CarGeek
|
راهنمای نقشه های الکتریکی پژو 206 فاز1 (ECO MUX)
5 سال پیش
6.31 مگابایت
نوع : pdf
بازدید : 30392
منتشرکننده : CarGeek
|
راهنمای نقشه های الکتریکی پژو 206 فاز0 (206جدید ایرانی)
5 سال پیش
4.82 مگابایت
نوع : pdf
بازدید : 13412
منتشرکننده : CarGeek
|
راهنمای تعمیرات تزئینات داخلی سمند
5 سال پیش
6.94 مگابایت
نوع : pdf
بازدید : 35259
منتشرکننده : CarGeek
|
راهنمای تعمیرات نیسان مورانو
5 سال پیش
15.18 مگابایت
نوع : pdf
بازدید : 15751
منتشرکننده : CarGeek
|
عیب یابی موتور از طریق رنگ دود اگزوز
5 سال پیش
0.64 مگابایت
نوع : pdf
بازدید : 6369
منتشرکننده : CarGeek
|
راهنمای آموزش تخصصی سیستم ضدسرقت رنو (تندر90،مگان،...)
5 سال پیش
10.26 مگابایت
نوع : pdf
بازدید : 4545
منتشرکننده : CarGeek
|
معرفی و نقشه ایموبیلایزر جدید CIM پژو 405،پارس و سمند
5 سال پیش
0.43 مگابایت
نوع : pdf
بازدید : 7608
منتشرکننده : CarGeek
|
راهنمای تعمیرات موتور و EMS سوزوکی گرندویتارا 2400
5 سال پیش
20.12 مگابایت
نوع : pdf
بازدید : 9998
منتشرکننده : CarGeek
|
راهنمای تعمیرات سیستم روغنکاری و خنک کننده موتور جیپ صحرا
5 سال پیش
1.47 مگابایت
نوع : pdf
بازدید : 12312
منتشرکننده : CarGeek
|
آشنایی با علائم الکتریکی و طریقه نقشه خوانی در برق خودرو
5 سال پیش
3.15 مگابایت
نوع : pdf
بازدید : 9645
منتشرکننده : CarGeek
|
معرفی سیستم ایموبیلایزر Continental
5 سال پیش
2.47 مگابایت
نوع : pdf
بازدید : 4558
منتشرکننده : CarGeek
|
دستورالعمل معرفی و عیب یابی تعریف کلید ایموبیلایزر CIM کلیه خودروها
5 سال پیش
0.66 مگابایت
نوع : pdf
بازدید : 7391
منتشرکننده : CarGeek
|
راهنمای تعمیرات ECU (موتورآزما ثمین)
5 سال پیش
2.95 مگابایت
نوع : pdf
بازدید : 13224
منتشرکننده : CarGeek
|
راهنمای تعمیرات اکسل جلو و عقب جیپ صحرا- فایل 2
5 سال پیش
2.7 مگابایت
نوع : pdf
بازدید : 5243
منتشرکننده : CarGeek
|
راهنمای تعمیرات اکسل جلو و عقب جیپ صحرا
5 سال پیش
1.88 مگابایت
نوع : pdf
بازدید : 5912
منتشرکننده : CarGeek
|
دلایل شاتون زدن یا شکسته شدن شاتون
5 سال پیش
3.44 مگابایت
نوع : pdf
بازدید : 10402
منتشرکننده : CarGeek
|
نقشه های سیم کشی های الکتریکی مزدا 323- فایل 2
5 سال پیش
5.95 مگابایت
نوع : pdf
بازدید : 7368
منتشرکننده : CarGeek
|
نقشه های سیم کشی های الکتریکی مزدا 323
5 سال پیش
7.14 مگابایت
نوع : pdf
بازدید : 22097
منتشرکننده : CarGeek
|
راهنمای تعمیرات سیستم هوشمند CEC پژو پارس
5 سال پیش
2.25 مگابایت
نوع : pdf
بازدید : 20898
منتشرکننده : CarGeek
|
راهنمای آموزش موتور و گیربکس تندر90
5 سال پیش
2.63 مگابایت
نوع : pdf
بازدید : 7097
منتشرکننده : CarGeek
|
راهنمای تعمیرات و سرویس تجهیزات الکتریکی زانتیا
5 سال پیش
5.05 مگابایت
نوع : pdf
بازدید : 10358
منتشرکننده : CarGeek
|
آشنایی با موتور خودرو سوزوکی (گرندویتارا-J20)
5 سال پیش
1.73 مگابایت
نوع : pdf
بازدید : 4152
منتشرکننده : CarGeek
|
راهنمای تعمیرات سیستم فرمان نیسان پیکاپ
5 سال پیش
1.68 مگابایت
نوع : pdf
بازدید : 7194
منتشرکننده : CarGeek
|
انژکتور دیزلی
5 سال پیش
1.95 مگابایت
نوع : pdf
بازدید : 8064
منتشرکننده : CarGeek
|
راهنمای فنی رسمی سیتروئن برای گیربکس اتوماتیک AL4
5 سال پیش
1.45 مگابایت
نوع : pdf
بازدید : 6809
منتشرکننده : CarGeek
|
راهنمای تعمیرات اکسل و سیستم تعلیق جلو و عقب نیسان پیکاپ- فایل 2
5 سال پیش
0.67 مگابایت
نوع : pdf
بازدید : 4144
منتشرکننده : CarGeek
|
راهنمای تعمیرات اکسل و سیستم تعلیق جلو و عقب نیسان پیکاپ
5 سال پیش
1.93 مگابایت
نوع : pdf
بازدید : 7731
منتشرکننده : CarGeek
|
راهنمای تعمیرات کلاچ و گیربکس پراید
5 سال پیش
5.89 مگابایت
نوع : pdf
بازدید : 22427
منتشرکننده : CarGeek
|
راهنمای تعمیرات جعبه دنده معمولی تندر90
5 سال پیش
4.72 مگابایت
نوع : pdf
بازدید : 13794
منتشرکننده : CarGeek
|
اصول رانندگی حرفه ای و نگهداری از خودرو به زبان ساده
5 سال پیش
6.57 مگابایت
نوع : pdf
بازدید : 3809
منتشرکننده : CarGeek
|
راهنمای تعمیرات ، معرفی و جانمایی دسته سیم ها و نقشه های الکتریکی خودرو هایما S7
5 سال پیش
18.79 مگابایت
نوع : pdf
بازدید : 5366
منتشرکننده : CarGeek
|
جزوه آموزشی سیستم های الکتریکی خودرو هایما S7
5 سال پیش
4.39 مگابایت
نوع : pdf
بازدید : 7766
منتشرکننده : CarGeek
|
جزوه آموزشی گیربکس اتوماتیک خودروی هایما S7
5 سال پیش
2.17 مگابایت
نوع : pdf
بازدید : 11658
منتشرکننده : CarGeek
|
راهنمای تعمیرات اجزاء سامانه مدیریت موتور ملی (جزوه سیستم انژکتورEF7)
5 سال پیش
2.19 مگابایت
نوع : pdf
بازدید : 6369
منتشرکننده : CarGeek
|
راهنمای آموزشی موتور XUM پژو پارس
5 سال پیش
6.82 مگابایت
نوع : pdf
بازدید : 14946
منتشرکننده : CarGeek
|
راهنمای تعمیرات ملحقات و تزئینات خانواده پژو 206
5 سال پیش
4.19 مگابایت
نوع : pdf
بازدید : 9016
منتشرکننده : CarGeek
|
راهنمای تعمیرات و عیب یابی سیستم ضدقفل ترمز ABS رانا
5 سال پیش
5.64 مگابایت
نوع : pdf
بازدید : 8537
منتشرکننده : CarGeek
|
راهنمای تعمیرات تزئینات پژو 405 و پارس (ملحقات داشبورد ، رادیو و رودری)
5 سال پیش
1.24 مگابایت
نوع : pdf
بازدید : 57359
منتشرکننده : CarGeek
|
راهنمای تعمیرات و عیب یابی ایربگ راننده پژو405، پارس، سمند
5 سال پیش
8.41 مگابایت
نوع : pdf
بازدید : 6929
منتشرکننده : CarGeek
|
راهنمای پیکربندی نودهای مالتی پلکس در خودرو رانا
5 سال پیش
1.9 مگابایت
نوع : pdf
بازدید : 10251
منتشرکننده : CarGeek
|
راهنمای تعمیرات سیستم ترمز سوزوکی گرند ویتارا
5 سال پیش
4.66 مگابایت
نوع : pdf
بازدید : 7723
منتشرکننده : CarGeek
|
راهنمای تعمیرات دنده کمک نیسان پیکاپ
5 سال پیش
1.89 مگابایت
نوع : pdf
بازدید : 10638
منتشرکننده : CarGeek
|
راهنمای تعمیرات گیربکس دستی نیسان پیکاپ
5 سال پیش
1.56 مگابایت
نوع : pdf
بازدید : 8865
منتشرکننده : CarGeek
|
راهنمای تعمیرات بخاری جیپ صحرا
5 سال پیش
1.48 مگابایت
نوع : pdf
بازدید : 5705
منتشرکننده : CarGeek
|
راهنمای تعمیرات سیستم های کنترل الکتریکی سوزوکی گرندویتارا
5 سال پیش
3.11 مگابایت
نوع : pdf
بازدید : 11608
منتشرکننده : CarGeek
|
راهنمای تعمیرات بدنه ، اتاق و تجهیزات سوزوکی گرندویتارا
5 سال پیش
25.42 مگابایت
نوع : pdf
بازدید : 6013
منتشرکننده : CarGeek
|
دفترچه عیب یابی وانت انژکتوری دوگانه سوز زامیاد با کیت گازسوز غرب استیل
5 سال پیش
0.2 مگابایت
نوع : pdf
بازدید : 49461
منتشرکننده : CarGeek
|
کاربرد زبان انگلیسی در عیب یابی خودرو
5 سال پیش
1.34 مگابایت
نوع : pdf
بازدید : 10653
منتشرکننده : CarGeek
|
راهنمای تعمیرات و عیب یابی کمک فنر کلیه خودروها
5 سال پیش
1.06 مگابایت
نوع : pdf
بازدید : 7110
منتشرکننده : CarGeek
|
دستورالعمل تعویض قطعات جعبه فرمان پراید
5 سال پیش
0.45 مگابایت
نوع : pdf
بازدید : 13181
منتشرکننده : CarGeek
|
راهنمای تعمیرات شاسی و بدنه جیپ صحرا
5 سال پیش
2.7 مگابایت
نوع : pdf
بازدید : 10257
منتشرکننده : CarGeek
|
راهنمای پیکربندی نودهای سیستم مالتی پلکس سمند و سورن
5 سال پیش
1.09 مگابایت
نوع : pdf
بازدید : 15406
منتشرکننده : CarGeek
|
راهنمای تعمیرات و سرویس موتور XU7JPL3 پژو پارس ، 405 و سمند
5 سال پیش
13 مگابایت
نوع : pdf
بازدید : 7236
منتشرکننده : CarGeek
|
راهنمای آشنایی با سیستم های دوگانه سوز پژو Roa و RD و وانت باردو
5 سال پیش
2.63 مگابایت
نوع : pdf
بازدید : 13179
منتشرکننده : CarGeek
|
راهنمای نگه داری ، عیب یابی ، شارژ و گارانتی باتری کلیه خودروها
5 سال پیش
0.76 مگابایت
نوع : pdf
بازدید : 4108
منتشرکننده : CarGeek
|
راهنمای تعمیرات و سرویس سیستم فرمان ریو
5 سال پیش
9.09 مگابایت
نوع : pdf
بازدید : 11575
منتشرکننده : CarGeek
|
راهنمای دیاگرام های الکتریکی سیتروئن C5
5 سال پیش
9.64 مگابایت
نوع : pdf
بازدید : 4413
منتشرکننده : CarGeek
|
راهنمای سیستم مالتی پلکس سیتروئن C5
5 سال پیش
12.68 مگابایت
نوع : pdf
بازدید : 5006
منتشرکننده : CarGeek
|
راهنمای کامل تجهیزات الکتریکی و برق سیتروئن C5- فایل 2
5 سال پیش
2.24 مگابایت
نوع : pdf
بازدید : 6316
منتشرکننده : CarGeek
|
راهنمای کامل تجهیزات الکتریکی و برق سیتروئن C5
5 سال پیش
15.9 مگابایت
نوع : pdf
بازدید : 10327
منتشرکننده : CarGeek
|
راهنمای تعمیرات سیستم های الکتریکی نیسان پیکاپ
5 سال پیش
8.54 مگابایت
نوع : pdf
بازدید : 33467
منتشرکننده : CarGeek
|
راهنمای تعمیرات و سرویس سیستم سوخت رسانی و جرقه ساژم S2000
5 سال پیش
20.01 مگابایت
نوع : pdf
بازدید : 9219
منتشرکننده : CarGeek
|
راهنمای تعمیرات و سرویس سیستم سوخت رسانی و جرقه SL96 پژو RD
5 سال پیش
2.1 مگابایت
نوع : pdf
بازدید : 8784
منتشرکننده : CarGeek
|
راهنمای تعمیرات سیستم برق جیپ صحرا
5 سال پیش
2.42 مگابایت
نوع : pdf
بازدید : 13947
منتشرکننده : CarGeek
|
راهنمای تعمیرات موتور جیپ صحرا (موتور میتسوبیشی 4G64)
5 سال پیش
3.24 مگابایت
نوع : pdf
بازدید : 21731
منتشرکننده : CarGeek
|
راهنمای تعمیرات سیستم سوخت رسانی و جرقه ساژم SL96 و S2000 (پیکان و پژو RD)
5 سال پیش
1.82 مگابایت
نوع : pdf
بازدید : 34964
منتشرکننده : CarGeek
|
راهنمای تعمیرات تجهیزات الکتریکی تندر90
5 سال پیش
10.13 مگابایت
نوع : pdf
بازدید : 9508
منتشرکننده : CarGeek
|
راهنمای تعمیرات موتور و متعلقات موتور تندر90
5 سال پیش
2.84 مگابایت
نوع : pdf
بازدید : 44413
منتشرکننده : CarGeek
|
معرفی و عیب یابی سیستم سوخت رسانی و جرقه Bosch MP 7.3 پژوپارس ELX و سمند سریر
5 سال پیش
5.21 مگابایت
نوع : pdf
بازدید : 9737
منتشرکننده : CarGeek
|
دستورالعمل هواگیری سیستم ترمز خودروهای پژو 405 ، پژو پارس وسمند
5 سال پیش
0.96 مگابایت
نوع : pdf
بازدید : 37459
منتشرکننده : CarGeek
|
راهنمای تعمیرات بدنه و تزئینات نیسان پیکاپ
5 سال پیش
2.34 مگابایت
نوع : pdf
بازدید : 7633
منتشرکننده : CarGeek
|
راهنمای تعمیرات سیستم فرمان خودروهای پژو 405 ، پژو پارس و سمند
5 سال پیش
4.95 مگابایت
نوع : pdf
بازدید : 44110
منتشرکننده : CarGeek
|
دستورالعمل شناسایی قطعات گارانتی در شبکه خدمات پس از فروش سایپا
5 سال پیش
1.85 مگابایت
نوع : pdf
بازدید : 11556
منتشرکننده : CarGeek
|
راهنمای تعمیرات سیستم خنک کاری و اگزوز موتور TU5 (پژو405SLX،پژو پارس LX و سمند)
5 سال پیش
2.71 مگابایت
نوع : pdf
بازدید : 7372
منتشرکننده : CarGeek
|
راهنمای تعمیرات سیستم های الکتریکی نیسان ماکسیما- فایل 2
5 سال پیش
4.41 مگابایت
نوع : pdf
بازدید : 5894
منتشرکننده : CarGeek
|
راهنمای تعمیرات سیستم های الکتریکی نیسان ماکسیما
5 سال پیش
4.3 مگابایت
نوع : pdf
بازدید : 31478
منتشرکننده : CarGeek
|
راهنمای تعمیرات سیستم کلاچ نیسان ماکسیما
5 سال پیش
0.6 مگابایت
نوع : pdf
بازدید : 8906
منتشرکننده : CarGeek
|
راهنمای تعمیرات موتور نیسان ماکسیما
5 سال پیش
4.07 مگابایت
نوع : pdf
بازدید : 19914
منتشرکننده : CarGeek
|
راهنمای تعمیرات سیستم هشداردهنده دنده عقب پژو پارس و سمند
5 سال پیش
0.6 مگابایت
نوع : pdf
بازدید : 66079
منتشرکننده : CarGeek
|
راهنمای تعمیرات سیستم ترمز ABS وانت زامیاد
5 سال پیش
2.35 مگابایت
نوع : pdf
بازدید : 16083
منتشرکننده : CarGeek
|
لیست مدل های مختلف ECU روی مدل های مختلف برندهای مختلف خودرو
5 سال پیش
2.63 مگابایت
نوع : pdf
بازدید : 26001
منتشرکننده : CarGeek
|
دستورالعمل تعمیرات و نگه داری کیت های دوگانه سوز LOVATO وانت زامیاد
5 سال پیش
2.4 مگابایت
نوع : pdf
بازدید : 9656
منتشرکننده : CarGeek
|
راهنمای تعمیرات خودرو پژو 207i
5 سال پیش
9.32 مگابایت
نوع : pdf
بازدید : 15694
منتشرکننده : CarGeek
|
مشخصات روانکارهای خودروهای تحت پوشش سایپا
5 سال پیش
0.68 مگابایت
نوع : pdf
بازدید : 5300
منتشرکننده : CarGeek
|
راهنمای تعمیرات گیربکس جدید پژو روآ
5 سال پیش
4.17 مگابایت
نوع : pdf
بازدید : 28760
منتشرکننده : CarGeek
|
راهنمای مدارات الکتریکی سیستم چراغ های جلو و عقب سایپا پراید
5 سال پیش
2.49 مگابایت
نوع : pdf
بازدید : 56765
منتشرکننده : CarGeek
|
راهنمای تعمیرات موتور دوگانه سوز OHVG پژو روآ و وانت پیکان
5 سال پیش
2.06 مگابایت
نوع : pdf
بازدید : 34514
منتشرکننده : CarGeek
|
معرفی پژو206 جدید ایرانی و تفاوت های آن با 206قدیمی از ایساکو
5 سال پیش
1.9 مگابایت
نوع : pdf
بازدید : 5184
منتشرکننده : CarGeek
|
راهنمای تعمیرات و سرویس تجهیزات الکتریکی پژو RD- فایل 2
5 سال پیش
8.3 مگابایت
نوع : pdf
بازدید : 5875
منتشرکننده : CarGeek
|
راهنمای تعمیرات و سرویس تجهیزات الکتریکی پژو RD
5 سال پیش
13.49 مگابایت
نوع : pdf
بازدید : 24914
منتشرکننده : CarGeek
|
راهنمای تعمیرات و سرویس کلیدهای کنترل روی فرمان و آپشن های رنو مگان
5 سال پیش
2.58 مگابایت
نوع : pdf
بازدید : 7187
منتشرکننده : CarGeek
|
راهنمای تعمیرات و عیب یابی اجزاء سیستم سوخت رسانی انژکتوری زیمنس بهبود یافته پراید
5 سال پیش
2.52 مگابایت
نوع : pdf
بازدید : 8054
منتشرکننده : CarGeek
|
معرفی و عیب یابی سیستم تهویه مطبوع (بخاری و کولر) کلیه خودروها
5 سال پیش
6.96 مگابایت
نوع : pdf
بازدید : 11975
منتشرکننده : CarGeek
|
راهنمای تعمیرات قطعات الکتریکی سمند
5 سال پیش
3.37 مگابایت
نوع : pdf
بازدید : 7644
منتشرکننده : CarGeek
|
راهنمای تعمیرات و سرویس کیسه هوا (ایربگ) سایپا تیبا
5 سال پیش
2.06 مگابایت
نوع : pdf
بازدید : 14754
منتشرکننده : CarGeek
|
راهنمای تعمیرات خودروهای دوگانه سوز CNG
5 سال پیش
11.4 مگابایت
نوع : pdf
بازدید : 11660
منتشرکننده : CarGeek
|
راهنمای تعمیرات سیستم انتقال قدرت ، گیربکس BE3/کلاچ /دیفرانسیل /پلوس ها پژو 405 ، پارس ، سمند
5 سال پیش
18.43 مگابایت
نوع : pdf
بازدید : 9088
منتشرکننده : CarGeek
|
راهنمای تعمیرات موتور ملی EF7 ایساکو
5 سال پیش
14.41 مگابایت
نوع : pdf
بازدید : 20607
منتشرکننده : CarGeek
|
راهنمای تعمیرات الکتریکال سیستم ECO-MUX سمند و سورن
5 سال پیش
2.66 مگابایت
نوع : pdf
بازدید : 9968
منتشرکننده : CarGeek
|
معرفی و عیب یابی انواع کیتهای خودروهای دوگانه سوز سمند (LX،EL و معمولی)
5 سال پیش
6.7 مگابایت
نوع : pdf
بازدید : 7777
منتشرکننده : CarGeek
|
مکانیزم عملکرد قطعات الکترونیکی MVM110 سه و چهار سیلندر
5 سال پیش
0.41 مگابایت
نوع : pdf
بازدید : 8597
منتشرکننده : CarGeek
|
راهنمای تعمیرات سیستم تعلیق، ترمز و فرمان خودرو رانا
5 سال پیش
14.65 مگابایت
نوع : pdf
بازدید : 7168
منتشرکننده : CarGeek
|
مرجع کامل تعمیرات موتور سوزوکی گرند ویتارا (Suzuki J20)
5 سال پیش
19.63 مگابایت
نوع : pdf
بازدید : 33621
منتشرکننده : CarGeek
|
معرفی و دستورالعمل عیب یابی سیستم مالتی پلکس سمند
5 سال پیش
4.19 مگابایت
نوع : pdf
بازدید : 16563
منتشرکننده : CarGeek
|
راهنمای تعمیرات و سرویس سیستم سوخت رسانی کیا ریو
5 سال پیش
13.52 مگابایت
نوع : pdf
بازدید : 14210
منتشرکننده : CarGeek
|
راهنمای موتور SQR 372 خودرو MVM110
5 سال پیش
0.55 مگابایت
نوع : pdf
بازدید : 13154
منتشرکننده : CarGeek
|
اطلاعیه روش شستشوی دریچه گاز هیوندای سوناتا،سانتافه،توسان (موتور THETA)
5 سال پیش
0.23 مگابایت
نوع : pdf
بازدید : 10524
منتشرکننده : CarGeek
|
راهنمای کامل آموزشی کارگاه برق پژو 206 ایساکو
5 سال پیش
4.55 مگابایت
نوع : pdf
بازدید : 7534
منتشرکننده : CarGeek
|
راهنمای تعمیرات و عیب یابی سیستم سوخت رسانی MVM110 چهارسیلندر
5 سال پیش
5.2 مگابایت
نوع : pdf
بازدید : 12310
منتشرکننده : CarGeek
|
دیزل از بدو تولید تا فناوری های نوین
5 سال پیش
0.99 مگابایت
نوع : pdf
بازدید : 4792
منتشرکننده : CarGeek
|
اصول عملکرد سیستم پاشش سوخت و جرقه زنی با استاندارد EURO 4 (جزوه انژکتور یورو4 پژو407)
5 سال پیش
1.26 مگابایت
نوع : pdf
بازدید : 9568
منتشرکننده : CarGeek
|
راهنمای امدادخودرو در مورد پژو 407
5 سال پیش
1.65 مگابایت
نوع : pdf
بازدید : 12291
منتشرکننده : CarGeek
|
راهنمای تعمیرات و عیب یابی سیستم تهویه مطبوع اتوماتیک دنا (کولر و بخاری)
5 سال پیش
1.99 مگابایت
نوع : pdf
بازدید : 40005
منتشرکننده : CarGeek
|
طراحی مدل تحلیل رفتار مصرف کننده خودرو با رویکرد داده کاوی (مطالعه موردی سایپا)
5 سال پیش
0.63 مگابایت
نوع : pdf
بازدید : 3023
منتشرکننده : CarGeek
|
بررسی تزریق مستقیم بنزین (GDI) روی موتور XU7 JP/L3 و مقایسه آن با حالت MPFI
5 سال پیش
0.49 مگابایت
نوع : pdf
بازدید : 6473
منتشرکننده : CarGeek
|
بررسی فناوری های نو و کاهش آلودگی ناشی از وسایل نقلیه موتوری
5 سال پیش
0.25 مگابایت
نوع : pdf
بازدید : 3023
منتشرکننده : CarGeek
|
جزوه راهنمای ایران خودرو در خصوص BSI پژو 206
5 سال پیش
1.76 مگابایت
نوع : pdf
بازدید : 11673
منتشرکننده : CarGeek
|
راهنمای تعمیرات تزئینات و قطعات خودرو رانا
5 سال پیش
7.6 مگابایت
نوع : pdf
بازدید : 9962
منتشرکننده : CarGeek
|
راهنمای تعمیرات و عیب یابی سیستم گازسوز پژو پارس + نقشه مدارها
5 سال پیش
9.82 مگابایت
نوع : pdf
بازدید : 13966
منتشرکننده : CarGeek
|
دستورالعمل عیب یابی و تعویض دینام/آلترناتور پراید
5 سال پیش
0.72 مگابایت
نوع : pdf
بازدید : 13172
منتشرکننده : CarGeek
|
راهنمای تعمیرات و سرویس بخاری و ایرکاندیشن نیسان پیکاپ
5 سال پیش
2.38 مگابایت
نوع : pdf
بازدید : 11125
منتشرکننده : CarGeek
|
راهنمای تعمیرات تعلیق جلو و عقب نیسان ماکسیما
5 سال پیش
1.2 مگابایت
نوع : pdf
بازدید : 7748
منتشرکننده : CarGeek
|
راهنمای مدارات الکتریکی سیستم ضدسرقت ایموبیلایزر زیمنس و ولئو سایپا پراید
5 سال پیش
0.94 مگابایت
نوع : pdf
بازدید : 6476
منتشرکننده : CarGeek
|
کاتالوگ کامل خانواده موتورهای هیوندای
5 سال پیش
7.57 مگابایت
نوع : pdf
بازدید : 19345
منتشرکننده : CarGeek
|
راهنمای تعمیرات سیستم سوخت رسانی پایه گازسوز پراید (Continental)
5 سال پیش
2 مگابایت
نوع : pdf
بازدید : 4673
منتشرکننده : CarGeek
|
راهنمای تعمیرات فرمان هیدرولیک و سیستم ضدقفل چرخ های تندر90
5 سال پیش
0.55 مگابایت
نوع : pdf
بازدید : 8252
منتشرکننده : CarGeek
|
راهنمای کامل آموزشی ایساکو در خصوص تعمیرات دنا (موتور EF7 و XUM)
5 سال پیش
12.27 مگابایت
نوع : pdf
بازدید : 11513
منتشرکننده : CarGeek
|
تشریح سیستم سوخت رسانی انژکتوری EFI روی مزدا323
5 سال پیش
3.69 مگابایت
نوع : pdf
بازدید : 5942
منتشرکننده : CarGeek
|
دفترچه راهنمای خودرو برلیانس H330 سایپا
5 سال پیش
7.76 مگابایت
نوع : pdf
بازدید : 54090
منتشرکننده : CarGeek
|
دفترچه راهنمای خودروهای H220 و H230 سایپا
5 سال پیش
4.12 مگابایت
نوع : pdf
بازدید : 38777
منتشرکننده : CarGeek
|
دفترچه راهنمای خودرو سایپا آریو (S300)
5 سال پیش
9.01 مگابایت
نوع : pdf
بازدید : 33874
منتشرکننده : CarGeek
|
راهنمای تعمیرات سیستم ترمز پراید
5 سال پیش
3.75 مگابایت
نوع : pdf
بازدید : 12765
منتشرکننده : CarGeek
|
راهنمای تعمیرات و عیب یابی سیستم ضدسرقت تندر90
5 سال پیش
0.4 مگابایت
نوع : pdf
بازدید : 4783
منتشرکننده : CarGeek
|
راهنمای تعمیرات ، معرفی و جانمایی دسته سیم های الکتریکی خودرو پژو 405 و پژو پارس
5 سال پیش
2.04 مگابایت
نوع : pdf
بازدید : 60200
منتشرکننده : CarGeek
|
عیب یابی و نقشه سیستم ایموبیلایزر ضدسرقت Bosch سایپا
5 سال پیش
0.38 مگابایت
نوع : pdf
بازدید : 5187
منتشرکننده : CarGeek
|
دستورالعمل تصویری کامل پیاده و سوارکردن گیربکس و جعبه دنده خودرو
5 سال پیش
0.99 مگابایت
نوع : pdf
بازدید : 20093
منتشرکننده : CarGeek
|
راهنمای کامل و اصلی تعمیر و نگه داری لیفان 620
5 سال پیش
18.14 مگابایت
نوع : pdf
بازدید : 24003
منتشرکننده : CarGeek
|
راهنمای تعمیرات و سرویس سیستم گرمایش و تهویه هوا (خنک کننده) X33
5 سال پیش
7.36 مگابایت
نوع : pdf
بازدید : 23965
منتشرکننده : CarGeek
|
جزوه آموزشی ایساکو در خصوص داشبورد جدید خانواده پژو پارس و پژو 405
5 سال پیش
5.05 مگابایت
نوع : pdf
بازدید : 20750
منتشرکننده : CarGeek
|
راهنمای سیستم تجهیزات الکتریکی سایپا 111
5 سال پیش
3.15 مگابایت
نوع : pdf
بازدید : 4226
منتشرکننده : CarGeek
|
راهنمای تعمیرات و سرویس مجموعه اکسل جلو و عقب تیبا- فایل 2
5 سال پیش
1.21 مگابایت
نوع : pdf
بازدید : 4417
منتشرکننده : CarGeek
|
راهنمای تعمیرات و سرویس مجموعه اکسل جلو و عقب تیبا
5 سال پیش
1.28 مگابایت
نوع : pdf
بازدید : 9719
منتشرکننده : CarGeek
|
راهنمای تعمیرات مدارات الکتریکی وانت شوکا
5 سال پیش
0.78 مگابایت
نوع : pdf
بازدید : 12413
منتشرکننده : CarGeek
|
راهنمای تعمیرات بدنه و تزئینات پراید (نسخه سایپا نمایندگی های خارجی)
5 سال پیش
5.26 مگابایت
نوع : pdf
بازدید : 8384
منتشرکننده : CarGeek
|
راهنمای تعمیرات تندر90 اتوماتیک ویژه معلولین
5 سال پیش
2.34 مگابایت
نوع : pdf
بازدید : 3923
منتشرکننده : CarGeek
|
نکاتی درباره نشتی روغن در موتور TU5 (پژو 206-207 ، پارسLX ، پژو 405SLX)
5 سال پیش
0.28 مگابایت
نوع : pdf
بازدید : 30635
منتشرکننده : CarGeek
|
راهنمای ایموبیلایزر و نحوه معرفی کدسوئیچ امدادخودرو- فایل 2
5 سال پیش
0.52 مگابایت
نوع : pdf
بازدید : 4759
منتشرکننده : CarGeek
|
راهنمای ایموبیلایزر و نحوه معرفی کدسوئیچ امدادخودرو
5 سال پیش
0.8 مگابایت
نوع : pdf
بازدید : 11836
منتشرکننده : CarGeek
|
راهنمای تعمیرات و عیب یابی موتور M13 یورو4 سایپا پراید
5 سال پیش
3.95 مگابایت
نوع : pdf
بازدید : 46625
منتشرکننده : CarGeek
|
راهنمای عیب یابی تجهیزات الکتریکی و ایموبیلایزر ریو
5 سال پیش
0.91 مگابایت
نوع : pdf
بازدید : 10151
منتشرکننده : CarGeek
|
راهنما و روش های عیب یابی ایموبیلایزر پژو206 و پژو207i
5 سال پیش
0.95 مگابایت
نوع : pdf
بازدید : 6583
منتشرکننده : CarGeek
|
راهنمای تعمیرات سیستم تهویه مطبوع سایپا تیبا
5 سال پیش
1.5 مگابایت
نوع : pdf
بازدید : 25198
منتشرکننده : CarGeek
|
راهنمای عیب یابی ، برنامه ریزی و تعمیر سیستم رادیو و پخش تندر90
5 سال پیش
1.24 مگابایت
نوع : pdf
بازدید : 17295
منتشرکننده : CarGeek
|
اطلاعیه فنی احتمال ایراد سیستم کولر و پرش شمارنده کیلومتر پژو206 و رانا + راه حل
5 سال پیش
0.21 مگابایت
نوع : pdf
بازدید : 8454
منتشرکننده : CarGeek
|
راهنمای عیب یابی سیستم سوخت رسانی تندر90
5 سال پیش
2.25 مگابایت
نوع : pdf
بازدید : 26711
منتشرکننده : CarGeek
|
معرفی سامانه خنک کاری موتور EF7
5 سال پیش
1.27 مگابایت
نوع : pdf
بازدید : 16697
منتشرکننده : CarGeek
|
مشخصات روغن موتور مناسب برای خودروهای تولید رنو
5 سال پیش
0.42 مگابایت
نوع : pdf
بازدید : 8691
منتشرکننده : CarGeek
|
گشتاور پیچ های خودروهای سمند ، پژو405 ،پژو پارس ، پژو206 ،پیکان و پژوRD
5 سال پیش
1.97 مگابایت
نوع : pdf
بازدید : 81349
منتشرکننده : CarGeek
|
نقشه سیستم سوخت رسانی و PinLayout و استراتژیEMS SSAT پژو 405 و پژو پارس
5 سال پیش
0.84 مگابایت
نوع : pdf
بازدید : 25739
منتشرکننده : CarGeek
|
راهنمای کامل تعمیرات و سرویس مدارهای الکتریکی تیبا + نقشه ها
5 سال پیش
18 مگابایت
نوع : pdf
بازدید : 44442
منتشرکننده : CarGeek
|
نکات مهم در خصوص تعمیرات خودرو کپچر
5 سال پیش
0.35 مگابایت
نوع : pdf
بازدید : 3696
منتشرکننده : CarGeek
|
کتاب لیست و مشخصات کامل قطعات یدکی خودرو رونیز
5 سال پیش
5.04 مگابایت
نوع : pdf
بازدید : 14993
منتشرکننده : CarGeek
|
راهنمای تعمیرات و سرویس مدارهای الکتریکی سایپا 132
5 سال پیش
6.86 مگابایت
نوع : pdf
بازدید : 14814
منتشرکننده : CarGeek
|
راهنمای کامل تعمیرات و سرویس مدارهای الکتریکی سایپا131 (پراید صندوق دار) + نقشه ها
5 سال پیش
1.62 مگابایت
نوع : pdf
بازدید : 60956
منتشرکننده : CarGeek
|
راهنمای کامل نقشه های سیم کشی پراید کاربراتور
5 سال پیش
8.18 مگابایت
نوع : pdf
بازدید : 118937
منتشرکننده : CarGeek
|
روش رفع ایراد روشن ماندن چراغ ایربگ پژو پارس ، پژو405 و سمند- فایل 2
5 سال پیش
0.61 مگابایت
نوع : pdf
بازدید : 10007
منتشرکننده : CarGeek
|
روش رفع ایراد روشن ماندن چراغ ایربگ پژو پارس ، پژو405 و سمند
5 سال پیش
0.37 مگابایت
نوع : pdf
بازدید : 20917
منتشرکننده : CarGeek
|
روش تنظیم موتور پراید کاربراتور
5 سال پیش
0.43 مگابایت
نوع : pdf
بازدید : 12687
منتشرکننده : CarGeek
|
فراخوان نشت سوخت از لوله های بالای باک پژو 405 و پژو پارس
5 سال پیش
0.72 مگابایت
نوع : pdf
بازدید : 15432
منتشرکننده : CarGeek
|
راهنمای فنی محرک برقی قفل درب های جانبی پژو 405 ، پژو پارس ، سمند و پژو RD
5 سال پیش
0.2 مگابایت
نوع : pdf
بازدید : 44825
منتشرکننده : CarGeek
|
لیست سرویس های دوره ای رنو کپچر
5 سال پیش
0.18 مگابایت
نوع : pdf
بازدید : 5043
منتشرکننده : CarGeek
|
اطلاعیه فنی احتمال خاموش شدن تندر90 بر اثر تماس سیم سنسور اکسیژن دوم با اگزوز
5 سال پیش
0.51 مگابایت
نوع : pdf
بازدید : 10819
منتشرکننده : CarGeek
|
آموزش رفع عیب گیرنده ریموت سازه پویش روی سمند ، پژو پارس و 405
5 سال پیش
0.28 مگابایت
نوع : pdf
بازدید : 7871
منتشرکننده : CarGeek
|
دستورالعمل عیب یابی و تعویض مقاومت فن دو دور پراید- فایل 2
5 سال پیش
0.18 مگابایت
نوع : pdf
بازدید : 12878
منتشرکننده : CarGeek
|
دستورالعمل عیب یابی و تعویض مقاومت فن دو دور پراید
5 سال پیش
0.97 مگابایت
نوع : pdf
بازدید : 57364
منتشرکننده : CarGeek
|
روش رفع ایراد پله ای عمل کردن شیشه بالابر در خودروهای مالتی پلکس دنا و سمند
5 سال پیش
0.33 مگابایت
نوع : pdf
بازدید : 27709
منتشرکننده : CarGeek
|
روش باز و بست سپر جلو پژو 207i
5 سال پیش
2.35 مگابایت
نوع : pdf
بازدید : 11798
منتشرکننده : CarGeek
|
دستورالعمل رفع صدای زوزه گیربکس BE3 پژو پارس ، 405 ، سمند
5 سال پیش
1.35 مگابایت
نوع : pdf
بازدید : 25663
منتشرکننده : CarGeek
|
راهنمای رسمی سیتروئن درخصوص ECUهای Bosch ME7.4.4/M7.4.4 و EOBD
5 سال پیش
0.6 مگابایت
نوع : pdf
بازدید : 9519
منتشرکننده : CarGeek
|
معرفی و راهنمای تعمیرات الکتریکال سیستم مدیریت موتور SSAT پژو 405 و پژو پارس و سمند
5 سال پیش
2.92 مگابایت
نوع : pdf
بازدید : 12389
منتشرکننده : CarGeek
|
نقشه سیم کشی ECU تندر 90
5 سال پیش
0.17 مگابایت
نوع : pdf
بازدید : 30493
منتشرکننده : CarGeek
|
جزوه آموزشی ایساکو ، سیستم انژکتور
5 سال پیش
3.87 مگابایت
نوع : pdf
بازدید : 20978
منتشرکننده : CarGeek
|
راهنمای تعمیرات میل گاردان و مجموعه دیفرانسیل نیسان پیکاپ
5 سال پیش
2.74 مگابایت
نوع : pdf
بازدید : 9555
منتشرکننده : CarGeek
|
راهنمای تعمیرات و سرویس مدارهای الکتریکی سمند و سورن
5 سال پیش
21.7 مگابایت
نوع : pdf
بازدید : 11492
منتشرکننده : CarGeek
|
راهنمای تعمیرات و سرویس سیستم تهویه مطبوع کیا ریو
5 سال پیش
6.32 مگابایت
نوع : pdf
بازدید : 17944
منتشرکننده : CarGeek
|
راهنمای تعمیرات بدنه و شاسی نیسان ماکسیما
5 سال پیش
2.11 مگابایت
نوع : pdf
بازدید : 6280
منتشرکننده : CarGeek
|
راهنمای تعمیرات بخاری ، تهویه مطبوع و سیستم حفاظت از سرنشین (ایربگ) مزدا3
5 سال پیش
9.72 مگابایت
نوع : pdf
بازدید : 7112
منتشرکننده : CarGeek
|
کتاب تعمیرات اساسی موتور و گیربکس پژو 405 ایساکو
5 سال پیش
8.93 مگابایت
نوع : pdf
بازدید : 34380
منتشرکننده : CarGeek
|
راهنمای تعمیرات موتور KA24DE نیسان پیکاپ و نیسان رونیز
5 سال پیش
8.61 مگابایت
نوع : pdf
بازدید : 19690
منتشرکننده : CarGeek
|
دستورالعمل عیب یابی و رفع عیب کمک فنر
5 سال پیش
2.26 مگابایت
نوع : pdf
بازدید : 5983
منتشرکننده : CarGeek
|
راهنمای بازکردن داشبورد پژو 206
5 سال پیش
1.69 مگابایت
نوع : pdf
بازدید : 38878
منتشرکننده : CarGeek
|
راهنمای سیستم بخاری و تهویه مطبوع سوزوکی گرندویتارا
5 سال پیش
7.13 مگابایت
نوع : pdf
بازدید : 11393
منتشرکننده : CarGeek
|
جزوه آموزشی کلاس دزدگیر اتومبیل- فایل 2
5 سال پیش
0.42 مگابایت
نوع : pdf
بازدید : 4962
منتشرکننده : CarGeek
|
جزوه آموزشی کلاس دزدگیر اتومبیل
5 سال پیش
2.84 مگابایت
نوع : pdf
بازدید : 5833
منتشرکننده : CarGeek
|
دفترچه راهنمای رسمی ایران خودرو رانا
5 سال پیش
2.8 مگابایت
نوع : pdf
بازدید : 42829
منتشرکننده : CarGeek
|
دفترچه راهنمای رسمی ایران خودرو پژو 206 (کلیه نسخه ها)
5 سال پیش
3.19 مگابایت
نوع : pdf
بازدید : 134934
منتشرکننده : CarGeek
|
نقشه الکتریکال EMS (مدیریت موتور) موتور ملی EF7 - بوش 7.4.9
5 سال پیش
1.19 مگابایت
نوع : pdf
بازدید : 50988
منتشرکننده : CarGeek
|
دستورالعمل عیب یابی سیستم ترمز خودروهای پژو پارس ، پژو 405 و سمند
5 سال پیش
0.83 مگابایت
نوع : pdf
بازدید : 20630
منتشرکننده : CarGeek
|
راهنمای تعمیرات گیربکس دستی MA5 پژو 206
5 سال پیش
9.08 مگابایت
نوع : pdf
بازدید : 15156
منتشرکننده : CarGeek
|
فیلم آموزش بازکردن ، عیب یابی و بستن گیربکس F۲۵MR مزدا۳۲۳ + مستندات اورهال
5 سال پیش
1.61 مگابایت
نوع : pdf
بازدید : 4859
منتشرکننده : CarGeek
|
راهنمای کامل آموزشی برق 206 مالتی پلکس- فایل 2
5 سال پیش
2.38 مگابایت
نوع : pdf
بازدید : 6561
منتشرکننده : CarGeek
|
راهنمای کامل آموزشی برق 206 مالتی پلکس
5 سال پیش
6.65 مگابایت
نوع : pdf
بازدید : 20654
منتشرکننده : CarGeek
|
کتاب کامل و اورجینال راهنمای تعمیرات پژو 206 در ابعاد مناسب چاپ
5 سال پیش
12.27 مگابایت
نوع : pdf
بازدید : 17366
منتشرکننده : CarGeek
|
راهنمای عیب یابی و تعمیرات سیستم ضد سرقت تندر 90
5 سال پیش
0.4 مگابایت
نوع : pdf
بازدید : 7690
منتشرکننده : CarGeek
|
راهنمای سریع عیب یابی و تعمیر BM34
5 سال پیش
1.56 مگابایت
نوع : pdf
بازدید : 10274
منتشرکننده : CarGeek
|
راهنمای تعمیرات سیستم تعلیق سیتروئن C5
5 سال پیش
5.47 مگابایت
نوع : pdf
بازدید : 11545
منتشرکننده : CarGeek
|
راهنمای تعمیرات سیستم های ترمز ، تعلیق و فرمان پژو 407
5 سال پیش
19.37 مگابایت
نوع : pdf
بازدید : 7076
منتشرکننده : CarGeek
|
آموزش نصب سیم بندی سیستم قفل مرکزی زانتیا
5 سال پیش
1.41 مگابایت
نوع : pdf
بازدید : 9010
منتشرکننده : CarGeek
|
راهنمای تعمیرات سیستم ترمز ABS پراید
5 سال پیش
3.59 مگابایت
نوع : pdf
بازدید : 42107
منتشرکننده : CarGeek
|
آموزش تصویری نصب چراغ و میکروسوئیچ داشبورد 206
5 سال پیش
0.5 مگابایت
نوع : pdf
بازدید : 11932
منتشرکننده : CarGeek
|
جزوه عیب یابی و تعمیر ECU + نحوه پروگرام کردن و تغییر کیلومتر
5 سال پیش
0.27 مگابایت
نوع : pdf
بازدید : 23979
منتشرکننده : CarGeek
|
راهنمای عیب یابی و تعمیرات صفحه نشانگرهای تندر 90
5 سال پیش
0.34 مگابایت
نوع : pdf
بازدید : 36671
منتشرکننده : CarGeek
|
معرفی کیت های گازسوز محصولات دوگانه سوز ایرانخودرو
5 سال پیش
2.39 مگابایت
نوع : pdf
بازدید : 6246
منتشرکننده : CarGeek
|
راهنمای تعمیرات سیستم سوخت رسانی کاربراتور مجهز به CLC پراید
5 سال پیش
5.31 مگابایت
نوع : pdf
بازدید : 11680
منتشرکننده : CarGeek
|
راهنمای تعمیرات و سرویس مدارهای الکتریکی سایپا 111
5 سال پیش
7.24 مگابایت
نوع : pdf
بازدید : 11000
منتشرکننده : CarGeek
|
نقشه های کامل الکتریکی مزدا 3
5 سال پیش
33.13 مگابایت
نوع : pdf
بازدید : 38965
منتشرکننده : CarGeek
|
راهنمای تعمیرات بخاری و تهویه مطبوع نیسان ماکسیما
5 سال پیش
3.87 مگابایت
نوع : pdf
بازدید : 16371
منتشرکننده : CarGeek
|
کنیستر و نحوه عملکرد آن از اداره استاندارد و مشخصات مهندسی پارس خودرو
5 سال پیش
0.15 مگابایت
نوع : pdf
بازدید : 11590
منتشرکننده : CarGeek
|
موتور TU5 :معرفی ، مشخصات و فیلم کامل تشریح اجزاء و باز کردن
5 سال پیش
0.38 مگابایت
نوع : pdf
بازدید : 15771
منتشرکننده : CarGeek
|
راهنمای تعمیرات و سرویس اکسل و سیستم انتقال قدرت ریو
5 سال پیش
2.54 مگابایت
نوع : pdf
بازدید : 6203
منتشرکننده : CarGeek
|
راهنمای تایم گیری موتور XU7-JP4-L4 (موتور زانتیا)
5 سال پیش
4.13 مگابایت
نوع : pdf
بازدید : 23473
منتشرکننده : CarGeek
|
نقشه ECU بوش 7.4.4 موتور TU5JP4 (پژو 206 تیپ 5 و پژو 207)
5 سال پیش
2.03 مگابایت
نوع : pdf
بازدید : 42950
منتشرکننده : CarGeek
|
راهنمای تعمیرات ، معرفی و عیب یابی سیستم های BSI و ایموبلایزر پژو 206
5 سال پیش
11.45 مگابایت
نوع : pdf
بازدید : 14746
منتشرکننده : CarGeek
|
راهنمای معرفی و عیب یابی سیستم ضدقفل ترمز ABS پژو 206
5 سال پیش
4.57 مگابایت
نوع : pdf
بازدید : 23083
منتشرکننده : CarGeek
|
راهنمای تعمیرات CNG انژکتوری زیمنس جدید پراید
5 سال پیش
13.63 مگابایت
نوع : pdf
بازدید : 11639
منتشرکننده : CarGeek
|
راهنمای عیب یابی و تعمیرات سیستم سوخت رسانی زیمنس یورو 4 پراید
5 سال پیش
2.43 مگابایت
نوع : pdf
بازدید : 30339
منتشرکننده : CarGeek
|
راهنمای تعمیرات الکتریکال سیستم مالتی پلکس SMS سمند و سورن
5 سال پیش
2.61 مگابایت
نوع : pdf
بازدید : 12004
منتشرکننده : CarGeek
|
نقشه ECU زیمنس SIM 2K-34
5 سال پیش
0.19 مگابایت
نوع : pdf
بازدید : 70960
منتشرکننده : CarGeek
|
نقشه ECU Bosch 7.3 زانتیا 1800
5 سال پیش
0.44 مگابایت
نوع : pdf
بازدید : 17689
منتشرکننده : CarGeek
|
نقشه ECU Bosch MP5.2 زانتیا 2000
5 سال پیش
0.4 مگابایت
نوع : pdf
بازدید : 24563
منتشرکننده : CarGeek
|
دستورالعمل تعویض طبق تعلیق پراید
5 سال پیش
0.7 مگابایت
نوع : pdf
بازدید : 8294
منتشرکننده : CarGeek
|
جزوه راهنمای تعمیر موتور پراید
5 سال پیش
0.9 مگابایت
نوع : pdf
بازدید : 35026
منتشرکننده : CarGeek
|
راهنمای کامل نقشه های برقی پژو 206 مولتی پلکس
5 سال پیش
4.19 مگابایت
نوع : pdf
بازدید : 90268
منتشرکننده : CarGeek
|
راهنمای تعمیرات مزدا3 : نقشه های الکتریکی
5 سال پیش
33.84 مگابایت
نوع : pdf
بازدید : 10719
منتشرکننده : CarGeek
|
راهنمای تعمیرات و سرویس سیستم مدارات الکتریکی کیا ریو
5 سال پیش
11.9 مگابایت
نوع : pdf
بازدید : 29715
منتشرکننده : CarGeek
|
راهنمای فنی سیستم کلاچ ، جعبه دنده و انتقال قدرت تندر 90
5 سال پیش
7.15 مگابایت
نوع : pdf
بازدید : 7769
منتشرکننده : CarGeek
|
راهنمای تعمیرات سیستم استارت ، شارژ و دینام آلترناتور نیسان ماکسیما
5 سال پیش
0.68 مگابایت
نوع : pdf
بازدید : 13122
منتشرکننده : CarGeek
|
معرفی پژو 206 جدید از ایساکو (مدل91 به بالا - ECO MUX - کدهای 27418،27419،26803،26805)
5 سال پیش
1.57 مگابایت
نوع : pdf
بازدید : 9789
منتشرکننده : CarGeek
|
روش تعویض اجزاء چراغ جلو پژو 206 (لامپ و موتور)
5 سال پیش
0.66 مگابایت
نوع : pdf
بازدید : 67494
منتشرکننده : CarGeek
|
سیستم فن خودرو (راهنمای امداد خودرو ایران)
5 سال پیش
1.69 مگابایت
نوع : pdf
بازدید : 31579
منتشرکننده : CarGeek
|
کامپیوترها و خودروها (تاثیر کامپیوتر و اجزای آن بر خودروهای امروزی)
5 سال پیش
5.31 مگابایت
نوع : pdf
بازدید : 7989
منتشرکننده : CarGeek
|
جزوه کارگاه آموزشی سیستم مالتی پلکس سمند ، رانا و 206 ايران (P6L)
5 سال پیش
1.72 مگابایت
نوع : pdf
بازدید : 14734
منتشرکننده : CarGeek
|
بررسی نقشه سیستم سوخت رسانی انژکتوری ECU S2000 (موتورXU7-JP/L3)
5 سال پیش
18.11 مگابایت
نوع : pdf
بازدید : 39841
منتشرکننده : CarGeek
|
راهنمای تعمیرات سیستم های الکتریکی سایپا پراید
5 سال پیش
12.06 مگابایت
نوع : pdf
بازدید : 17975
منتشرکننده : CarGeek
|
مروری بر انواع گیربکس های شرکت پژو
5 سال پیش
0.67 مگابایت
نوع : pdf
بازدید : 31042
منتشرکننده : CarGeek
|
برنامه ارتقاء کیفیت و تنوع محصولات ایران خودرو (نسخه نهایی آبان 93)
5 سال پیش
1.43 مگابایت
نوع : pdf
بازدید : 4030
منتشرکننده : CarGeek
|
لیست سرویس و بازدیدهای دوره ای محصولات ایرانخودرو
5 سال پیش
6.93 مگابایت
نوع : pdf
بازدید : 49126
منتشرکننده : CarGeek
|
دستورالعمل تنظیم موتورهای خودروهای پژو405 ، پژو RD ، پیکان 1600کاربراتور
5 سال پیش
0.34 مگابایت
نوع : pdf
بازدید : 16239
منتشرکننده : CarGeek
|
راهنمای کامل نقشه های الکتریکی پژو پارس (غیرمالتی پلکس)
5 سال پیش
4.94 مگابایت
نوع : pdf
بازدید : 136198
منتشرکننده : CarGeek
|
کتاب کامل Peugeot 405 (petrol) Service and Repair Manual
5 سال پیش
10.2 مگابایت
نوع : pdf
بازدید : 10050
منتشرکننده : CarGeek
|
دفترچه راهنمای کامل پژو 405 مدل های تک سوز و دوگانه سوز GLX و SLX
5 سال پیش
2.74 مگابایت
نوع : pdf
بازدید : 148317
منتشرکننده : CarGeek
|
راهنمای عیب یابی استارت و شارژ مگان (سیستم سوخت رسانی S3000)
5 سال پیش
0.7 مگابایت
نوع : pdf
بازدید : 10091
منتشرکننده : CarGeek
|
راهنمای مدارهای الکتریکی و توزیع برق MVM X33
5 سال پیش
17.86 مگابایت
نوع : pdf
بازدید : 62409
منتشرکننده : CarGeek
|
دفترچه راهنمای کامل خودرو دنا نگارش 2015
5 سال پیش
3.58 مگابایت
نوع : pdf
بازدید : 24989
منتشرکننده : CarGeek
|
کتابچه کامل برند ایران خودرو (Iran Khodro Brand Booklet)
5 سال پیش
2.36 مگابایت
نوع : pdf
بازدید : 8537
منتشرکننده : CarGeek
|
دفترچه راهنمای کامل کلیه مدل های پژو پارس نگارش 2015
5 سال پیش
4.37 مگابایت
نوع : pdf
بازدید : 98104
منتشرکننده : CarGeek
|
دستورالعمل سرویس و شستشوی پمپ هیدرولیک فرمان پژو 405 و پارس و سمند
5 سال پیش
0.21 مگابایت
نوع : pdf
بازدید : 48219
منتشرکننده : CarGeek
|
معرفی ، عیب یابی و دستورالعمل تعویض قطعات استارتر سایپا پراید
5 سال پیش
0.55 مگابایت
نوع : pdf
بازدید : 9194
منتشرکننده : CarGeek
|
دفترچه راهنمای استفاده مزدا3 قدیم و جدید- فایل 2
5 سال پیش
9.1 مگابایت
نوع : pdf
بازدید : 6354
منتشرکننده : CarGeek
|
دفترچه راهنمای استفاده مزدا3 قدیم و جدید
5 سال پیش
14.98 مگابایت
نوع : pdf
بازدید : 29879
منتشرکننده : CarGeek
|
اصول پایه تعمیرات بدنه تندر 90
5 سال پیش
5.67 مگابایت
نوع : pdf
بازدید : 5580
منتشرکننده : CarGeek
|
معرفی و عیب یابی ترمز ABS از ایساکو
5 سال پیش
8.49 مگابایت
نوع : pdf
بازدید : 10751
منتشرکننده : CarGeek
|
راهنمای تعمیرات سیستم خنک کننده و روغنکاری موتور نیسان ماکسیما
5 سال پیش
0.88 مگابایت
نوع : pdf
بازدید : 12340
منتشرکننده : CarGeek
|
جزوه آموزش گیربکس اتوماتیک تندر 90
5 سال پیش
6.85 مگابایت
نوع : pdf
بازدید : 16910
منتشرکننده : CarGeek
|
فهرست عملیات سرویس های اولیه و سرویس های دوره ای سایپا پراید
5 سال پیش
0.15 مگابایت
نوع : pdf
بازدید : 15779
منتشرکننده : CarGeek
|
راهنمای زمان استاندارد تعمیرات خودرو پژو 206
5 سال پیش
2.23 مگابایت
نوع : pdf
بازدید : 9317
منتشرکننده : CarGeek
|
راهنمای زمان استاندارد تعمیرات خودرو پژو پارس
5 سال پیش
4.13 مگابایت
نوع : pdf
بازدید : 9449
منتشرکننده : CarGeek
|
کلاچ چیست؟ چرا لازم است؟ چگونه کار می کند؟
5 سال پیش
0.48 مگابایت
نوع : pdf
بازدید : 3895
منتشرکننده : CarGeek
|
کتابچه راهنمای استفاده از خودرو بسترن FAW B50F
5 سال پیش
14.37 مگابایت
نوع : pdf
بازدید : 20881
منتشرکننده : CarGeek
|
سیستم تعلیق خودرو چگونه کار می کند؟
5 سال پیش
0.38 مگابایت
نوع : pdf
بازدید : 4356
منتشرکننده : CarGeek
|
جزوه تعمیرات موتور TU5-JP4L4 خودروی رانا
5 سال پیش
17.78 مگابایت
نوع : pdf
بازدید : 16099
منتشرکننده : CarGeek
|
راهنمای تعمیرات سیم کشی های الکتریکی مگان
5 سال پیش
2.63 مگابایت
نوع : pdf
بازدید : 28179
منتشرکننده : CarGeek
|
راهنمای تعمیرات و تجهیزات جانبی الکتریکی پژو 206
5 سال پیش
1.16 مگابایت
نوع : pdf
بازدید : 13118
منتشرکننده : CarGeek
|
نقشه های الکتریکی پژو 206 مالتی پلکس فرانسوی
5 سال پیش
36.85 مگابایت
نوع : pdf
بازدید : 101034
منتشرکننده : CarGeek
|
دستورالعمل معرفی و عیب یابی قطعات آپشن پژو پارس و سمند
5 سال پیش
3.77 مگابایت
نوع : pdf
بازدید : 8946
منتشرکننده : CarGeek
|
راهنمای تعمیرات گیربکس رانا (گیربکس BE)
5 سال پیش
8.2 مگابایت
نوع : pdf
بازدید : 14027
منتشرکننده : CarGeek
|
راهنمای تعمیرات و سرویس سیستم تعلیق جلو و عقب پژو 405
5 سال پیش
31.3 مگابایت
نوع : pdf
بازدید : 25701
منتشرکننده : CarGeek
|
فهرست موتورهای پژو XU7 و سیستم سوخت رسانی و EMS
5 سال پیش
1.56 مگابایت
نوع : pdf
بازدید : 14070
منتشرکننده : CarGeek
|
بهینه سازی چندراهه ورودی موتور XU7/L3 با هدف افزایش بازده تنفسی
5 سال پیش
0.71 مگابایت
نوع : pdf
بازدید : 17265
منتشرکننده : CarGeek
|
معرفی و عیب یابی انواع کیت های خودروهای دوگانه سوز پژو 405
5 سال پیش
5.23 مگابایت
نوع : pdf
بازدید : 13656
منتشرکننده : CarGeek
|
راهنمای آزمایش سیستم سوخت رسانی موتور XU7
5 سال پیش
14.52 مگابایت
نوع : pdf
بازدید : 13656
منتشرکننده : CarGeek
|
راهنمای تعمیرات و سرویس مدارهای الکتریکی سمند با موتور ملی (سمند EF7) - نسخه انگلیسی
5 سال پیش
11.7 مگابایت
نوع : pdf
بازدید : 52718
منتشرکننده : CarGeek
|
راهنمای عیب یابی سیستماتیک برق پراید
5 سال پیش
0.41 مگابایت
نوع : pdf
بازدید : 29298
منتشرکننده : CarGeek
|
راهنمای تعمیرات و عیب یابی 206 صندوقدار دوگانه سوز
5 سال پیش
3.27 مگابایت
نوع : pdf
بازدید : 20228
منتشرکننده : CarGeek
|
راهنمای تعمیرات سیستم خنک کاری،منیفولد و اگزوز پژو پارس با موتور TU5
5 سال پیش
1.83 مگابایت
نوع : pdf
بازدید : 23254
منتشرکننده : CarGeek
|
راهنمای تعمیرات مکانیکی پژو پارس با موتور TU5 (مشابه 405SLX و 206 تیپ 5و6)
5 سال پیش
14.28 مگابایت
نوع : pdf
بازدید : 30529
منتشرکننده : CarGeek
|
نقشه الکترونیکی صفحه آمپر سیتروئن C5 جدید
5 سال پیش
0.47 مگابایت
نوع : pdf
بازدید : 3217
منتشرکننده : CarGeek
|
معرفی شبکه مالتی پلکس و راهنمای سیستم های الکترونیکی سیتروئن C5 جدید
5 سال پیش
1.27 مگابایت
نوع : pdf
بازدید : 4953
منتشرکننده : CarGeek
|
مشخصات دقیق و عیب یابی موتور EF7
5 سال پیش
11 مگابایت
نوع : pdf
بازدید : 15840
منتشرکننده : CarGeek
|
مقایسه موتور EF7.TC در حالت سوخت گاز و بنزین با استفاده از شبیه سازی گرمایی پیستون و محفظه احتراق
5 سال پیش
0.36 مگابایت
نوع : pdf
بازدید : 5517
منتشرکننده : CarGeek
|
راهنمای تعمیرات و سرویس کلاچ و گیربکس ریو
5 سال پیش
6.21 مگابایت
نوع : pdf
بازدید : 8854
منتشرکننده : CarGeek
|
مکانیزم عملکرد و راهنمای تعمیرات سیستم تعلیق خودرو MVM X33
5 سال پیش
8.17 مگابایت
نوع : pdf
بازدید : 9664
منتشرکننده : CarGeek
|
راهنمای تعمیرات و سرویس گیربکس اتوماتیک مزدا3 (FN4A-EL/FS5A-EL)- فایل 2
5 سال پیش
8.66 مگابایت
نوع : pdf
بازدید : 6048
منتشرکننده : CarGeek
|
راهنمای تعمیرات و سرویس گیربکس اتوماتیک مزدا3 (FN4A-EL/FS5A-EL)
5 سال پیش
12.53 مگابایت
نوع : pdf
بازدید : 19275
منتشرکننده : CarGeek
|
راهنمای فنی سیستم تعلیق سوزوکی گرند ویتارا
5 سال پیش
5.42 مگابایت
نوع : pdf
بازدید : 7550
منتشرکننده : CarGeek
|
راهنمای فنی سیستم انتقال قدرت و اکسل سوزوکی گرند ویتارا
5 سال پیش
8.98 مگابایت
نوع : pdf
بازدید : 8640
منتشرکننده : CarGeek
|
راهنمای عیب یابی سیستم گازسوز CNG (میکسری) پراید
5 سال پیش
1.26 مگابایت
نوع : pdf
بازدید : 116521
منتشرکننده : CarGeek
|
راهنمای تعمیرات و سرویس بخاری و سیستم تهویه (کولر) مگان
5 سال پیش
8.77 مگابایت
نوع : pdf
بازدید : 35660
منتشرکننده : CarGeek
|
راهنمای تعمیرات و سرویس سیستم هیدرولیک زانتیا
5 سال پیش
18.42 مگابایت
نوع : pdf
بازدید : 10564
منتشرکننده : CarGeek
|
راهنمای تعمیرات و سرویس بخاری و سیستم تهویه (کولر) تندر 90
5 سال پیش
5.99 مگابایت
نوع : pdf
بازدید : 50142
منتشرکننده : CarGeek
|
راهنمای تعمیرات و سرویس بخاری و سیستم تهویه (کولر) سمند
5 سال پیش
2.74 مگابایت
نوع : pdf
بازدید : 106905
منتشرکننده : CarGeek
|
جدول گشتاورهای لازم پیچ و مهره ها در تعمیرات خودروهای پراید
5 سال پیش
0.17 مگابایت
نوع : pdf
بازدید : 70157
منتشرکننده : CarGeek
|
راهنمای تعمیرات و سرویس سیستم تهویه مطبوع زانتیا
5 سال پیش
4.19 مگابایت
نوع : pdf
بازدید : 34379
منتشرکننده : CarGeek
|
راهنمای تعمیرات مزدا 3 (اطلاعات عمومی و موتور)
5 سال پیش
7.83 مگابایت
نوع : pdf
بازدید : 21611
منتشرکننده : CarGeek
|
راهنمای تعمیرات موتورهای 2 لیتری پژو 407 (موتورهای سری EW10A - EW10J4 - EW10J4S)
5 سال پیش
6.87 مگابایت
نوع : pdf
بازدید : 6772
منتشرکننده : CarGeek
|
کتاب Advanced Vehicle Technology از Heinz Heisler
5 سال پیش
9.21 مگابایت
نوع : pdf
بازدید : 3880
منتشرکننده : CarGeek
|
راهنمای کامل تعمیرات مکانیکی و الکترونیکی گیربکس AL4- فایل 2
5 سال پیش
7.55 مگابایت
نوع : pdf
بازدید : 13643
منتشرکننده : CarGeek
|
راهنمای کامل تعمیرات مکانیکی و الکترونیکی گیربکس AL4
5 سال پیش
5.68 مگابایت
نوع : pdf
بازدید : 25678
منتشرکننده : CarGeek
|
راهنمای سرویس عمومی سیتروئن زانتیا
5 سال پیش
3.04 مگابایت
نوع : pdf
بازدید : 9644
منتشرکننده : CarGeek
|
راهنمای تعمیرات و سرویس بدنه سمند سورن
5 سال پیش
8.74 مگابایت
نوع : pdf
بازدید : 8173
منتشرکننده : CarGeek
|
راهنمای عیب یابی و تعمیرات ایربگ و کمربند ایمنی سمند سورن
5 سال پیش
1.6 مگابایت
نوع : pdf
بازدید : 13006
منتشرکننده : CarGeek
|
کتاب کامل (2جلد) راهنمای تعمیرات گیربکس اتوماتیک نیسان ماکسیما- فایل 2
5 سال پیش
4.25 مگابایت
نوع : pdf
بازدید : 5409
منتشرکننده : CarGeek
|
کتاب کامل (2جلد) راهنمای تعمیرات گیربکس اتوماتیک نیسان ماکسیما
5 سال پیش
5.42 مگابایت
نوع : pdf
بازدید : 14410
منتشرکننده : CarGeek
|
راهنمای ایرادها و عیب یابی موتور EF7
5 سال پیش
0.74 مگابایت
نوع : pdf
بازدید : 21818
منتشرکننده : CarGeek
|
راهنمای تعمیر موتور K4M استفاده شده روی تندر 90 مشابه موتور مگان 1600
5 سال پیش
19.03 مگابایت
نوع : pdf
بازدید : 15569
منتشرکننده : CarGeek
|
راهنمای تعمیرات و سرویس موتور XU7 پژو405، پارس و سمند
5 سال پیش
6.9 مگابایت
نوع : pdf
بازدید : 31714
منتشرکننده : CarGeek
|
معرفی و راهنمای قطعات مکانیکی موتور 0.2NA (موتور MVM 530 و چری تیگو X33)
5 سال پیش
12.01 مگابایت
نوع : pdf
بازدید : 14993
منتشرکننده : CarGeek
|
کتابچه راهنمای تعمیرات پژو 206 صندوقدار
5 سال پیش
231.16 مگابایت
نوع : pdf
بازدید : 23680
منتشرکننده : CarGeek
|
راهنمای عیب یابی سیستم سوخت رسانی گاز تندر 90
5 سال پیش
1.03 مگابایت
نوع : pdf
بازدید : 12617
منتشرکننده : CarGeek
|
کتاب کامل راهنمای تعمیرات و سرویس بدنه سمند
5 سال پیش
231.87 مگابایت
نوع : pdf
بازدید : 13753
منتشرکننده : CarGeek
|
استفاده از سیستم ترمز ریتاردر تکمیل شده در خودروها
5 سال پیش
0.17 مگابایت
نوع : pdf
بازدید : 4149
منتشرکننده : CarGeek
|
راهنمای تعمیرات و سرویس مجموعه موتور کیا ریو از سایپا یدک (موتور A5D)
5 سال پیش
4.5 مگابایت
نوع : pdf
بازدید : 18565
منتشرکننده : CarGeek
|
راهنمای عیب یابی موتور ، سیستم کلاچ و گیربکس و ترمزهای پراید
5 سال پیش
1.48 مگابایت
نوع : pdf
بازدید : 16101
منتشرکننده : CarGeek
|
راهنمای نصب کوئیک شیفتر
5 سال پیش
1.1 مگابایت
نوع : pdf
بازدید : 13836
منتشرکننده : CarGeek
|
راهنمای تعمیرات موتور زانتیا
5 سال پیش
21.26 مگابایت
نوع : pdf
بازدید : 26208
منتشرکننده : CarGeek
|


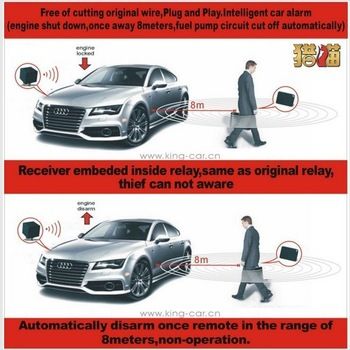


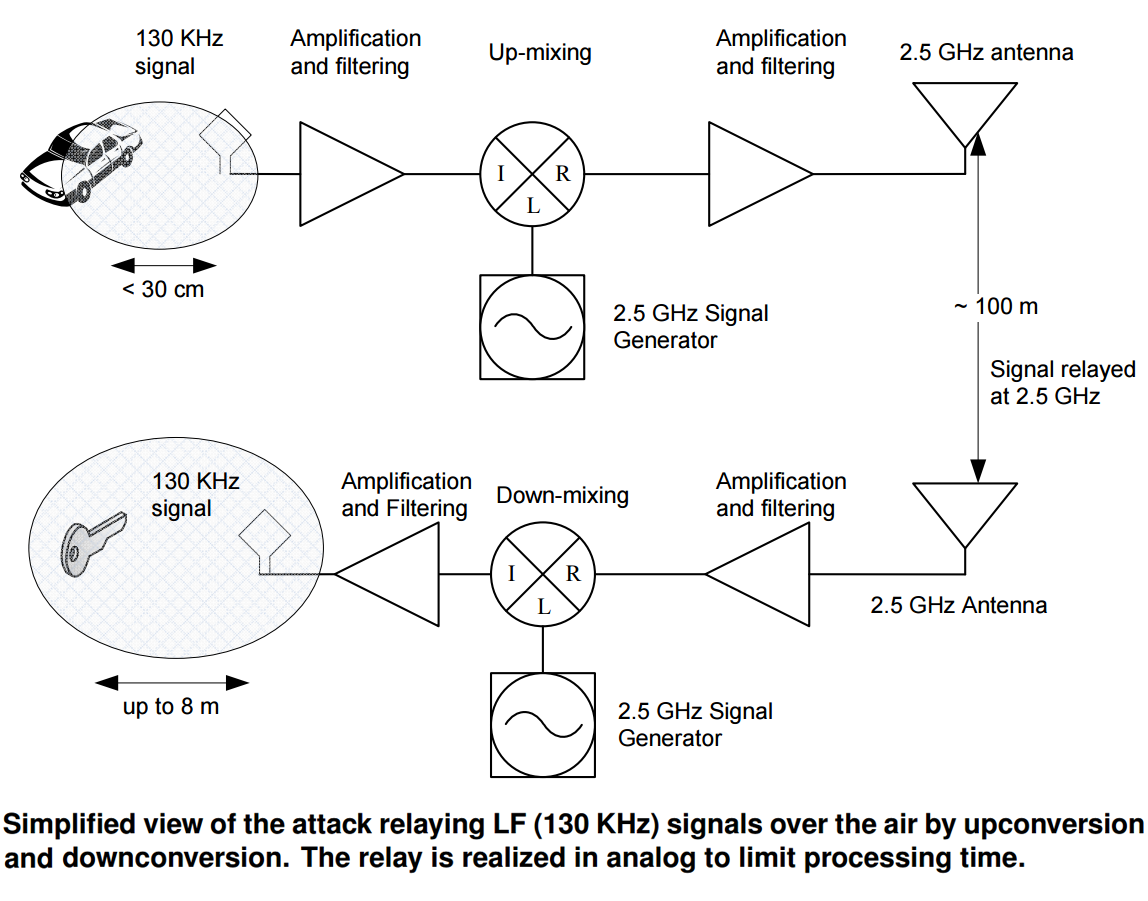

 برای پسندکردن باید عضو شوید
برای پسندکردن باید عضو شوید



